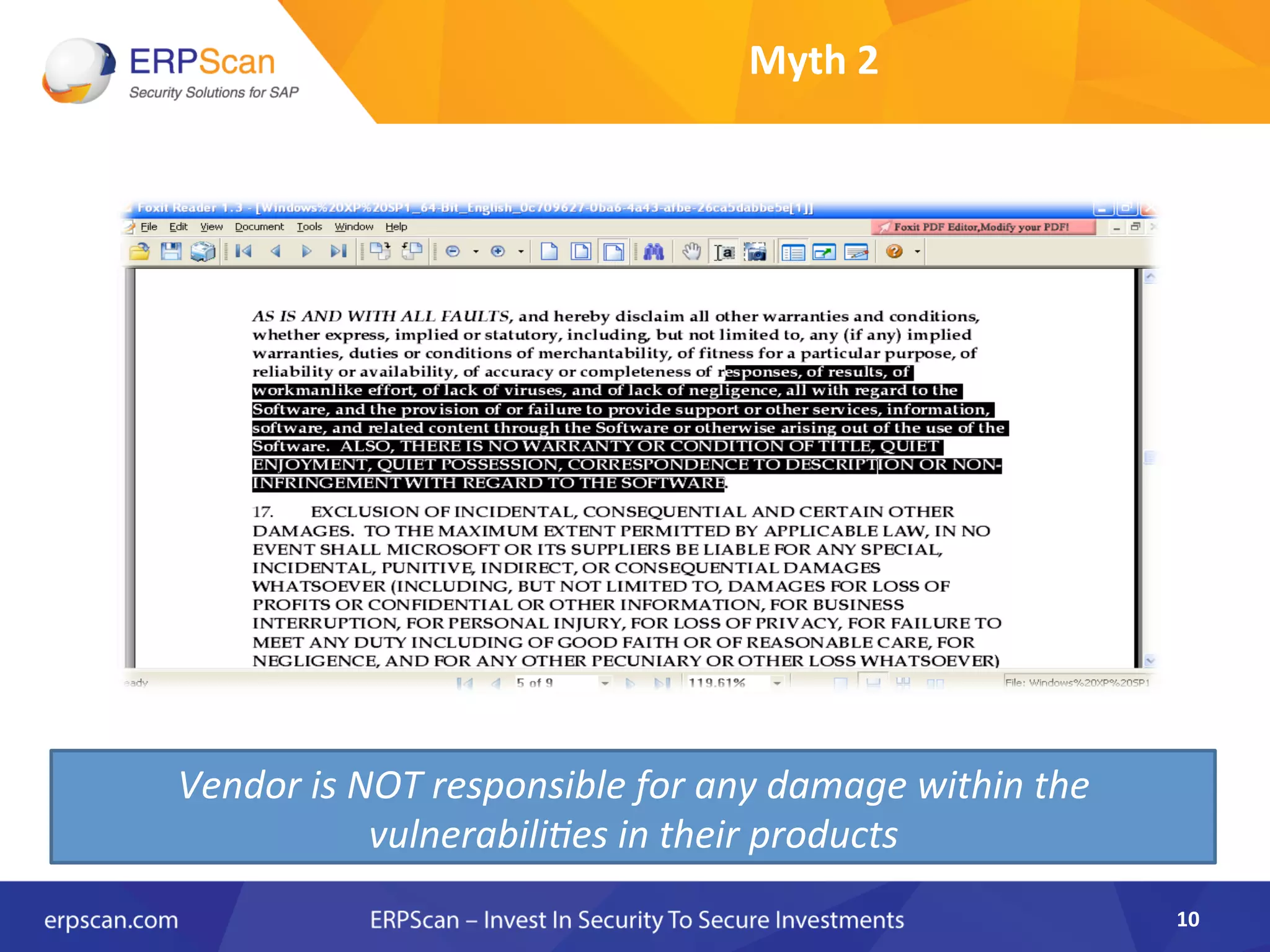
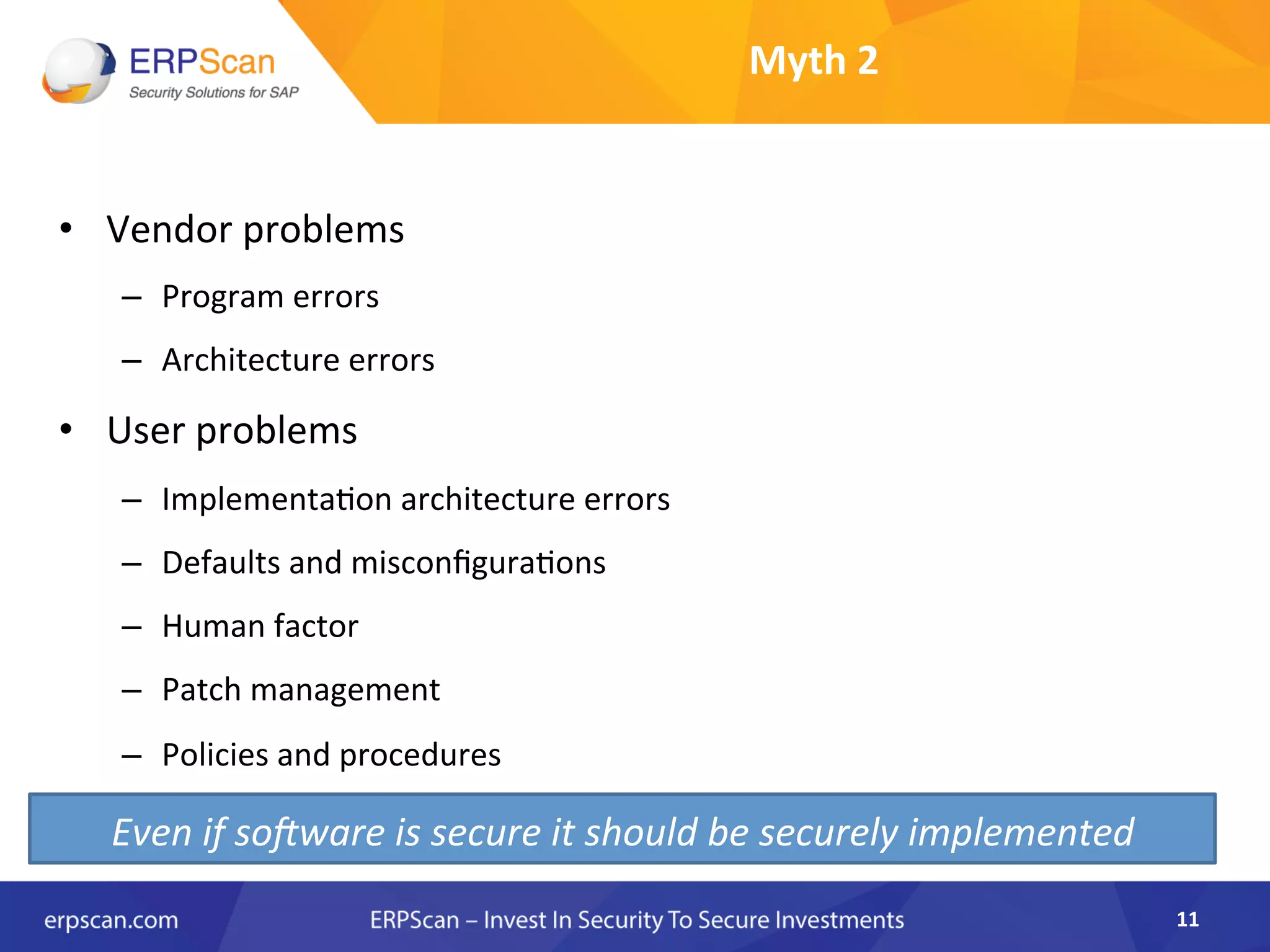
