The document is a minor project report on securing Mobile Ad Hoc Networks (MANETs) against wormhole attacks using neighbor node analysis. It highlights the inherent vulnerabilities of MANETs due to their dynamic topology and lack of centralized administration, proposing a simulation-based solution to improve secure transmission. The study emphasizes the need to address various types of attacks, particularly highlighting the necessity for robust security mechanisms in the context of rapidly changing network conditions.


![Https://ThesisScientist.com
CHAPTER 1
INTRODUCTION
1 Introduction:
The higher demand of wireless communication and wireless devices have tends to research on
self-organizing, self-healing networks beyond the interference of some centralized or pre-
established infrastructure/authority. The networks not present of any centralized or pre-
established structure are known as Ad hoc networks. Ad hoc Networks are the class of wireless
networks that are uses multiple hop radio relay. Mobile Ad-hoc Network (MANET) is a
combination of wireless mobile nodes and connected other in dynamic way. Nodes make a
temporary/short-term network without any fixed infrastructure where nodes are fully free to
move arbitrarily.
FIGURE 1.1 Mobile Ad Hoc Network
The Nodes must behave like routers, take part in discovery and keep routes to other nodes in the
network [1] Wireless links in MANET are highly error level and can go down easily due to
mobility of nodes. Stable routing is a complicated task due to highly dynamic environment in
Mobile Ad-hoc Network [2]. So mobile ad-hoc network (MANET) is a self-organised network
of mobile routers (and associated hosts) associated by wireless links - the union of which form a](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-3-320.jpg)
![Https://ThesisScientist.com
random topology. The routers free to move randomly and organize themselves at random. a
network operates in a separate fashion, or may be link to the higher level of Internet. Minimal
configuration and fast deployment make ad hoc networks flexible for emergency situations like
natural or human prompted disaster areas, military conflicts, and emergency medical situations.
[3]
1.1 Research Motivation
With the speedy area of mobile devices and their extensive use in modem lifestyle, the paradigm
of networking has transfer from fixed networks to mobile wireless networking technologies with
limited or without infrastructure support. This paradigm transfer was designated in [8] [9], where
unworkable researchers describe the future integration of mobile networking technology with the
Internet. Mobile ad hoc networks have fast significance in current pervasive networking due to
their desirable characters such as fast deployment and without infrastructure.
• Lack of routers, nodes in the network have to participate and accept the routing and service of
data requirement.
• so the free architecture of the network where the nodes are independent join in and leave any
time, a rogue node can join the network to reason harm.
• Most widely used ad hoc routing protocols such as Ad hoc On-demand Distance Vector routing
(AODV) [to] and Dynamic Source Routing (DSR) [11] are created under the assumption that all
nodes trust each other and there are no malicious attacker nodes in the network. Therefore, the
presencey of any such nodes imposes the security challenges. Malicious nodes can creat
disturbance through a wide range of attacks including both routing and data forwarding attacks.
• Exacting resource constraints exist in MANETs; for example, most of the nodes in MANETs
rely on exhaustible battery resources and intruders can activity this to compromise routing and
data forwarding service in the network.
• Highly dynamic topology of the network due to nodes' mobility makes it difficult to detect the
attacking node. Therefore, the fundamental motivation of the research described in this thesis
appear from realizing the need to secure mobile ad hoc networks from a wide variety of attacks.
Attacks from intruder or malicious nodes cause various degree of damage to the network
depending on the type of attack used. We note that a considerable research effort has already](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-4-320.jpg)

![Https://ThesisScientist.com
1.3 MANETs Paradigm:
1.3.1 Background& Standards
In 1997 the IETF produce the Mobile Ad hoc Networking Working Group [14] and since then
considerable effort has been put in by the research community for similarity on this arrive
paradigm. The aim of this working group is to similarity the routing protocol by considering their
suitable functionality in MANETs environment. They established two standard track routing
protocol particular as reactive MANET protocols and proactive MANET protocols. One of the
main considerations for the similarity of routing protocols is their performance matter such as
loop freedom, demand based operations, distributed operation and proactive operations [15].
Take into consideration the configuration matter of MANETs, IETF recently figure another
working group called Ad Hoc Networks Auto configuration (auto conf) [16]. The main purpose
of this working group is to describe the matter in addressing model for ad hoc networks that is
how the nodes in ad hoc network constract their address both locally and globally when they
connect to other networks. The auto configure working group has addition in a form of internet
draft [17], where they propose and describe a model for constract IP addresses in ad hoc
networks. The research society perspective on this multi hop ad hoc networking technology has
chang as the technology has developed in the last two line. In [18] they define the term pure
MANETs referring to an ad hoc network with no infrastructure help as compared to one with
bounded infrastructure support.
1.3.2 Ad-Hoc Networks
Ad-Hoc networks have without arrangement where the nodes are free to add and left the
network. The nodes are attached with each other through a wireless link. A node can serve as a
router to send the data to the neighbors’ nodes. Therefore this type of network is also known as
infrastructure low networks. These networks have no centralized administration. Ad-Hoc
networks have the able to handle any malfunctioning in the nodes or many changes that its
experience due to topology changes. Whenever a node in the network is down or leave the
network that reason the link between other nodes is broken. The effected nodes in the network](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-6-320.jpg)

![Https://ThesisScientist.com
and interference, and has less bandwidth than a wired network. In some scenarios, the
path between any pair of users can Travers many wireless links and the link themselves
can be heterogeneous.
Light Weight Terminals: In many cases, the MANET nodes are mobile devices with low
CPU processing capability, small memory size, and lower power storage. Such devices
involve optimized algorithms and mechanisms that implement the joint up and
communicating functions.
Types of Mobile Ad-Hoc Network:
1. Vehicular Ad-Hoc Networks (VANET’s)
2. Intelligent Vehicular Ad-Hoc Networks ( InVANET’s)
3. Internet Based Mobile Ad-Hoc Networks (iMANET’s
1 Vehicular Ad-Hoc Networks (VANET’s):
VANET is a type of Mobile Ad-Hoc network where vehicles are assembled with wireless and
form a network no help of any infrastructure. The equipment is located private vehicles as well
as on the road for giving access to other vehicles in order to form a network and communicate.
2 Intelligent Vehicular Ad-Hoc Networks (In-VANET’s):
Vehicles that form Mobile Ad-Hoc Network for communication using WiMAX IEEE 802.16
and WiFi 802.11. The main focus of designing In-VANET’s is to ignoring vehicle collision so as
to keep passengers as safe as possible. This also helps drivers to keep secure gap between the
vehicles as well as assist them at how much speed other vehicles are coming. In-VANET’s
applications are also employed for military purposes to interact with each other.
3 Internet Based Mobile Ad-Hoc Networks (i-MANET’s):
These are used for connecting the mobile nodes and fixed internet gateways. In these networks
the simple routing algorithms does not apply [2].](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-9-320.jpg)
![Https://ThesisScientist.com
1.4 Applications of MANETs:
Ad hoc networks are fitted for use in situations where an infrastructure is unaccessible or to
deploy one is not total effective [39]. The following are selected of the important applications.
Business Applications: many possible uses of mobile Ad hoc networks is in any
business environments, where the need for Gray Hole computing might be most
important outside the office environment than inside, such as in a business meeting
outside the office to brief clients on a given work. Work has been going on to introduce
the fundamental aim of game theory and its applications in telecommunications. Game
theory originated from economics and has been applied in various fields. Game theory
contract with multi-person decision making, in which each decision maker tries to
maximize his speciality. The concert of the users is necessary to the operation of Ad hoc
networks; therefore, game theory give a good basis to analyse the networks. People
playing multi-player games usually do so over the Internet, uses a remote host. This
model is call the client-server model. In the class of multiple users, each user just
connected to a common server, and the server forwards the packets to connected users.
