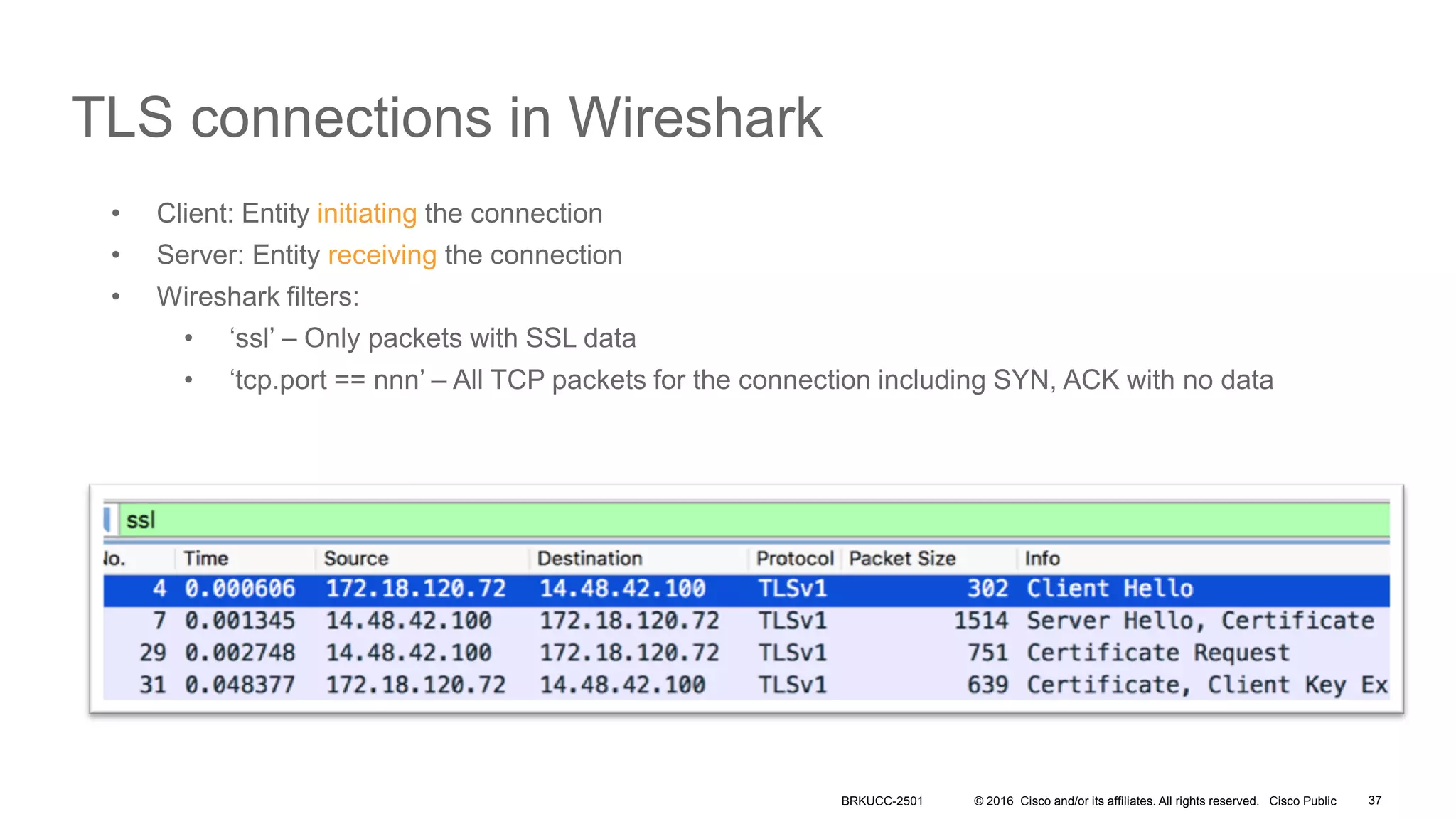
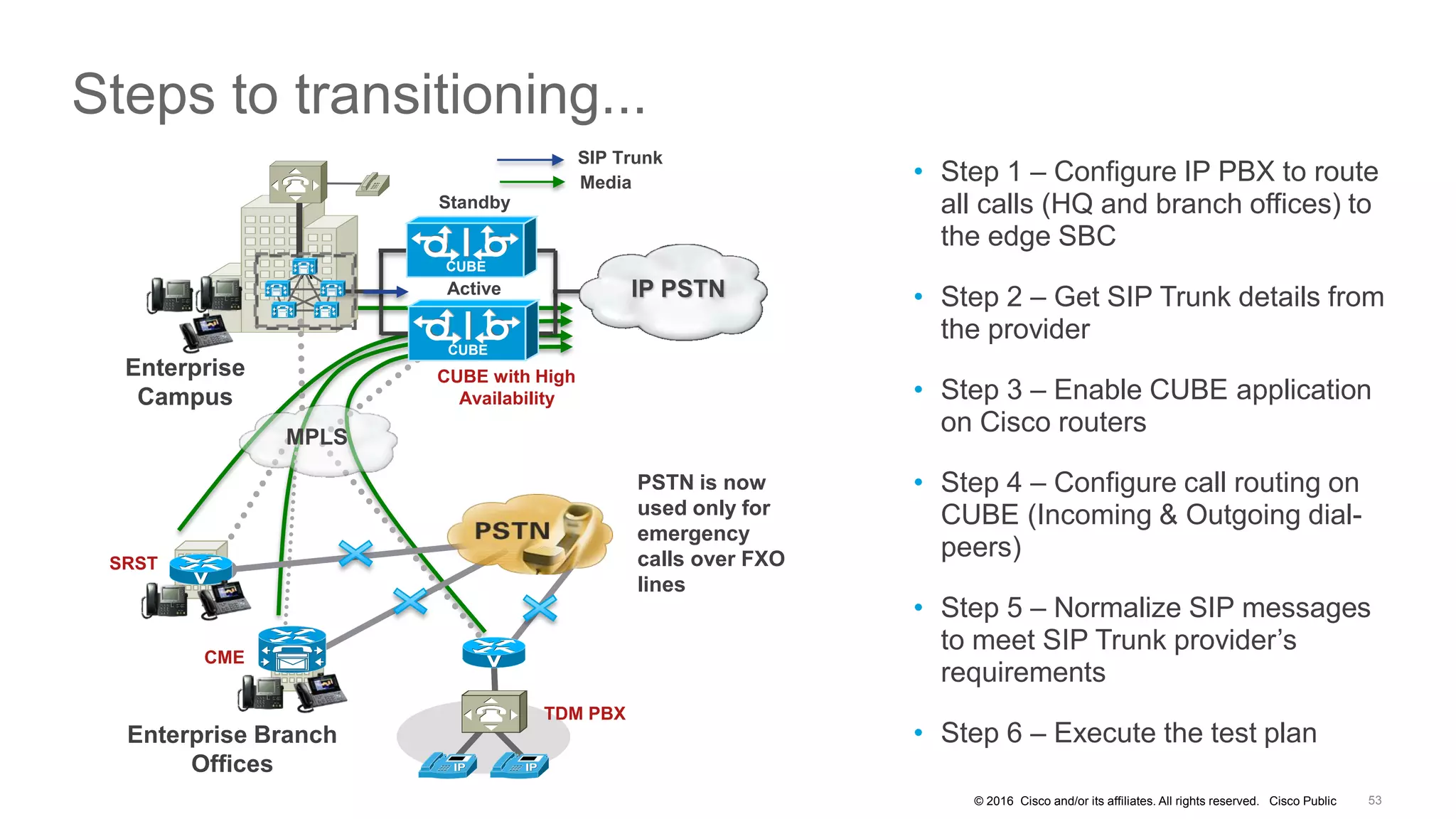
- The document discusses securing VoIP deployments using Cisco Unified Communications Manager (CUCM) and Cisco Unified Border Element (CUBE)/Session Border Controller (SBC).
