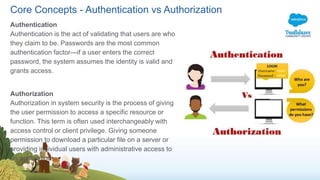
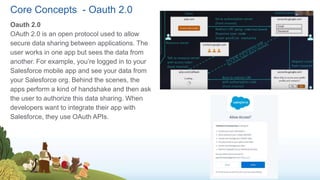
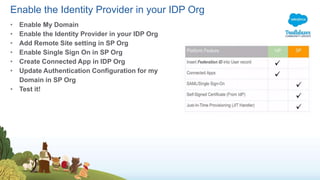
The document outlines a presentation on Salesforce Identity Management, highlighting key concepts such as authentication, authorization, identity providers, and OAuth 2.0. It mentions potential risks related to forward-looking statements made during the presentation and provides an agenda for the discussion, which includes demos and a Q&A session. The document emphasizes the importance of centralized user account management and various protocols for secure data sharing between applications.