Military Applications: Military applications have motivated recent research on Ad hoc
networks. The capability to quickly set up a network among military units in hostile
territory without any infrastructure help can provide friendly forces with a considerable
tactical advantage on the battlefield. For instance, each soldier can transfer a mobile
device that represents one of the mobile nodes in an Ad hoc network connected all
soldiers, tanks, and other vehicles as shown in Fig 3.3. Recently advances in robotics
have also motivated the plan of automated battlefields in which unmanned fighting
vehicles are send into battle. Supporting military applications requires self-maintained
mechanisms that provide robust and reliable communication in dynamic battle condition.
Emergency Operations: other promising application field for Ad hoc networks is
emergency services, including search and rescue and disaster recovery operations. for
example of search and rescue, consider airline that attached to small wireless devices to](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-10-320.jpg)



![Https://ThesisScientist.com
Fig.1.2 MANETs Routing Protocols
A. Reactive Protocols:
Reactive protocols also called as on demand driven reactive protocols. The fact they are called
reactive protocols is, they don’t initiate route discovery by themselves, until they are requested,
when a source node request to search a route. These protocols setup routes when demanded [3,
4]. When a node needs to conversation with another node in the network, and the source node
does not have a route to the node it wants to contact with, reactive routing protocols will
establish a route for the source to destination node. usually reactive protocols
Don’t find route until demanded
When tries to find the destination “on demand”, it uses flowing technique to propagate
the query.
Do not consume bandwidth for sending information.
They consume bandwidth only, when the node start transmitting the data to the
destination node.
1. Ad-Hoc On Demand Distance Vector Protocol (AODV):
AODV is define in RFC 3561 [5]. It’s reactive protocol, when a node wishes to start transfer
with another node in the network to which it has no route; AODV will provide topology
information for the node. AODV uses control messages to search a route to the destination node
in the network. That are three types of control messages in AODV which are discussed .](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-14-320.jpg)

![Https://ThesisScientist.com
B. Dynamic Source Routing Protocol:
Dynamic source routing protocol compress as DSR is also a reactive protocol. DSR use to update
its route caches by finding fresh routes. It updates its cache with fresh route discovered or when
there exist a direct route between source and destination node. When a node needs to transmit
data, it design a route for the transmission and then starts transmitting data through the described
route. There are two processes for route discovery and maintenance which are defined below.
Route Discovery Process:
When a source node need to start data transmission with any node in the network, it checks its
routing cache. The cache route is not available to the destination in its cache or a route is
expired, it broadcast RREQ. When the destination is placed or any intermediate node that has
new enough route to the destination node, RREP is generated [15]. When the source node get the
RREP it updates its caches and the traffic is routed through the route.
Route Maintenance Process: the transferring of data started, it is the responsibility of the node
that is transfer data to confirm the next hop received the data along with source route. The node
creates a route wrong message, if it does not receive another confirmation to the originator node.
The originator node again performs fresh route discovery process.
1.6.2 Proactive Protocols:
Proactive routing protocols work as the another way around as compared to reactive routing
protocols. That protocols constantly maintain the updated topology of the network. Each node in
the network knows around the other node in advance, in other words the whole network is called
to all the nodes making that network. All the routing facts is usually keep in tables [6]. Whenever
there is a change in the network topology, that tables are updated accordance to the change. The
nodes exchange topology information with each other; they can have route information any time
when they require [6].
1. Optimized Link State Routing Protocol (OLSR):
The Optimized link State Routing (OLSR) protocol is defined in RFC3626 [7]. OLSR is
proactive routing protocol that is also known as table driven protocol by the information that it
updates its routing tables. OLSR has also three types of control messages which are defined.
Hello: This control message is transmitted for sensing the neighbor and for Multiple Point
Distribution Relays (MPR) calculation.](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-17-320.jpg)

![Https://ThesisScientist.com
to A. there is two way communications between both of the nodes we call the connection as
symmetric connection. HELLO message have all the information about the neighbors. MPR
node broadcast topology control (TC) message, without link status information at a
predetermined TC interval.s
Fig:1.6 Hello Message Exchange
1.7 Basic Security Concepts:
To understand security method it is vital to know the attribute or basic concepts on which a
network security is tested. These attribute related to security are the desired objectives of
Cryptographic mechanism. Cryptography can be defined in different ways, in [66] it is defined as
Cryptography terminologies, key concepts, types are summarized in [67].
1.7.1 Non-Repudiation
Non-repudiation ensures that an entity in a dispute cannot wrong deny its action or cancel the
validity of the contact. For example, during a transmission non replication service prevents the
sender from denying sending a message which he sent fastly, or a receiver cannot claim to have
received the message wrong.
1.7.2 Availability
Availability is another most important attribute, referring to ensuring that system resources and
services are reachable for use by authorized users of the system. It is imperative to make assure
all the network services remain available for its users given that an intruducer can attempt to](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-19-320.jpg)
![Https://ThesisScientist.com
harm services in the network through denial of service attacks, and that a network without
desired services is as poor as having no network.
1.8 Vulnerability of MANET Routing Protocols:
Vulnerability, threat, and attacks are the terms used often in computer network security.
We begin this subsection with defining these terms [66]:
1.8.1 Confidentiality
Confidentiality is also called as secrecy or privacy. Confidentiality is the process of concealing
information on the network, i.e. it ensures that news content cannot be revealed by not authorized
entities that are normally called as internal or external attacker or intruders. It can also be
described as a security service that ensures only intended receivers could interpretation the
information transmitted on the network. Confidentially is very important security service in
MANETs since wireless links in such networks are effortlessly susceptible to eavesdropping.
1.8.2 Integrity:
Integrity confirms that data packets are unaltered during transition from source to destination i.e.
unapproved user could not manipulate data through insertion, substitution, deletion or forging
data. To keep integrity, data is usually signed by the source and the receiver proves the digital
signature to be sure of integrity of the data. Such mechanism will incur extra overhead for nodes
in MANETs with controlled processing abilities and also because nodes relay data for other
nodes, so integrity cheeks wants to carried out at every hop. In [20] Gavidia et.al realize the cost
of guaranteeing data integrity mechanism for MANETs and proposed a answer based on
probabilistic integrity checks and traffic analysis. They prove that probablistic verification is an
effective technique to restrict the amount of corrupted content and their spread i.e. ensures data
reliability in MANETs.
1.8.3 Authentication:
Authentication is a process that allows node to confirm the identity of the other nodes with it is
communicating. Two types of verification are entity and data authentication [36]. Entity
verification ensures that other communicating parties are who they claim to be and data
authentication is concentrated on providing a guarantee as to the origin of the data.](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-20-320.jpg)
![Https://ThesisScientist.com
1.9 Flaws in MANETS:
MANETs are very adaptable for the nodes i.e. nodes can freely join and leave the network. There
is no main body that keeps watching on the nodes arriving and leaving the network. All these
weaknesses of MANETs make it susceptible to attacks and these are discussed bellow.
1.9.1 Non Secure Boundaries:
MANET is susceptible to different kind of attacks due to no clear secure boundary. The nature of
MANET, nodes have the self-determination to join and leave inside the network. Node can join a
network unconsciously if the network is in the radio range of the node, thus it can communicate
with other nodes in the network. Due to no secure limitations, MANET is more susceptible to
attacks. The attacks may be passive or active, leak of information, false message reply, denial of
service or changing the data integrity. The contacts are compromised and are open to various link
attacks. Attacks on the link interfere between the nodes and then invading the link, destroying
the link after performing misbehave. There is no guard against attacks like firewalls or access
control, which result the susceptibility of MANET to attacks. Spoofing of node’s characteristics,
data tempering, confidential information leakage and impersonating node are the results of such
attacks when security is cooperated [10].
