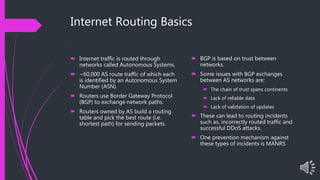
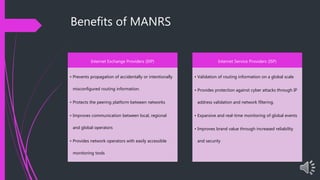
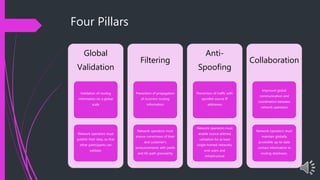
The document presents an overview of MANRS (Mutually Agreed Norms for Routing Security), highlighting its importance in addressing internet routing incidents which can lead to data theft, loss of reputation, and disruptions. It outlines the key actions required for implementation across four pillars: global validation, filtering, anti-spoofing, and collaboration, aimed at improving the security and reliability of internet infrastructure. Key takeaways emphasize the benefits of MANRS for Internet Exchange Providers (IXPs) and Internet Service Providers (ISPs) in mitigating incidents and enhancing service security.