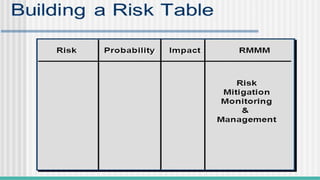
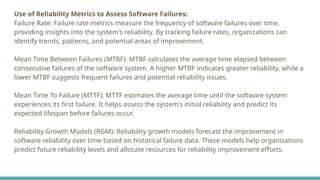
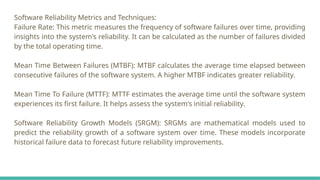
SCM is the discipline of managing and controlling changes in software. It ensures consistency, traceability, and version control across the development lifecycle.SQA is a set of activities designed to ensure that the software development process and the software product conform to defined quality standards.