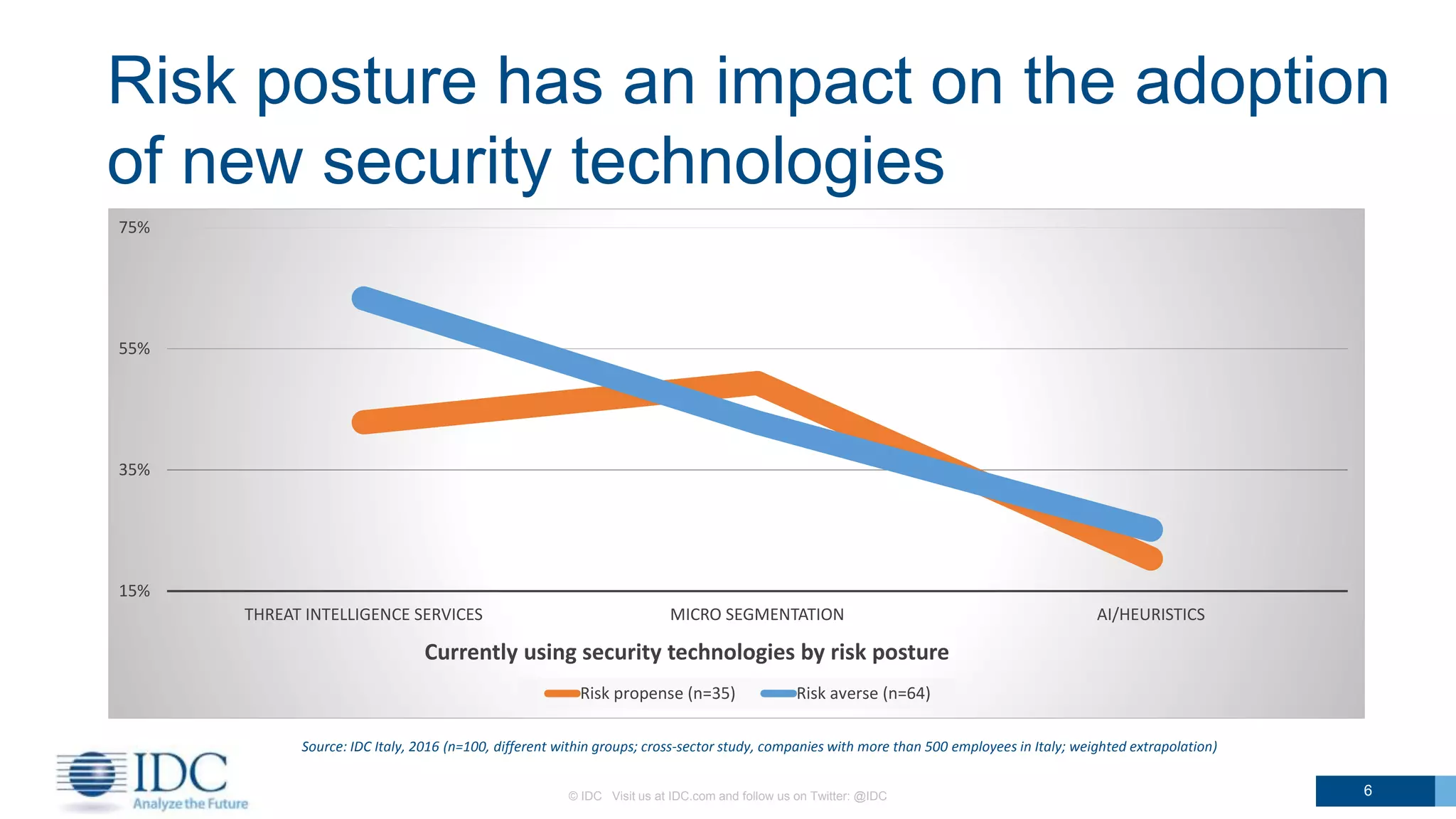
The document discusses the challenges and trends in IT risk management and cybersecurity for companies in Italy, emphasizing the increasing adoption of new security technologies amid pressure from digital transformation. It highlights that organizations face various obstacles, including budget constraints and skills shortages, which affect their ability to enhance security measures. Additionally, it forecasts significant shifts in security practices and the integration of advanced technologies, such as AI and biometrics, in response to evolving cyber threats.



![© IDC Visit us at IDC.com and follow us on Twitter: @IDC
5
TIME (MONTHS) TO MAINSTREAM
ORGANIZATIONALIMPACT
Asingle
department
orabusinessunit
Multiple
departments
orbusinessunitsCompanywide
0-12 12-24 24+
1
2
3
4
5
6
7
8
9
10
[CELLRANGE
]
[CELLRANG
E]
[CELLRANG
E]
[CELLRANGE]
[CELLRANGE]
[CELLRANGE
]
[CELLRANGE]
[CELLRAN
GE]
[CELLRA
NGE]
[CELLRANGE]
IDC FutureScape 2017
Security Products and Services, Western Europe Implications
1
2
3
4
5
6
7
8
9
10
By 2021, 50% of all online transactions will incorporate biometric
authentication driven by a ubiquitous technology infrastructure
that enables low implementation costs and broad user
acceptance.
By 2019, more than 75% of IoT device manufacturers will
improve their security and privacy capabilities, making them
more trustworthy partners for technology buyers.
By 2019, 60% of major multinational corporations with ties to
Europe will face significant cybersecurity attacks aimed at
disruption of commodities.
Over the next 18 months, 85% of consumers in Western
European nations will defect from a business because their
personally identifiable information is impacted in a security
breach.
By 2019, 70% of Western European enterprise cybersecurity
environments will incorporate cognitive/AI technologies to assist
humans in dealing with the vastly increasing scale and complexity of
cyberthreats.
By 2018, 50% of enterprise customers will leverage analytics as
a service to help solve the challenge of combing through
security-related data and events.
By 2020, cloud security gateway functionality will begin to be
integrated as part of web service offerings to entice IT leaders to
move offerings to the cloud.
By 2020, 25% of Western European broadband homes will have
at least one IP-enabled home automation or security monitoring
sensor/device.
By 2021, 60% of Western European enterprises will invest in
incident response retainers.
By 2020, more than 25% of Western European enterprises will
secure their IT architectures through cloud, hosted, or SaaS
security services.
Note: The size of the bubble indicates complexity/cost to address.
Source: IDC, 2016](https://image.slidesharecdn.com/security2017redux-170515074455/75/Sicurezza-IT-una-nuova-cultura-del-rischio-IT-per-promuovere-la-trasformazione-digitale-5-2048.jpg)