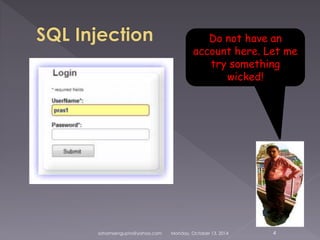
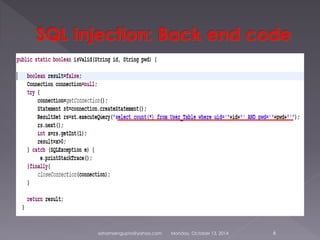
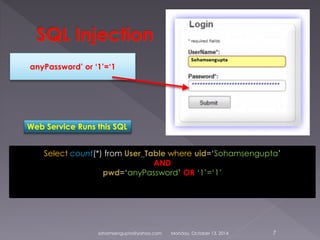
Soham Sengupta will give a presentation on surfing the web safely. He will discuss possible attacks like SQL injection, malicious cookies and software. Sengupta will demonstrate attacks and prevention mechanisms like basic cryptography. He warns about risks of using public networks, pirated software, and untrusted browsers and extensions that could steal personal information. Sengupta recommends using trusted browsers like Chrome, activating two-step authentication, and being wary of links and downloads from unknown sources to surf safely.