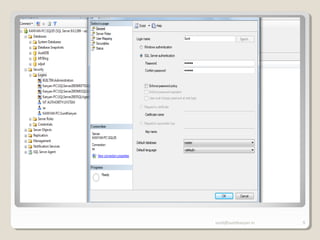
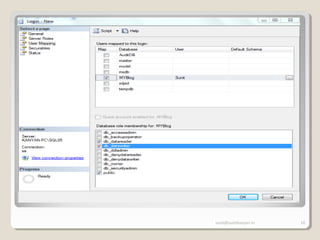
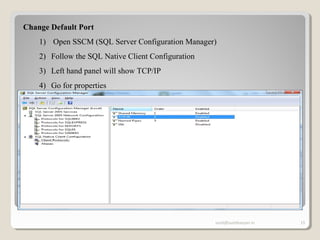
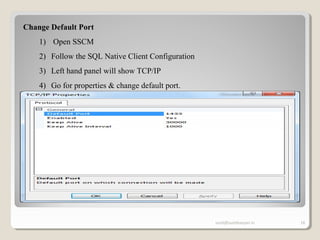
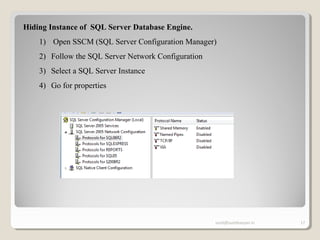
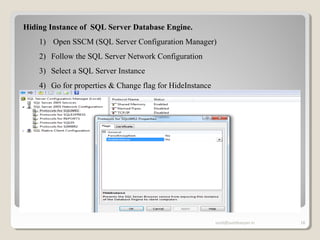
The document discusses SQL Server security, emphasizing the importance of authentication and authorization to protect against data threats and server attacks. It outlines different authentication modes, such as Windows and mixed mode, and provides guidelines for securing data and servers. Key recommendations include using least privilege access, encrypting sensitive information, and implementing security best practices like changing default ports and disabling unnecessary accounts.