1.9.2 Compromised Node:
Several of the attacks are to get access inside the network in order to get control over the node in
the network expending unfair means to carry out their malicious activities. Mobile nodes in
MANET are free to move, link or leave the network in other words the mobile nodes are self-
sufficient [11]. Due to this autonomous factor for mobile nodes it is complex for the nodes to
prevent mischievous activity it is communicating with. Ad-hoc network mobility makes it easier
for a compromised node to change its position so frequently making it extra difficult and
troublesome to track the malicious activity. It can be grasped that these threats from
compromised nodes inside the network is more complex than attacking threats from outside the
network.](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-21-320.jpg)
![Https://ThesisScientist.com
1.9.3 No Central Management:
MANET is a self-configurable network, which contains of Mobile nodes where the
communication among these mobile nodes is done lacking a central control. Each and every
node act as router and can forward and receive packets [12]. MANET works without any
preexistent infrastructure. This lack of centralized management tips MANET more weak to
attacks. Detecting attacks and monitoring the traffic in extremely dynamic and for large scale
Ad-Hoc network is very complex due to no central management. When there is a central entity
taking carefulness of the network by applying proper security, authentication which node can
joint and which can’t. The node connect which each other on the basis of blind mutual trust on
every other, a central entity can succeed this by applying a filter on the nodes to find out the
suspicious one, and let the other nodes know which node is doubtful.
1.9.4 Problem of Scalability:
In old-style networks, where the network is built and each machine is associated to the other
machine with help of wire. The network topology and the scale of the network, while designing
it is defined and it do not change much through its life. In other words we can say that the
scalability of the network is definite in the beginning phase of the designing of the network. The
case is fairly opposite in MANETs because the nodes are mobile and due to their mobility in
MANETs, the scale of the MANETs is varying. It is too hard to know and predict the numbers of
nodes in the MANETs in the future. The nodes are free to travel in and out of the Ad-Hoc
network which makes the Ad-Hoc network very much ascendable and shrinkable. Keeping this
property of the MANET, the protocols and all the services that a MANET affords must be
flexible to such changes.](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-22-320.jpg)
![Https://ThesisScientist.com
Chapter 2
LITERATURE REVIEW
2.1 Background
2.1.1 MANETs and Wormhole Attacks
A MANET is a network structure lacking a centralized infrastructure, making it vulnerable to
some types of attacks such as wormhole attacks. Wormhole attacks goal to attack a breakable
MANET by using two or more nasty nodes to fool a source node, which is trying to send the
data. Naturally, the malicious node uses a fake route which presents itself as the direct route to
the destination node [3]. Frequently, two nodes are involved: one is used to record the data and
the extra is used to forward the data back into the original network [4]. Contrary to mischievous
attacks, it was advised [8] that if a wormhole attack is not used for malicious means (for
instance, the case where it is produced by security personnel to test a network), the performance
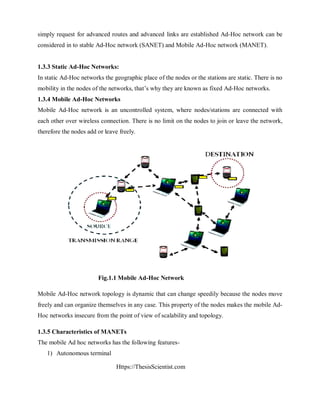
of the network can be enhanced. An example of a wormhole link is depicted in Figure. 2.1 [9]:
Figure 2.1: Wormhole Link](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-23-320.jpg)
![Https://ThesisScientist.com
In Figure. 2.1, nodes X and Y are colluding nodes which form a wormhole connection. These
two nodes are part of the MANET and have the skill to communicate with each other as well as
other normal, behaving nodes such as b or c. However, unlike behaving nodes, X and Y have a
advanced transmission power which gives them the skill to attract to themselves, allowing
malicious acts to take place.
2.1.2 AODV Protocol
AODV [10] is a routing protocol which has been planned to wait for requests before attempting
to catch the most optimal route for use by one node (source) to send messages to another node
(destination). The most best route is determined by the distance or the number of hops between
nodes. The AODV procedure works as follows:
1. A source node is mandatory to signify the need to send packets to a particular destination
node.
2. The source node broadcasts a route request packet (RREQ) to all neighbouring nodes.
3. The middle nodes continues broadcasting the RREQ to other neighbouring nodes until the
destination node is found.
4. When foundation, the destination node broadcasts a route reply packet (RREP) back to the
source node using different routes found by the RREQ broadcast.
5. When the source receives the RREP messages, it selects the route with the lowest hop count to
forward the data packets to the destination node.
2.1.3 Message Delivery Protocols
There are two types of message transfer protocols; namely, unicast and multicast. Unicast
message delivery [11] is a kind of message passing mechanism used in AODV. Unicast involves
two nodes of interest, one node in need to send a message and another node that will receive the
message. Thus, unicast is commonly famous as `one-to-one' message transmission. For example,
next a source node receives a RREP from a destination node, it can simply send the data packets
to the destination node and no other nodes. Also, once the destination node receives a RREQ, it
builds a RREP and unicast the packet to the source node by reviewing the hops of the RREQ.
Multicast message delivery [12] is another type of message delivery system. Unlike unicast,
multicast can include two or more nodes of interest. Therefore, multicast is generally known as](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-24-320.jpg)
![Https://ThesisScientist.com
`one-to-many' message transmission. For example, later a source node receives a RREP from
changed destination nodes of interest, it sends the data all together to all the targeted destination
nodes. In this thesis, firstly unicast transmission is used. Since MANETs are open wireless
networks which are vulnerable to attacks, we will want methods to protect messages and data
packets which are passed over the network. The Diffe-Hellman (DH) algorithm [13] is ideal for
use in AODV since it each permits two nodes in the same network that are not alert of any
predefined or called parameters of other to securely exchange secret keys in an unconfident
network environment. We will be consuming the Advanced Encryption Standard [14] in CBC
mode as the security protocol used to deliver additional security of these secret keys.
2.2 Literature Review on Wormhole Attacks
Some works address the problem of detecting, preventing or justifying wormhole attacks
in MANETs. The following review signifies a few of these solutions To detect malicious nodes
and avoid routing from these nodes strong secure routing has been proposed by K. Sivakumar
and Dr. G. Selvaraj [4]. In this technique called Robust Secure Routing (RSR), the idea of FR
packets was introduced which inform nodes along a route that they should expect specified data
flow within a assumed time frame. The path elements can therefore be on the lookout for the
assumed data flow, and in the event that they do not accept the traffic flow, they can transmit
info to the source informing it that the data flow they expected did not reach. A route tracing
algorithm for detection and prevention of wormhole attack has been planned by P. Anitha and M.
Sivaganesh [11]. The PT algorithm runs on every node in a path during the AODV route
discovery process. It calculates per hop distance built on the RTT value and wormhole link using
frequency appearance count. The matching node detects the wormhole if per hop distance
exceeds the all-out threshold range.
