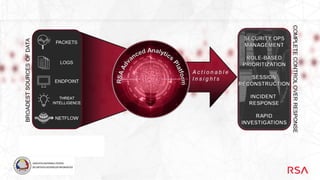
Centralizing incident response is important to minimize loss from attacks. Tools that provide visibility into logs, packets, endpoints and threat intelligence are essential for detection and response. They allow security teams to spot anomalous activity, investigate incidents, and respond in a timely manner. RSA NetWitness provides a framework to centralize incident response through security operations centers that capture, enrich and analyze data to improve detection and guide investigations. It enables rapid response through data enrichment and analytics.