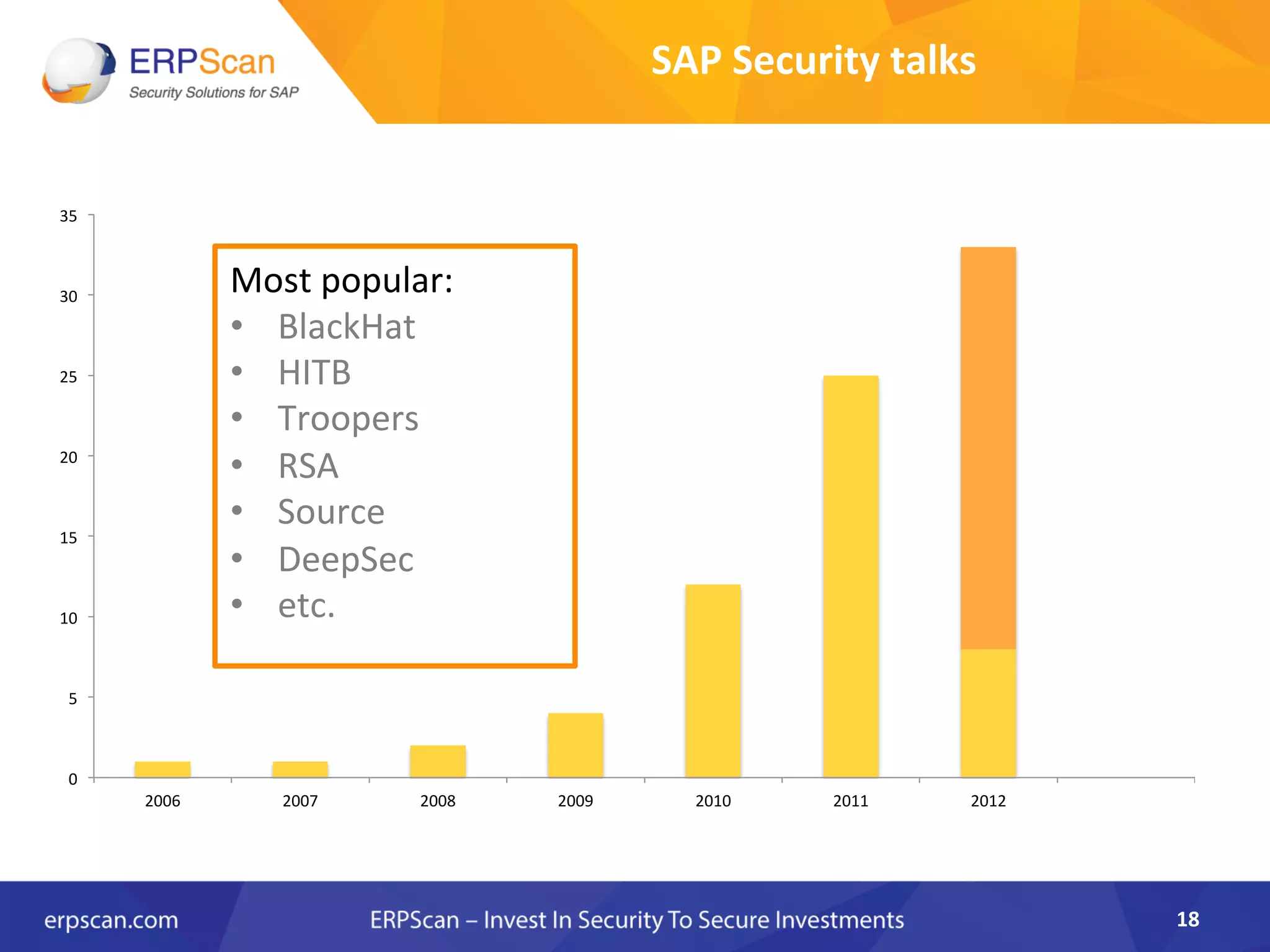
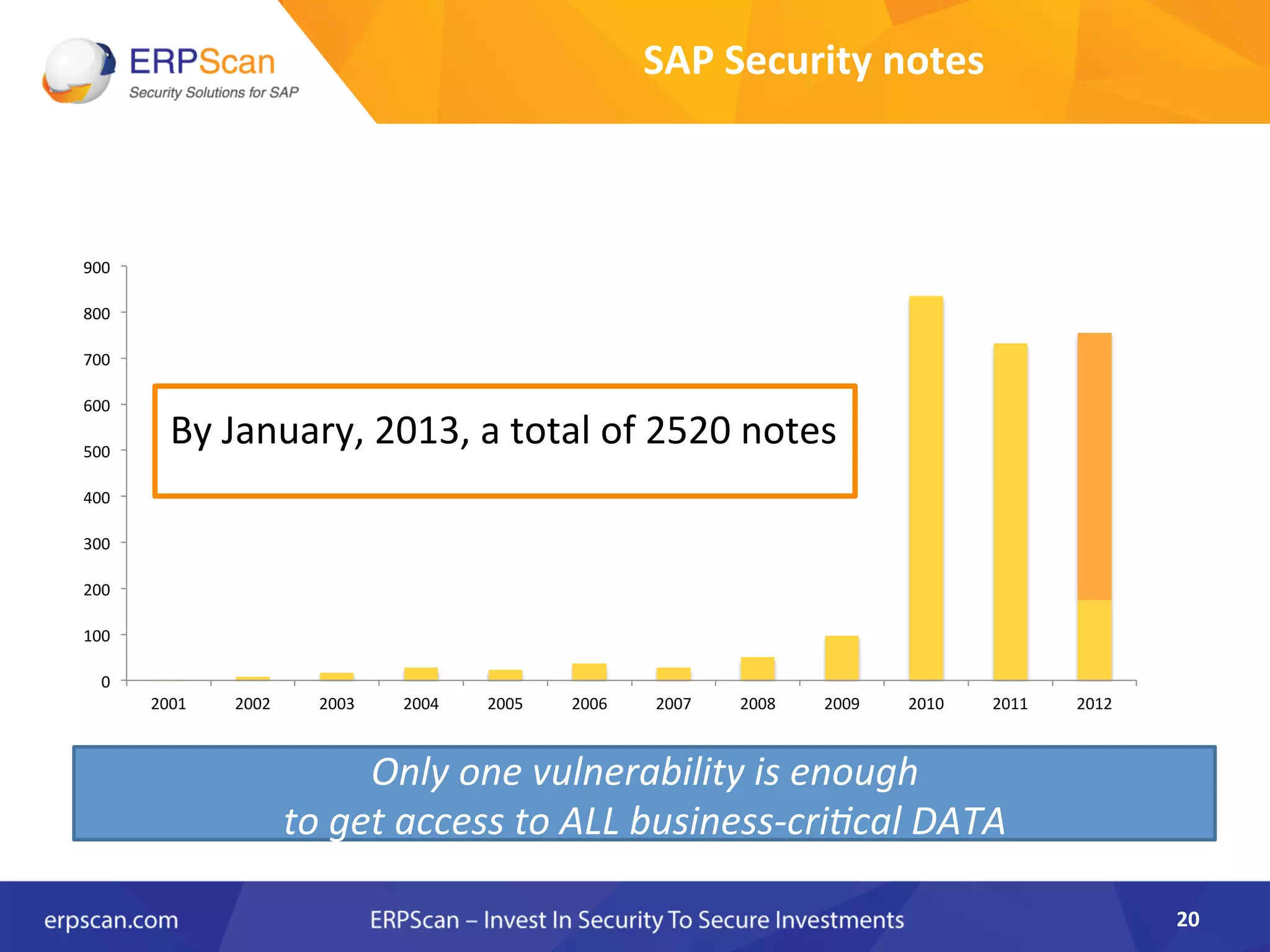
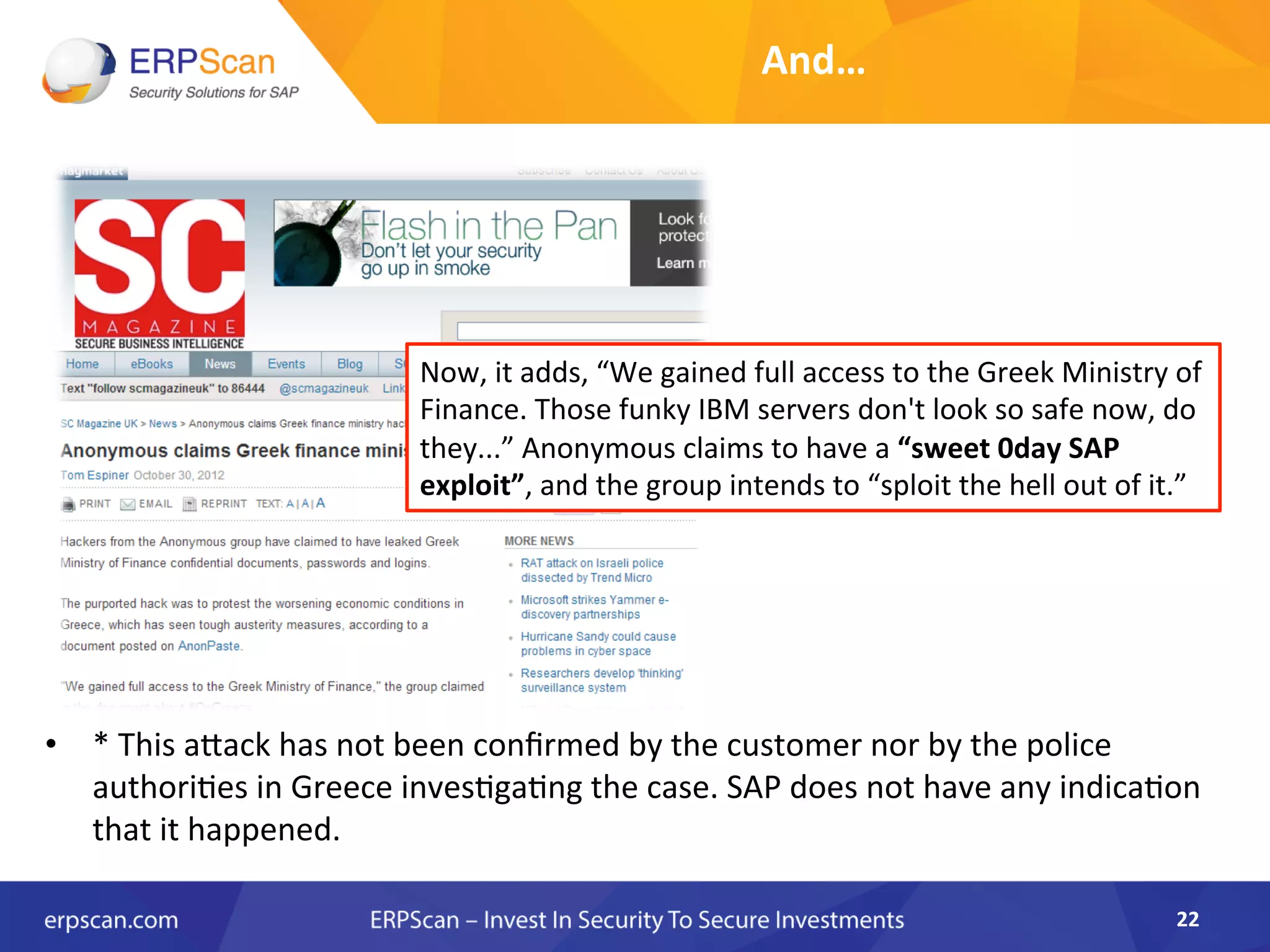
