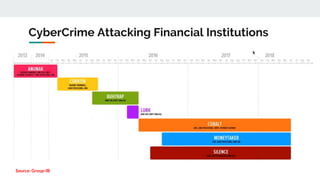
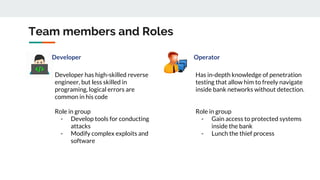
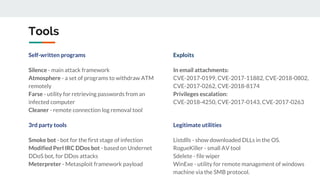
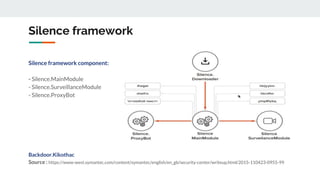
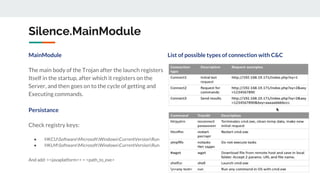
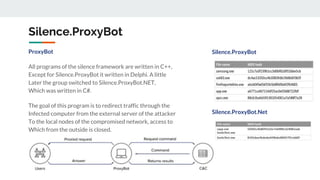
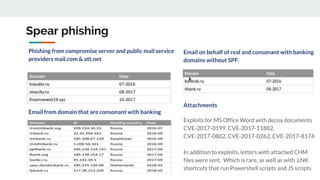
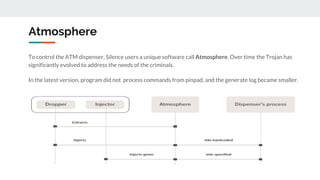
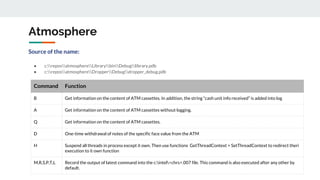
The document describes the Silence cybercrime group that has been conducting attacks against financial institutions from 2016-2018. It details the group's members and roles, targets in various countries, tools used (including their custom Silence framework and Atmosphere ATM cashout software), and spear phishing techniques. The Silence framework includes modules for command and control, surveillance of infected systems, and proxy bots. Atmosphere has evolved over time to better control ATMs and reduce logging of cashouts.