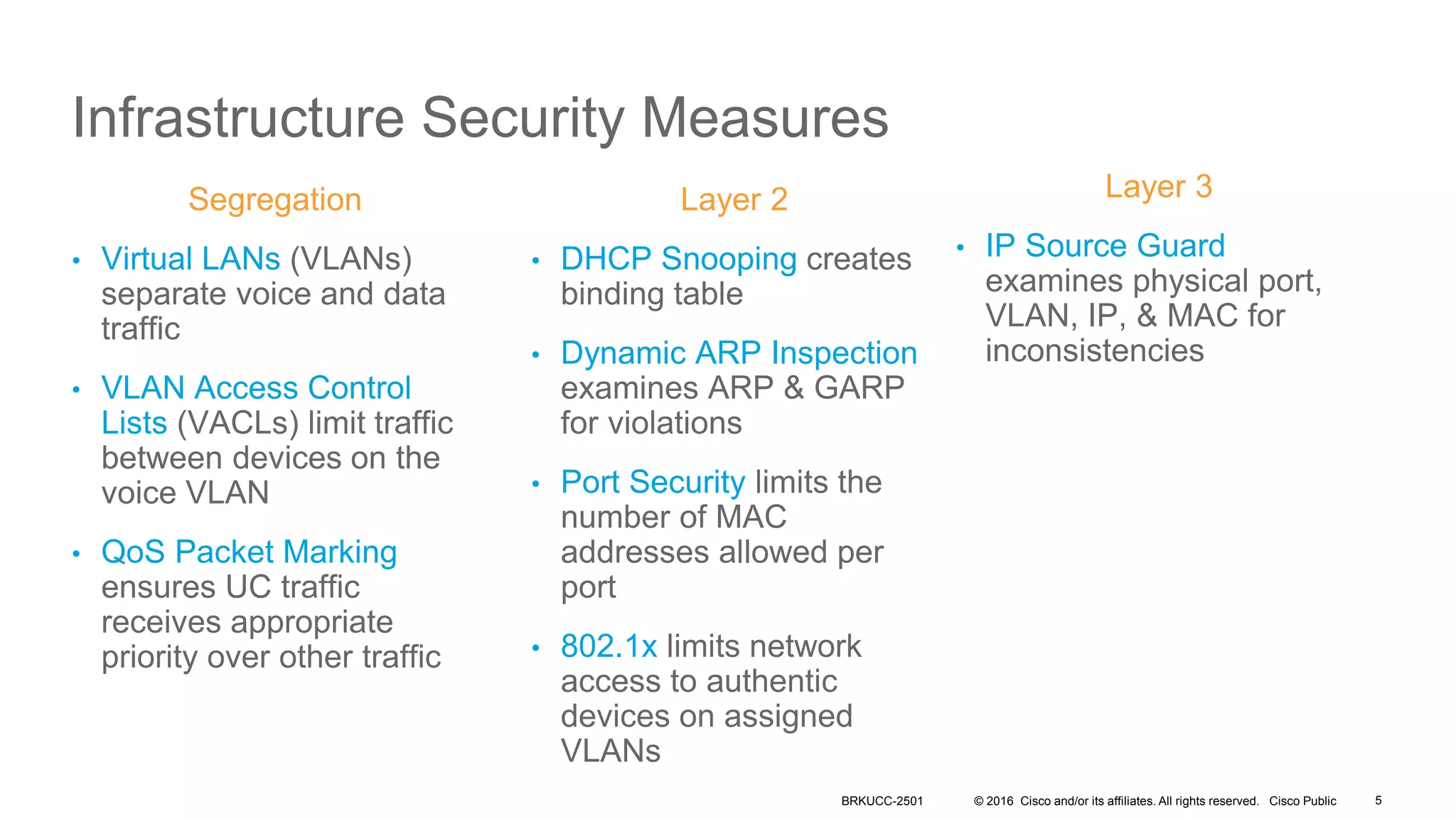
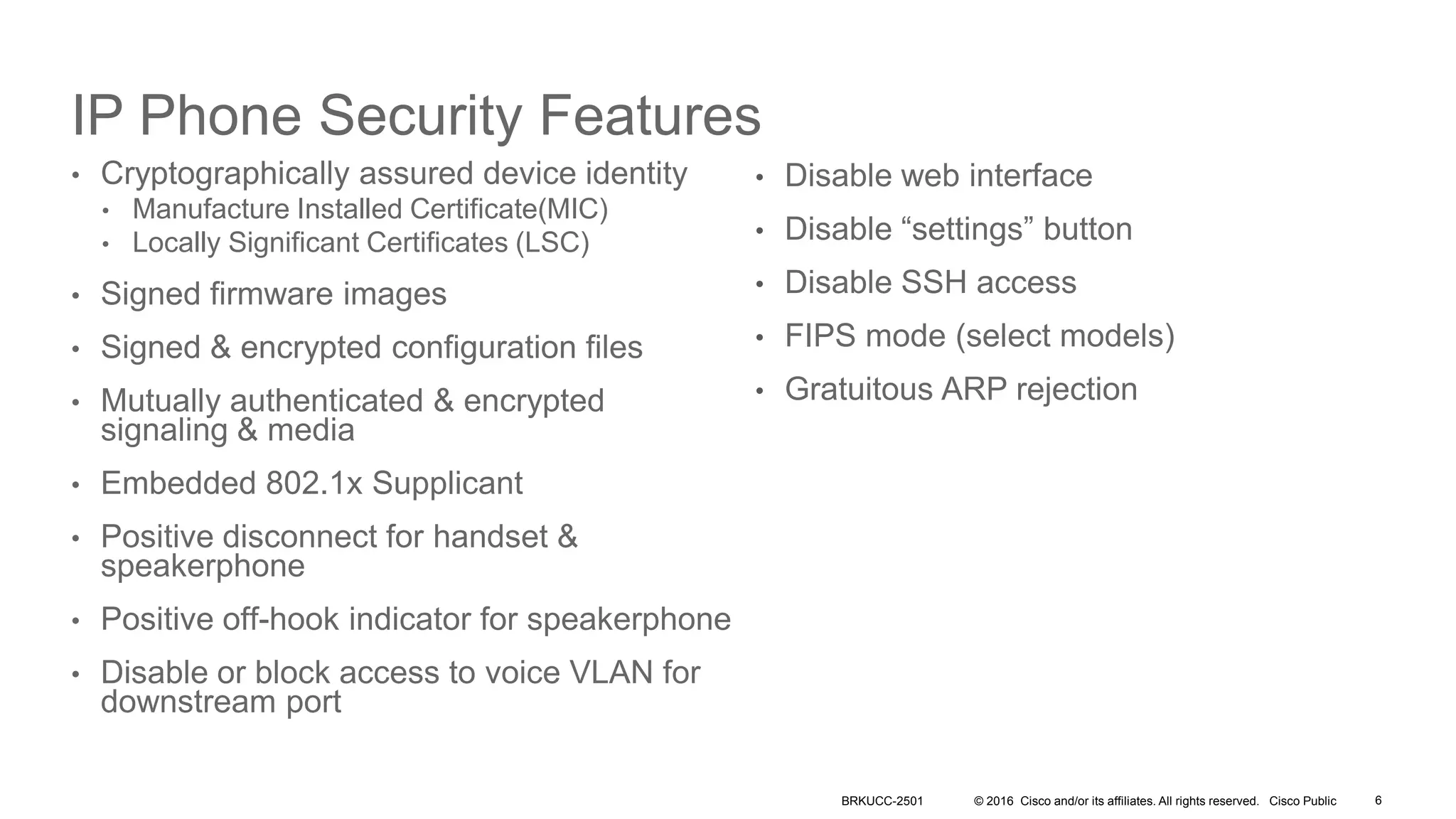
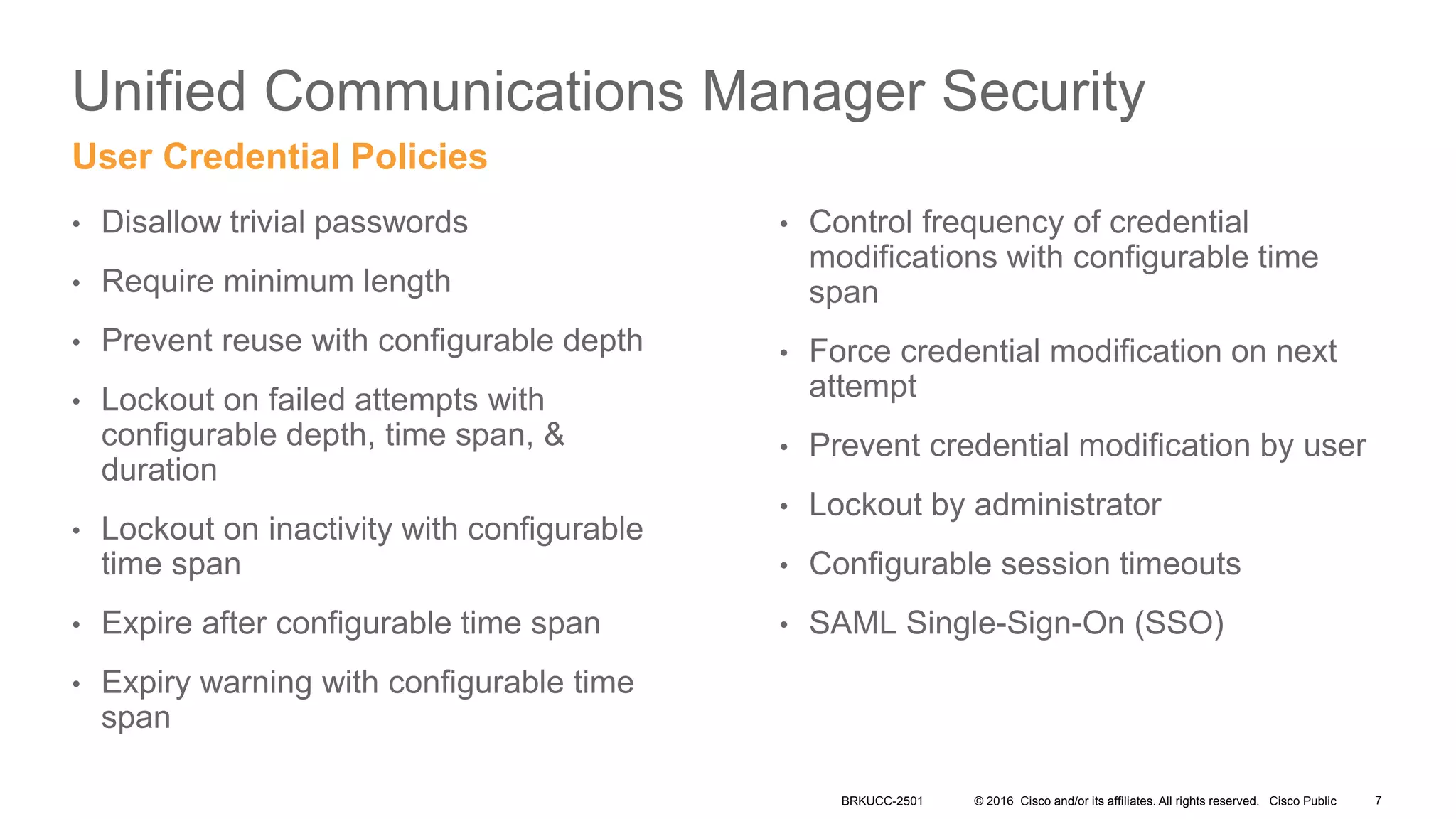
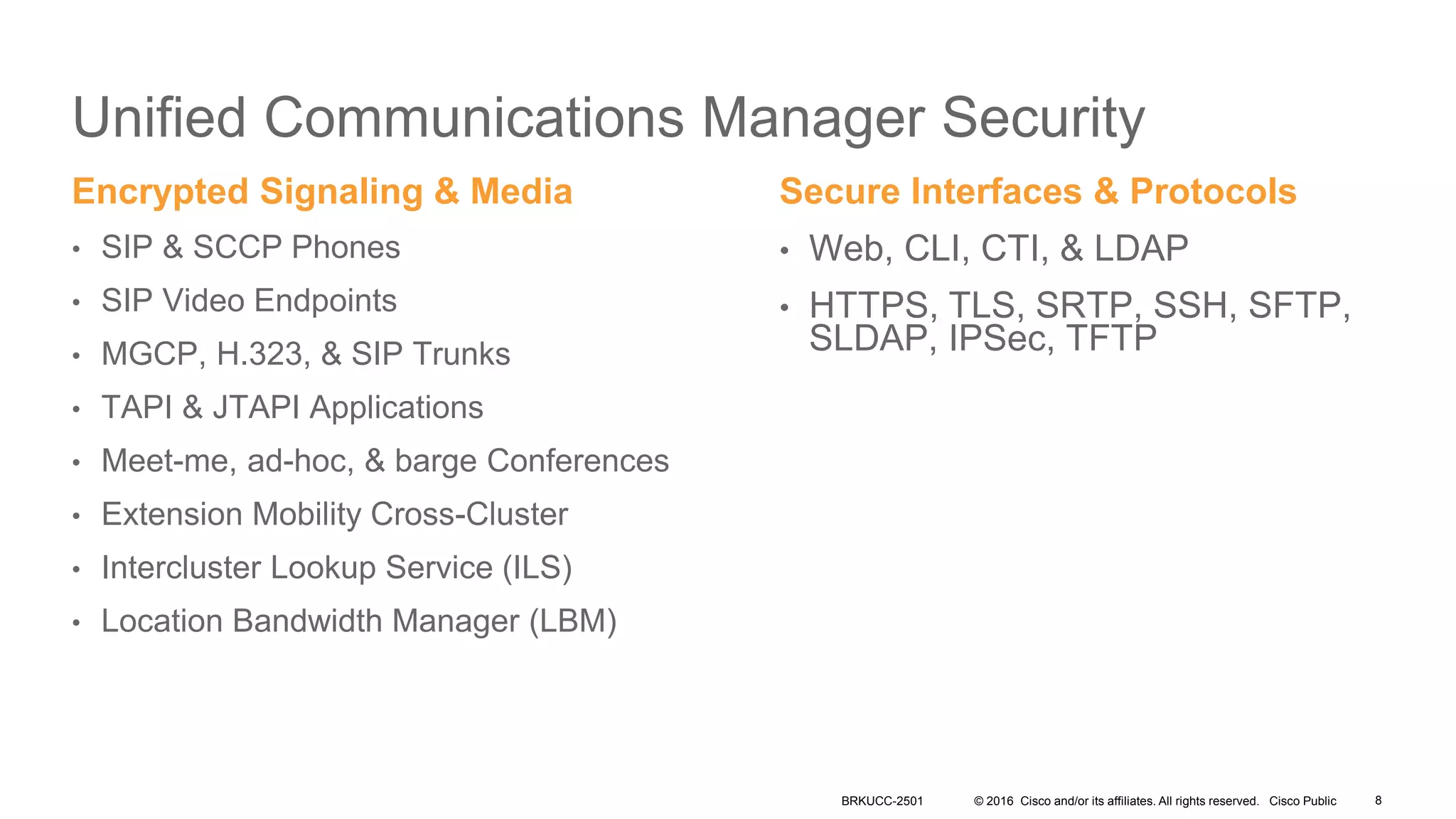
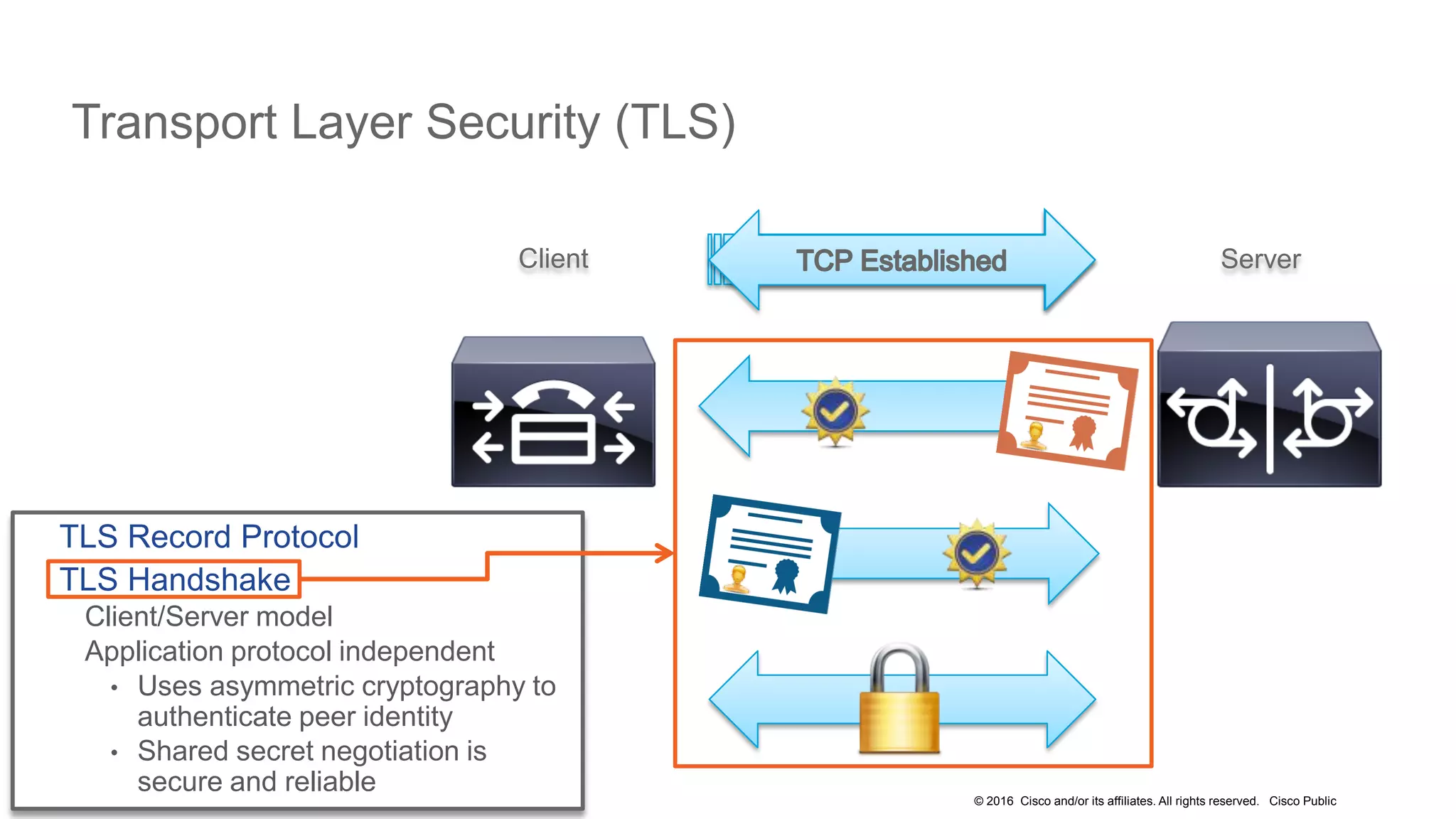
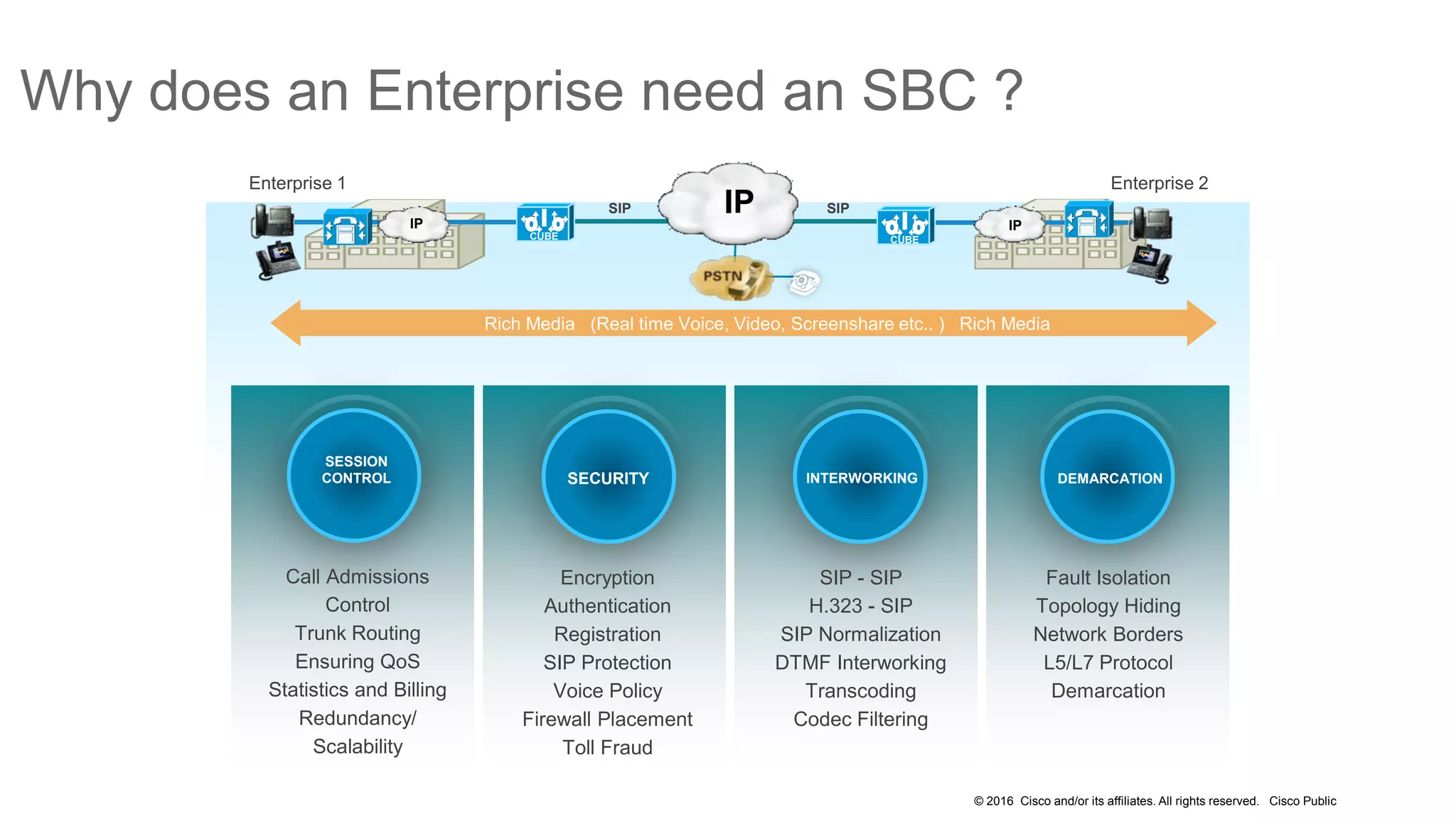
