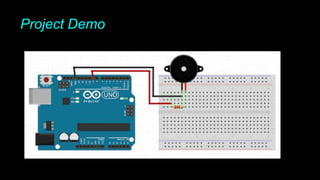
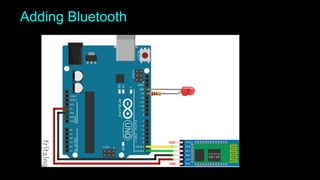
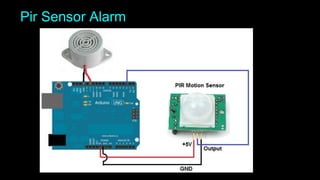
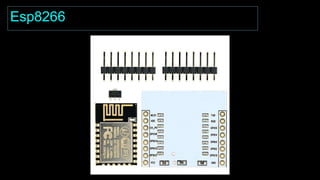
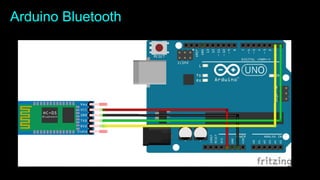
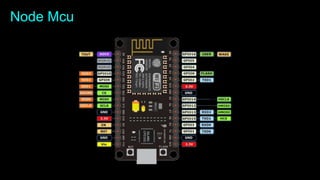
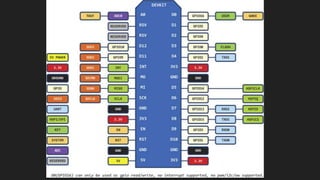
The document is an introduction to hardware hacking and the Internet of Things (IoT) by Mohsin Khan, who shares his journey and experience as a hardware hacker and penetration tester. It covers various topics including Arduino, Node MCU, and practical IoT projects, while also discussing hardware attacks and defenses. The document provides resources for beginners and emphasizes the importance of hands-on learning in hardware hacking.