Embed presentation
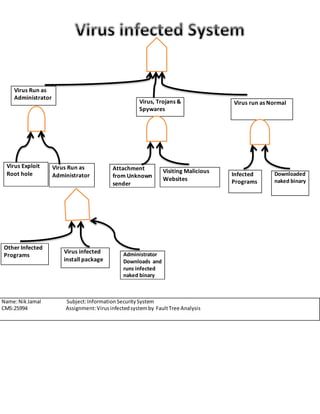

The document discusses how a virus can infect a system by exploiting administrator privileges. It notes that a virus can run as an administrator by exploiting a root hole, infecting install packages, or tricking the administrator into downloading and running an infected binary. Once running as an administrator, the virus can then infect other programs and download additional malware like trojans or spyware. The virus can also infect systems through email attachments from unknown senders, visiting malicious websites, or downloading other infected programs and naked binaries.