An work return based trust model to detect and evade wormhole attack is planned by Shalini Jain
and Dr.Satbir Jain in [12] where every one node executing the trust model, measures the
accuracy and honesty of the immediate neighboring nodes by monitoring their participation in
the packet sending mechanism. The transfer node verifies the different fields in the forwarded IP
packet for mandatory modifications through a sequence of integrity checks. If the integrity
instructions succeed, it confirms that the node has acted in a benevolent manner and so its](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-25-320.jpg)
![Https://ThesisScientist.com
nonstop trust counter is incremented. Similarly, if the integrity checks flop or the forwarding
node does not transmit the packet at all, its corresponding direct trust size is decremented. This
derived trust is then used to inspiration the routing decisions, which in turn leader a node to
avoid communication through the wormholes.
For detection and prevention of attack in MANET an well-organized multipath algorithm was
proposed by Waseem Ahad and Manju Sharma [10]. This algorithm will casually generate a
number in between 0 to maximum number of nodes and kind the node with same number as
transmitter node as wormhole attack is complete by transmitter and receiver so have to decide
the transmitter and receiver. Then create the route from selected transmitting node to any
destination node with specified average route distance. After this it will send packet giving to
selected destination and start timer to count hops and delay. By repeating the whole method up to
this point will be required as to store ways and their hops and delay. Now for detection of
malicious node, if the hop count for a particular direction decreases abruptly for average hop
count then at least one node in the route must be attacker. Algorithm will check the interruption
of all previous routes which involve any on node of the suspicious path. The node not encounter
previously should be malicious.
An end-to-end detection of wormhole attack (EDWA) in wireless ad hoc networks is planned by
Xia Wang and Johnny Wong [8]. Authors first presented the wormhole detection which is
created on the smallest hop count estimation in the middle of source and destination. If the hop
count of a received shortest route is much lesser than the estimated value an alert of wormhole
attack is higher at the source node. Then the source node will start a wormhole finding procedure
to identify the two end points of the wormhole. Lastly, a legitimate route is selected for data
communication.
In [15], Khalil et al. suggested a protocol (so-called LiteWorp) to discover and avoid wormhole
attacks in a static network. LiteWorp works by instructing each node involved to find 2-hop
routing information from their immediate neighbours. The suggested technique is an extension of
their original protocol in which each node only saves 1-hop routing information. According to
the authors, analyzing the routing info on routes which are 2-hops away will help wormhole
detection. In addition, nodes will also monitor their private neighbour nodes and possibly
become guard nodes for a pair of nodes which are all-out 2-hops apart. Guard nodes are designed](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-26-320.jpg)
![Https://ThesisScientist.com
to monitor neighbouring nodes activity to aid wormhole detection. However, the LiteWorp idea
was only designed for static networks and is impractical for a mobile network such as MANETs.
In [4], Hu et. al packet leashing introduces a way to prevent wormhole attacks. Their idea of
using packet leashes consists of information in a commuting packet that detects and prevents
abnormal transmission. In doing so, some timings are inserted in the packet
when it is forwarded by the sending node to a receiving node (not necessarily from source to
destination). Next, the receiver compares its own timings with the sender's timings resulting in a
calculated latency between the two nodes. The authors pointed out a limitation to this technique
since it is possible that two malicious nodes collude together to break their scheme while still
being within an acceptable distance. They state that a network which includes node positioning
analysis will overcome such vulnerability. Unfortunately, this solution suggests that only a
network with such topology will be able to prevent this detrimental attack.
In [16], a scheme called TrueLink was proposed to prevent wormhole attacks. True Link also
uses a timing based solution to the wormhole problem. Two nodes which are seemingly
neighbours exchange nonces or values which are used only once. This method is monitored
under strict timing restrictions (similar to those used in [4]) so that it is impossible for colluding
malicious nodes to replicate it since the packets routed through the wormhole will be more time
consuming than those forwarded normally. After the exchange of nonces, the two apparent
neighbours send messages to each other authenticating that the nonces were from the respective
nodes. If any intrusion is discovered, there will be a mismatch in messages and the system will
detect the malicious activity. This scheme suffers various limitations. First, unexpected delays
caused by legitimate events such as signal interference may increase the timings past accepted
ranges, thereby causing a drop of genuine packets. Second, it is assumed that an authenticating
mechanism (which may not exist) is already in place. Third, if the security mechanism is not
available, this method will be benign and ineffective to detect malicious attacks on the packets
being forwarded within the network.
In [5], Mamatha et al. proposed an AODV-based scheme for preventing wormhole attacks in
MANETs in which the hash identifier of the original packet is inserted in the data as it gets
forwarded from node to node. The procedure of their scheme is outlined as follows.
1. The system gets the hash (treated as a marker) and includes it in the data frame of the packet.](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-27-320.jpg)
![Https://ThesisScientist.com
2. The packet is then divided into sub-packets with a predetermined size and sent to the
destination node.
3. The intermediate nodes read the data frame to get the destination of the packets and then
continue forwarding to the next neighbouring node based on the AODV protocol.
4. Once the sub-packets are received by the destination, they are reconstructed to form the
original packet and the hash value is calculated.
5. The receiver will continue to extract the hash value stored in the data frame of the packet and
then checks if these values match. If that is the case, the receiver will reply with an
acknowledgement (ACK) frame containing an ACK field to confirm safe receipt of the packet.
However, if there is no match, the ACK frame will contain a Confidentiality Lost field which
will be forwarded to the sender informing it that the hash value was changed. If the
acknowledgement frame is not received by the sender within the allotted time, then the packets
are assumed to be lost. Few limitations of this method are as follows. This method does not
address other major effects of wormhole attacks. For instance, falsified nodes cannot be
prevented from recording the packet chunks. Indeed, packet chunks can be copied or recorded
without modifying the packet itself, thus the hash value will not change. Additionally, if packet
chunks are recorded, they can possibly be reconstructed by malicious nodes. Thus, it is possible
for a wormhole attack to record packets while remaining undetected.
In [17], Singh and Vaisla introduced an approach to detect wormhole attacks, where time is
considered as a key parameter. In their scheme, during the RREQ broadcast phase of route
discovery, each node will save a TREQ (time of request) which will record the time it takes for
the current node to forward a RREQ to its neighbour node. Once the RREQ reaches the
destination, a RREP is sent by the destination node to the sender and a TREP (time of reply) is
recorded at each node as the algorithm retraces its steps back to the sender. Finally, a RTT
(round trip time) of each successive intermediate node is calculated as the difference between the
TREP and the TREQ (RTT = TREP - TREQ). The RTT is calculated at each node to check if the
value is higher or lower than other RTT values calculated along the route. If no attack is
detected, the value of the RTT will be similar for all nodes. However, if the value of the RTT at a
certain node is higher than that of other successive nodes, then a wormhole attack may have
occured at that specific node. The method assumes that the RTT between two colluding attacking](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-28-320.jpg)
![Https://ThesisScientist.com
nodes will be significantly higher than two good nodes. However, calculating only the RTT may
not be sufficient to detect wormhole attacks.
In [9], a method is proposed that does not use timings or delays as a factor in detecting wormhole
attacks in wireless networks. Each node has a disk which its surrounding neighbors may
populate. The method exploits the long range wormholes by using unit disk graphs (UDGs) as an
unit radius disk in the network plane that models the range in which a node can communicate
using an omni-directional antenna. Since long-range links will be more than a unit radius, this
will indicate the presence of a wormhole link in the network. Although their proposed scheme
was shown to effectively detect wormholes in wireless networks, the case when nodes are mobile
was not treated.
In [18], Choi et al. proposed a method which is based on the DSR routing protocol to detect
wormholes in MANETs. Their method consists of a neighbor node monitoring
technique and a wormhole route detection method controlled by means of a timer (so-called
wormhole prevention timer). This scheme does not rely on any speci_c hardware for node
location or time synchronization. However, the assumptions that nodes will continue to monitor
active transmission at the link layer even though some of these nodes may not be intended
receivers is not realistic.
