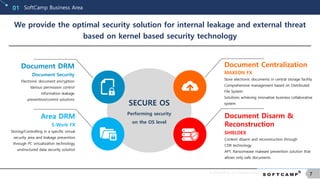
Softcamp Co., Ltd., established in 1999, specializes in information security solutions, focusing on internal leakage prevention and external threat mitigation through innovative technology. With a strong emphasis on research and development, the company boasts numerous certifications and awards for its product efficacy, particularly in the Japanese market where it leads in document security. The organization aims to expand its presence in Southeast Asia, North America, and the EU, promoting a corporate vision of being a global leader in security solutions.






![© SOFTCAMP Co., LTD. All rights reserved.
10
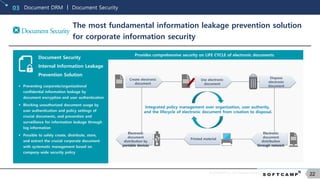
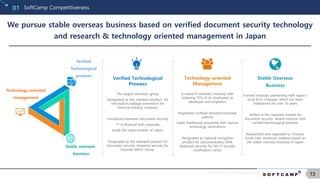
SoftCamp Overseas Business01
From early stage of establishment, we have successfully expanded to Japan
and created new development drives through overseas business
SOFTCAMP
41%
HITACHI
18%
ADOBE
9%
ORACLE
7%
EMC 3%
Etc.
22%
Japan IRM(DRM) Market Share
[ITR Market View – Contents market 2010 report]
Japan
IRM
(DRM)
Japanese Local Partners Overseas Market Expansion Efforts
1999 Expanded to Japanese market
Upon Establishment, successfully expanded to Japan through public PC
management program ‘Win-Keeper’
Successfully settled in the Japanese
document security market
Launched document DRM ‘Document Security’ in Japan through Alps
System Integration(ALSI)
Introduced and settled in large corporates with over 1000 employees
Gained first position in Japanese document
security market share
2010 ‘ ITR : ITR Market View contents management market report
Launched Japan CDR/Disarm & Reconstruction
market
Launched CDR/Disarm & Reconstruction solution ‘SHIELDEX’ complying
with the Japanese municipal government’s ‘Regulation on Network
separation and disarmament’
Introduced and led the market for disarm solution all over Japanese
municipal government](https://image.slidesharecdn.com/softcacmpcompanyintroductioneng201806-180619004415/85/Softcamp-Company-Introduction_ENG-10-320.jpg)



![© SOFTCAMP Co., LTD. All rights reserved.
19
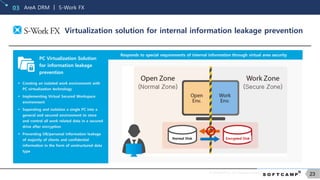
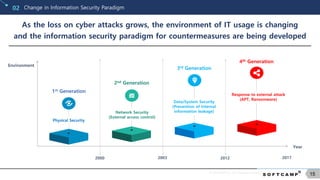
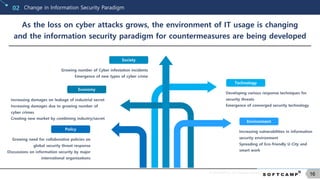
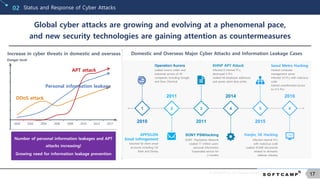
Information Leakage Prevention Market Status02
The information leakage prevention market is on the rise, as the loss
on technology leakage caused by industrial spies continue to increase
6
26
29
31 32
42 43 41
46
30
49
63
0
10
20
30
40
50
60
70
2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 2013 2014
Number of detection of industrial spies according to year
The higher the technology,
the more industrial spies there are!
“Industrial spies are one of the biggest business in the 21st
century, and they will never disappear!”
– Futurist Alvin Toffler –
Industrial spies in scale field
16%
64%
Large
corporate
s
SMEs
Large Corporate<SME
The damage is greater
2010~2014 / 5 years base
*Other 20%
University
Public research center
Precision instrument
Electric
Communication Bioengineering
Other Chemical
34%
26%
16%
14%
7%
3%
Precision instrument was
the highest at 34%
Moved from electric
to precision instrument
2010~2014 / 5 years base
Expected loss
on technology leakage
Average annual loss of
technology leaked
companies
50 trillion
KRW estimate
KAITS source
3% of GDP in 2014
SMEs X 4,700
Equivalent to an SME’s
annual revenue
SME’s annual revenue
10.7 billion(2013)
[Source : NIS industrial secret protection center]](https://image.slidesharecdn.com/softcacmpcompanyintroductioneng201806-180619004415/85/Softcamp-Company-Introduction_ENG-19-320.jpg)