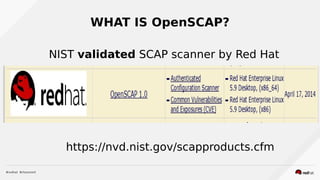
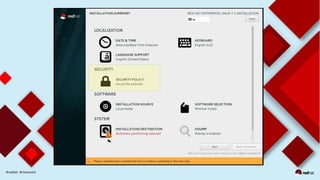
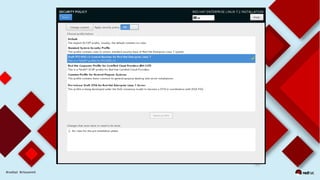
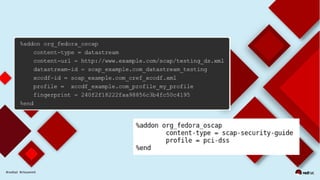
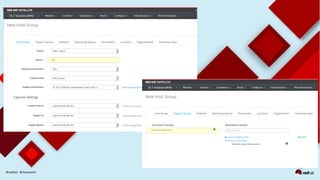
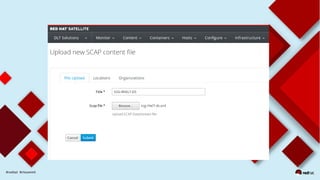
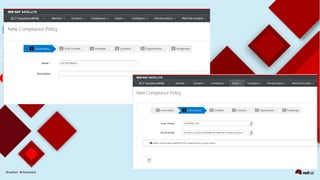
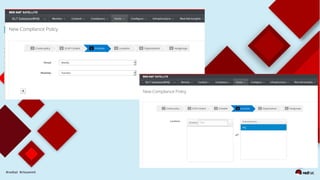
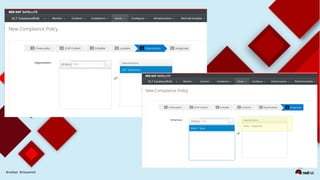
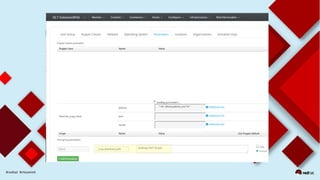
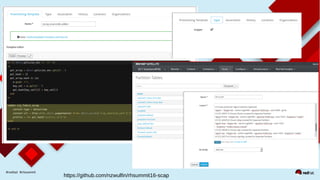
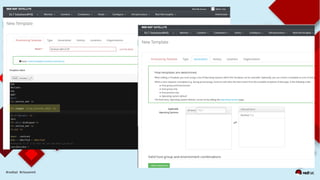
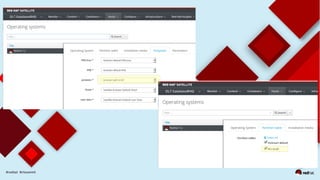
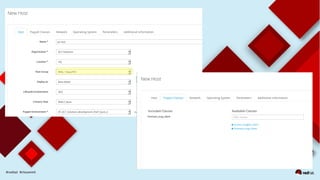
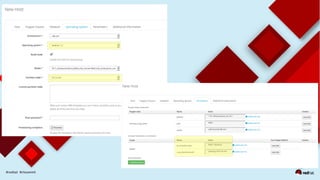
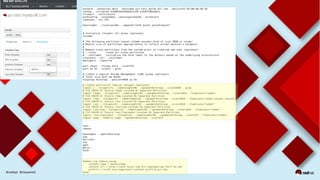
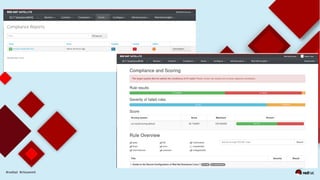
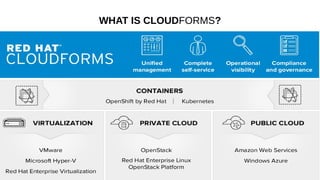
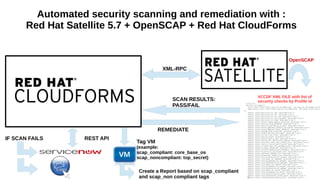
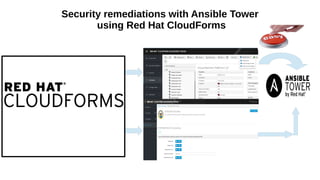
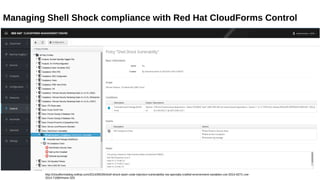
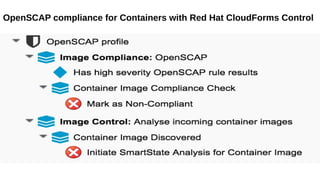
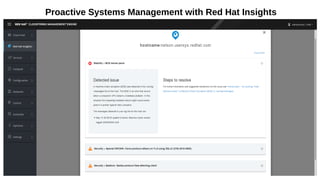
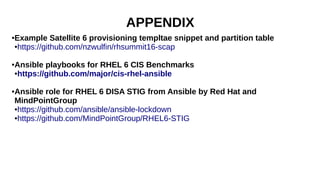
This document discusses automating security compliance and remediation using Red Hat tools. It describes two methods for creating secure hosts at provisioning time using either Satellite 6 with OpenSCAP or CloudForms with Satellite and Ansible Tower. It also discusses automating ongoing security patching and compliance through CloudForms with Satellite and OpenSCAP, CloudForms with Ansible Tower, or CloudForms control policies working with Red Hat Insights.



![Compliance, what's it good for?
CA DOJ recommends CIS Critical Security Controls as “minimum level
of information security” to meet standard of reasonableness
– California Breach Report https://oag.ca.gov/breachreport2016#findings
“Patch management and associated vulnerability management
processes represent the biggest problem areas, because they’re rarely
well documented and automated.”
– Anton Chuvakin [http://blogs.gartner.com/anton-chuvakin/2014/02/13/highlights-
from-verizon-pci-report-2014/]](https://image.slidesharecdn.com/5df7565a-c35c-48b3-bc9f-c28012c958a3-160721132619/85/SS42731_v2_KernerMicene-4-320.jpg)