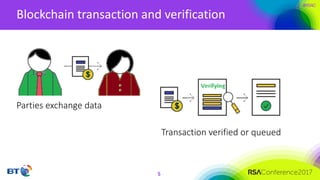
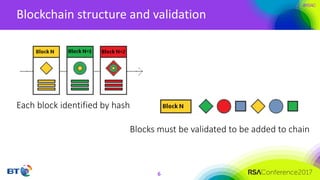
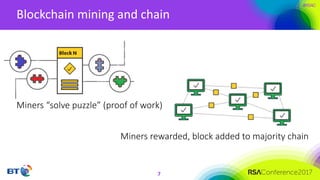
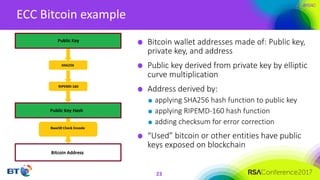
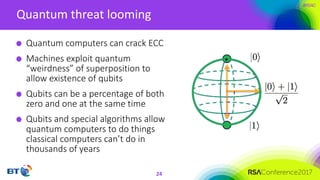
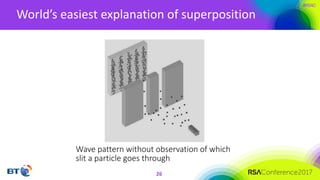
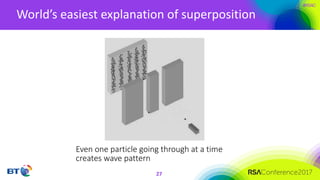
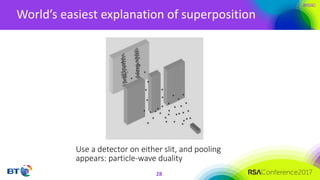
The document discusses the evolution and security challenges of blockchain technology, highlighting notable attacks and vulnerabilities since Bitcoin's inception in 2008. It outlines various forms of attacks on blockchain infrastructure, code, and wallets, as well as the looming threat of quantum computing to current encryption methods. Recommendations for enhancing blockchain security, including prioritizing testing and considering post-quantum solutions, are emphasized for organizations developing or using blockchain applications.