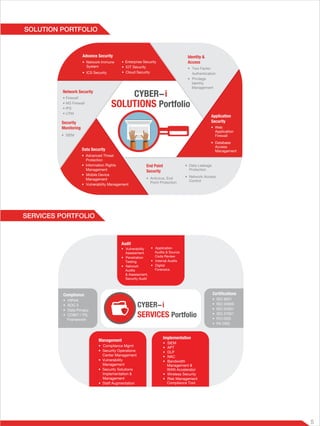
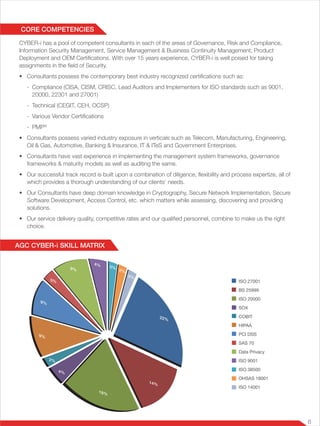
AGC Networks is a prominent global solution integrator providing customized business solutions to boost revenue, market penetration, and operational efficiency across multiple sectors. As a subsidiary of the Essar Group, AGC operates in 20 countries and offers comprehensive services in areas such as cyber security, unified communications, and enterprise applications. The company's Cyber-i services enhance security posture and compliance through flexible managed security solutions backed by extensive expertise and advanced threat intelligence.