In [19], Hayajneh et al. proposed a technique called DeWorm which utilizes discrepancies in
routing between neighbours of nodes that are along a route of a selected path between the source
and destination nodes. DeWorm takes advantage of the fact that a wormhole link attempts to
attract a large amount of traffic to itself. Moreover, the routes through the wormhole link are
shorter than that of legitimate nodes within the network. Each node along the route, after being
selected during the route discovery phase, will initiate the DeWorm algorithm which relies on
the acquisition of different routes to a target node. This route discovery phase involves nodes
which are 1-hop neighbours of the current node performing the scheme. Additional information
has been added to each packet in order to carry necessary information used by the method.
Therefore, this method su_ers from a large overhead. Due to this large overhead, the
computation used to analyze the necessary information will increase, thereby increasing the
amount of energy consumed. Since the method is not energy efficient, this protocol is not quite
suitable for mobile networks for which the target is energy conservation.](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-29-320.jpg)
![Https://ThesisScientist.com
In an attempt to improve DeWorm, Dhurandher et al. [20] proposed a scheme (so-called E2SIW)
which is based on the AODV protocol. It is designed to be energy efficient and can mitigate
wormhole attacks in MANETs. Their method uses the location coordinates of nodes within the
MANET in order to detect the presence of wormholes. The authors discussed that wormhole
links will be low in hop counts. The hop count needs to be low in order to attract a large amount
of traffic to the wormhole nodes. By using GPS to examine the connectivity information for all
neighbouring nodes of a given node, the method is able to detect exactly how far the nodes are
from each other. Moreover, as the RREQ is being broadcasted, each hop is analyzed by their
respective nodes. Information about nodes which are two hops away are tested and temporary
routes are analyzed as well. Thus, this technique continually monitors the actual position of
nodes as well as the temporary routes during the route discovery phase. By detecting anomalies
within the network throughout and each hop of the discovery process, the method continuously
builds a route which avoids the wormhole link. However, the authors have not disclosed the
overhead for such a scheme since a lot of information is analyzed throughout each step of the
route discovery process.
2.3 Attacks:
There are two mainly protocols are used in MANET networks, Link layer protocol are used to
provide connectivity between different mobile nodes in order to ensure one-hop connectivity by
using multihop wireless channels. On the other hand if we like to extend connectivity to different
multiple hops then MANET network uses network layer protocols. In the coordination process
distributed protocols typically assume that all mobile nodes are cooperating with respect to
communication but actually this assumption is not possible in hostile mobile networks
environment because cooperation is not enforced in MANET. The question arises why? The
reason is because of malicious attackers violating protocol specification in order to disrupt
network operations.
2.3.1 Network Layer operation
There are two main network-layer operations in MANET.
1. Ad hoc routing
2. Data packet forwarding](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-30-320.jpg)
![Https://ThesisScientist.com
They interact with each other and delivering packets from source to destination. The main
function of the ad hoc routing protocols is to provide routing among nodes; they exchange
routing messages between different mobile nodes in order to maintain routing information at
each node. According to the routing states, the second network layer operation data packets are
used to forward data by intermediate next node which is an established route to the destination
node. These both operations are vulnerable to malicious attacks, and which will lead to various
types of malfunction in network layer.
2.3.2 Network Layer Attack
Due to this reason network-layer generally fall into two categories attacks:
1. Routing attacks
2. Packet forwarding attacks
There are different categories of routing attacks that does not follow routing protocol
specification. There are different routing protocols in MANET so therefore different attack
behaviors related to different routing protocols. Some of them are discuss below:
1. According to the context of DSR [1] MANET routing protocol there are following different
attacks which are given below [6]:
An attacker modifies source routing list with respect to RREQ or RREP packets.
Switching order of different nodes in the routing list.
Deleting entries from the list.
Appending new node entries into the list.
2. According to the context of AODV [2] MANET routing protocol there are also different
attacks which are given below [7]:
An attacker advertise route with wrong distance metric with respect to actual distance to
the destination.
Advertise wrong routing updates with a large sequence number with respect to actual
sequence number.
An attacker invalidates all routing updates from other nodes.
3. According to the context of TORA routing protocol, there are also different attacking
methods:](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-31-320.jpg)
![Https://ThesisScientist.com
Attackers construct routing paths by interfering with the protocols' mechanisms, e.g.
routes can be forced to use attacking nodes to go through them.
Attackers can also exhaust network resources by maliciously act of injecting, modifying
and dropping data packets.
In order to divert traffic attackers attack on the routing protocols and divert traffic towards
certain destinations under their control, and then they cause problematic situation in the network
along a route which is not optimal or even nonexistent. The attackers can also create routing
loops in the network, due to this way it creates network congestion in certain areas. There are
also some other attacks like multiple colluding attacks which may cause to prevent source in
order not to find route to the destination and also partition the network in the worst.
2.3.3 Active Attacks
There are also some different active attacks which are really difficult to locate or identify
because these attacks are more sophisticated and they are considered as subtle routing attacks
some of them are given below [8]:
Attacker may further subvert existing nodes in the network.
They can also fabricate their identity
They can also impersonate other legitimate node
Attackers in pair nodes may create a wormhole [9]
They also creates shortcut in normal flows between each other
The attackers target the route maintenance process and advertise operational link is
broken [6]
According to context of routing attacks there are also some other kind of attacks like attacker
launch attacks against packet forwarding operations as well due to this way it will not only
disrupt the routing protocol it also poison the routing states at every node. For example, the
attacker established route and drop packets, or also modify the content of the packets, or
duplicate the packets. Another type of packet forwarding attack is denial-of-service (DoS) attack
through network-layer packet blasting, in this type of attack attacker inserts large amount of junk
packets in network. Due to this action significant portion of the network resources are wasted,
and introduce severe wireless channel contention and network congestion in the network.](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-32-320.jpg)
![Https://ThesisScientist.com
There are identified vulnerabilities of the link-layer protocols, especially in the IEEE standard
802.11 MAC protocols [3], for mobile ad hoc network. It’s true that 802.11 WEP is vulnerable to
different types of cryptography attacks by misusing the cryptographic primitives [10]. The IEEE
802.11 protocol is vulnerable to many DoS attacks due to this way it targeting reservation
schemes and channel contention. The attacker exploits binary exponential back off scheme in
order to deny access to the wireless channel from its local neighbors [11, 17].
2.3.4 Routing Attacks:
Generally there are four different types of MANET routing protocol attacks which is divided in
to two main types which are given below:
1. Routing disruption attacks
2. Resource consumption attacks
Fig. 2.5 Classification of attacks on MANET routing protocols
In case of routing disruption attacks, the main task of attacker is to disrupt routing process by
routing packets in order to introduce wrong paths. In case of resource consumption attacks are](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-33-320.jpg)

![Https://ThesisScientist.com
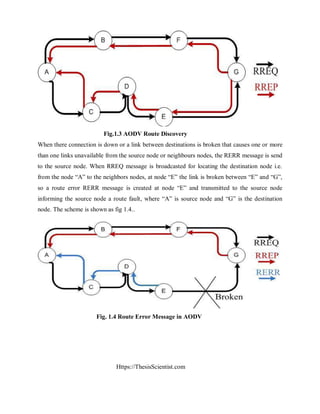
E. Attacks using Fabrication: In this type of attacks, where an attacker as a malicious
node try to inject wrong messages or fake routing packets in order to disrupt the routing process.