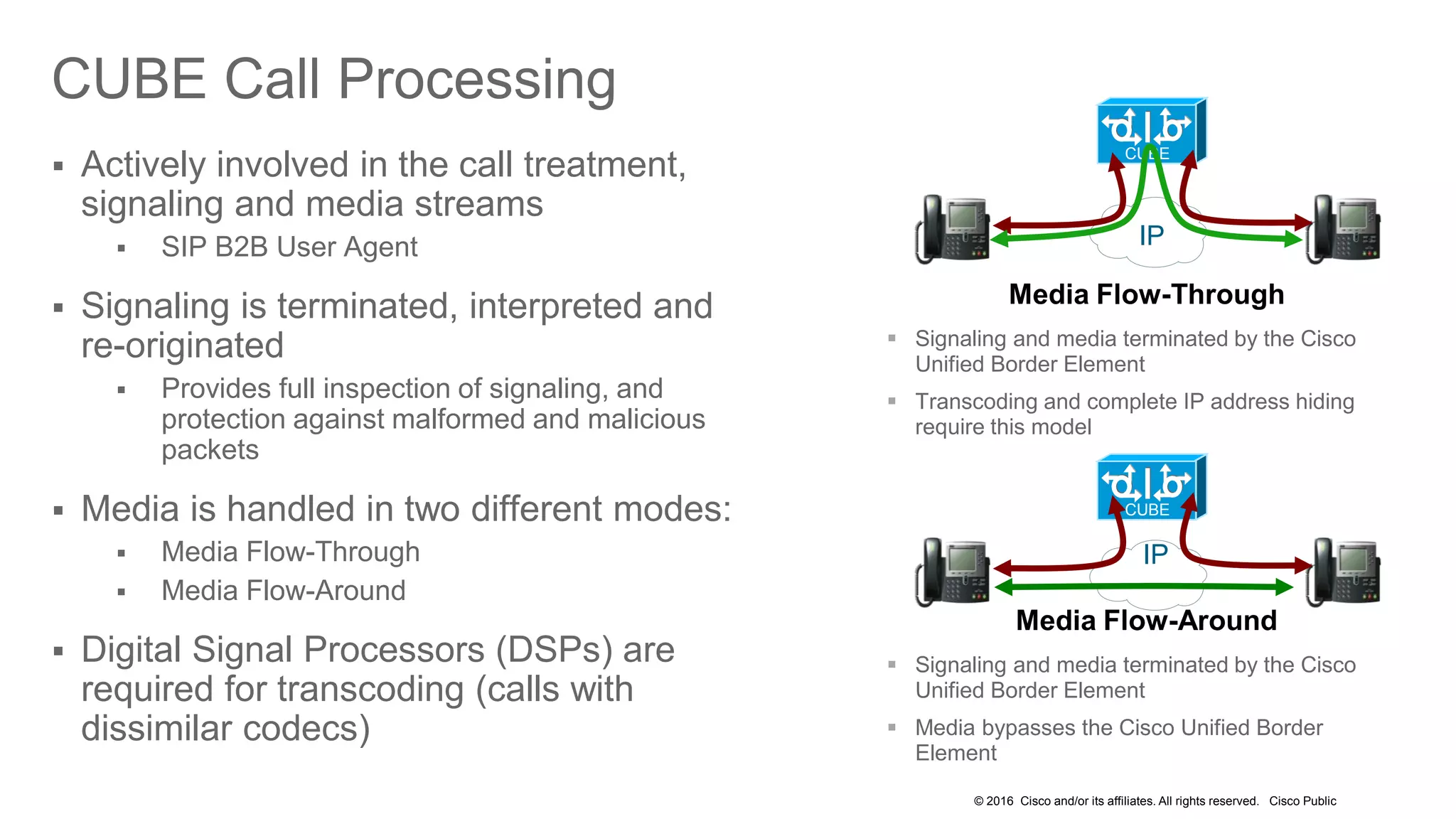
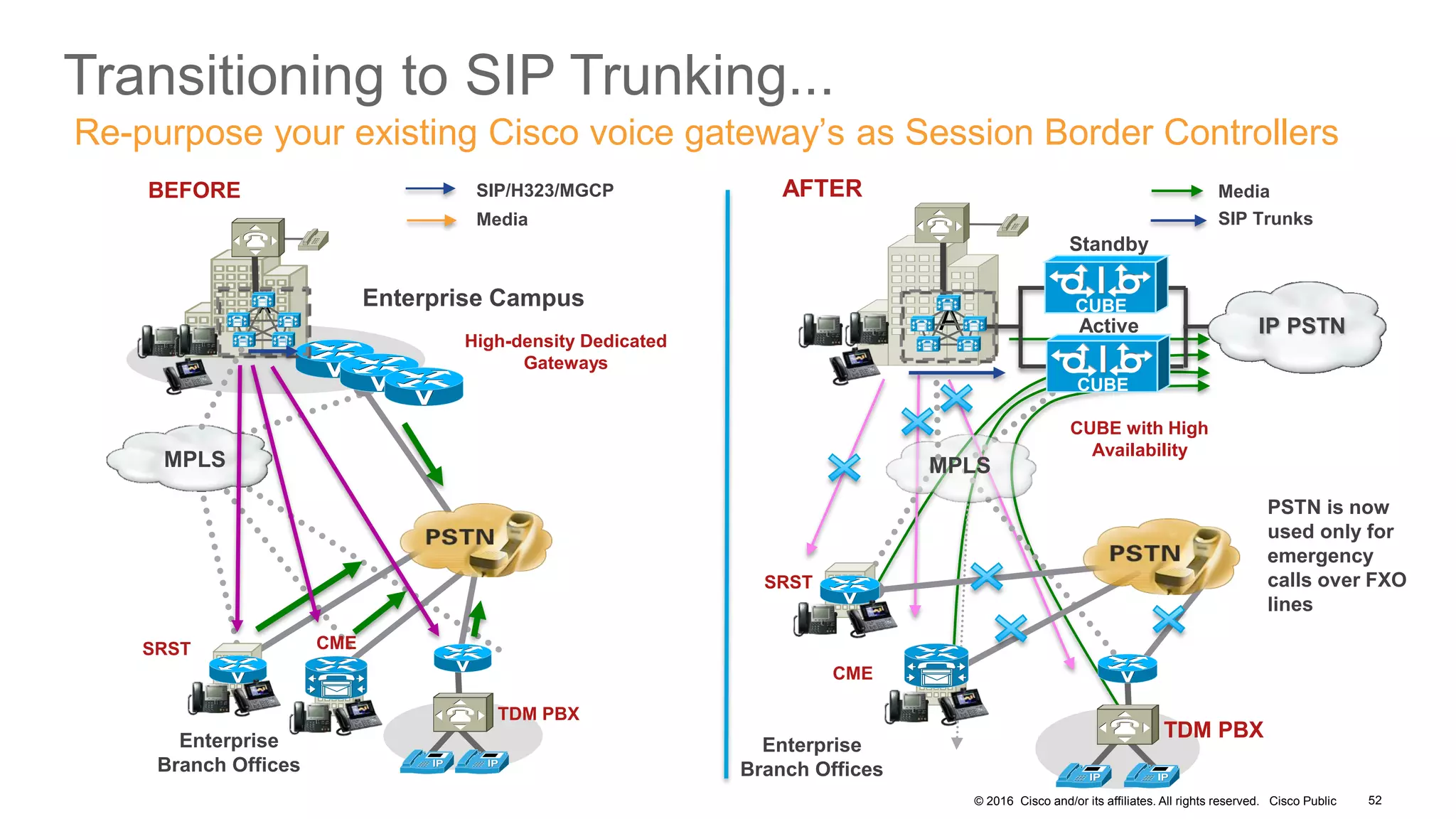
- It covers security measures for the network infrastructure, endpoints, and call control using CUCM as well as securing the edge of the network with CUBE/SBC.