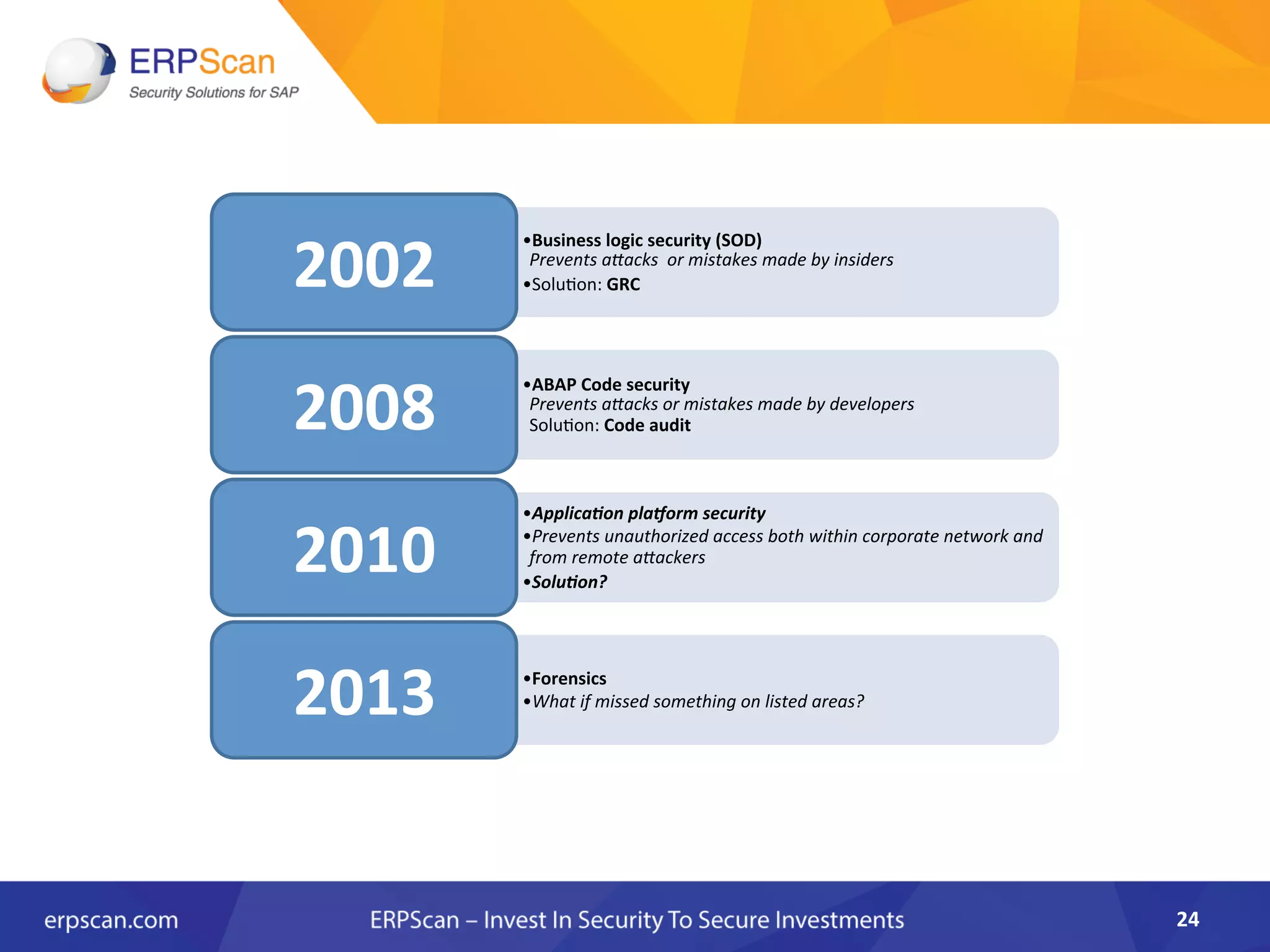
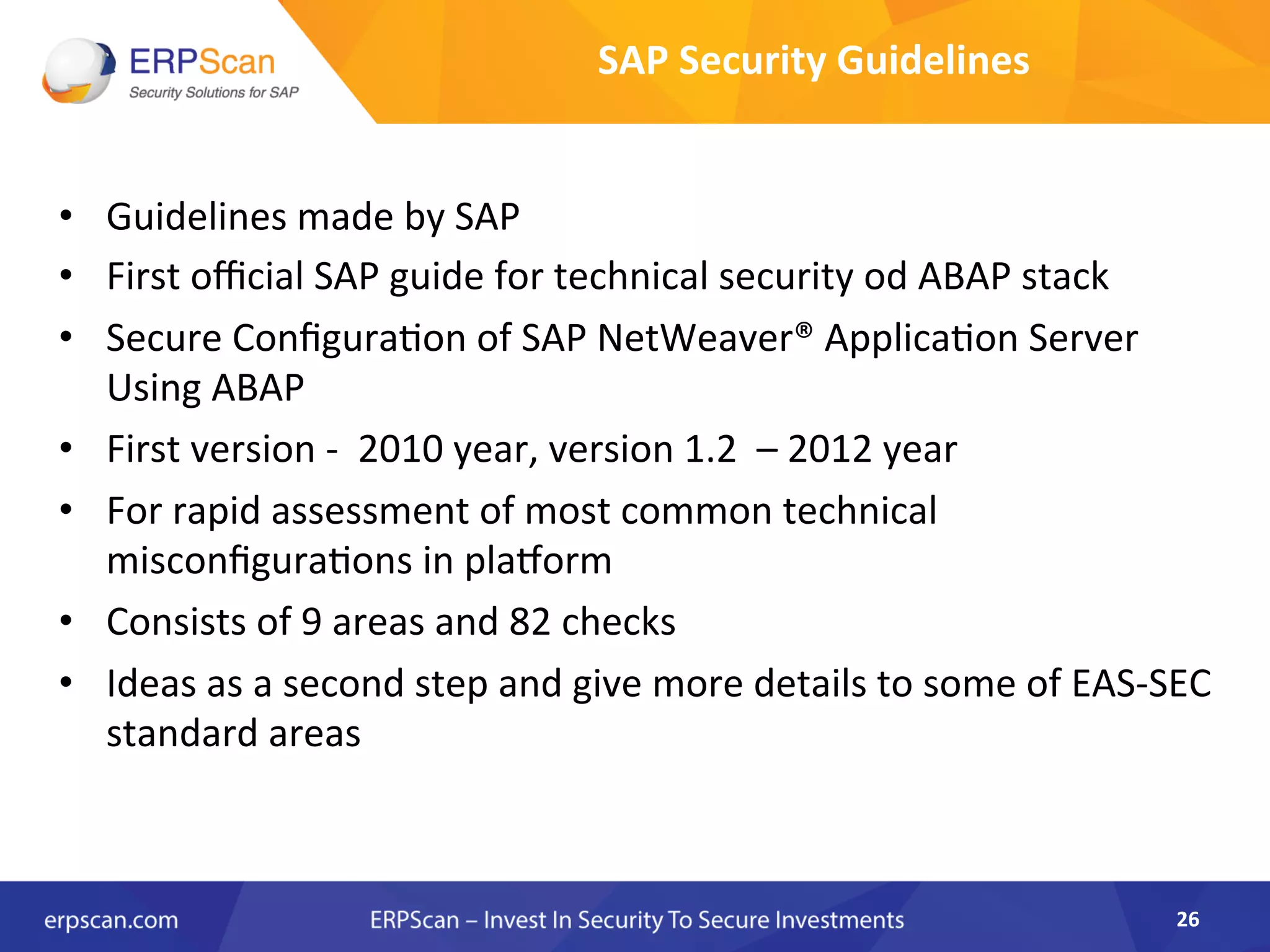