The fabrication attacks are very much difficult to detect in the mobile ad hoc network. Attacks
using fabrication process are discussed very well in [20] and [21]. In Figure 2.8 where
fabrication attacks is explained by an example. In the example where the source node S wants to
send data towards the destination node X, so therefore at start it sends broadcast message and
request for route towards the destination node X. An attacker as a malicious node M try to
pretends and modify route and returns route reply to the node (S). Furthermore, an attacker’s
nodes use to fabricate RERR requests and advertise a link break nodes in a mobile ad hoc
network by using AODV or DSR routing protocols.
Fig. 2.8 Fabrication attack example
2.8 Special Attacks
There are also some other severe attacks in MANET network which are possible against routing
protocols such as AODV and DSR.
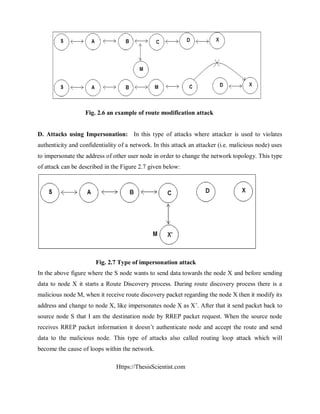
A. Wormhole Attack: The wormhole attack [15] is one of the severe types of attack in
which an attacker introduces two malicious nodes in the network where an attacker used
to forward packets through a private “tunnel”. This complete scenario described in Figure
2.9 which is given below:](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-36-320.jpg)
![Https://ThesisScientist.com
Fig. 2.9 Wormhole attack example
B. Black hole attack: This kind of attack is described very well in detail in [21]. In this
type of attack, node is used to advertise a zero metric to all destinations, which become
cause to all nodes around it in order to route data packets towards it. The AODV protocol
is vulnerable to such kind of attack because of having network centric property, where
each node of the network has to shares their routing tables among each other.
In the above example where there are two malicious nodes M1 and M2 which link through a
private connection. In this type of attack every packet which an attacker receive from network 1
forward to other network where another malicious node exist, simple speaking these two nodes
use to exchange network information and fabricate traffic among each other. The traffic between
the two nodes passes through “wormhole” among each other. Due to this way it will become the
cause of disrupts routing protocols and violating normal flow of routing packets. These types of
attacks are very difficult to detect in a network, and become the cause of severe damages to the
nodes. These types of attacks can be prevented by using mechanism packet leashes [15], which
are used to authenticate nodes among each other by timing information process.](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-37-320.jpg)
![Https://ThesisScientist.com
Chapter 3
Methodologies and Technical Background
In this chapter, we describe the methods that we proposed to address wormhole attacks in
MANETs as follows: (1) we analyze two different single wormhole scenarios and its effects on
MANETs by injecting two colluding malicious nodes which drop data packets; (2) we introduce
our E-HSAM method to enhance the HSAM scheme. The enhancements are twofold (a)
performing for the _rst time a simulation study of the HSAM protocol, (b) introducing a more
efficient approach to securing the routes in the route selection phase of the HSAM protocol; (3)
we design AODV-WADR-TDES as a complement to AODV-WADRAES in order to test the
performance difference when using two different cryptographic algorithms with the same
AODV-WADR scheme. This study is valuable because there exists modern day technology, such
as many smart cards, which do not necessarily support AES [21]; (4) we combine the techniques
and strengths of both E-HSAM and AODV-WADR-AES to design our novel scheme (so-called
TSMI). TSMI is able to ward of collaborative wormhole attacks effectively while maintaining
the performance of both E-HSAM and AODV-WADRAES.
3.1 Prevention against Single Wormhole Attacks
To begin our study of MANETs, we need to examine the effects of single wormhole attacks
before investigating collaborative attacks. We developed two simple scenarios where a MANET
is affected by a single wormhole attack. Both scenarios involve a wormhole which targets the
integrity of data packets.
3.1.1 Single Wormhole: Method 1
In this scenario, we simulate two different single wormhole attacks. In order to do this, we must
define the two colluding or malicious nodes. In this simulation, we use nodes 6 and 10 as the two
colluding nodes. The idea is to get these two nodes to have direct communication with each](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-38-320.jpg)
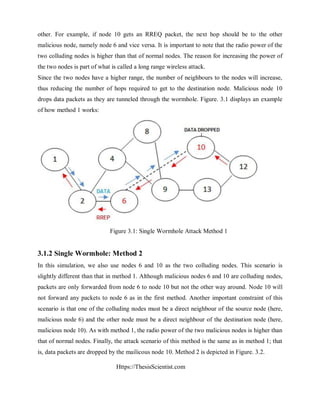
![Https://ThesisScientist.com
Figure 3.2: Single Wormhole Attack Method 2
3.2 Prevention Against Collaborative Wormhole Attacks
3.2.1 A Secured Routing Protocol for Preventing Packet Dropping and Message Tampering
Attacks In this section, we introduce an enhancement to an existing secured routing protocol [5]
against packet dropping and message tampering attacks in MANETs called the Highly Secured
Approach against Attacks in MANETs (HSAM). Our goal is to improve the data integrity part of
HSAM. The focus of the method is to create a dynamic methodology which tests a selected route
as data packets are being sent when using the AODV protocol within MANETs. Before a data
packet is about to be sent to the desired destination node, the algorithm splits the packet into
packet chunks and calculates a hash marker for each chunk. Once in chunks, each sub packet is
sent to the destination. If the hash value is incorrect, the route is blacklisted. The number of data
chunks sent as well as unsuccessful transmissions are recorded and a tolerance ratio is calculated.
After all the chunks are sent, the original data packet is reconstructed at the destination node.
Although HSAM deals with the integrity of the data packet, there are still attacks which make
this method vulnerable. For instance, he copying of packets is not addressed, i.e. malicious nodes
could potentially record all the data packet chunks and assemble them together to get the original
packet.
3.2.1.1 Highly Secured Approach Against Attacks in MANETs
As mentioned, the main focus of the Highly Secured Approach Against Attacks in MANETs
(HSAM) method is to create more security for data packets as they are being forwarded within a
MANET. Route discovery is obtained using the regular AODV methods (i.e. sending out RREQs](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-40-320.jpg)
![Https://ThesisScientist.com
and receiving RREPs). Once a route is ready, data packets are first divided into 48 byte data
frames. Information about the source node and destination node as well as a hash marker and
time of delivery is inserted into the data frame. The hash value will help maintain the data
integrity since a slight change in the data frame will result in a different hash value. After the
data frame is sent, a counter (cpkt) will be incremented to keep track of the number of chunks
sent. The authors referred to this technique as one way hash chain. They also argued that it will
be impossible for an attacker to break it. Next, intermediate nodes will forward the data frame
until it reaches the destination. Once the destination node receives the data frame, the hash will
once again be calculated and matched against the hash code obtained from the data frame. One
of the following two different acknowledgement frames or ACK frame will be created by the
destination node and sent back to the source node:
The hash code matches the code within data frame. An ACK frame containing an ACK field,
which indicates that the hash code is verified and secure, is sent back to the source node The
hash code does not match the code within the data frame. In this case, an ACK frame containing
a Confidentiality Lost field, which indicates that the hash code has been compromised, is sent
back to the source node. Once the ACK frame is received by the source node: If the integrity is
verified (i.e. ACK field is received), the receipt time is calculated and recorded. If the difierence
between the send and receipt time is equal or less than 20ms, then the route is deemed to be
secure and the next 48 byte data chunk will be sent. However, if the time is greater than 20ms,
the packet is assumed to have been lost and a counter (cmiss) will be incremented in order to
keep track of the number of conceivably missed packets.