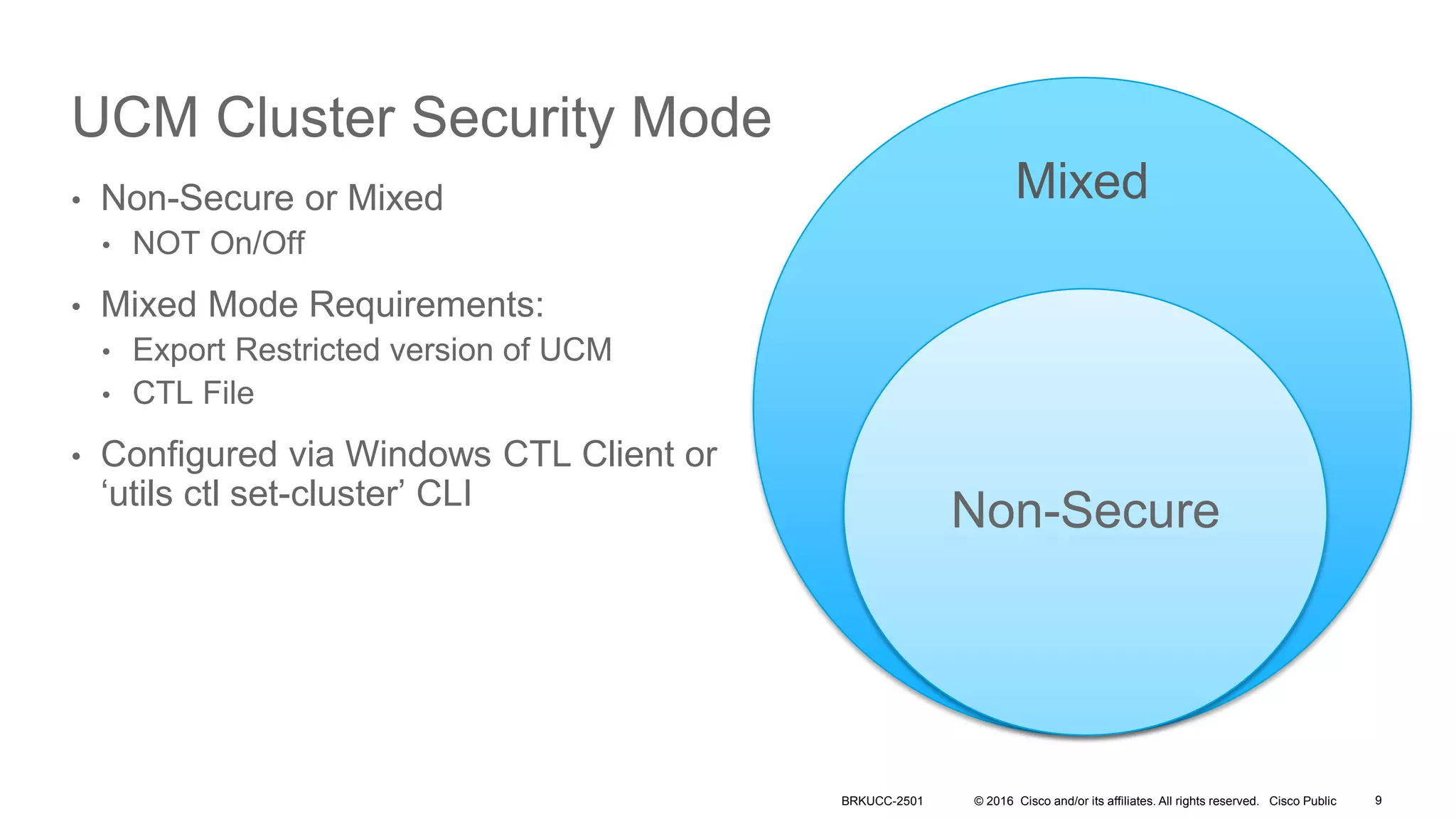
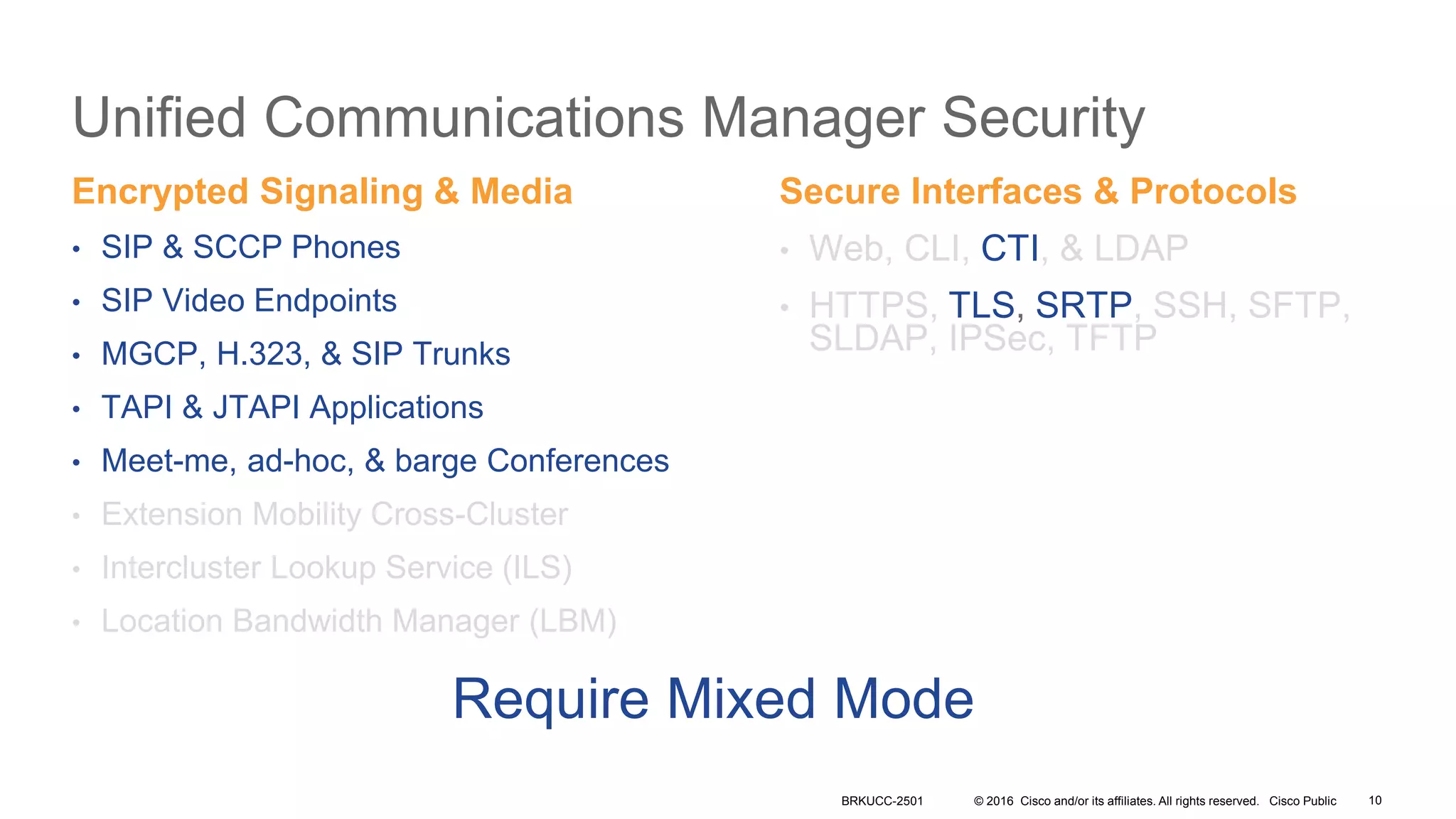
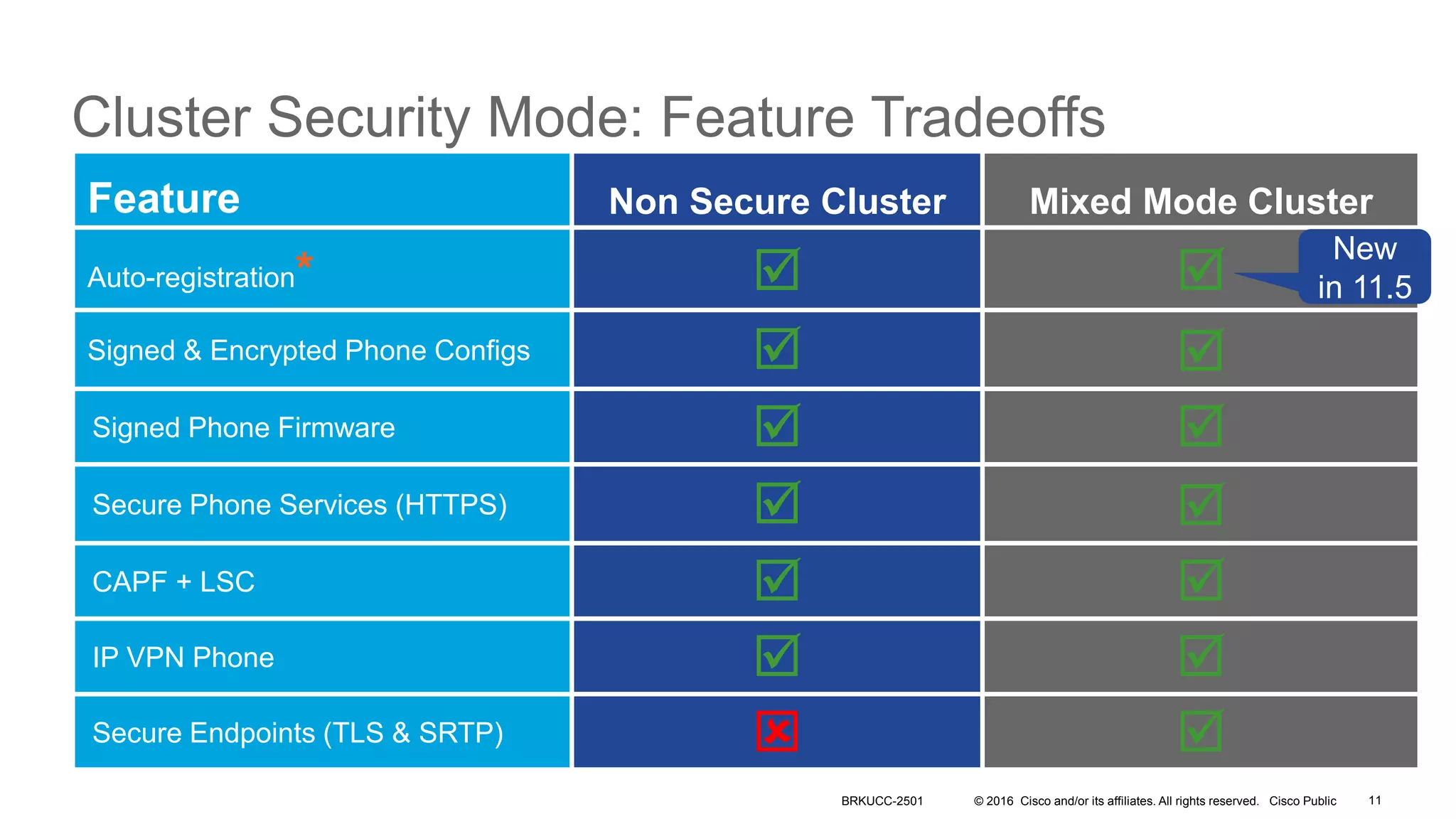
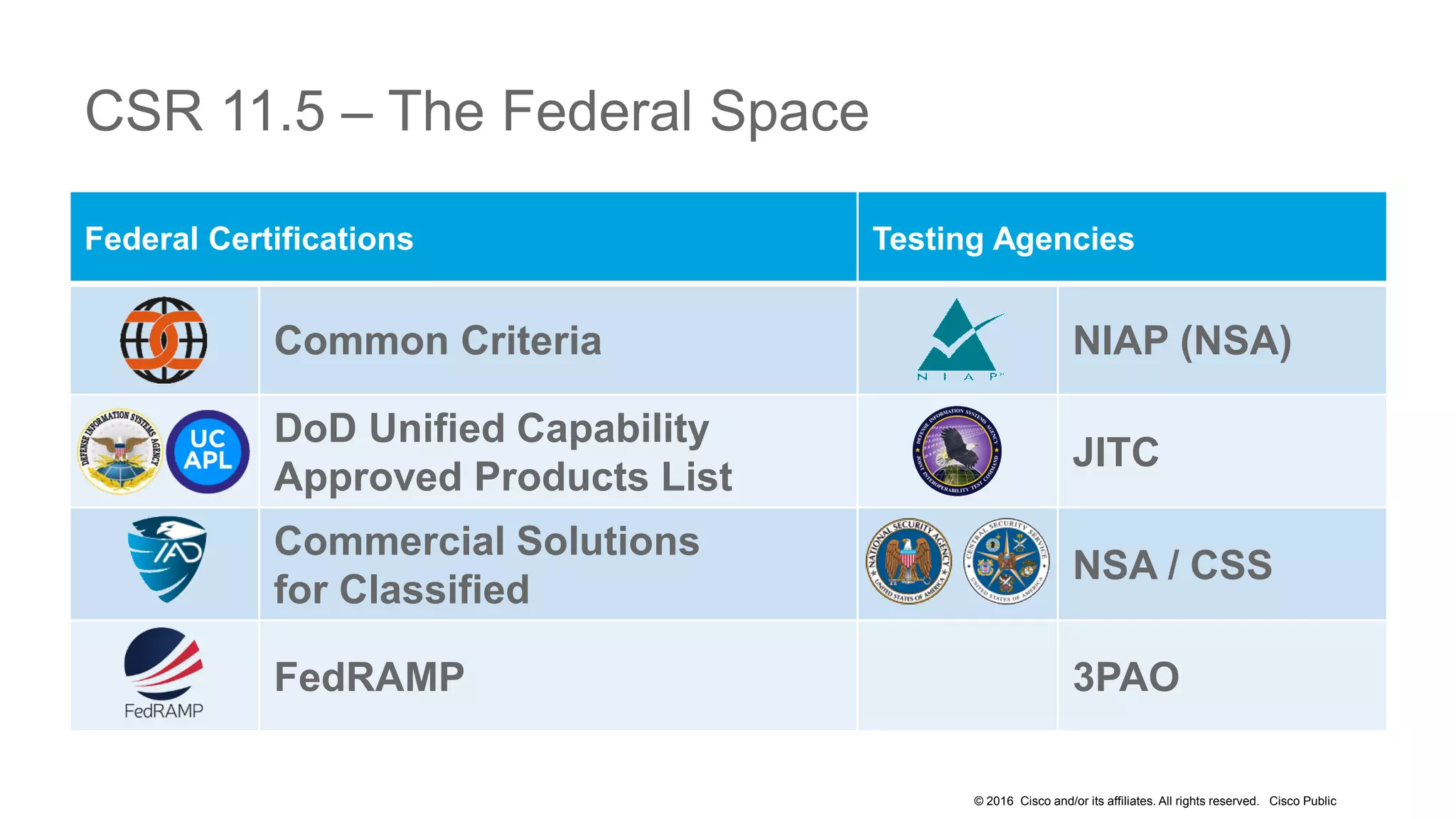
