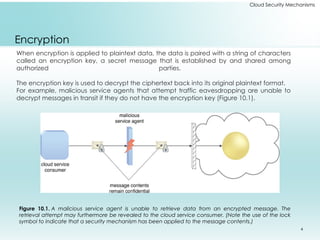
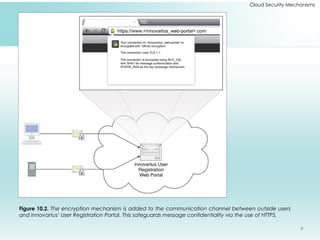
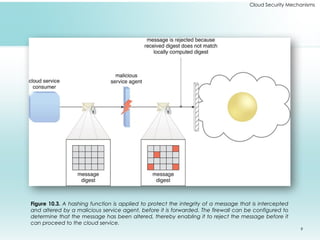
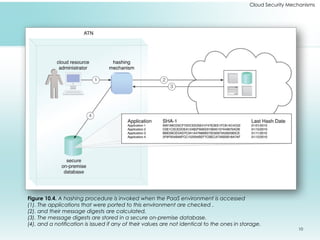
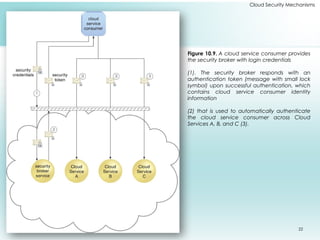
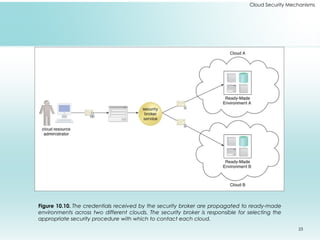
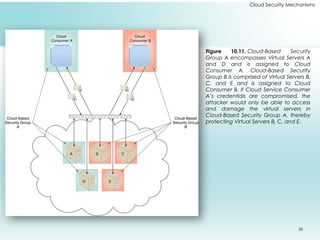
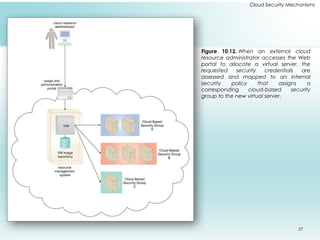
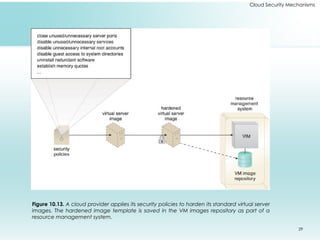
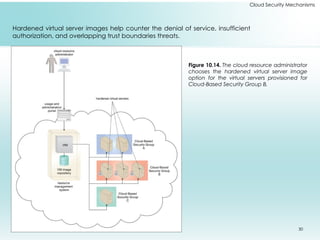
This document outlines fundamental cloud security mechanisms to address various security threats, including encryption, hashing, and identity management. Key concepts include symmetric and asymmetric encryption, digital signatures for data integrity, public key infrastructure for key management, and identity and access management to control user privileges. Additionally, it discusses the importance of single sign-on, cloud-based security groups for resource segmentation, and the role of hardened virtual server images in enhancing security.