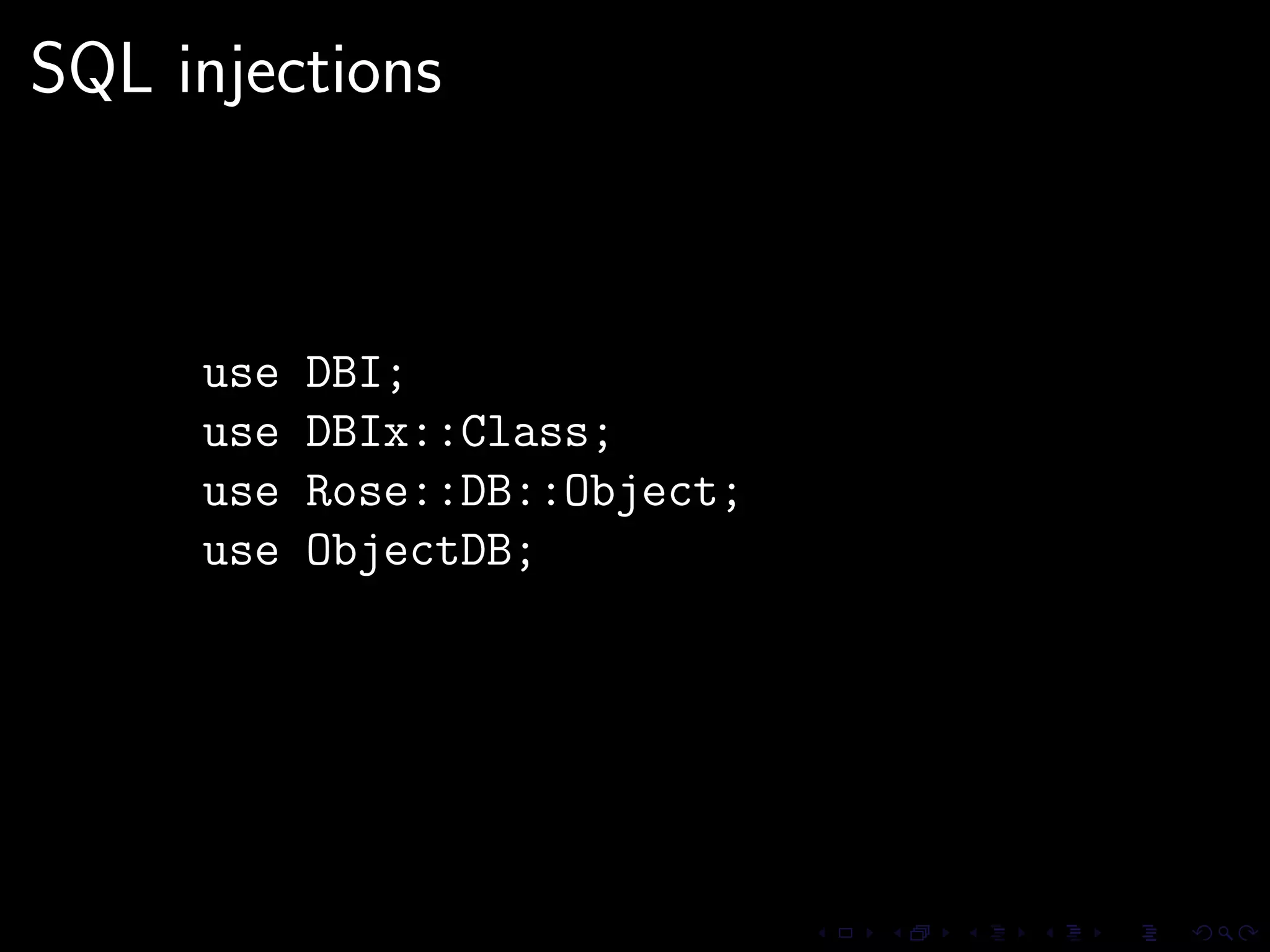
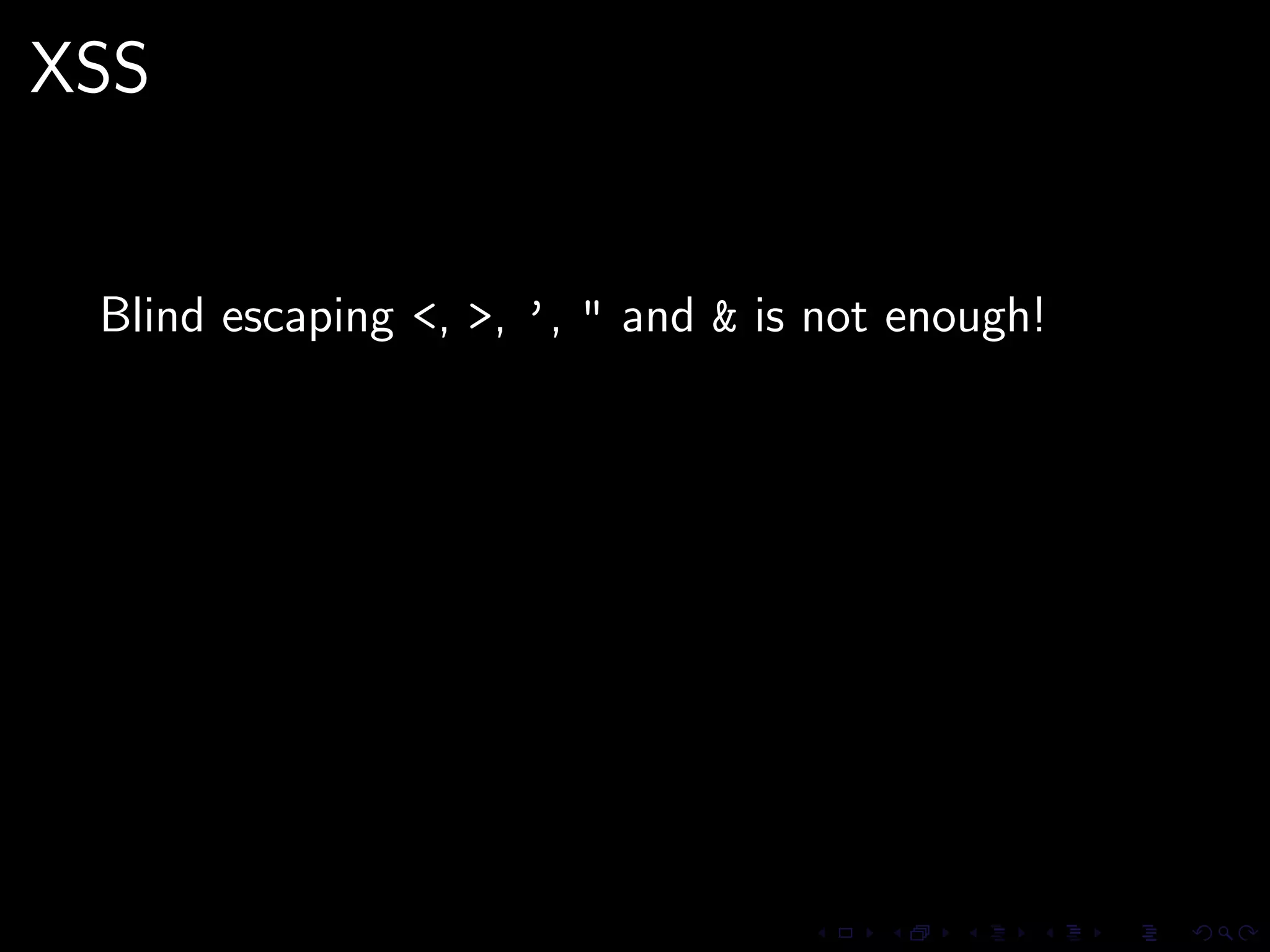
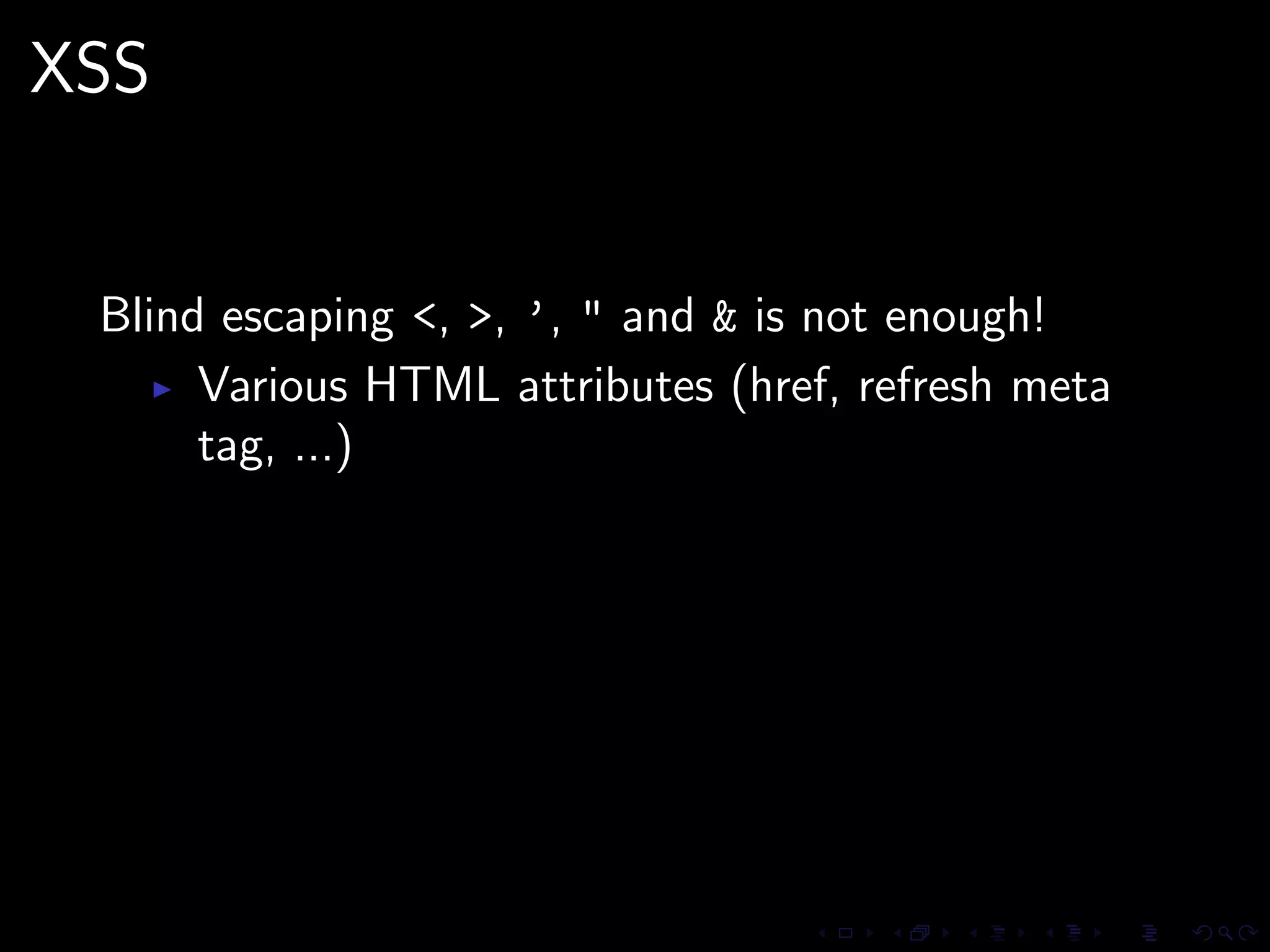
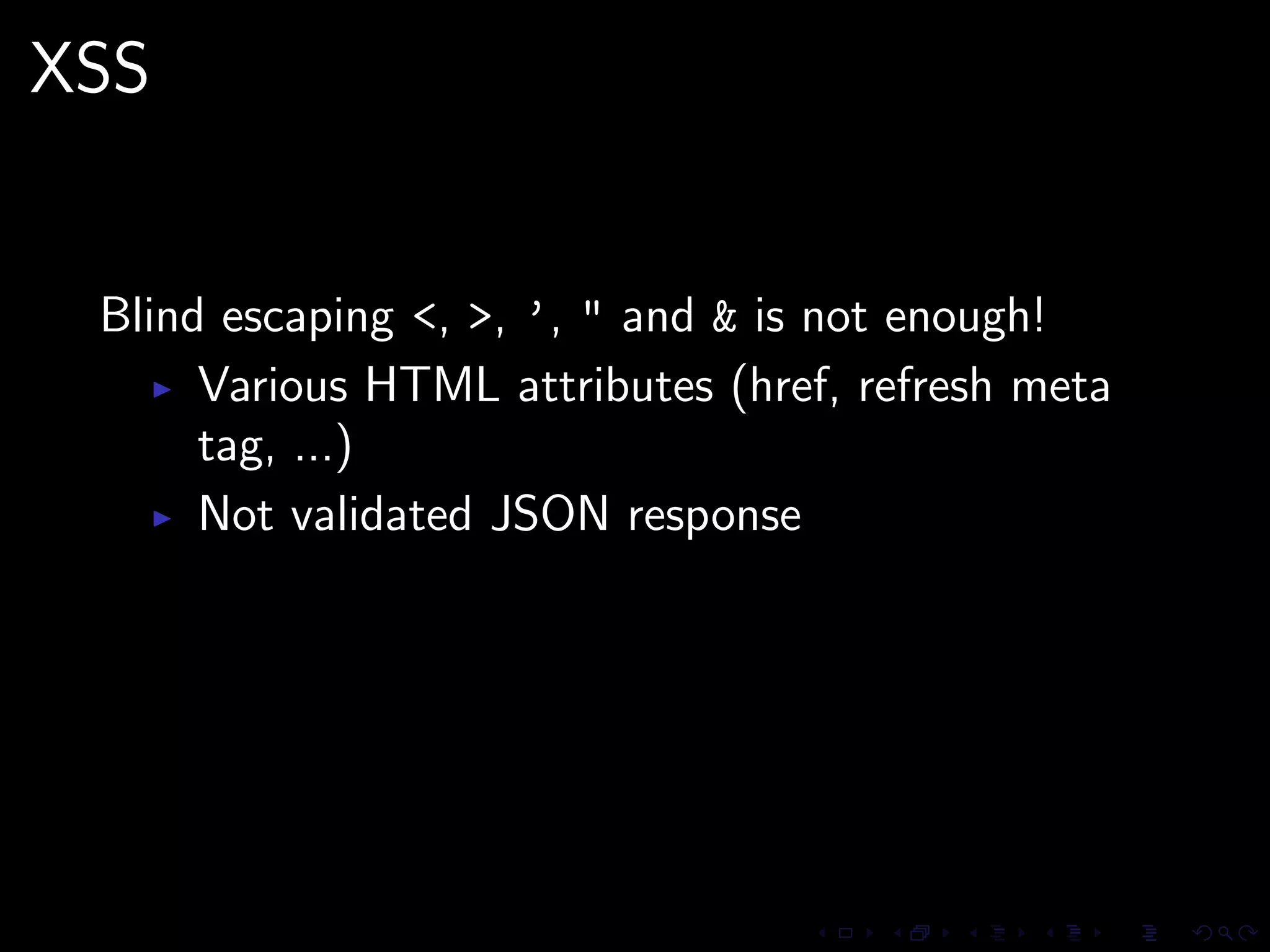