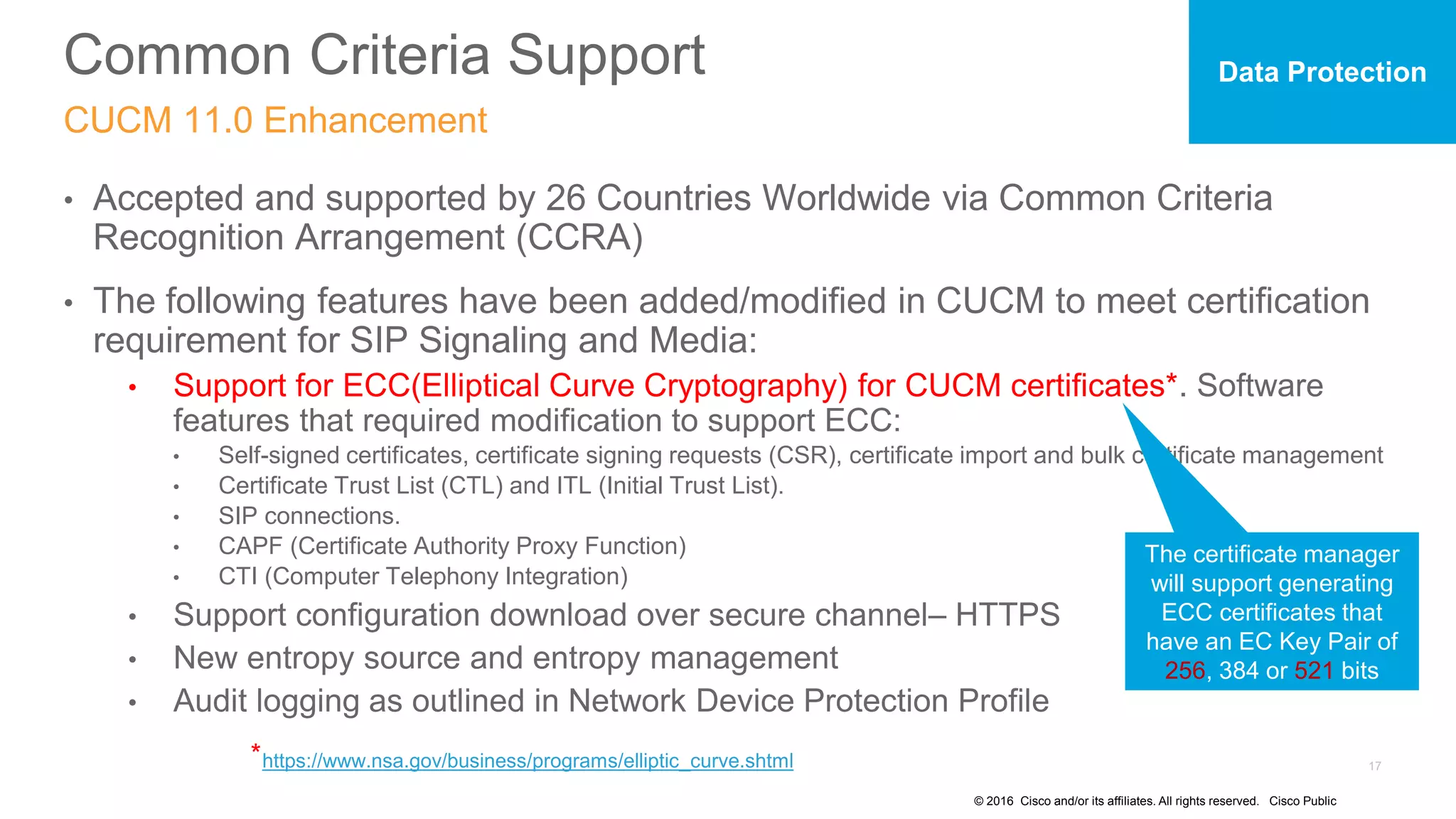
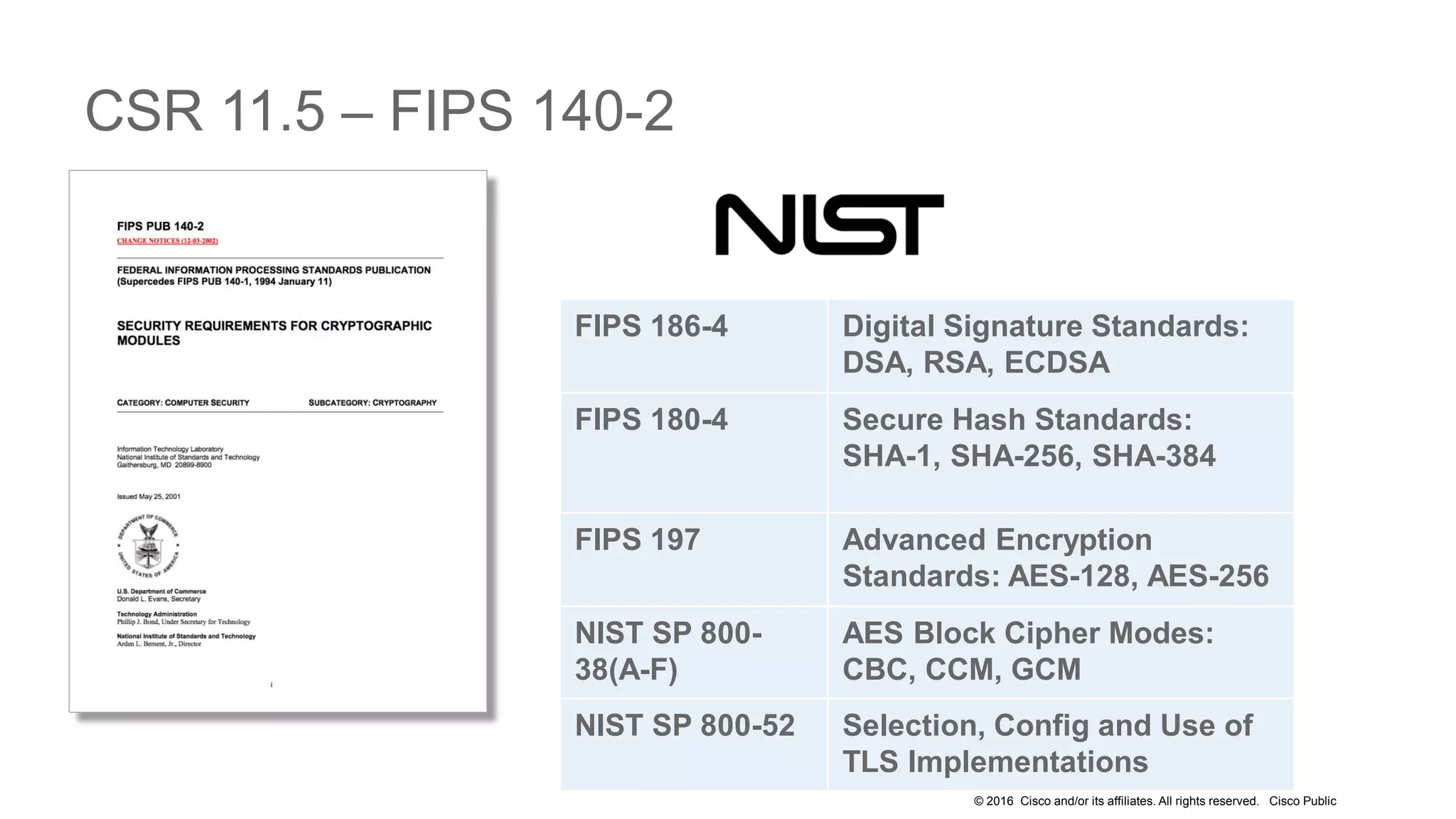
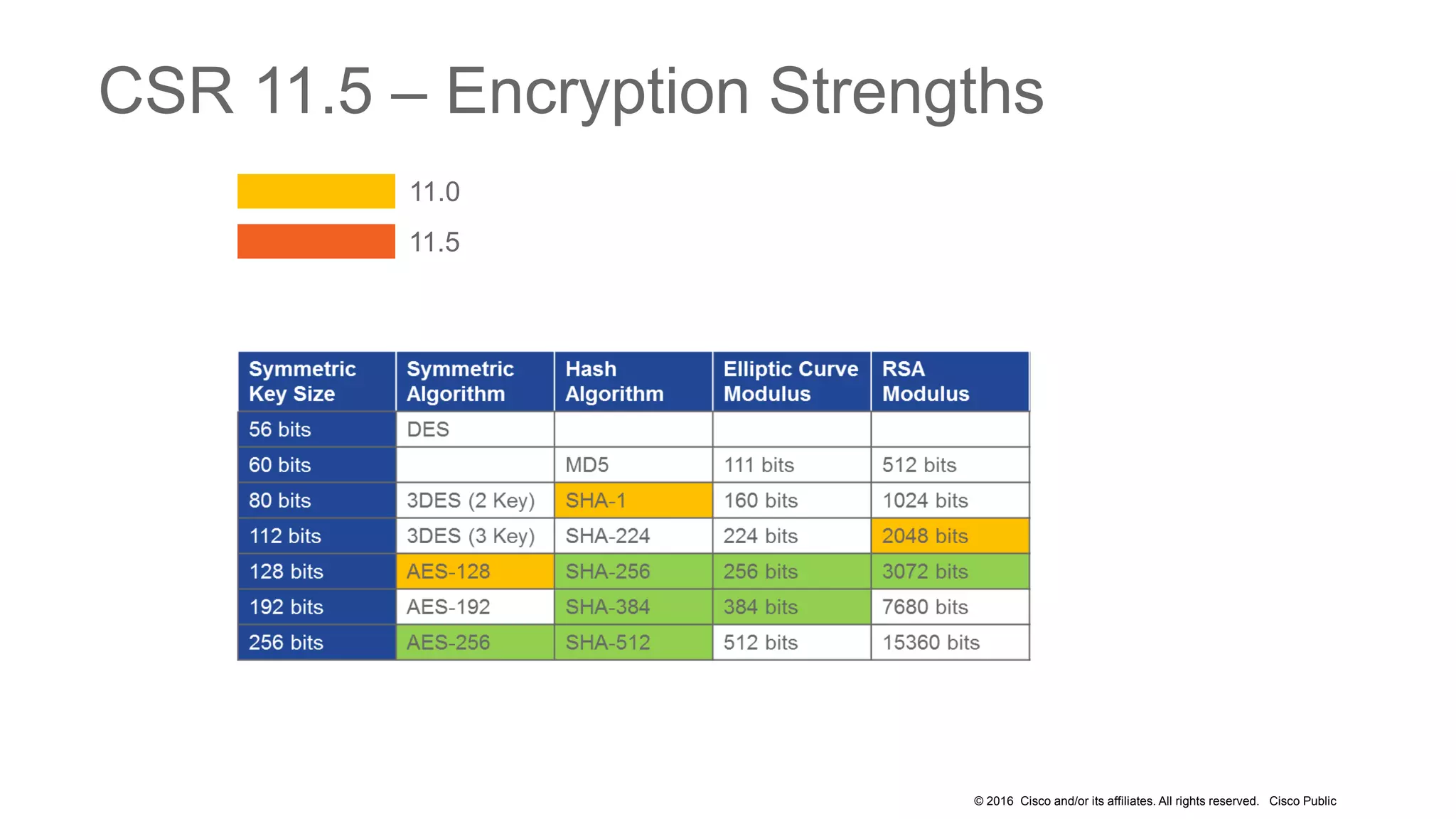
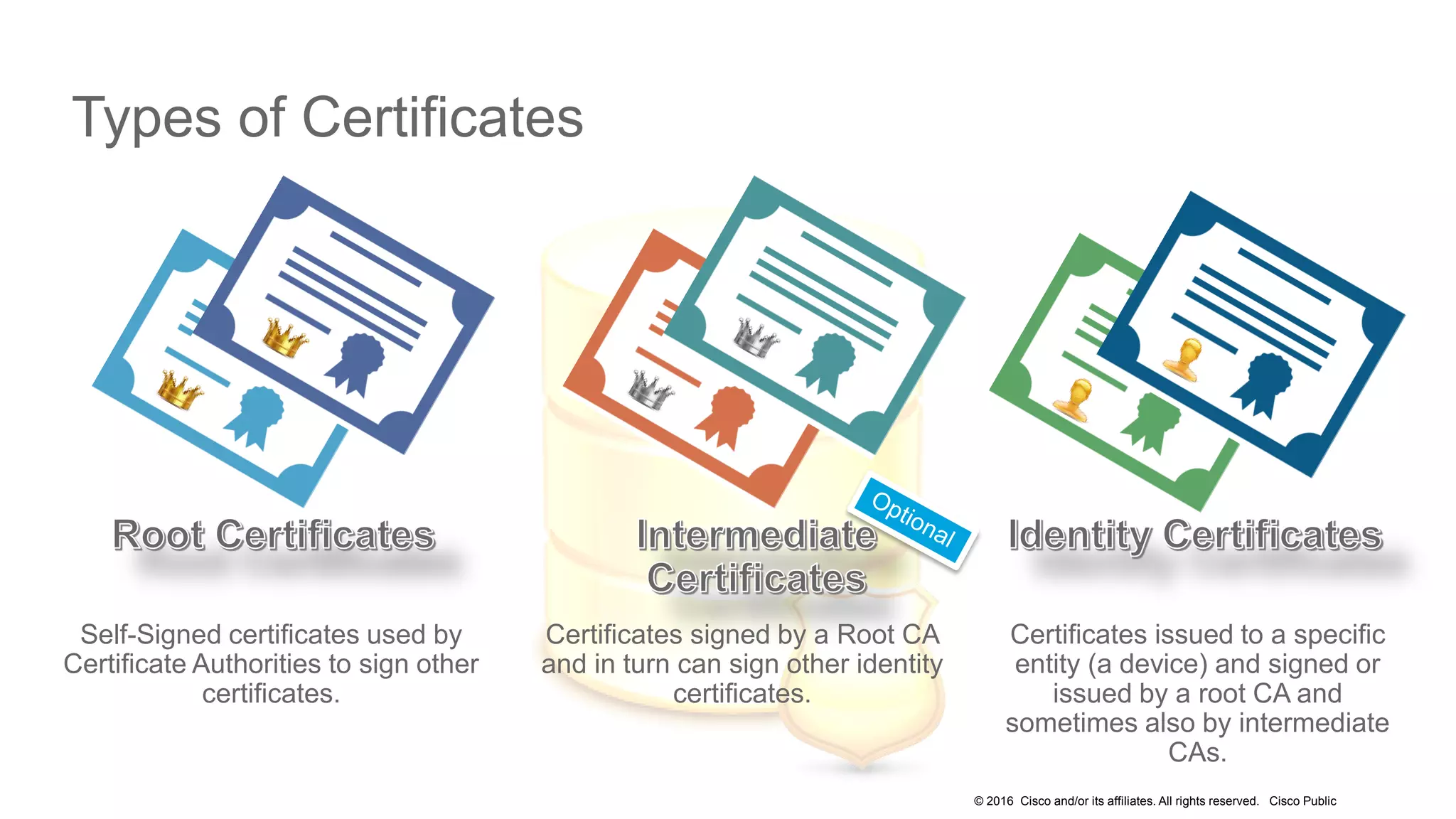
