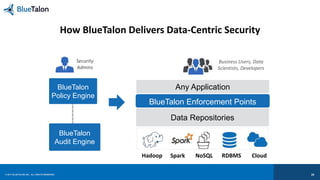
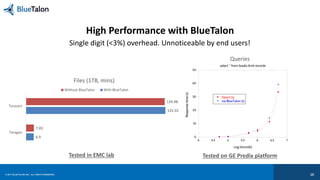
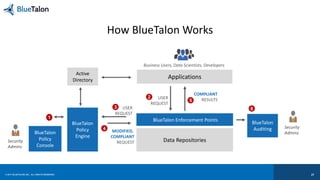
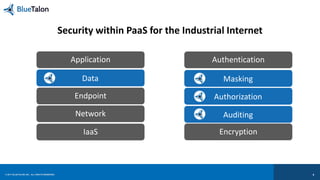
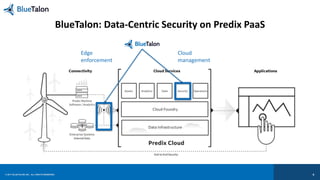
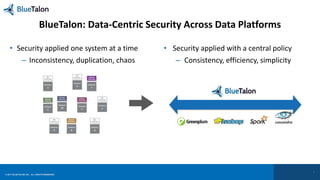
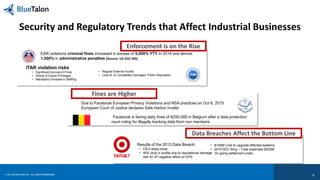
The document outlines key requirements for data security in Predix, emphasizing the importance of business context in policy definitions, automated enforcement across platforms, and maintaining user experience. It also discusses the rise of enforcement actions and regulatory trends that impact industrial businesses, highlighting the need for centralized policy decisions and visibility over data activities. Bluetalon's approach focuses on data-centric security and consistent policy application to improve efficiency and compliance.


![© 2017 BLUETALON, INC. ALL RIGHTS RESERVED.
[1] Policies are Defined by Business within a Context
“Patient information and exams are sensitive data”
“Our contracts prohibit the use of machine diagnostics data
to redesign products”
“Service managers should be able to see only their fleet data”
10](https://image.slidesharecdn.com/2017-170223074613/85/Security-of-IoT-Data-Implementing-Data-Centric-Security-and-User-Access-Strategy-10-320.jpg)
![© 2017 BLUETALON, INC. ALL RIGHTS RESERVED.
[1] Policies Applied at the Data Layer Enables Business
Blocking
Enabling
11
“Patient information and exams are sensitive data”
“Our contracts prohibit the use of customer data outside west coast”](https://image.slidesharecdn.com/2017-170223074613/85/Security-of-IoT-Data-Implementing-Data-Centric-Security-and-User-Access-Strategy-11-320.jpg)
![© 2017 BLUETALON, INC. ALL RIGHTS RESERVED.
[1] Controlling Access for Different Users & Needs
Row filtering
Field level
Cell level
Sub-cell level masking
12
Joyce looks up
her data
Her manager looks
up Joyce’s data](https://image.slidesharecdn.com/2017-170223074613/85/Security-of-IoT-Data-Implementing-Data-Centric-Security-and-User-Access-Strategy-12-320.jpg)
![© 2017 BLUETALON, INC. ALL RIGHTS RESERVED.
[1] Example of Controls Directly Applied On Data
• Access to client account is conditional, based on zipcode
• Data is partially masked
Results
Rules on Data
13](https://image.slidesharecdn.com/2017-170223074613/85/Security-of-IoT-Data-Implementing-Data-Centric-Security-and-User-Access-Strategy-13-320.jpg)
![© 2017 BLUETALON, INC. ALL RIGHTS RESERVED.
[1] Attributes Bring Context to Policies
type
location
title / role
group
function
clearance level
LOB
user session
location
timestamp
application
connection type
data
sensitivity
clearance required
action requested
# of rows returned
data source
• Context helps assess whether the data request is legitimate
14](https://image.slidesharecdn.com/2017-170223074613/85/Security-of-IoT-Data-Implementing-Data-Centric-Security-and-User-Access-Strategy-14-320.jpg)

![© 2017 BLUETALON, INC. ALL RIGHTS RESERVED.
[2] Why Centralizing Policy Decisions, Distributing Enforcement?
• IoT Platforms and Predix are hybrid environments that make
use of multiple modern data management platforms:
– RDBMS
– Hadoop
– Spark
– Cassandra
– Cloud repositories
16
Cloud On-prem](https://image.slidesharecdn.com/2017-170223074613/85/Security-of-IoT-Data-Implementing-Data-Centric-Security-and-User-Access-Strategy-16-320.jpg)
![© 2017 BLUETALON, INC. ALL RIGHTS RESERVED.
[2] Centralize Decisions to Manage Polices from One Place
17
Authorization — what a user or a role can do with the data
Decision — against all rules, can a user see a data element
Enforcement — apply the decision at the time of user’s request](https://image.slidesharecdn.com/2017-170223074613/85/Security-of-IoT-Data-Implementing-Data-Centric-Security-and-User-Access-Strategy-17-320.jpg)
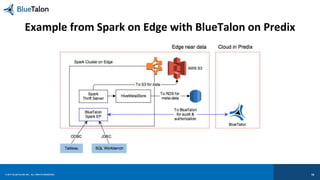
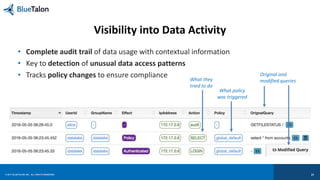
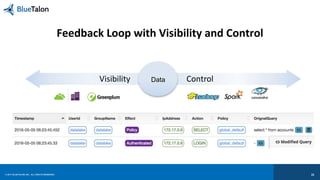
![© 2017 BLUETALON, INC. ALL RIGHTS RESERVED. 20
[3] Visibility Leverage the Same Enforcement Points](https://image.slidesharecdn.com/2017-170223074613/85/Security-of-IoT-Data-Implementing-Data-Centric-Security-and-User-Access-Strategy-20-320.jpg)