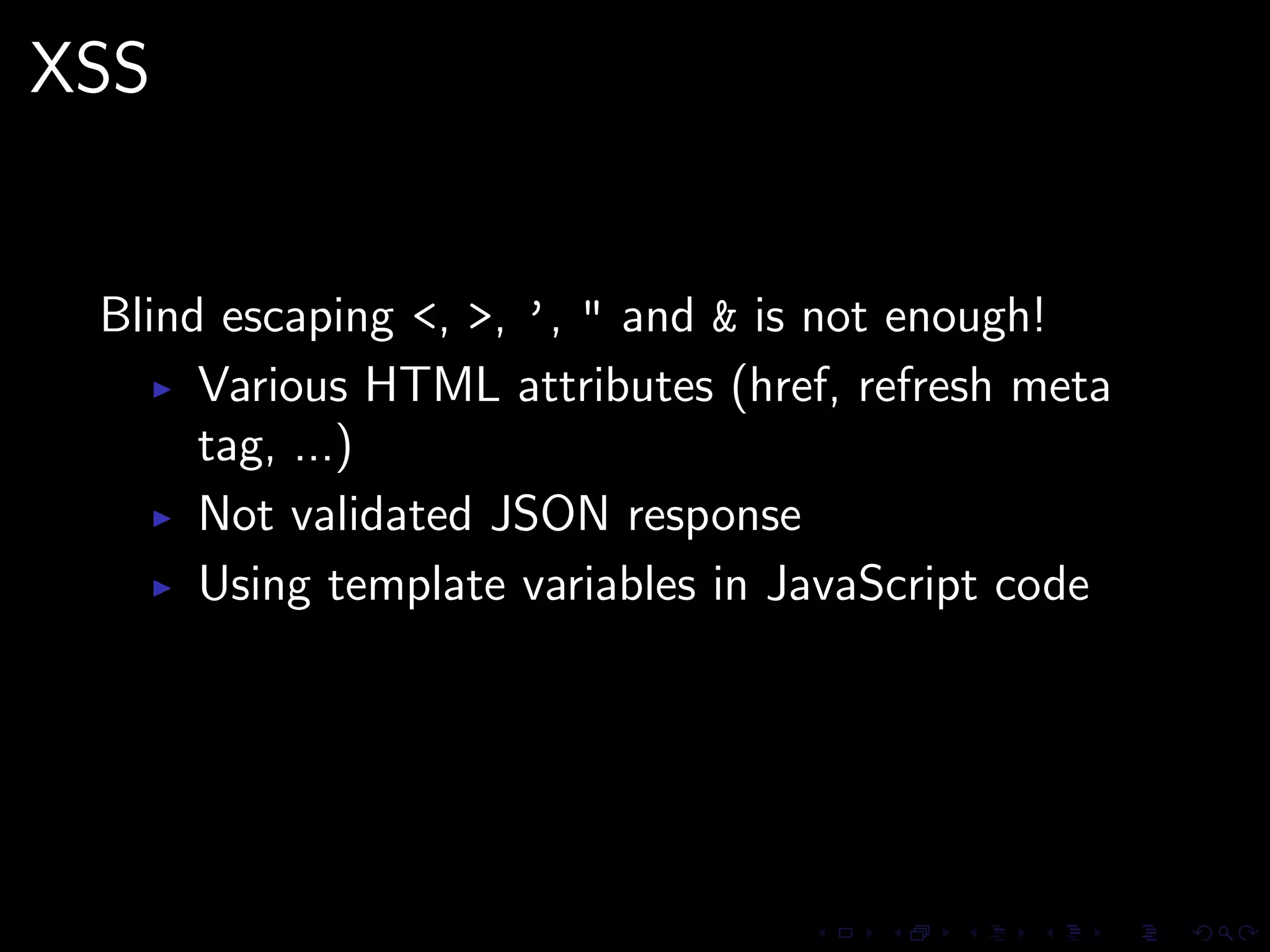
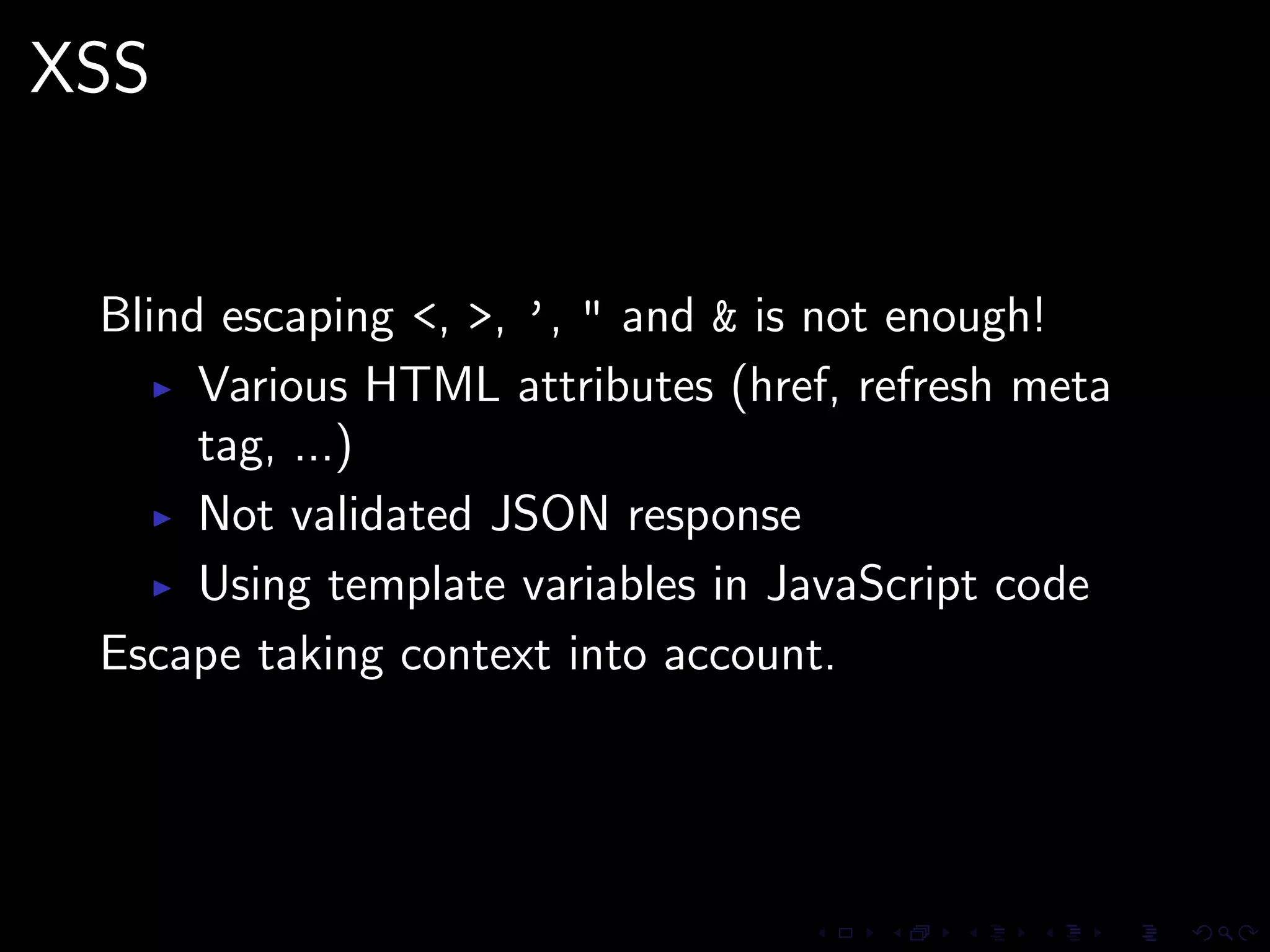
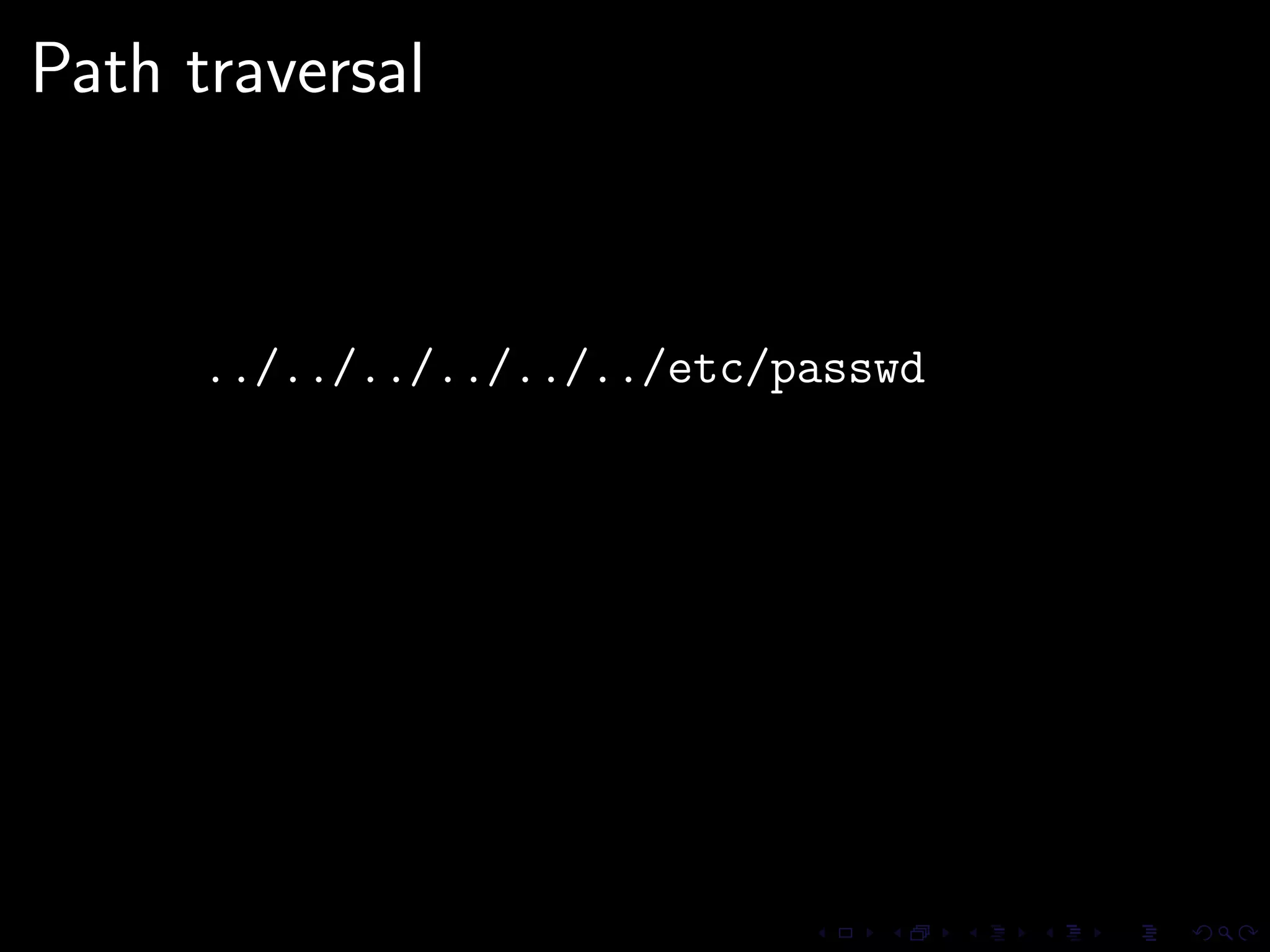