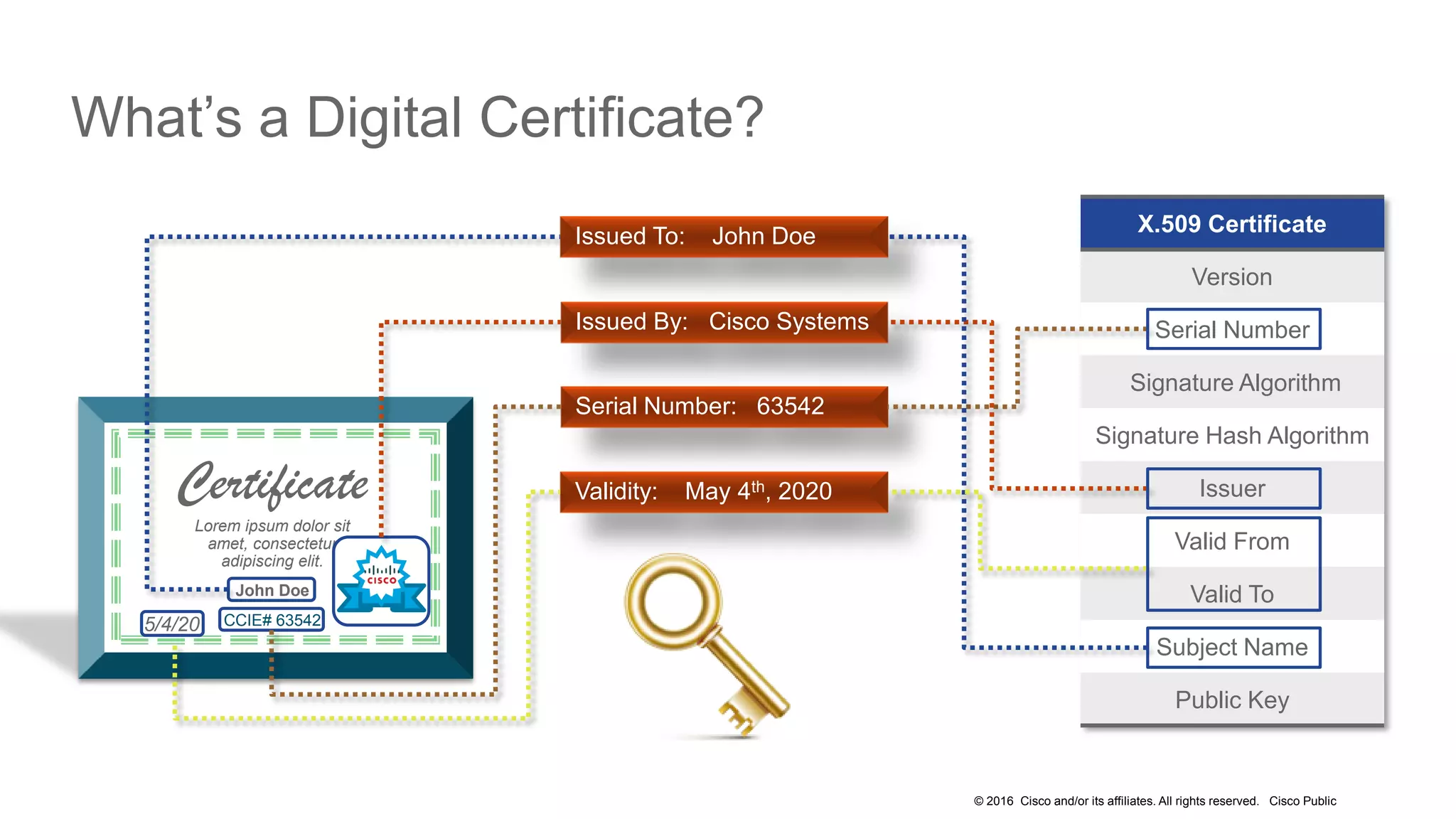
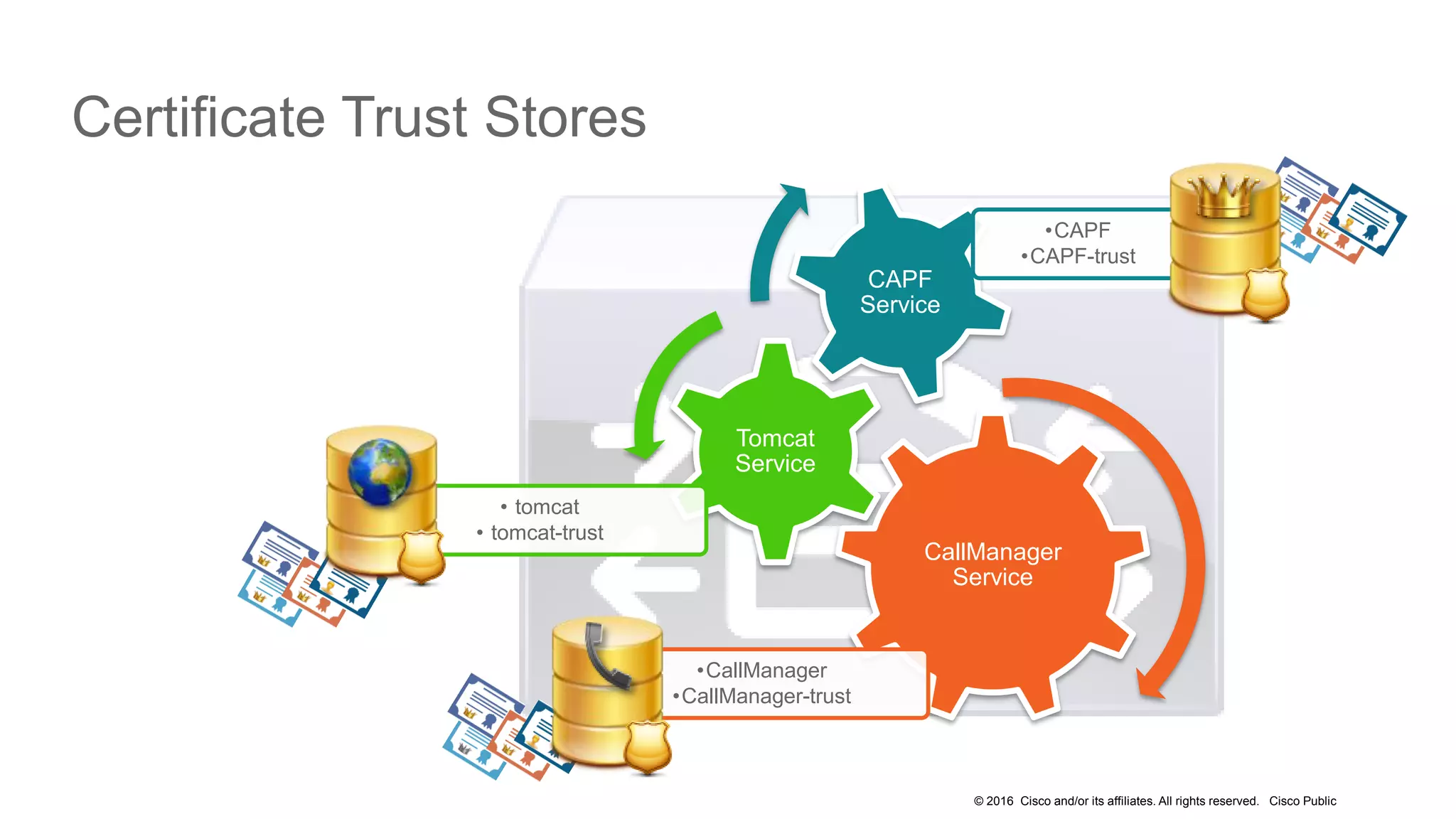
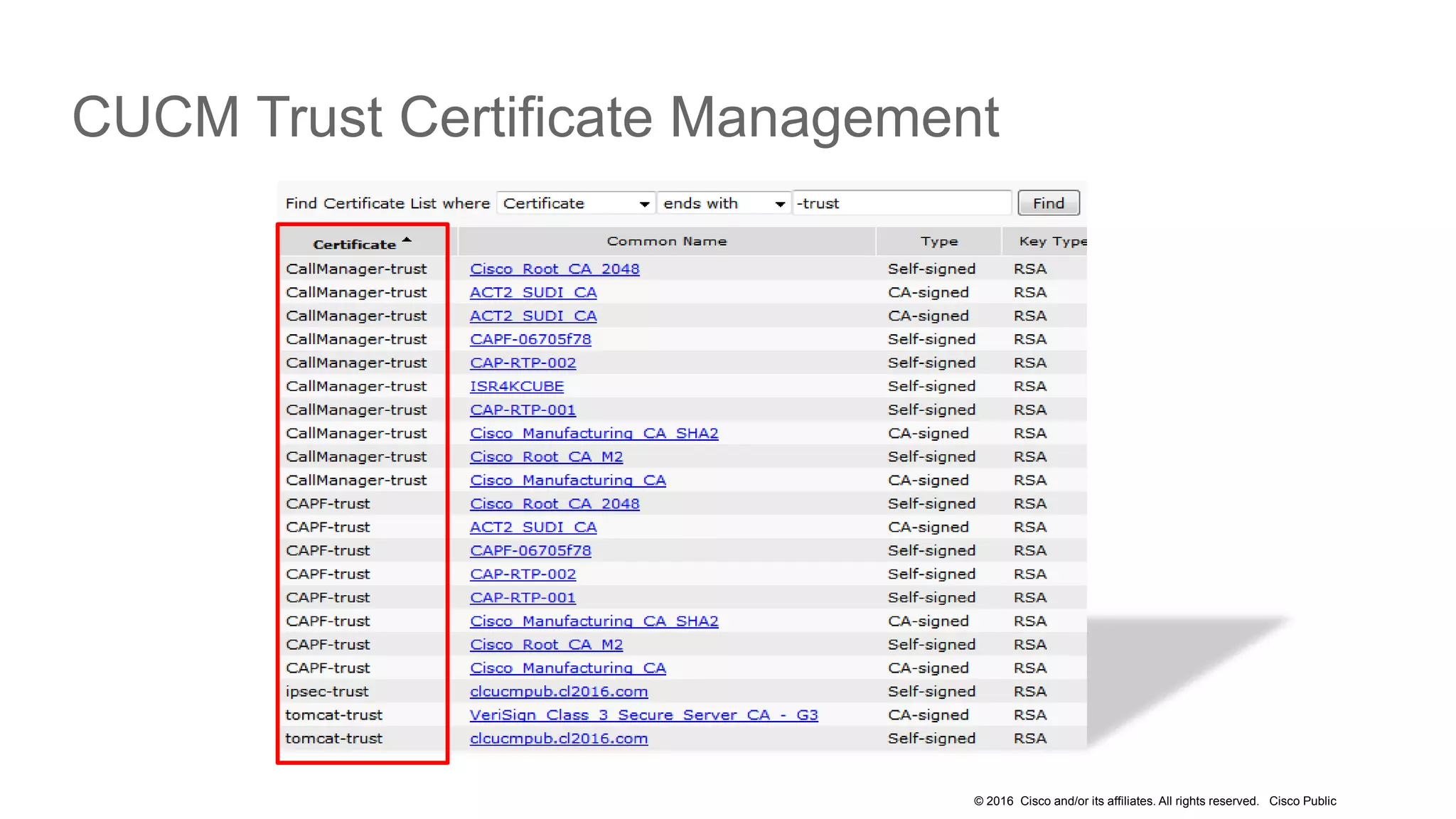
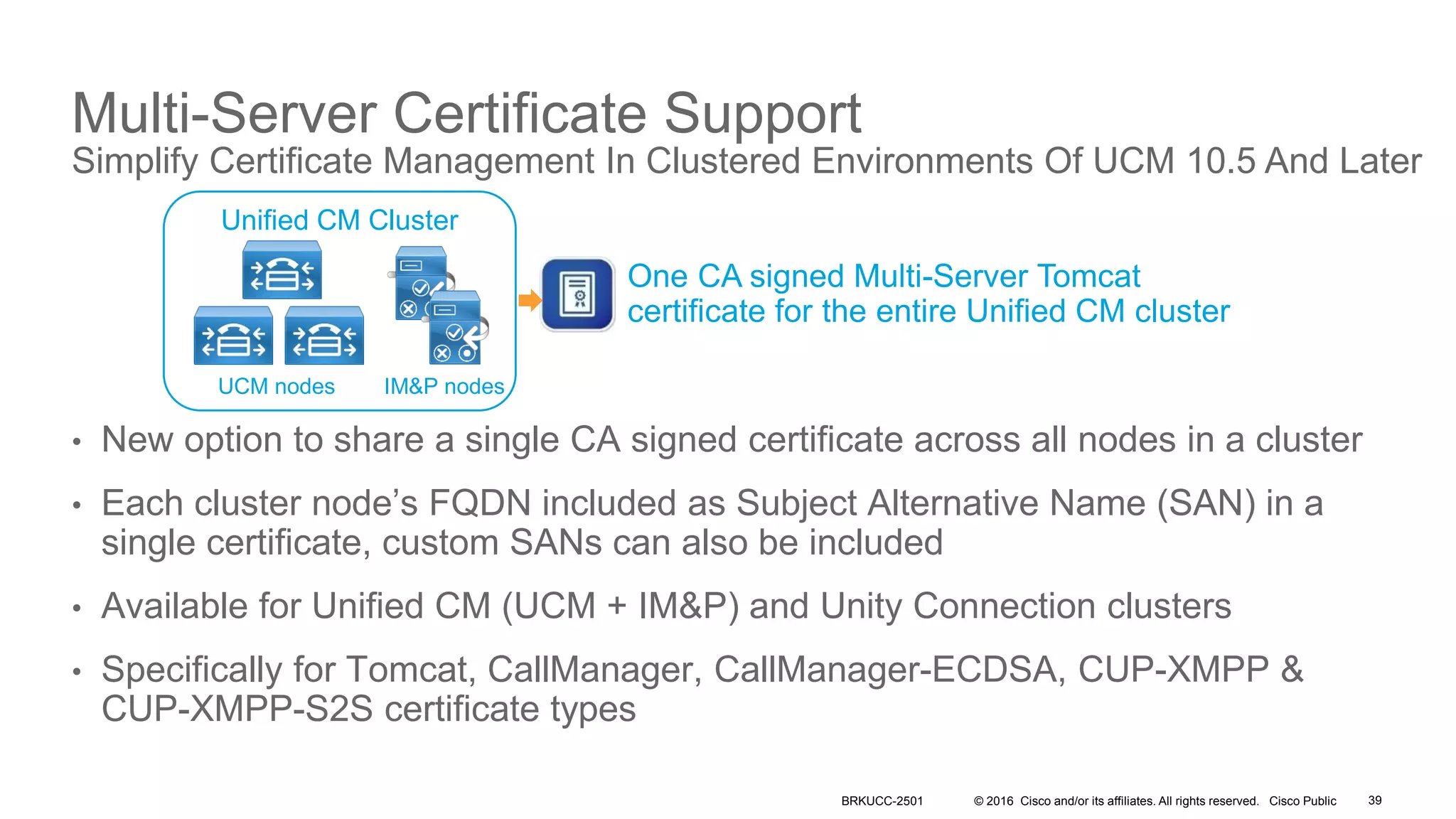
