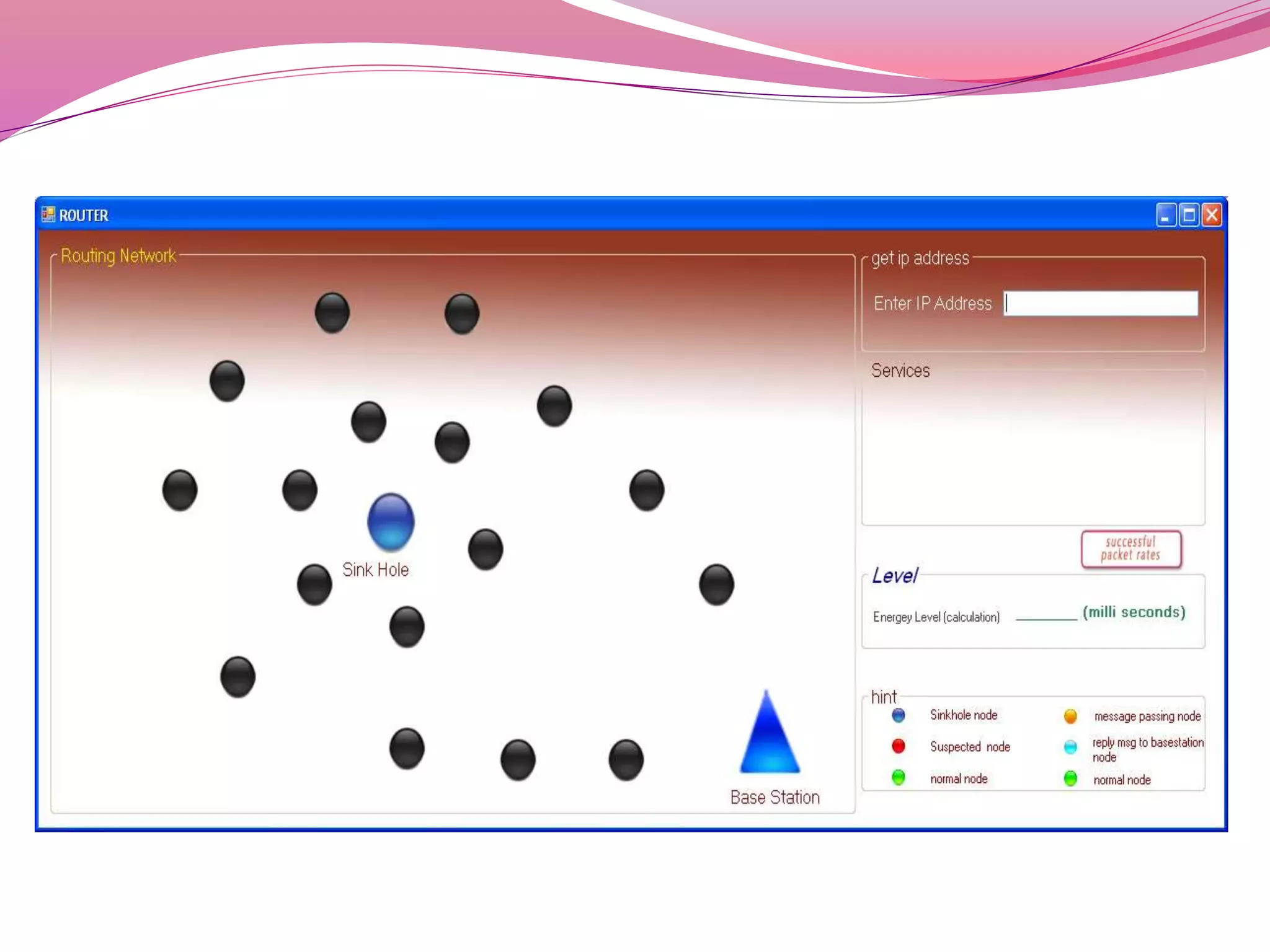
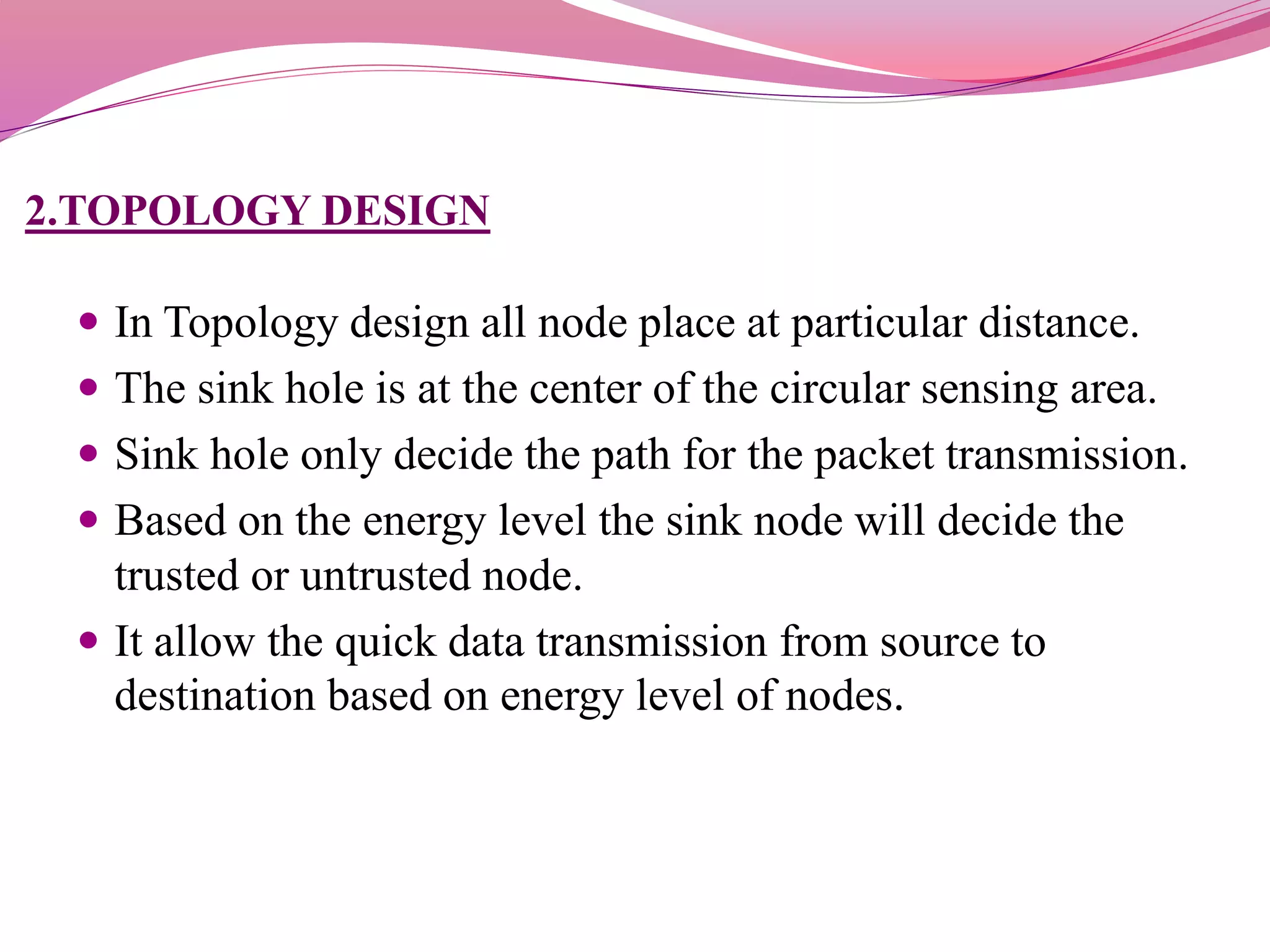
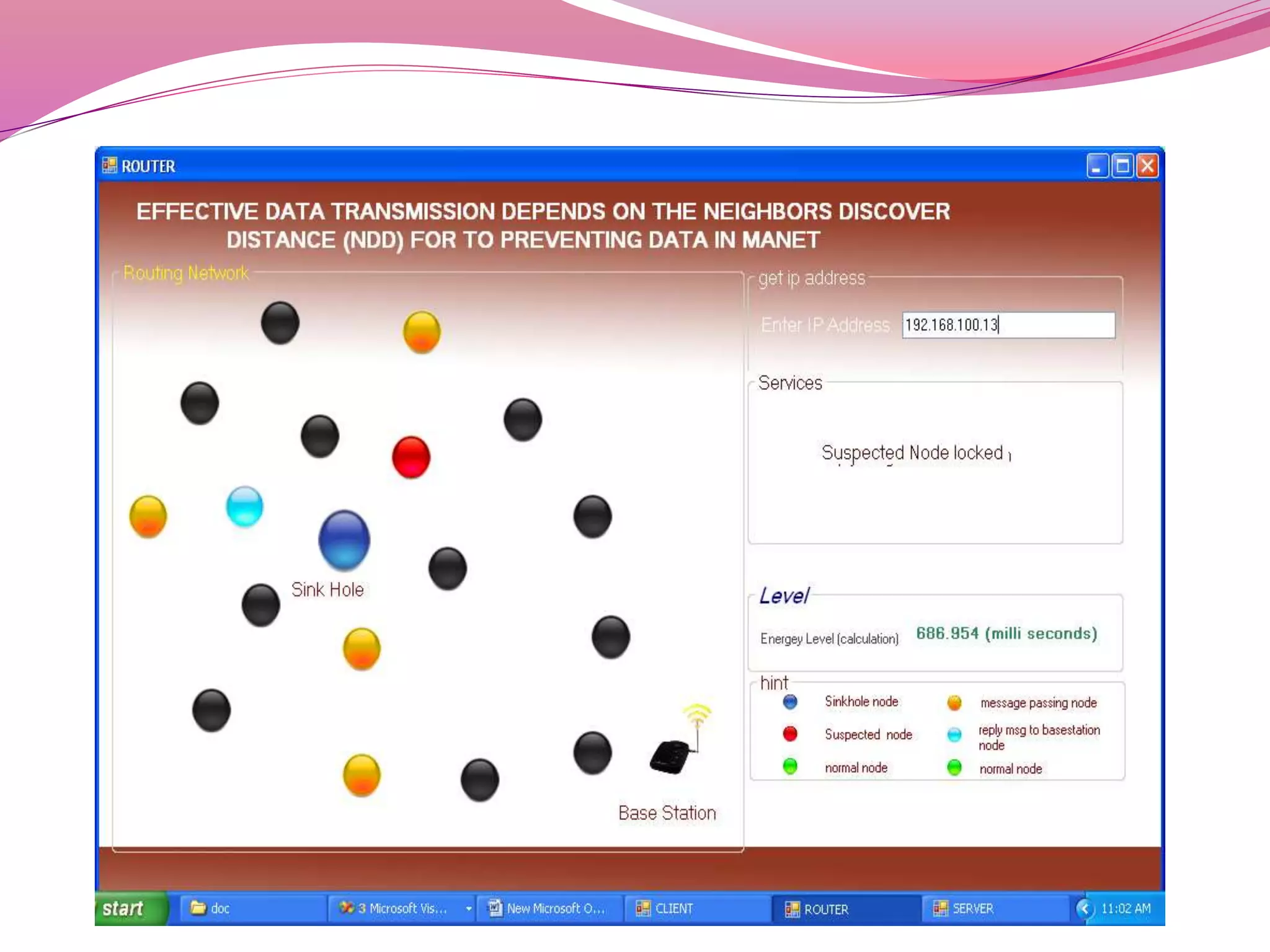
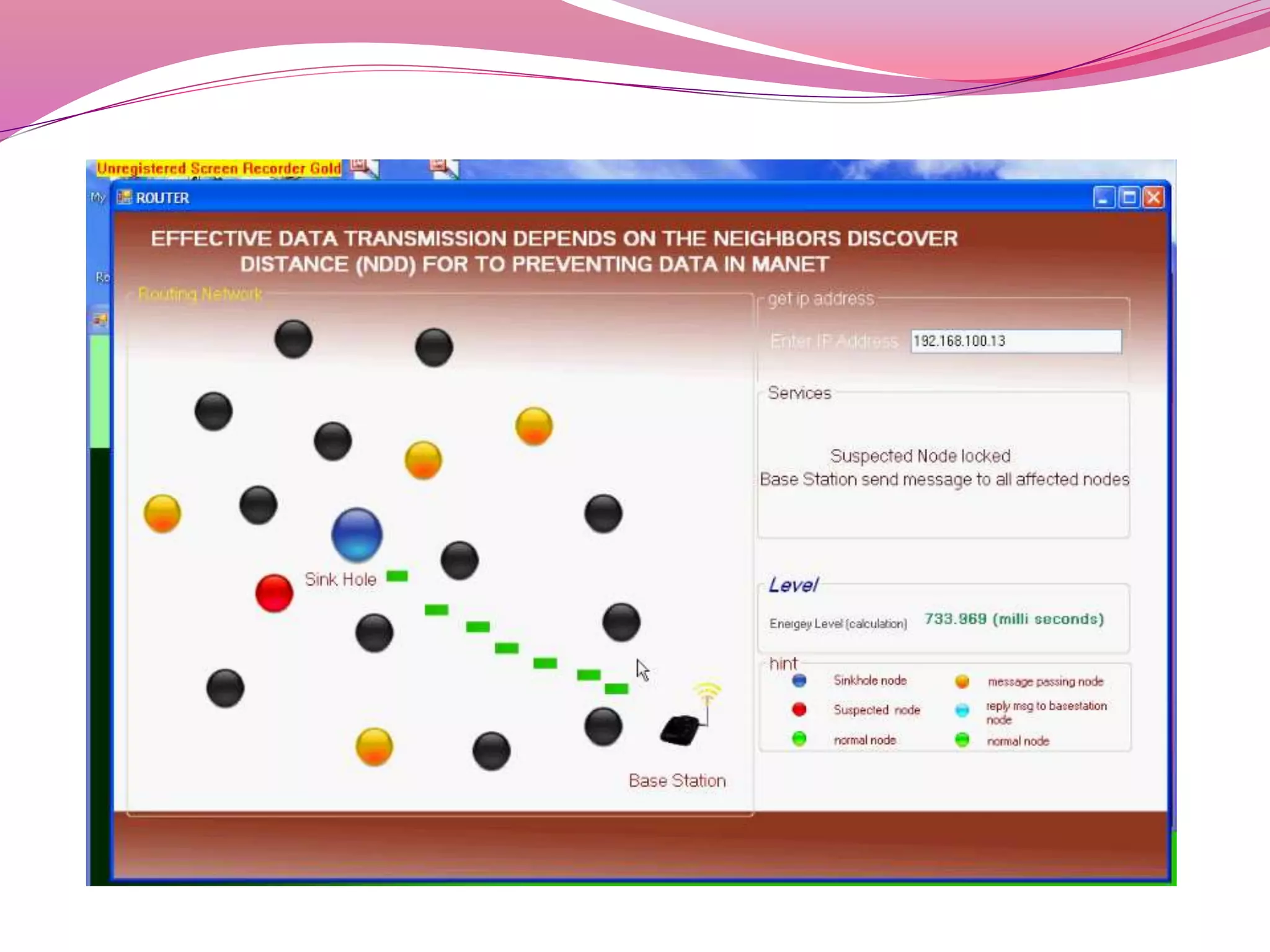
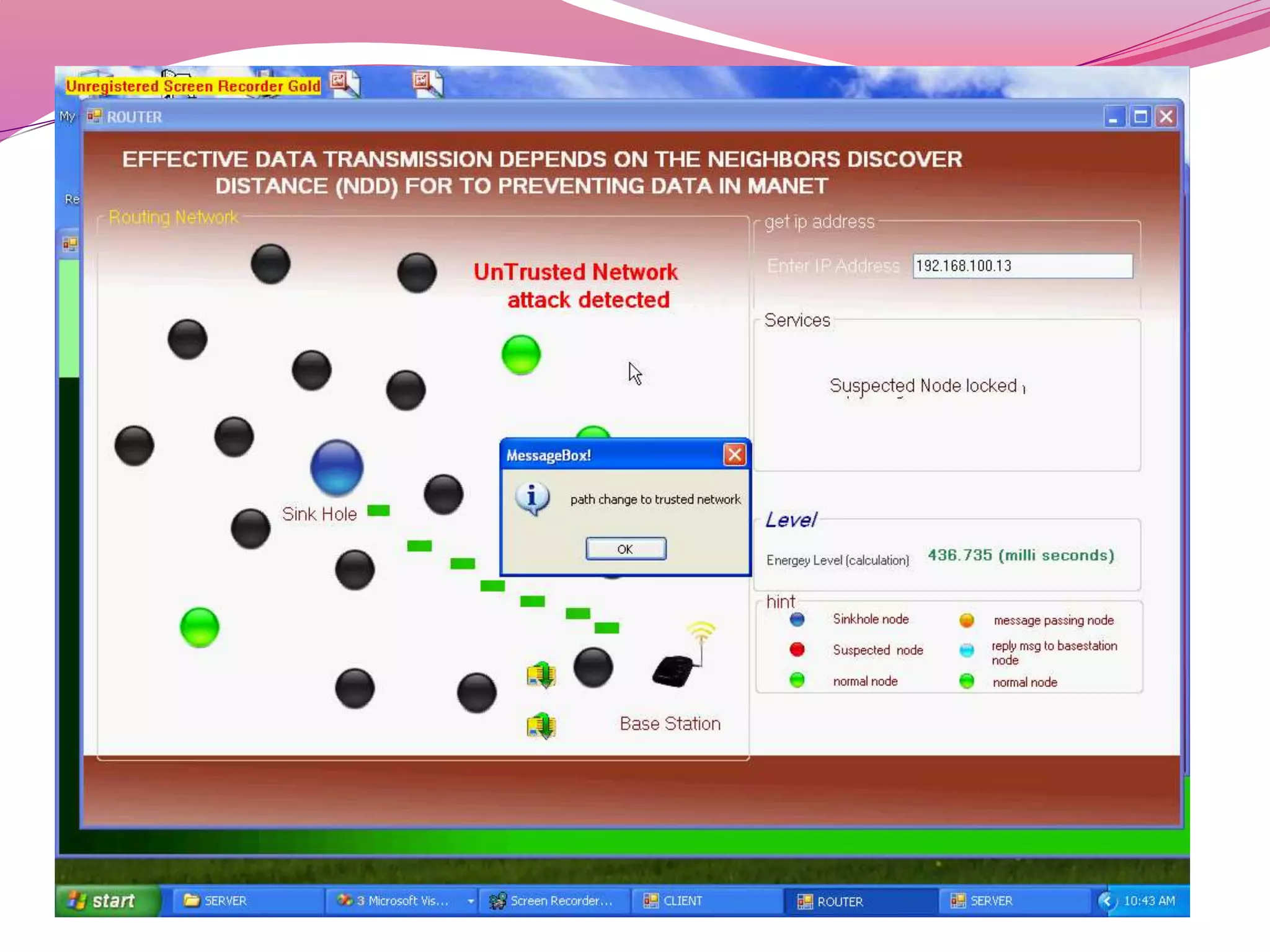
The document discusses a proposed system to detect Sybil attackers in a wireless network using a centralized base station without additional hardware like GPS. It aims to identify Sybil identities with accuracy even when nodes are mobile. A Sybil attacker can create multiple identities on a single device to launch coordinated attacks. The proposed system uses a Neighbor Discovery Distance algorithm and centralized authentication server to reduce packet delay and detect attackers, enabling efficient secure data transmission. It evaluates topology design, neighbor discovery, and how Sybil attacks work to spoof identities and impact networks. Simulation results showed the scheme can effectively detect static and mobile Sybil attackers.