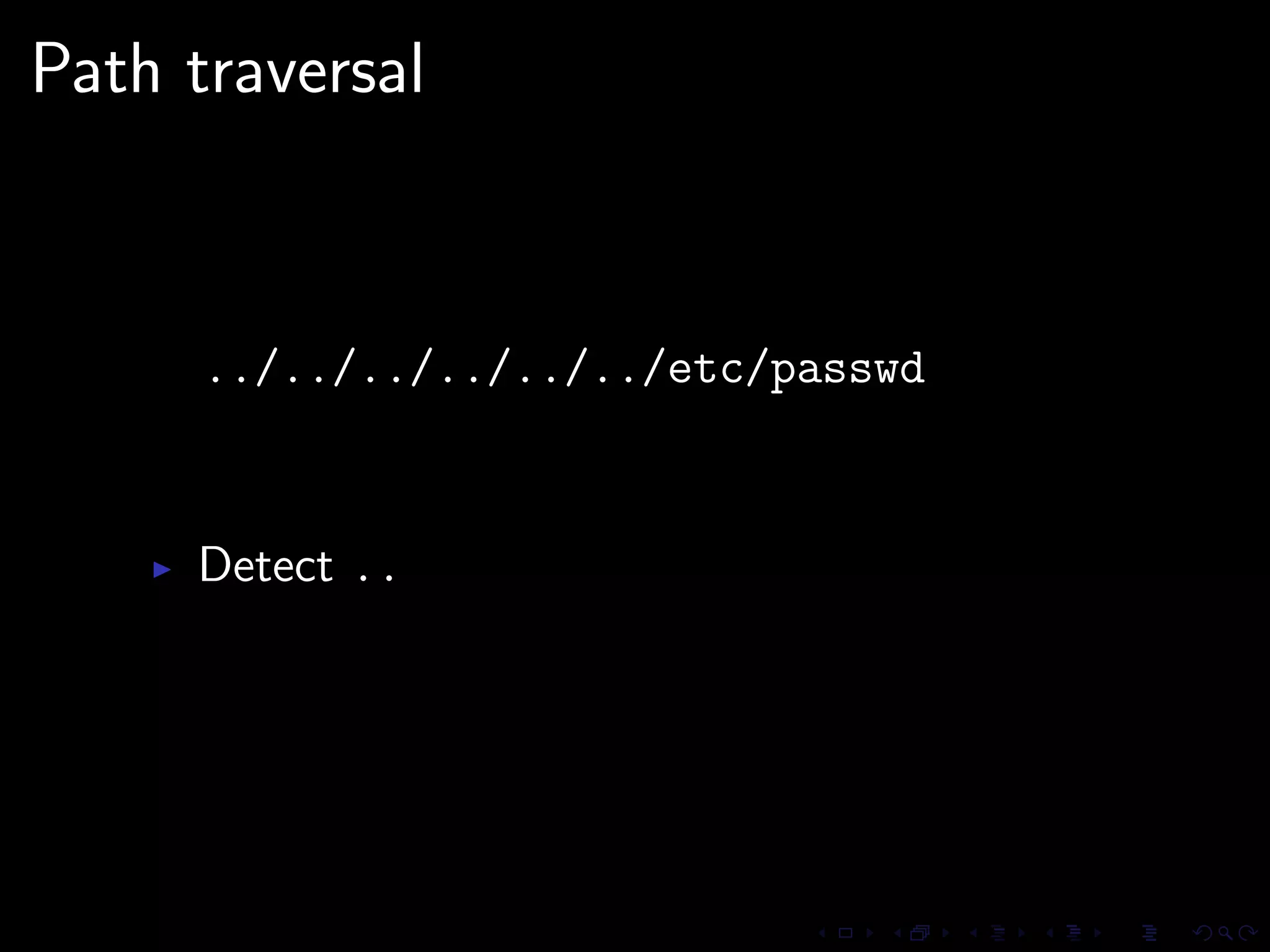
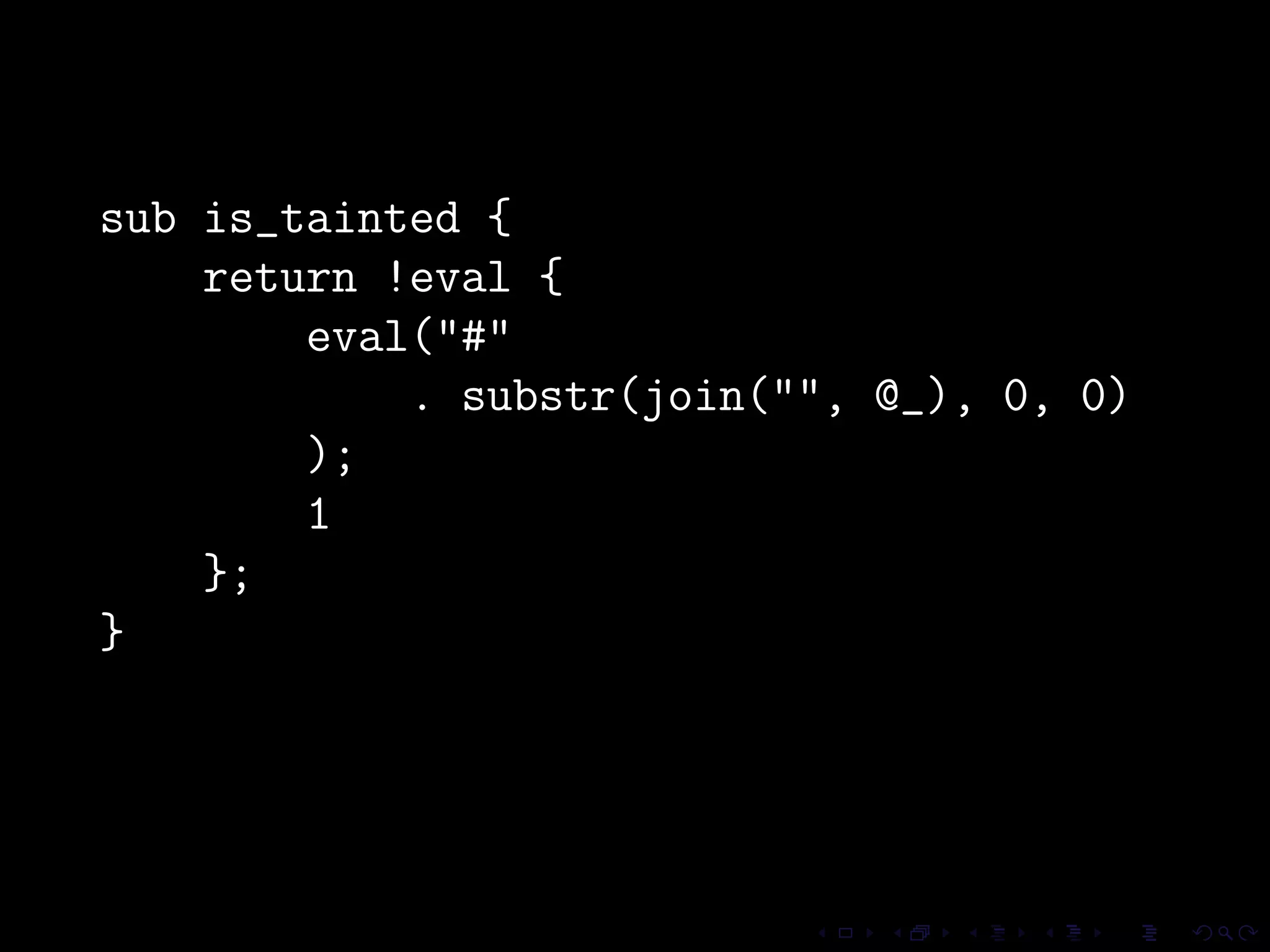
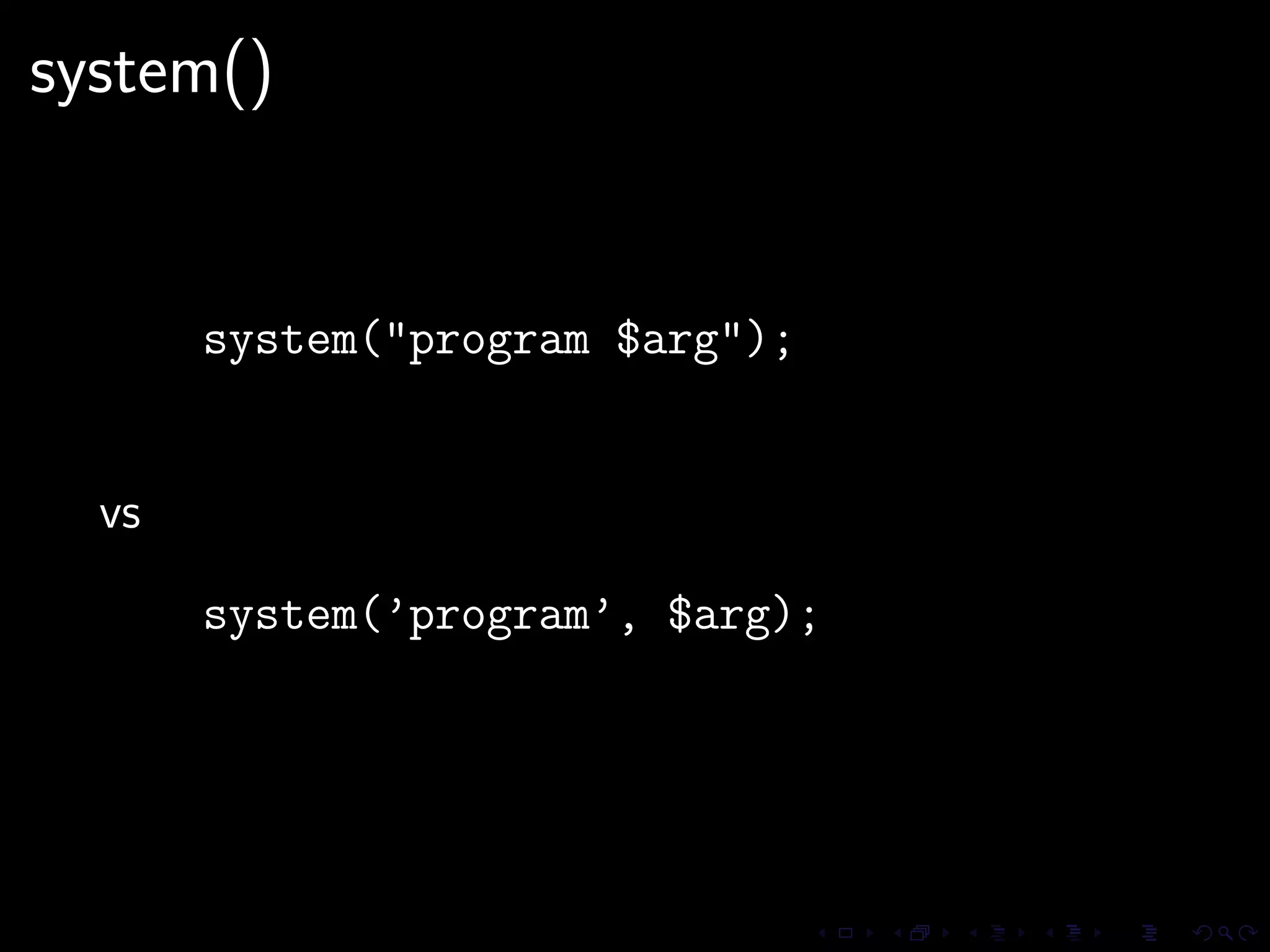
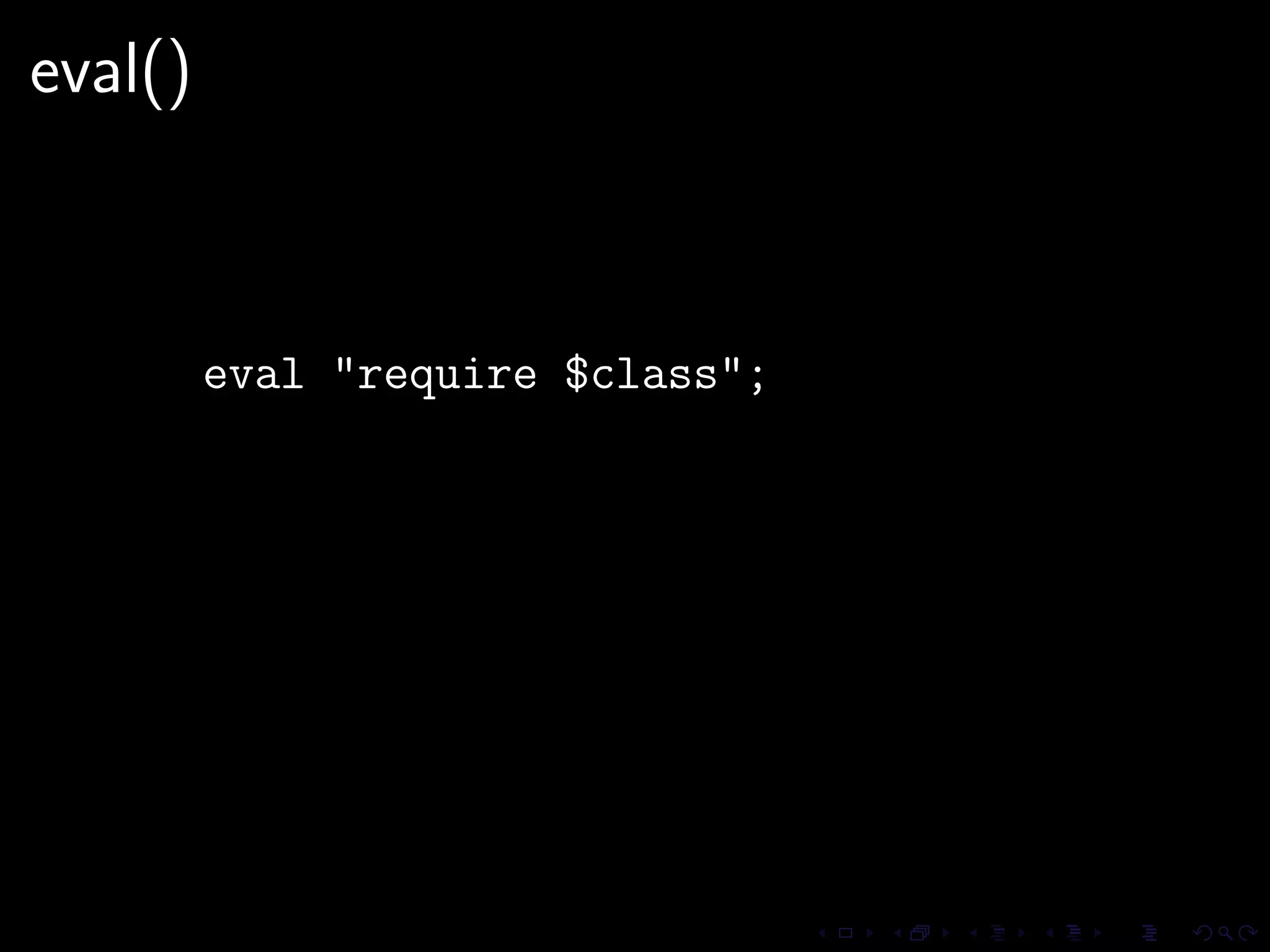
