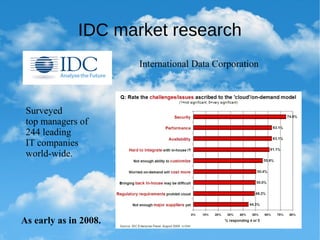
1. Cloud computing provides flexibility and economies of scale but introduces new security risks as sensitive data and infrastructure are placed outside traditional secure perimeters.
2. Traditional security measures like firewalls and intrusion detection become more difficult in cloud environments where virtual machines are dynamically allocated across shared physical servers.
3. Ensuring data integrity, updating security software, complying with regulations, and monitoring administrator access require new solutions to prove security and respond to vulnerabilities in cloud infrastructure and virtual environments.