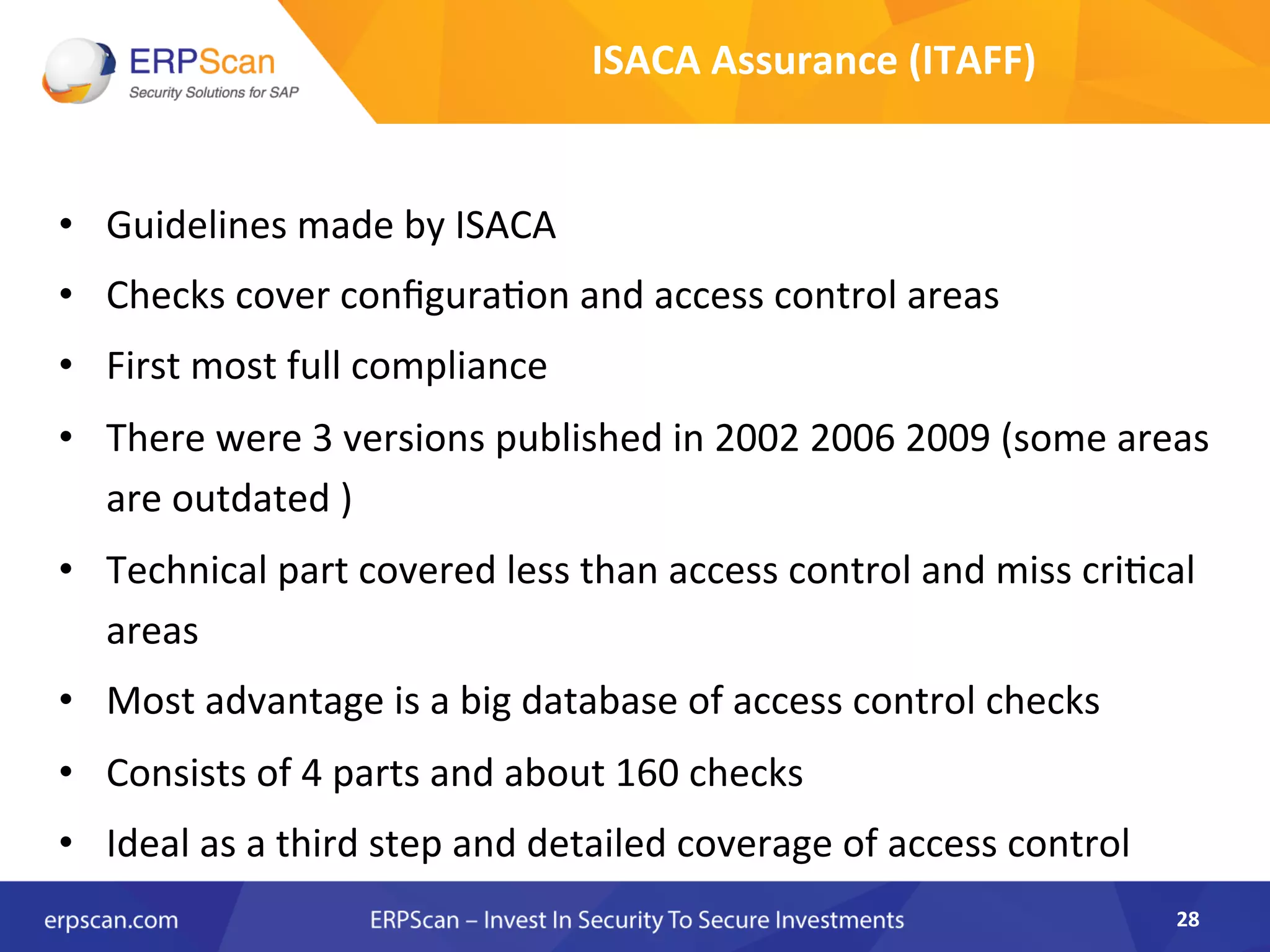
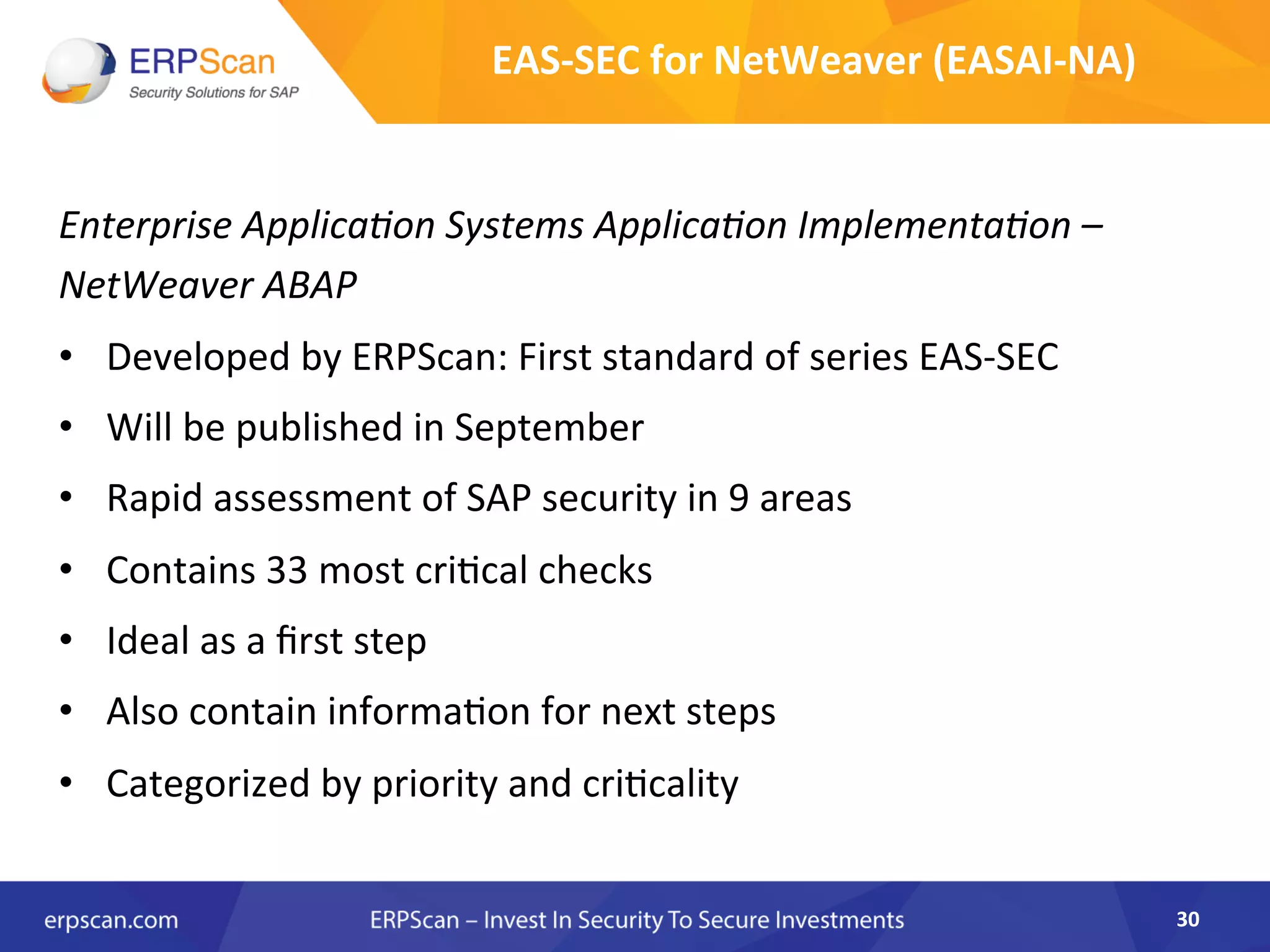
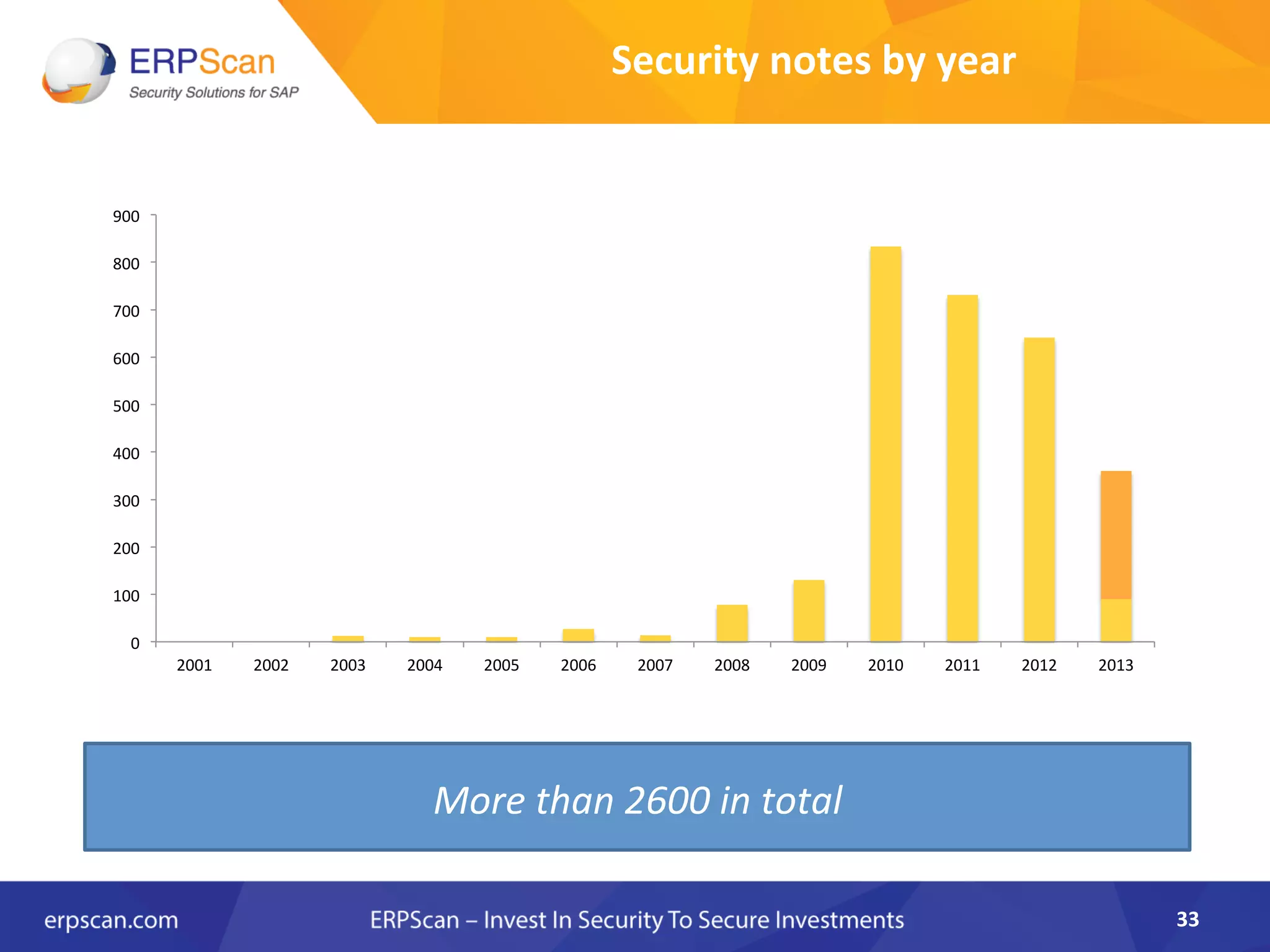