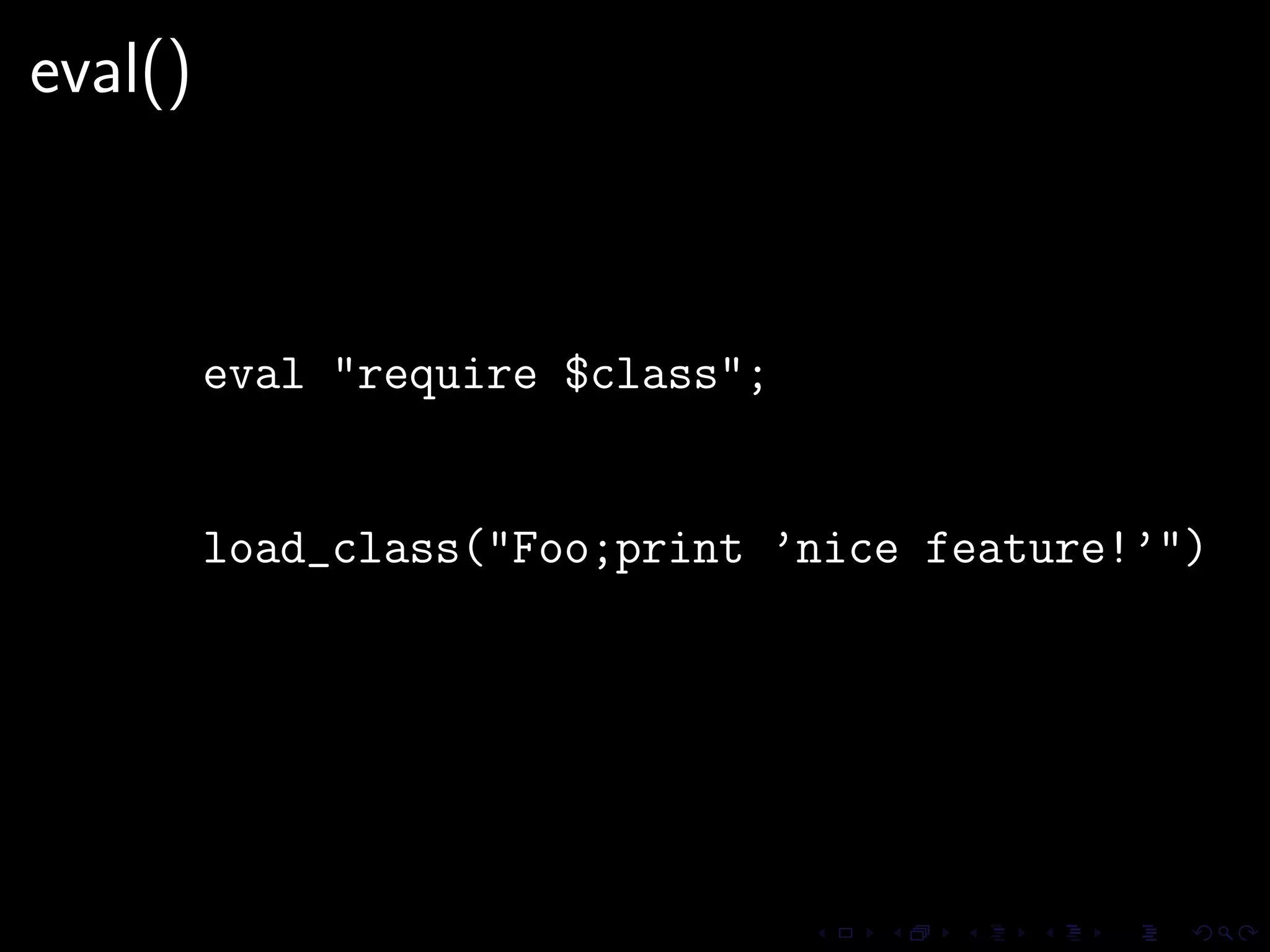
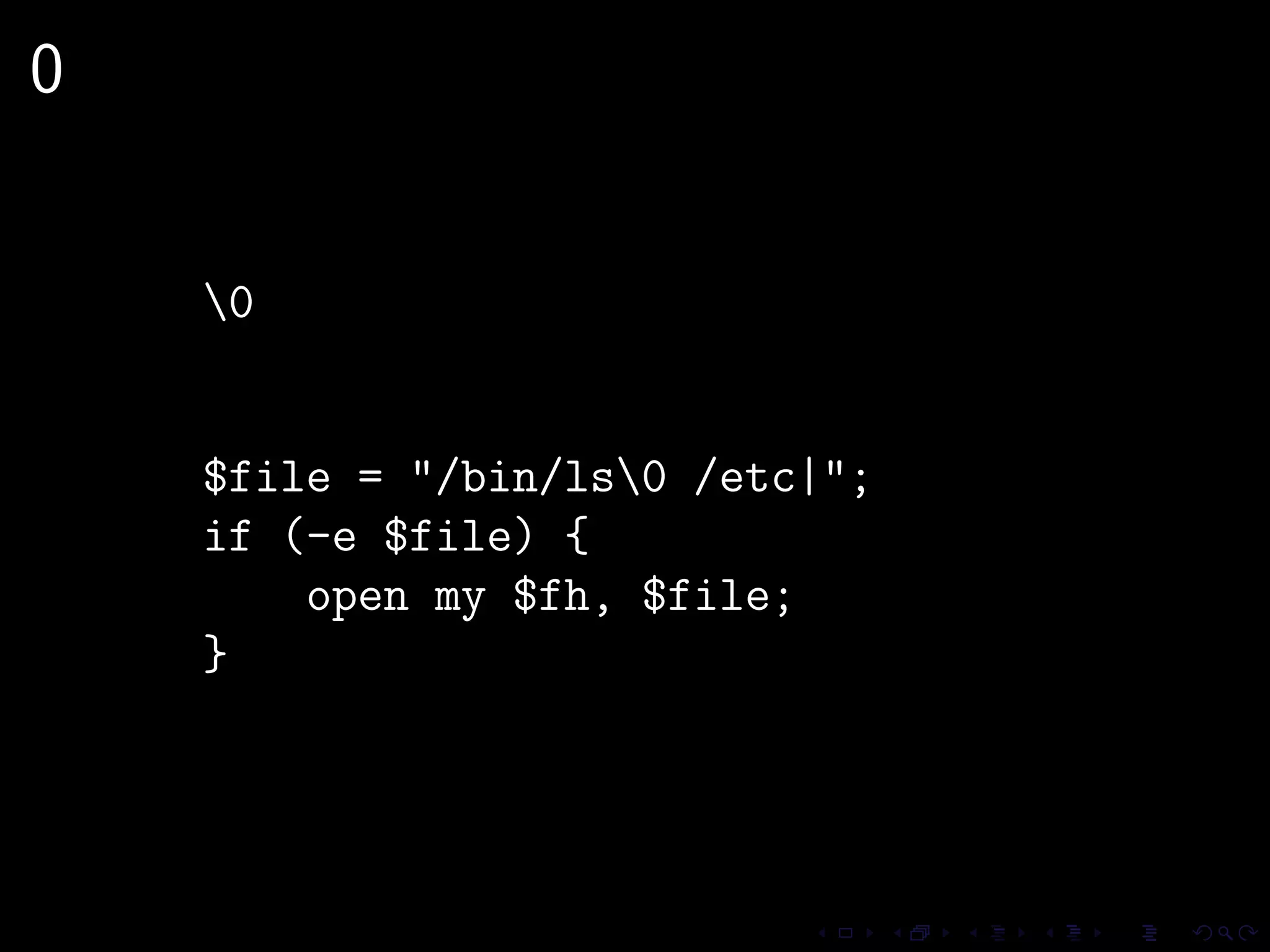
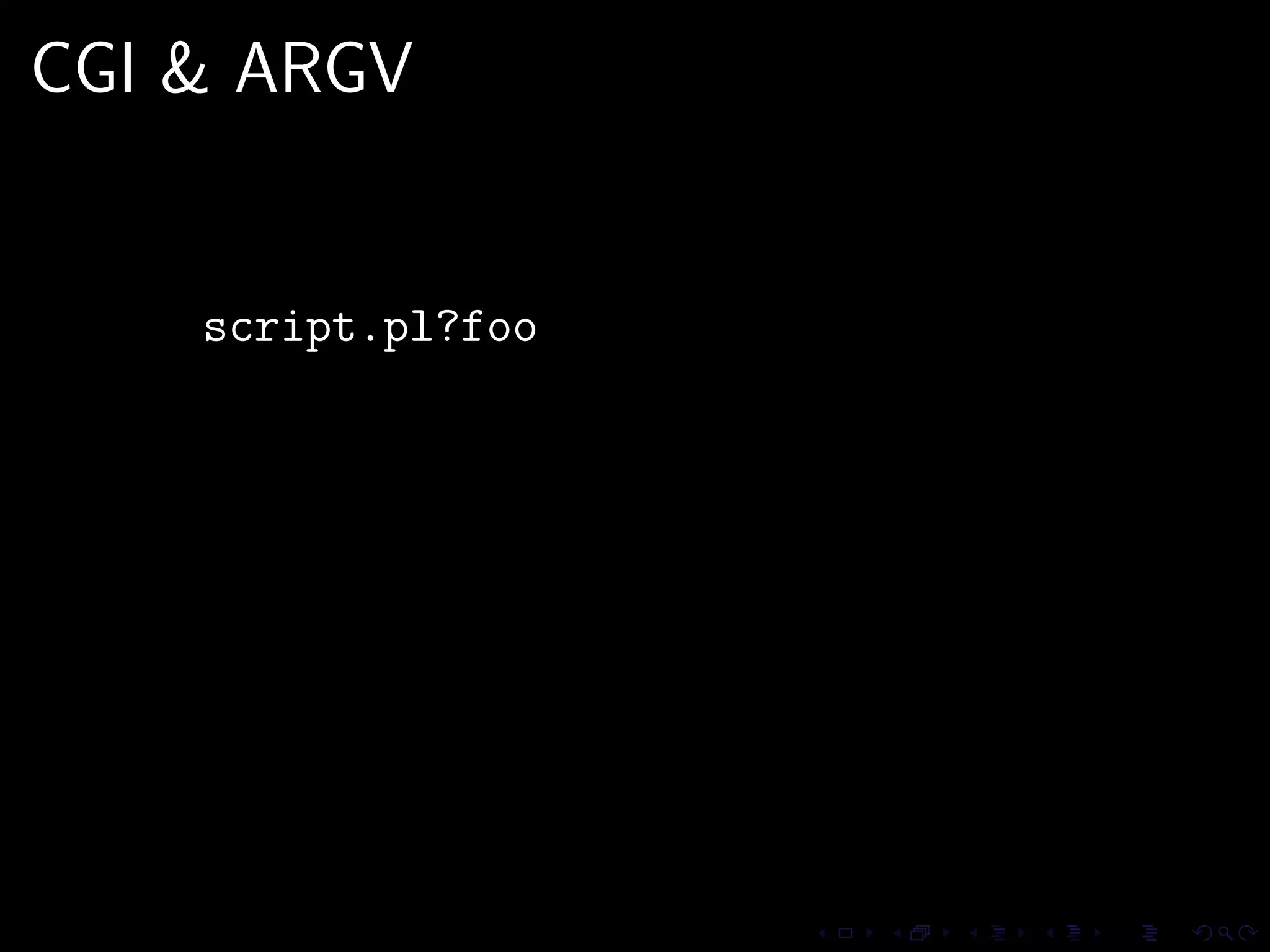