_ If the hash code does not match with the one within the data frame (i.e. Confidentiality Lost
field received), the route is discarded, blacklisted and the next route is chosen using regular
AODV methods. Assuming that the packet integrity is validated and all the packet chunks have
been sent, a ratio called the Limit of Tolerance will be calculated. The Limit of Tolerance is
based on the Principle Flow of Conservation [22] in order to measure the forwarding
misbehavior of nodes. The ratio, cmiss/cpkt, that is, the number of missed packets over the
number of packet chunks sent, will be calculated and a limit of 0.2 or 20% will be set for its
value. If this ratio is equal or less than 0.2, the route will be deemed safe. Otherwise, the route
will be considered as insecure and the next available route will be used to send the next set of
packet chunks.](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-41-320.jpg)





![Https://ThesisScientist.com
31: S calculates the ratio cmiss/cpkt to obtain the Limit of Tolerance value
32: if ratio is less than or equal to 0.2 (20%) then
33: R is not discarded from the routing table and is deemed acceptable and secure
34: The real data packet and hash code (encrypted with AES) are sent to the destination node
using route R
35: else
36: S blacklists and discards R, broken links are incremented, S selects the next R from the
routing table and restarts mock packets process (i.e. repeat line 8)
37: end if
All single operations of the E-HSAM-AES algorithm are approximately O(1). The need to send
all the sub-packets to the destination node costs approximately O(n) where n is the number of
packets. Therefore, the complexity of this algorithm is approximately O(n) +O(1) or O(n).
3.2.2 Securing AODV Against Wormhole Attacks in Emergency
MANET Multimedia Communications
In this section, we examine the method of Securing AODV against Wormhole Attacks in
Emergency MANET Multimedia Communications (so-called AODV-WADR-AES) [6]. AODV-
WADR-AES is a scheme which uses the Advanced Encryption Standard (AES) as the
cryptographic algorithm as well as nodal timing analysis to aid in preventing wormhole attacks.
3.2.2.1 AODV-WADR-AES Scheme
In [6], Panaousis et al. introduced AODV-WADR-AES to overcome and mitigate wormhole
attacks in emergency MANETs (e-MANETs) multimedia communications. In their scheme, the
AES and Diffe-Hellman (DH) key exchange methods are used to deter attackers from retrieving
information from control packets while node to node timing analysis is performed. The reason
for using the DH key exchange is to help nodes authenticate each other in an insecure network
[13]. AODV-WADR-AES begins by obtaining routes using the normal AODV protocol. The
method then proceeds by extracting the hop count from the RREP during the route discovery. If
the route obtained is not 3-hops, then normal AODV routing protocol is initiated. Assuming that
a 3-hop route has been selected, the source node attempts to authenticate itself along with the
destination node using an AES encrypted DH key along with timing parameters on the messages
used during identity verification. If authenticated, the source begins transferring the data packets](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-47-320.jpg)
![Https://ThesisScientist.com
to the destination. However, there are some drawbacks associated with this method: (1) the data
packets are not protected during their transmission using AODV-WADR-AES. For example, if a
node
is hijacked by a malicious user, it is possible for the user to tamper with data packets; (2)
AODV-WADR-AES is restricted to analyzing 3-hop routes only. Even though the authors
claimed that this requirement is sufficient, it is possible that wormhole links exist in routes that
have less or more than 3-hops. For instance, if a MANET is initiated and a wormhole link exists
on a route which has more than 3-hops, the algorithm will not be used to analyze this route since
the 3-hop requirement will be violated. Therefore, it is possible for malicious nodes to perform
some of their deeds before being detected by the algorithm.
The following are some de_nitions used within the the algorithm.
Net Traversal Time (NetTT) in milliseconds (ms): this defines the maximum time allotted
for receiving a RREP from the destination node after the source has broadcasted a RREQ
Node Traversal Time (NodeTT) in milliseconds (ms): this defines the maximum time
allotted for packets to travel between each hop
Actual Traversal Time (ATT) in milliseconds (ms): this defines the actual calculated time
for receiving a RREP from the destination node after the source has broadcasted a RREQ
Actual Traversal Time WADR (ATT WADR) in milliseconds (ms): this defines the
actual calculated time for receiving a modified AODV WADR packet from the
destination after the source has sent an original AODV WADR packet
Maximum Traversal Time (MTT) in milliseconds (ms): this is defined by 6 x NodeTT
since only destinations that are 3 hops away are considered by this method The main
focus of the AODV-WADR-AES approach is to maintain the security of the data packets
as they are being forwarded within an AODV-based MANET. One main requirement of
this approach is that the destination node should be 3-hops away from the source node.
The authors [6] argued that this restriction is sufficient to prevent wormhole attacks for
two reasons:
1. If a source node (S) detects and prevents a wormhole, any routes passing through S will be
diverted away from the wormhole.](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-48-320.jpg)
![Https://ThesisScientist.com
2. It will be difficult for S, which is more than 3-hops away from the destination, to know which
node in the route is malicious since S will only keep the information about the next hop node
(which is one main features of AODV) AODV-WADR-AES begins with small additions to the
normal operations of the AODV protocol as follows. A source node that is in need of a route to
send its packets to a
destination node will broadcast a RREQ and will record the time which the request was made.
When the source node receives a RREP, it will record the receipt time of the RREP packet. The
two recorded times are used to calculate the actual traversal time (ATT) which will be used
compared against the net traversal time (NetTT) to determine whether the algorithm will be
launched or not. Indeed, if ATT is greater than NetTT, AODV-WADRAES will be ignored and
the normal AODV operations will commence. If ATT is less than NetTT and the hop count is not
3, AODV will operate normally. If ATT is less than NetTT and the hop count is 3, AODV-
WADR-AES will be launched. The next step is to check if the ATT is greater than the maximum
traversal time (MTT). If ATT is less than MTT, the source node will consider that the route is
safe and the normal AODV operations will continue. If ATT is greater than MTT, there is a
greater chance that a wormhole may exist in the network (since the network will experience an
increase in latency between nodes).
Once a wormhole is suspected, a shared secret key is created between the source and destination
nodes. The DH method is used to determine this key. The DH algorithm is ideal for use in
AODV since it allows two nodes which are not aware of any predefined or known parameters of
each other to securely exchange secret keys in an insecure network environment [13].
The source node will _rst send a message to the destination node, stating that DH key exchange
is needed and records the send time. Once a reply is received from the destination node, the
source node will record the receipt time and compare it to the send time. If ATT of the message
is greater than NetTT, a wormhole attack is suspected and the source will delete the route from
its routing table. Additionally, the source will update its blacklist with the next hop node. If ATT
of the message is less than NetTT, the DH key exchange will commence.
Once the DH key is created, the source node will then send an encrypted message to the
destination node and record the time. The destination node will decrypt message, add its unique
ID number associated with itself to it, re-encrypt message and send it back to the source node.
The source node will then record the time of receipt and calculate the actual traversal time of](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-49-320.jpg)

![Https://ThesisScientist.com
21: A wormhole is suspected, S deletes R from its routing table and updates its blacklist with the
next hop node of the suspect route
22: end if
23: else
24: A wormhole is suspected, S deletes R from its routing table and updates its blacklist
(blacklist wa) with the next hop node of the suspect route
25: end if
26: else
27: Route is considered safe and normal AODV operations commence
28: end if
29: end if
30: Normal AODV operations commence
31: else
32: Normal AODV operations commence
33: end if
30
All single operations are approximately O(1). The need to forwarding messages and packets to
the destination node costs approximately O(n) where n is the total number of control packets as
well as AODV-WADR-AES messages. Therefore, the complexity of this algorithm can be
measured to approximately O(n) + O(1) or O(n).
