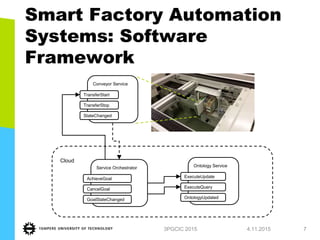
The document outlines research on security challenges in cloud-based cyber-physical systems, discussing issues in factory automation and smart mobility services. It highlights risks such as denial of service attacks, unauthorized data access, and the importance of systematic security methods in multi-cloud environments. The findings emphasize the necessity of careful selection of cloud service providers and the integration of security measures into the design and deployment of these systems.



![Recent Research on
Security in Cloud-Based
Cyber-Physical Systems (1/2)
• Cloud-based systems are accessed over the
internet → DoS and DDoS
–Pattern-based request filtering
Mobile Phone Networks [1] Smartphones [2]
● Availability of
Public services;
DoS
● Privacy; sensor
access
Vehicular Clouds [3]
● Context-awareness
● CVSMs
4.11.20153PGCIC 2015 4](https://image.slidesharecdn.com/securesyscomm2015presentation1570163779-151109111929-lva1-app6892/85/Security-in-Cloud-based-Cyber-physical-Systems-4-320.jpg)
![Recent Research on
Security in Cloud-Based
Cyber-Physical Systems (2/2)
• Risk and threat analysis
– attack tree models considering
both the cyber and the physical
aspects [4]
– calculation of risk of each attack
path as a function of vulnerability
and threat [4]
• Object-oriented security requirements
analysis, specification, prioritization,
and policy development framework
[5]
Ultimate Goal
Sub Goal A Sub Goal B
Sub Goal C Sub Goal D
AND
[4]
User
Activities
Malicious
Activities
Prevention
Options
[5]
4.11.20153PGCIC 2015 5
OR](https://image.slidesharecdn.com/securesyscomm2015presentation1570163779-151109111929-lva1-app6892/85/Security-in-Cloud-based-Cyber-physical-Systems-5-320.jpg)









![References
[1] L. Liu, X. Zhang, G. Yan, and S. Chen, “Exploitation and Threat Analysis of Open Mobile Devices,” in Proceedings
of the 5th ACM/IEEE Symposium on Architectures for Networking and Communications Systems, ser. ANCS ’09. New
York, NY, USA: ACM, 2009, pp. 20–29.
[2] L. Lei, Y. Wang, J. Zhou, D. Zha, and Z. Zhang, “A Threat to Mobile Cyber-Physical Systems: Sensor-Based
Privacy Theft Attacks on Android Smartphones,” in 2013 12th IEEE International Conference on Trust, Security and
Privacy in Computing and Communications (TrustCom), Jul. 2013, pp. 126–133.
[3] J. Wan, D. Zhang, S. Zhao, L. Yang, and J. Lloret, “Context-aware vehicular cyber-physical systems with cloud
support: architecture, challenges, and solutions,” IEEE Communications Magazine, vol. 52, no. 8, pp. 106–113, Aug.
2014.
[4] F. Xie, T. Lu, X. Guo, J. Liu, Y. Peng, and Y. Gao, “Security Analysis on Cyber-physical System Using Attack Tree,”
in 2013 Ninth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Oct. 2013,
pp. 429–432.
[5] K. Fletcher and X. Liu, “Security Requirements Analysis, Specification, Prioritization and Policy Development in
Cyber-Physical Systems,” in 2011 5th International Conference on Secure Software Integration Reliability Improvement
Companion (SSIRI-C), Jun. 2011, pp. 106–113.
4.11.20153PGCIC 2015 16](https://image.slidesharecdn.com/securesyscomm2015presentation1570163779-151109111929-lva1-app6892/85/Security-in-Cloud-based-Cyber-physical-Systems-16-320.jpg)