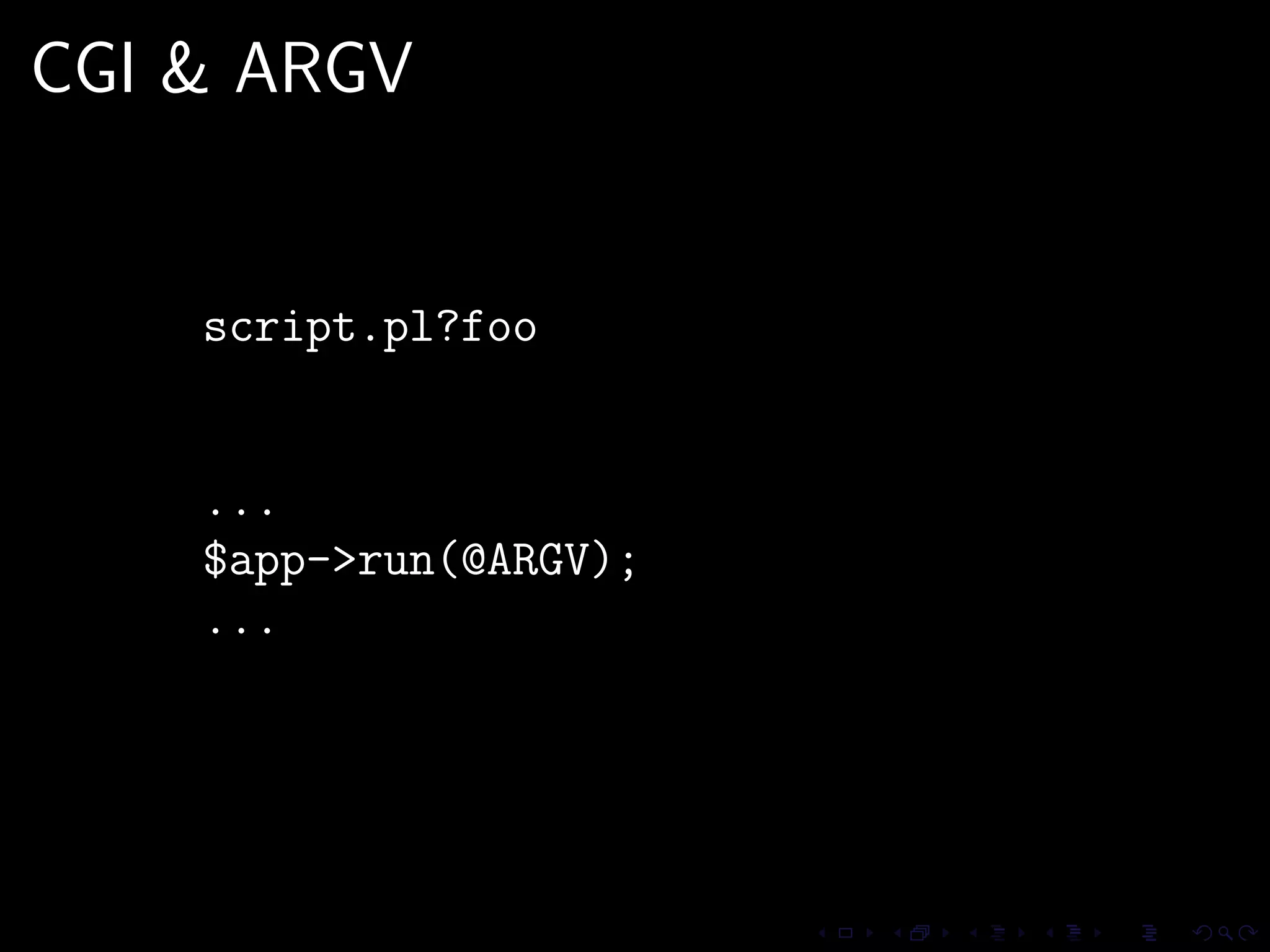
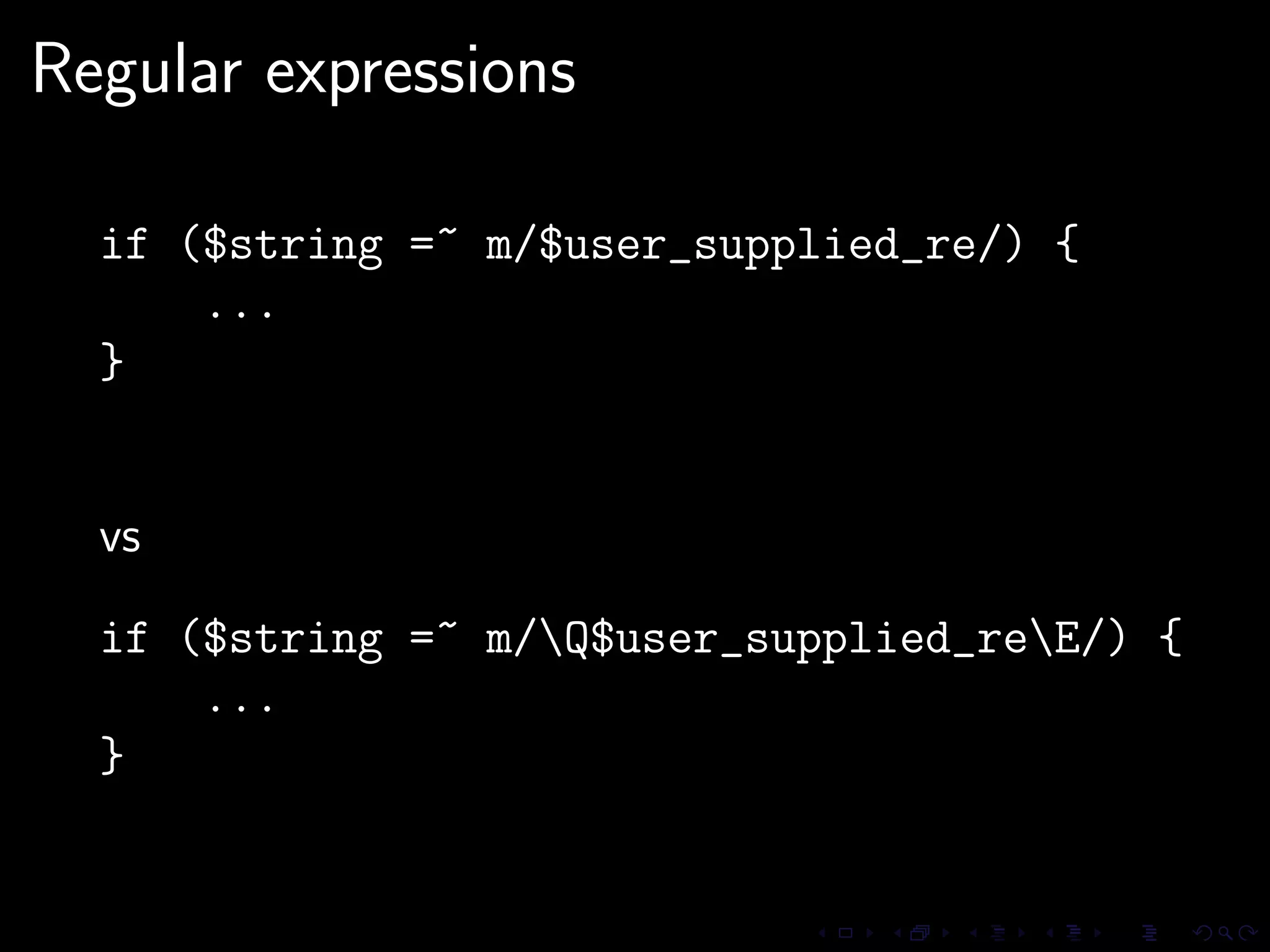
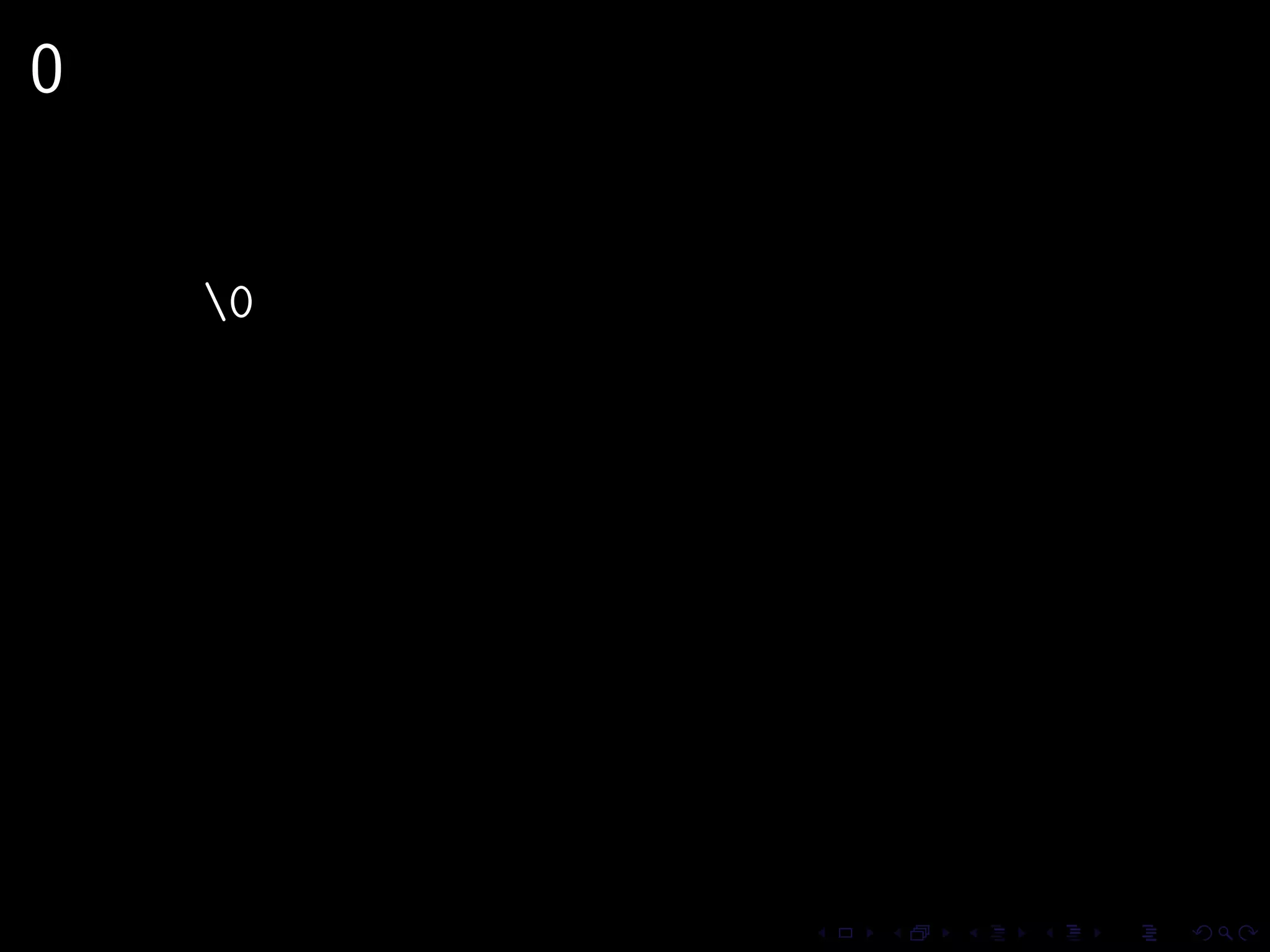This document discusses common security issues in Perl web applications and provides recommendations to address them. It covers input validation, SQL injections, cross-site scripting (XSS), cookies, CSRF, path traversal, Perl-specific issues like buffer overflows, tainting, system calls, eval, CGI parameters, regular expressions, and randomness. The document recommends using secure Perl modules from CPAN, following best practices, and using web scanners to test for vulnerabilities.