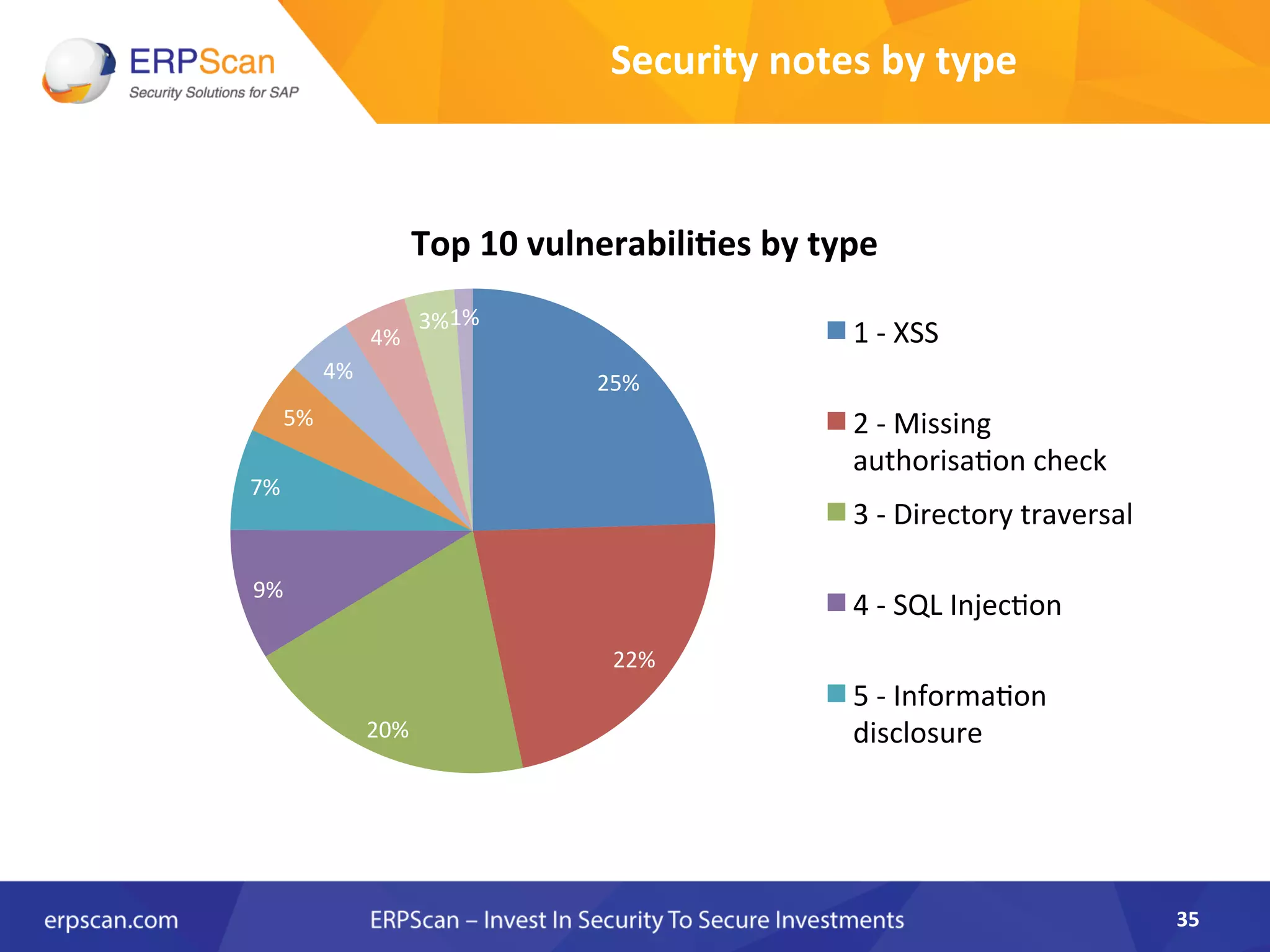
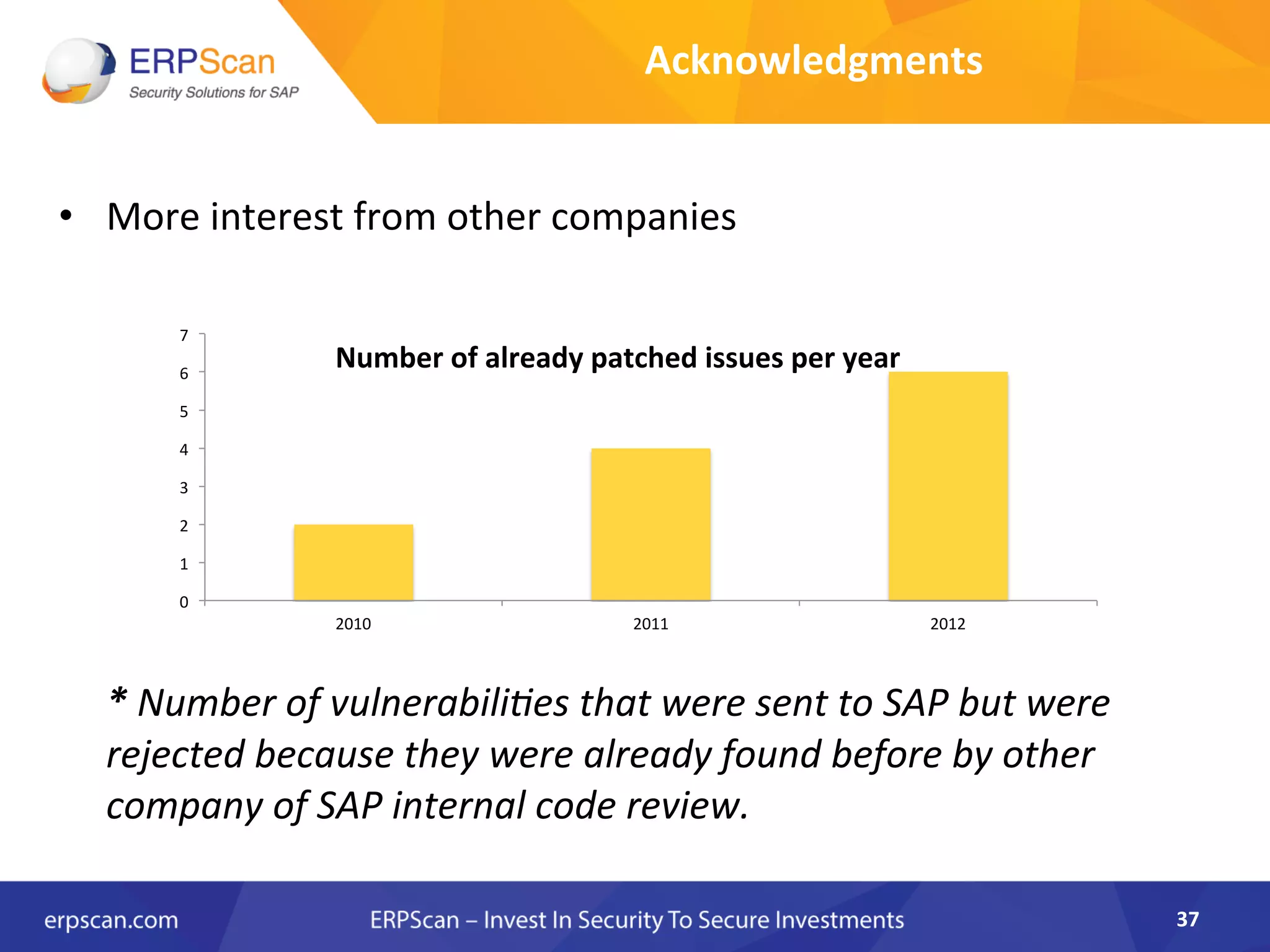
