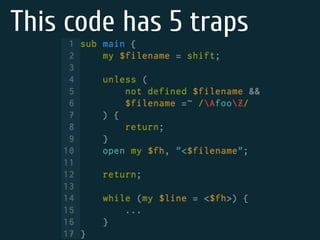
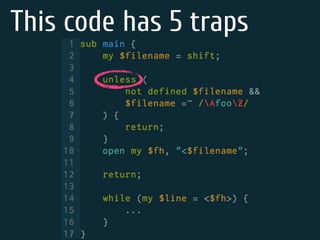
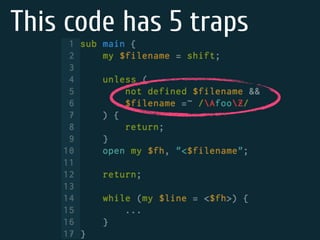
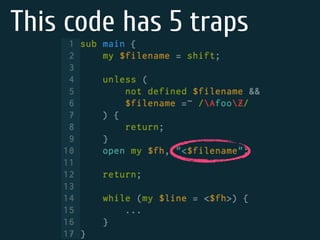
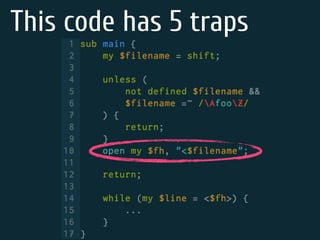
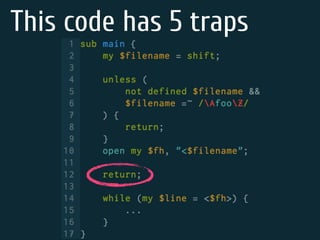
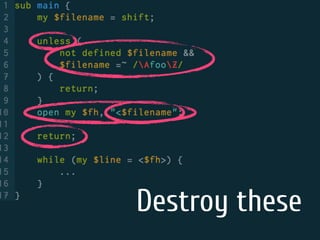
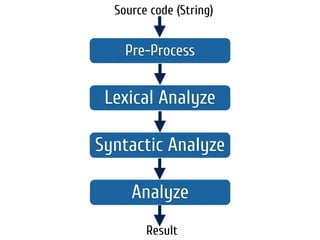
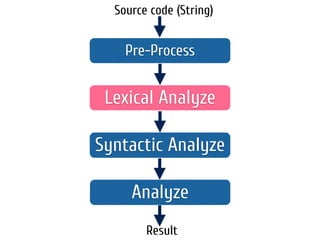
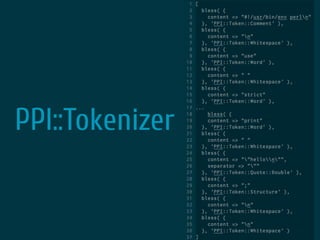
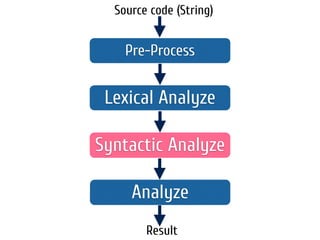
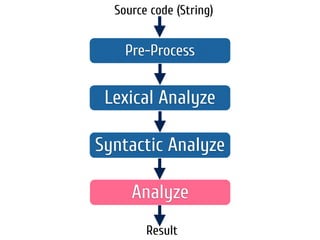
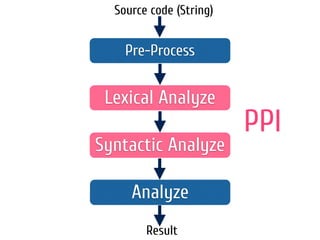
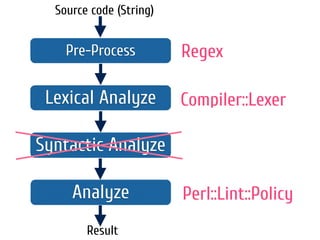
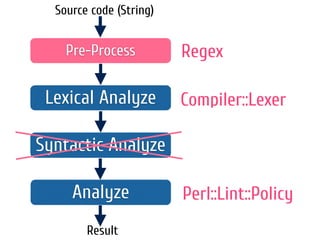
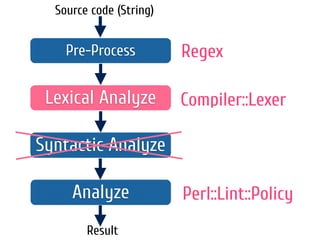
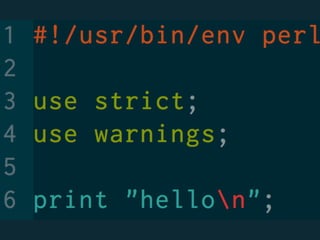
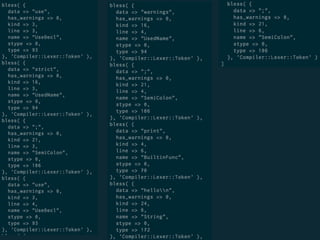
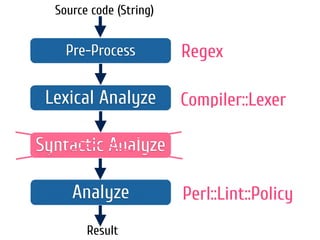
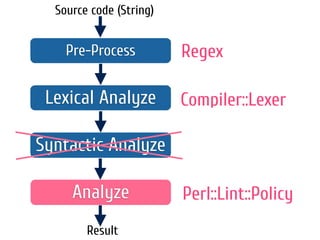
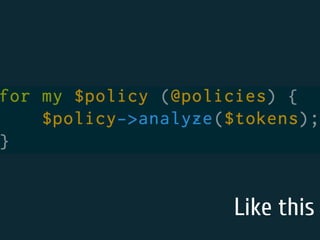
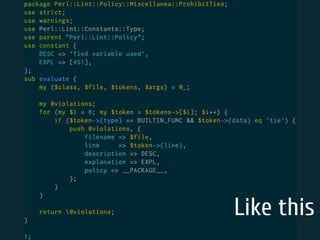
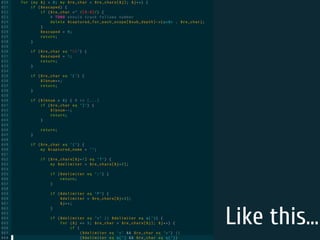
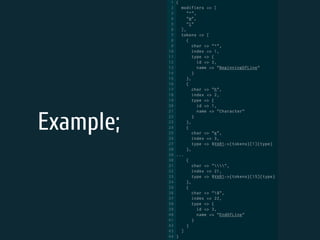
The document discusses static code analysis for Perl code. It introduces Perl::Lint, a static analysis tool developed by the author to analyze Perl code faster than existing tools like Perl::Critic. Perl::Lint uses Compiler::Lexer to tokenize the code and individual policy modules to check the tokens against coding rules. The document outlines Perl::Lint's architecture and opportunities for future improvement, such as better documentation and supporting additional Perl features.