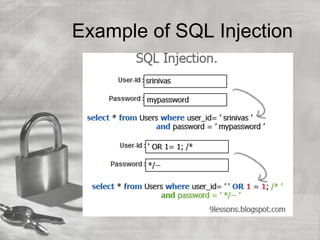
A SQL injection vulnerability has been identified that puts organizational data at high risk of unauthorized access and theft. To mitigate this high-level threat, a three-phased approach is recommended: 1) Implement immediate authentication protections, 2) Develop a project plan within 90 days to re-write vulnerable software, 3) Provide long-term SQL injection security training to prevent future vulnerabilities. Management approval is requested to proceed with Phase I while gaining support for resource-intensive Phases II-III.