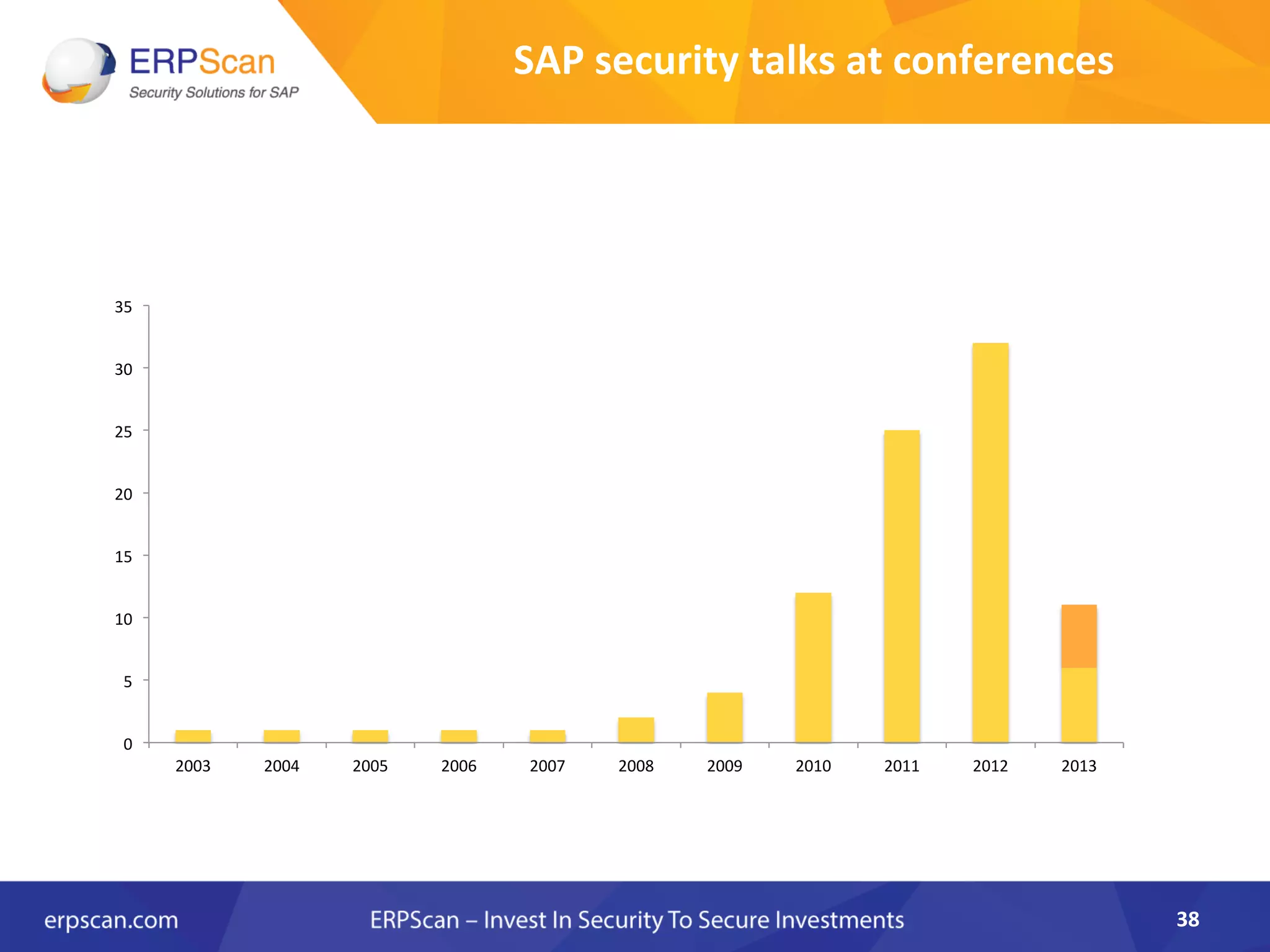
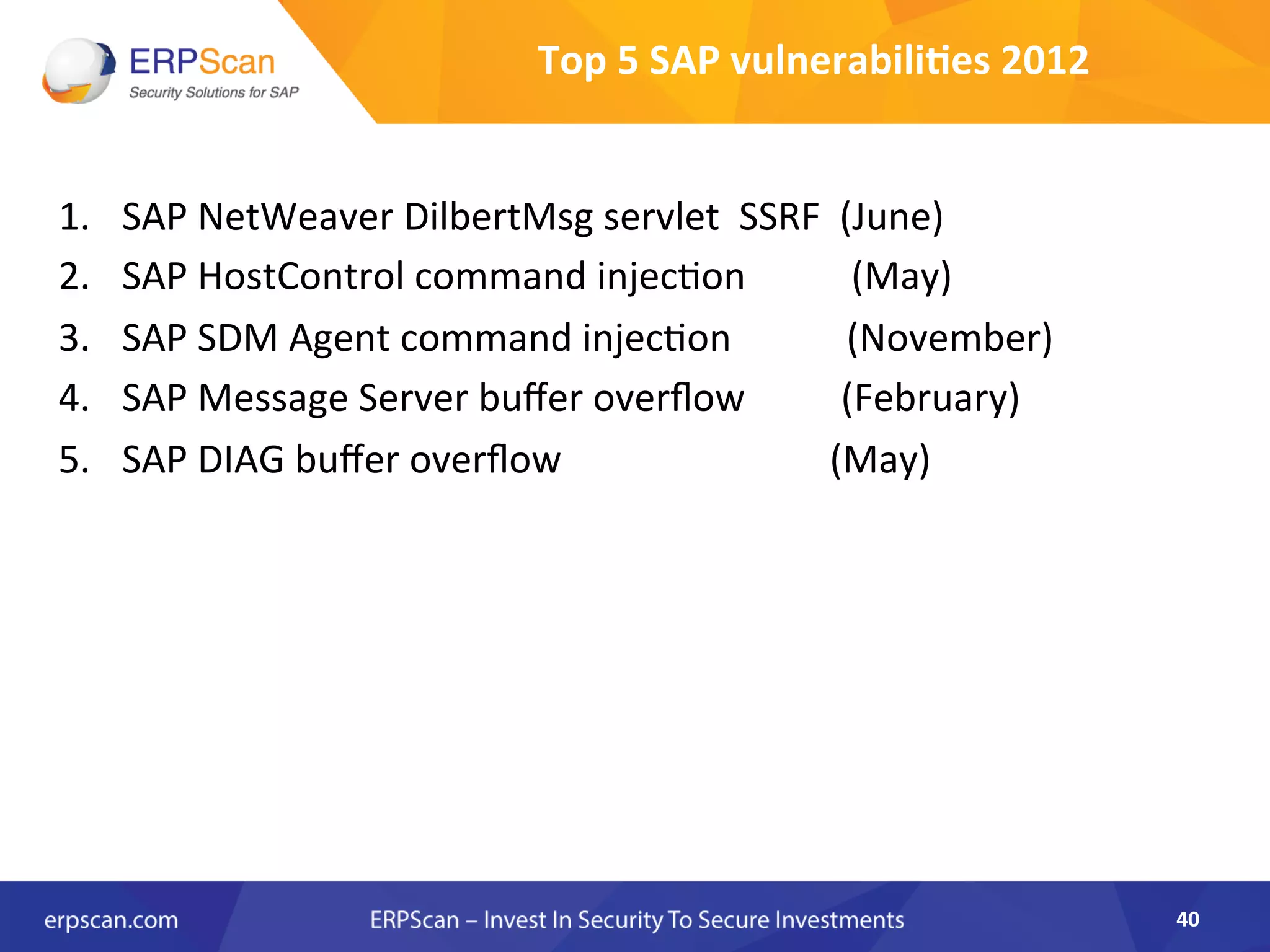