3.2.2.2 AODV-WADR-TDES Scheme
AES encryption is widely accepted as the next generation encryption technique [23]. However,
technologies such as smart cards, which can be considered as eMANET nodes, are incompatible
with AES implementations [21]. In light of this incompatibility, a different encryption technique
called the Triple Data Encryption Standard (TDES) is recommended by [24, 25]. As a
complement to the AODV-WADR-AES scheme, we introduce AODVWADR- TDES. The
methods found in AODV-WADR-TDES are similar to AODV-WADRAES. However, the
cryptographic algorithm of choice is TDES. By implementing longer variable key sizes to DES,
three different possible key combinations, the pseudo-randomness of the algorithm increases,
Thereby increasing its security potential. The AODV-WADR-TDES protocol follows similar
steps as the AODV-WADR-AES protocol. However, some differences occur in the manner the](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-51-320.jpg)




![Https://ThesisScientist.com
REFERENCES
[1] Achint Gupta, Priyanka V J, Saurabh Upadhyay, “Analysis of wormhole Attack in AODV
based MANET Using Opnet Simulator”, International Journal of Computing, Communications
and Networking Vol. 1, October 2012.
[2] Jatin D. Parmar, Ashish D. Patel, Rutvij H. Jhaveri1, Bhavin I. Shah, “ MANET Routing
Protocols and Wormhole Attack against AODV”, IJCSNS International Journal of Computer
Science and Network Security, Vol. 10, No.4, April 2010.
[3] Reshmi Maulik, Nabendu Chaki, “A Study on Wormhole Attacks in MANET”, International
Journal of Computer Information Systems and Industrial Management Applications ISSN 2150-
7988 Vol. 3, pp. 271-279, 2011.
[4] K. Sivakumar, Dr. G. Selvaraj, “Analysis of Worm Hole Attack In MANET And Avoidance
Using Robust Secure Routing Method”, International Journal of Advanced Research in
Computer Science and Software Engineering Vol. 3, No. 1, January 2013.
[5] Yashpalsinh Gohil, Sumegha Sakhreliya, Sumitra Menaria, “ A Review on Detection and
Prevention of Wormhole Attcaks in MANET”, International Journal of Scientific and Research
Publications, Vol. 3, No. 2, February 2013.
[6] Abari Bhattacharya, Himadri Nath Saha, “ A Study of Secure Routing in MANET various
attacks and their countermeasures”, IEMCON organized in collaboration with IEEE in January
2011.
[7] Susheel Kumar, Vishal Pahal, Sachin Garg, “ Wormhole Attack in Mobile Ad Hoc Networks:
A Review”, IRACST, Vol. 2, April 2012.
[8] Xia Wang, Johnny Wong, “An End-to-end Detection of Wormhole Attack in Wireless Ad
hoc Networks”,](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-56-320.jpg)
![Https://ThesisScientist.com
31st Annual International Computer Software and Applications Conference IEEE, 2007.
[9] Pallavi Sharma, Prof. Aditya Trivedi, “An Approach to Defend Against Wormhole Attack in
Ad Hoc Network Using Digital Signature”, IEEE, 2011.
[10] Waseem Ahad, Manju Sharma, “Efficient Multipath Algorithm in MANETs to Prevent
Wormhole Attack”, CT International Journal of Information &Communication Technology Vol.
1, No. 1, 2013.
[11] P. Anitha, M. Sivaganesh, “Detection And Prevention Of Wormhole Attacks In Manets
Using Path Tracing”, International Journal of Communications Networking System, Vol. 01, No.
02, December 2012.
[12] Shalini Jain, Dr.Satbir Jain, “ Detection and prevention of wormhole attack in mobile adhoc
networks” , International Journal of Computer Theory and Engineering, Vol. 2, No. 1 February,
2010.
[13] I. Woungang, S. Dhurandher, and V. Koo, Comparison of two security protocols for
preventing packet dropping and message tampering attacks on aodv-based mobile ad hoc
networks," in submission to the IEEE 4th International Workshop on Mobility Management in
the Networks of the Future World (MobiWorld 2012), Anaheim, California, USA. December 3-
7, 2012.
[14] Y. Wang and M. Hu, Timing evaluation of the known cryptographic algorithms," in
International Conference on Computational Intelligence and Security (CIS 2009), Beijing, China,
vol. 2, pp. 233 {237, December 11-14, 2009.
[15] I. Khalil, S. Bagchi, and N. Shroff, Liteworp: a lightweight countermeasure for the
wormhole attack in multihop wireless networks," in International Conference on Dependable
Systems and Networks (DSN 2005), West Lafayette, Indiana, USA, pp. 612 { 621, June 28 - July
1, 2005.
[16] J. Eriksson, S. V. Krishnamurthy, and M. Faloutsos, Truelink: A practical countermeasure
to the wormhole attack in wireless networks," in International Conference on Network Protocols
(ICNP 2008), Orlando, Florida, USA, pp. 75{84, October 19-22, 2006.](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-57-320.jpg)
![Https://ThesisScientist.com
[17] A. Singh and K. Vaisla, A mechanism for detecting wormhole attacks on wireless ad hoc
network," International Journal of Computer Science and Network Security, vol. 2, pp. 27{31,
September 2010.
[18] S. Choi, D. young Kim, D.-H. Lee, and J.-I. Jung, Wap: Wormhole attack prevention
algorithm in mobile ad hoc networks," in Proceedings of IEEE International Conference on
Sensor Networks, Ubiquitous and Trustworthy Computing (SUTC 2008), Taichung, Taiwan, pp.
343 {348, June 11-13, 2008.
[19] T. Hayajneh, P. Krishnamurthy, and D. Tipper, Deworm: A simple protocol to detect
wormhole attacks in wireless ad hoc networks," in Proceedings of the 3rd International
Conference on Network and System Security (NSS 2009), Gold Coast, Queensland, Australia,
pp. 73{80, October 19-21, 2009.
[20] S. K. Dhurandher, I. Woungang, A. Gupta, and B. K. Bhargava, E2siw: An energy efficient
scheme immune to wormhole attacks in wireless ad hoc networks," in International Conference
on Advanced Information Networking and Applications Workshops, Fukuoka, Japan, pp.
472{477, March 26-29, 2012. 62
[21] H. O. Alanazi, B. B. Zaidan, A. A. Zaidan, H. A. Jalab, M. Shabbir, and Y. Al-Nabhani,
New comparative study between des, 3des and aes within nine factors," Computer Research
Repository, vol. abs/1003.4085, 2010.
[22] O. Gonzalez, M. Howarth, and G. Pavlou, Detection of packet forwarding misbehavior in
mobile ad-hoc networks," in Proceedings of the 5th international conference on Wired/Wireless
Internet Communications (WWIC 2007), Coimbra, Portugal, pp. 302{ 314, May 23-25, 2007.
[23] B. Preneel, Aes and nessie: Cryptographic algorithms for the 21st century," Eurocacs 2002
Keynote. Budapest, Hungary. March 24-28, 2002
[24] U. N. I. of Standards and T. S. P. (SP), Recommendation for the triple data algorithm,"
Tech. Rep. FIPS SP 800-67, US Department of Commerce / National Bureau of Standards,
Spring_eld, Virginia. May 2004.
[25] S. Lucks and R. Weis, How to make des-based smartcards for the 21-st century:
Cryptographic techniques for advanced security requirements," in Proceedings of the 4th
working conference on smart card research and advanced applications on Smart card research
and advanced applications, Bristol, United Kingdom, pp. 93{114, September 20-22, 2000.](https://image.slidesharecdn.com/securingmanetagainstwormholeattackusingneighbornodeanalysis-170506105006/85/wormhole-attacks-in-wireless-networks-58-320.jpg)
