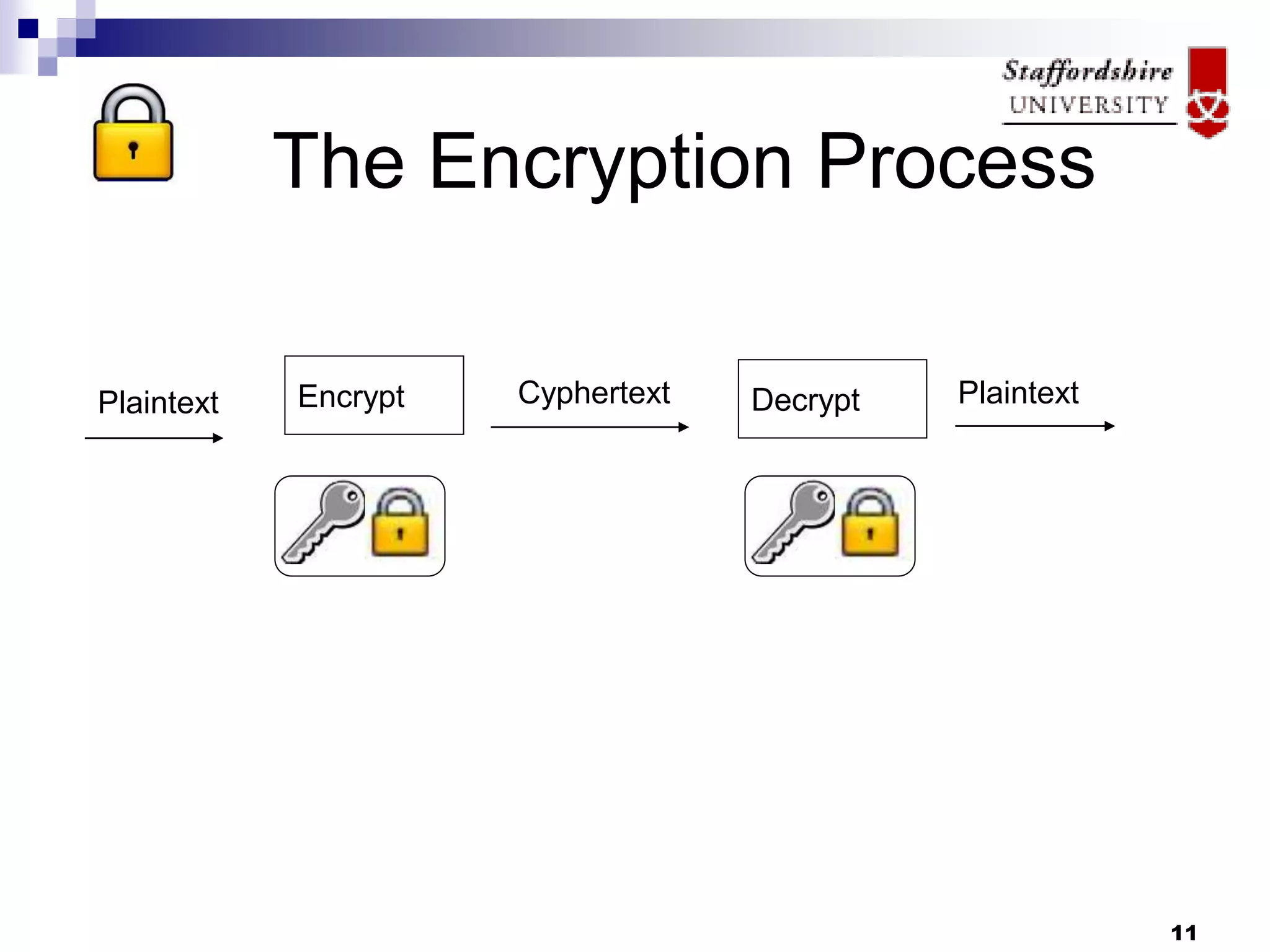
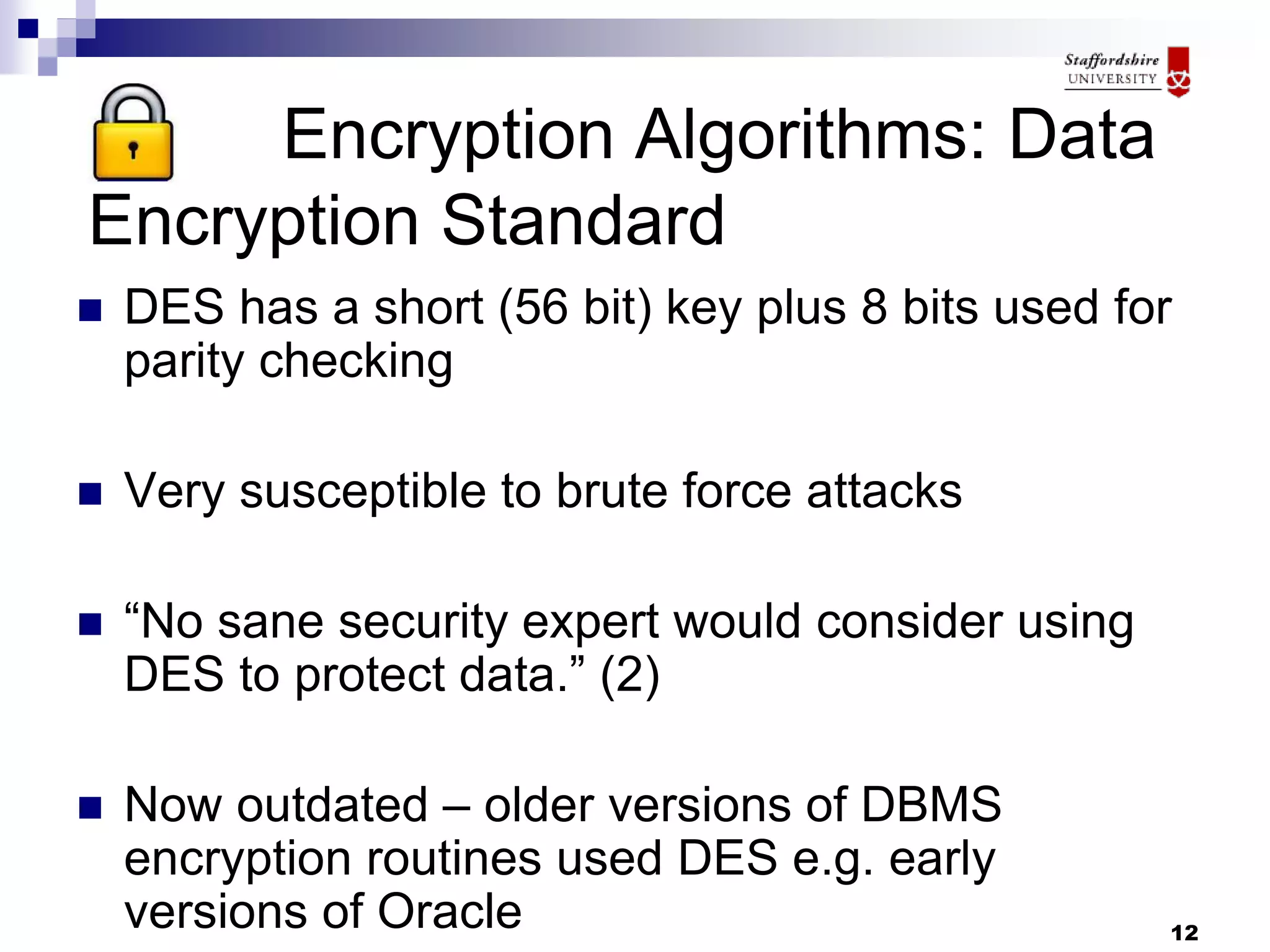
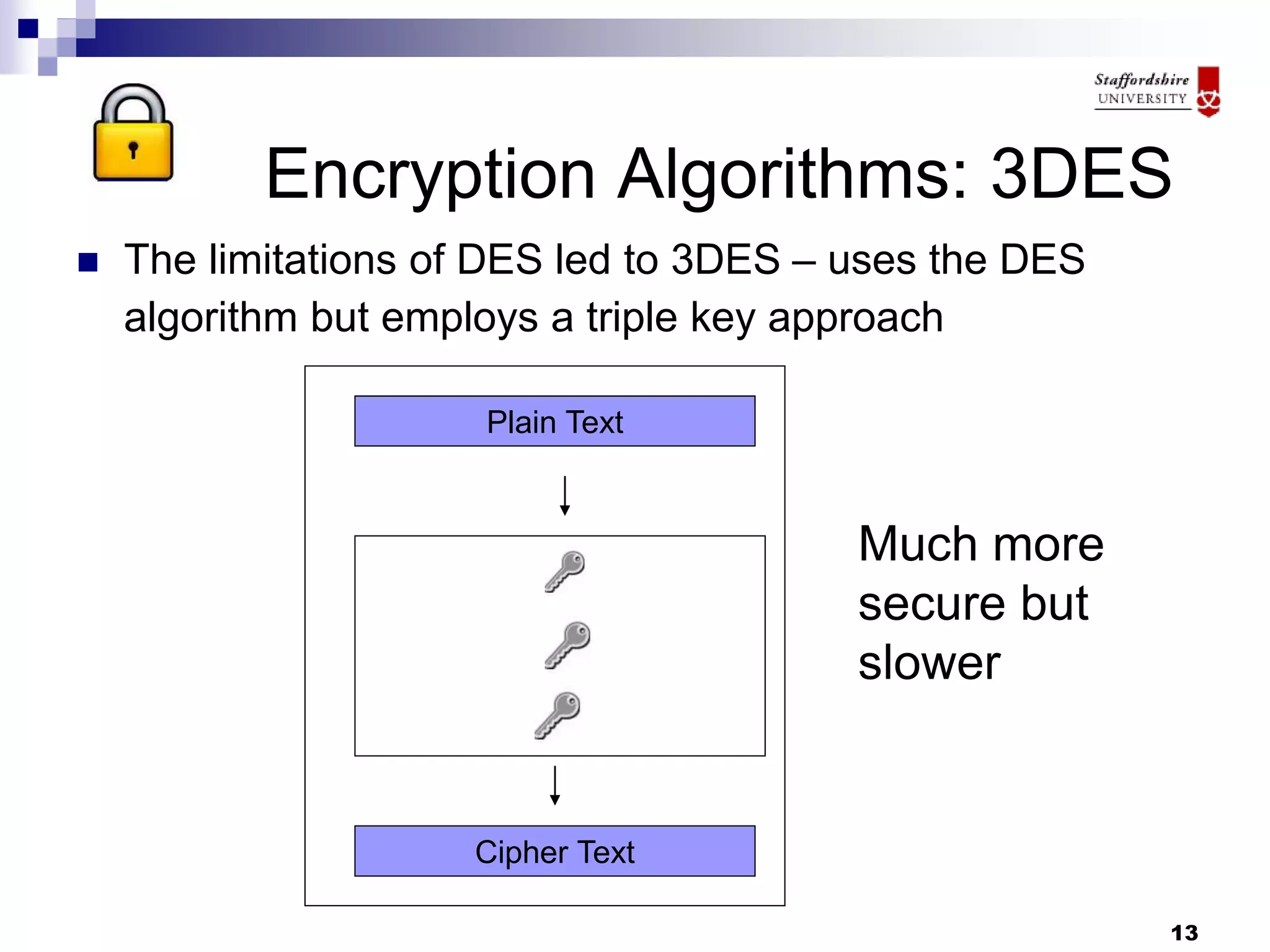
This document discusses database encryption and some of the key considerations for implementing encryption. It covers different types of encryption like whole database encryption, partial/column encryption, and encryption algorithms like AES, 3DES, and RC5. Some of the tradeoffs discussed are performance impact versus security and key management challenges. Overall, the document suggests that encryption can provide an extra layer of protection but should be part of a broader security policy, and that the specific encryption strategy depends on factors like the value of the data and threats.