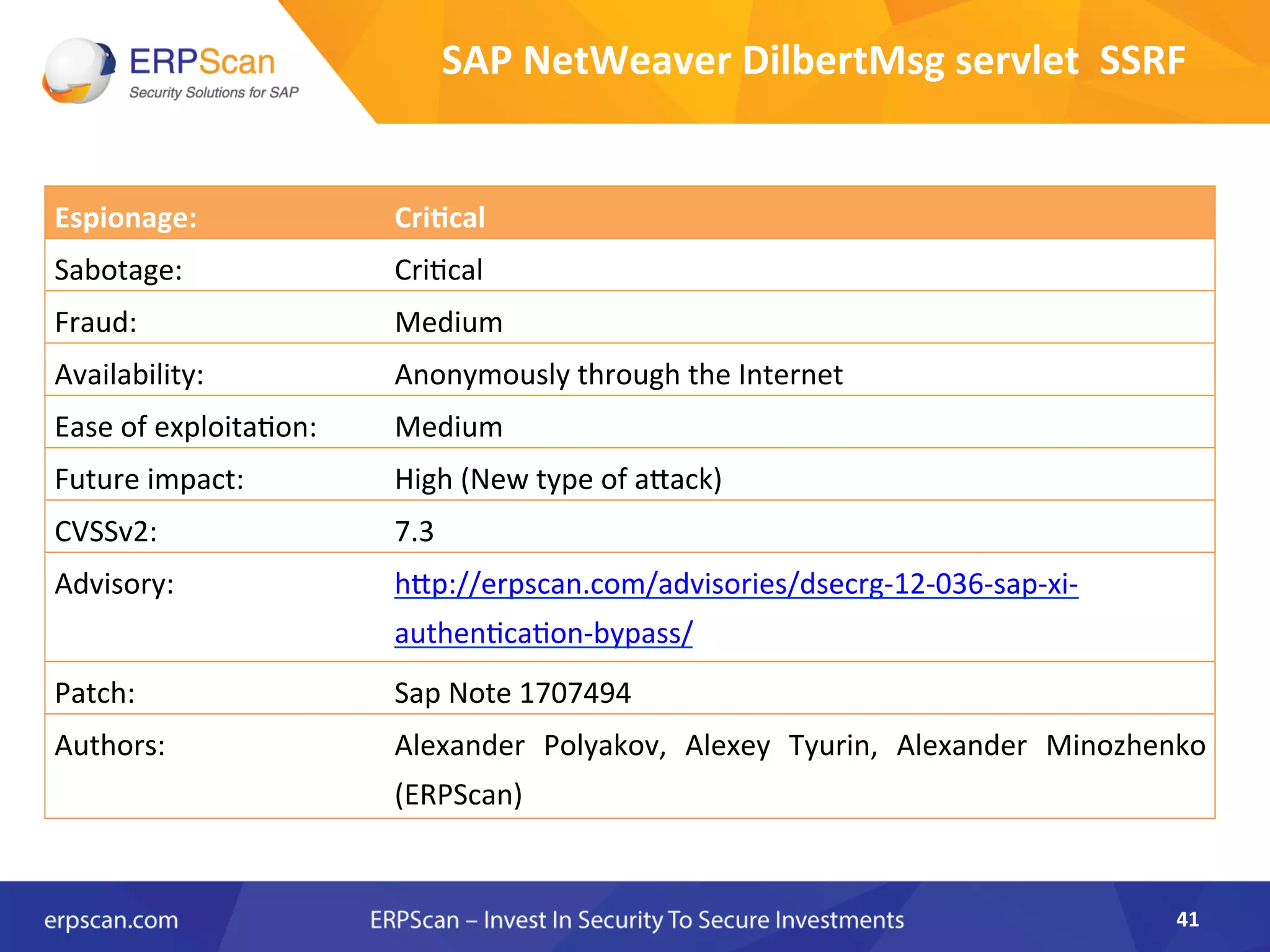
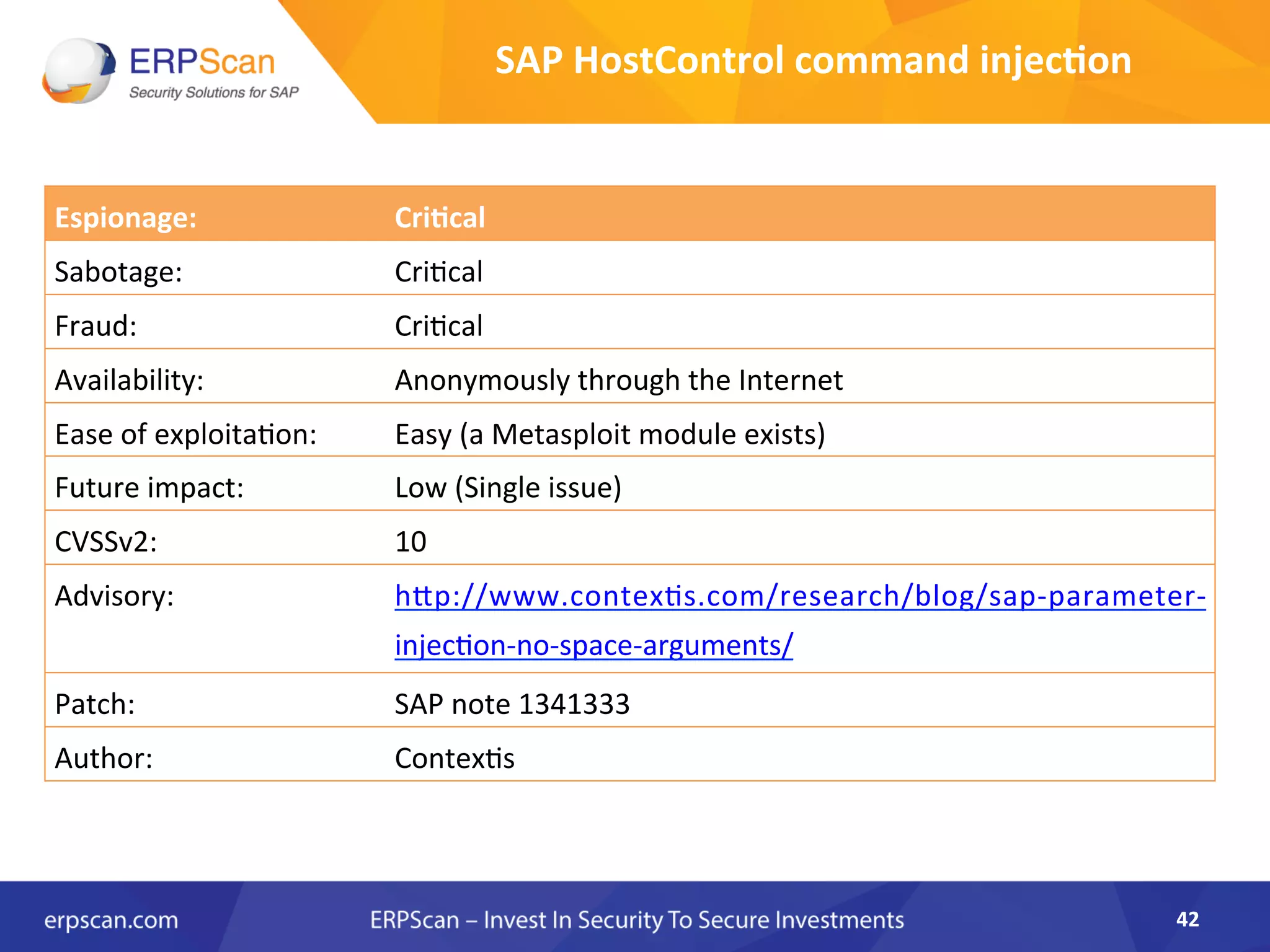
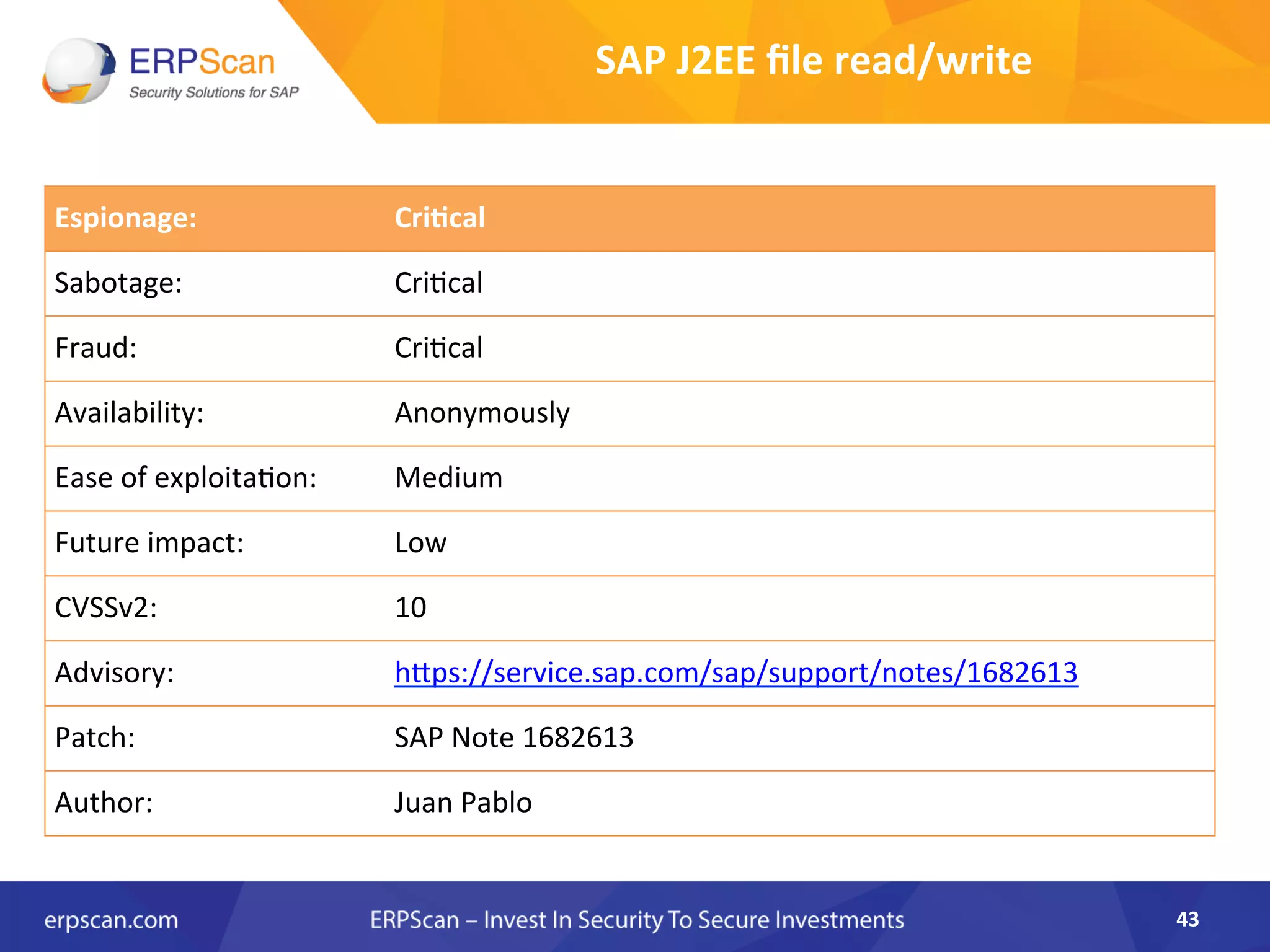
