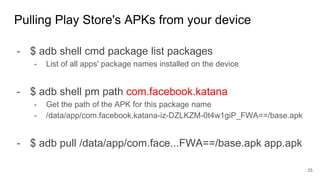
This document provides an overview of techniques for reverse engineering mobile applications and systems. It discusses both static and dynamic analysis approaches. For static analysis, it recommends analyzing the app's manifest, resources, classes, native code, and certificate information. Tools mentioned include APKtool, smali, dex2jar, jadx, and IDA Pro. For dynamic analysis, it suggests debugging and instrumentation to observe runtime behavior like network traffic. The document provides tips on finding apps to analyze and reversing non-trivial aspects like encrypted strings and dynamic code loading. The goal is to understand an app's functionality and identify security vulnerabilities by applying the right analysis approach for the task.


![- The goal: understand what X does and how it does it
- "X" could be an Android app, a MS Windows program, OS functionality,
a piece of hardware, a mechanical/physical engine, ...
- "[...] process by which a man-made object is deconstructed to reveal its
designs, architecture, or to extract knowledge from the object." (wiki)
- Why is it an "art"?
- There is no "recipe" that works in all cases
- Learn from experience which approaches work best
- I'll teach you the principles & starting points, I can't teach you everything
The "Art" of Reverse Engineering
3](https://image.slidesharecdn.com/mobisec2018-08-reverseengineering-230215084702-0685c7c7/85/MOBISEC-2018-08-Reverse-Engineering-pptx-3-320.jpg)