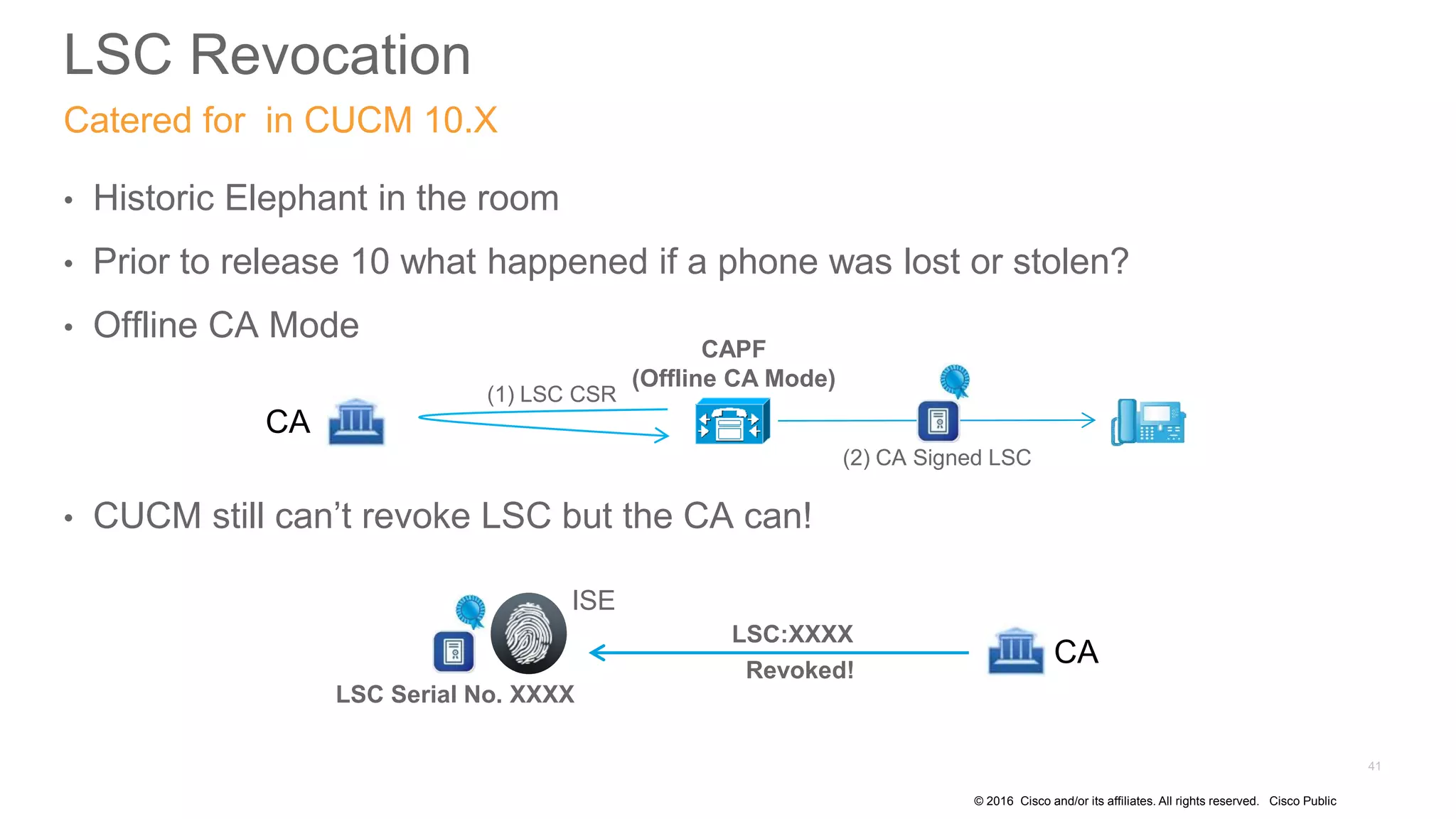
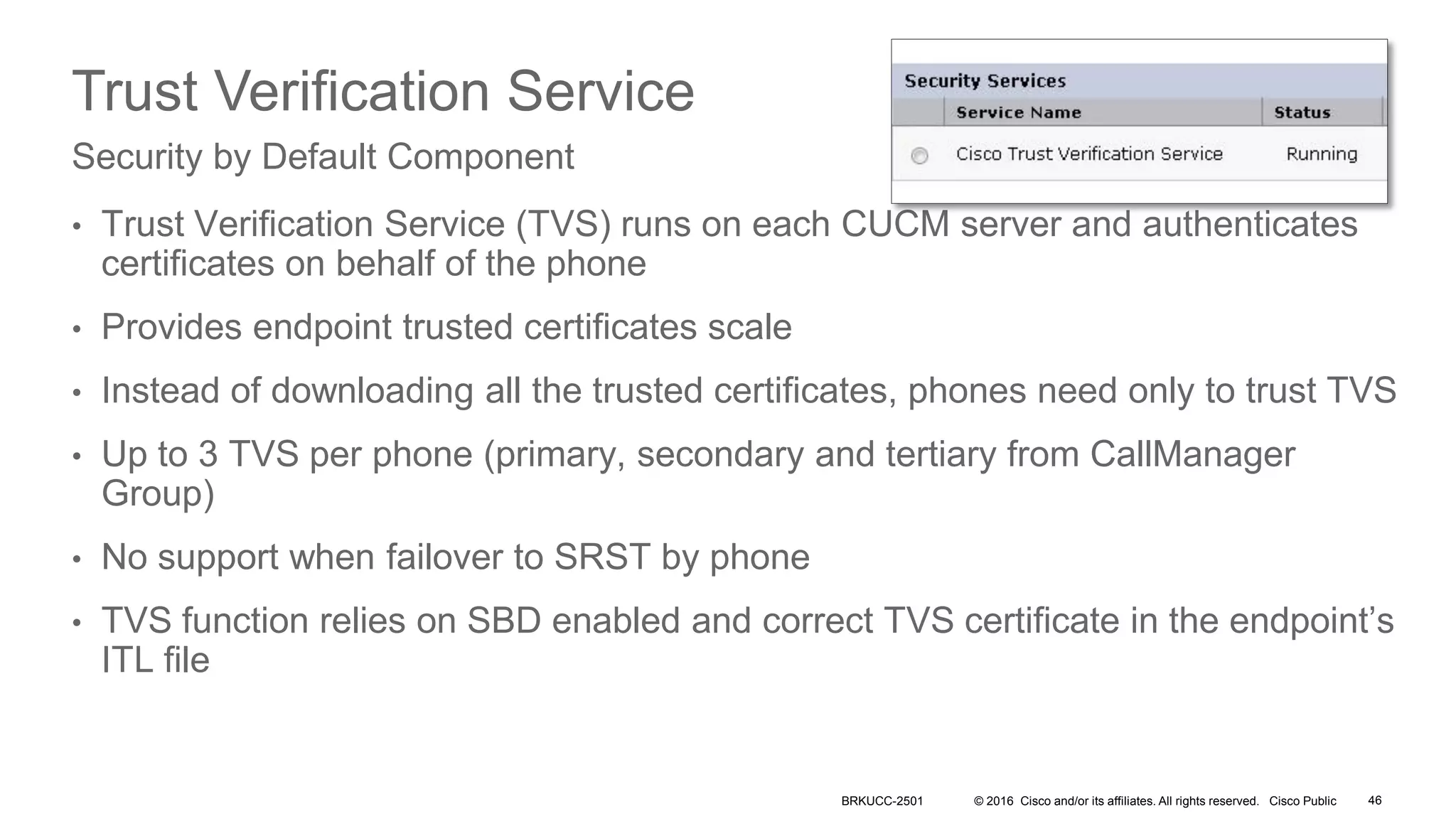
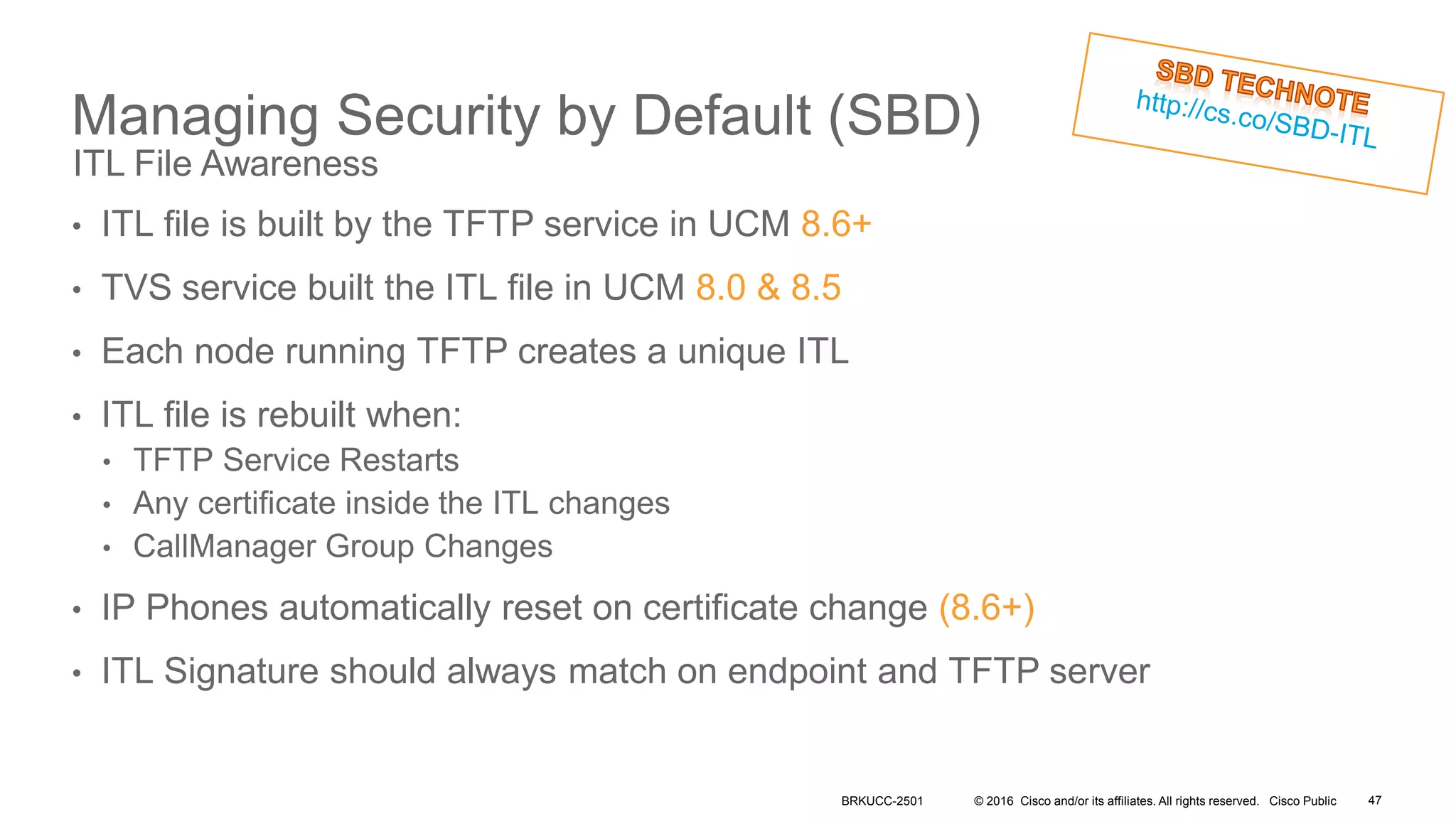
- The presentation also discusses CUCM release 11.5 security updates including encryption strengths that meet federal requirements and enhancements for certificate management.