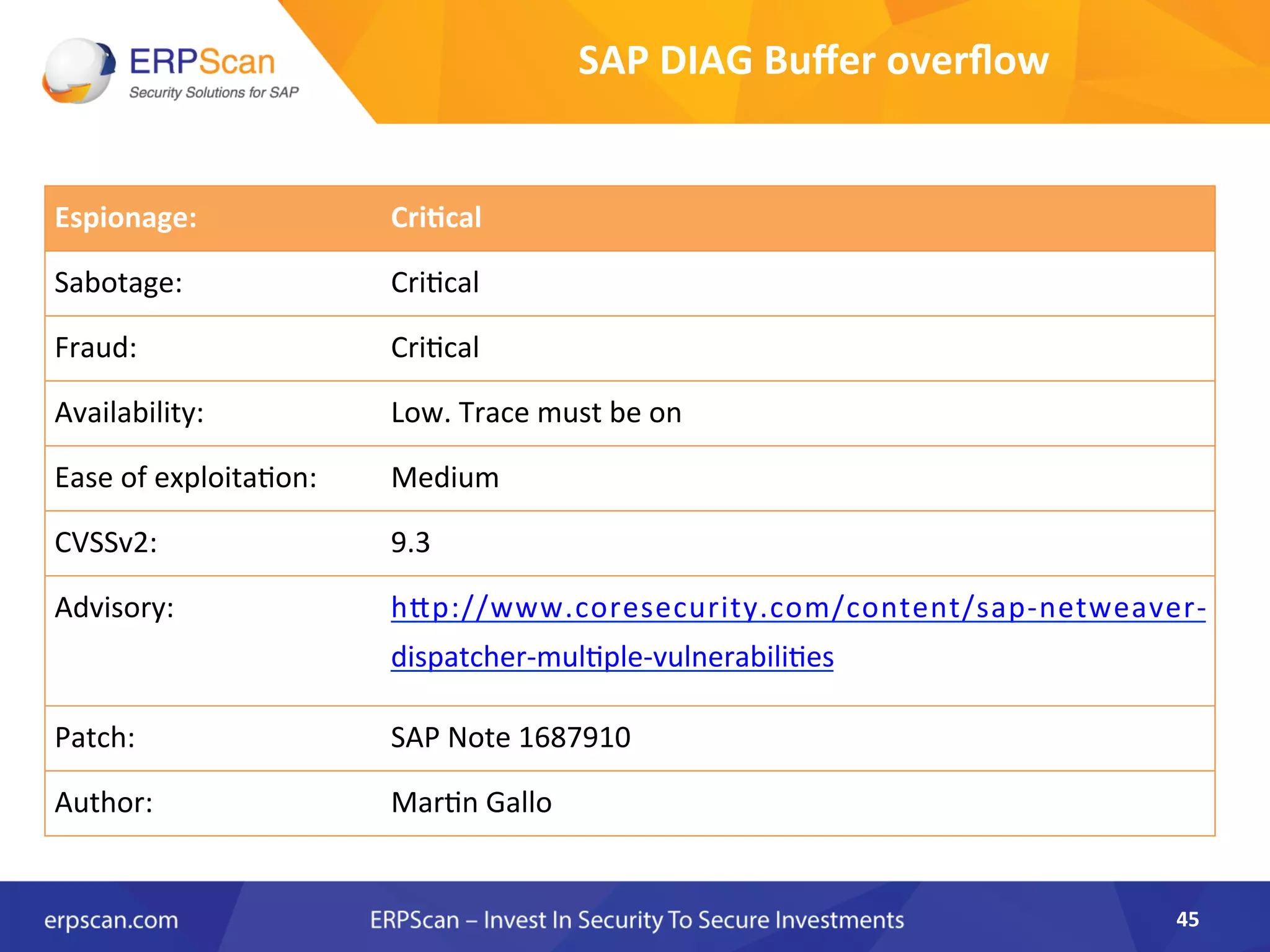
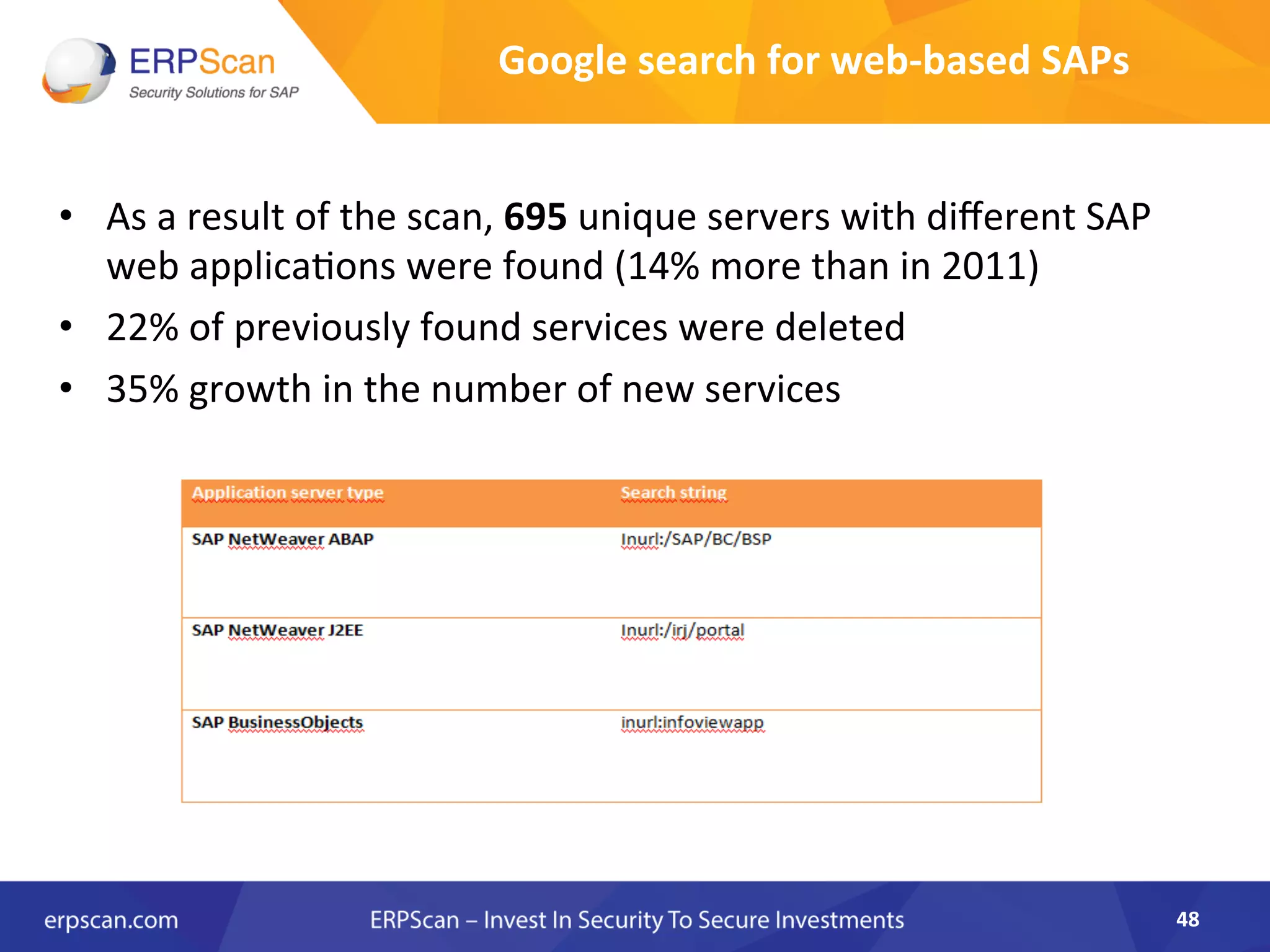
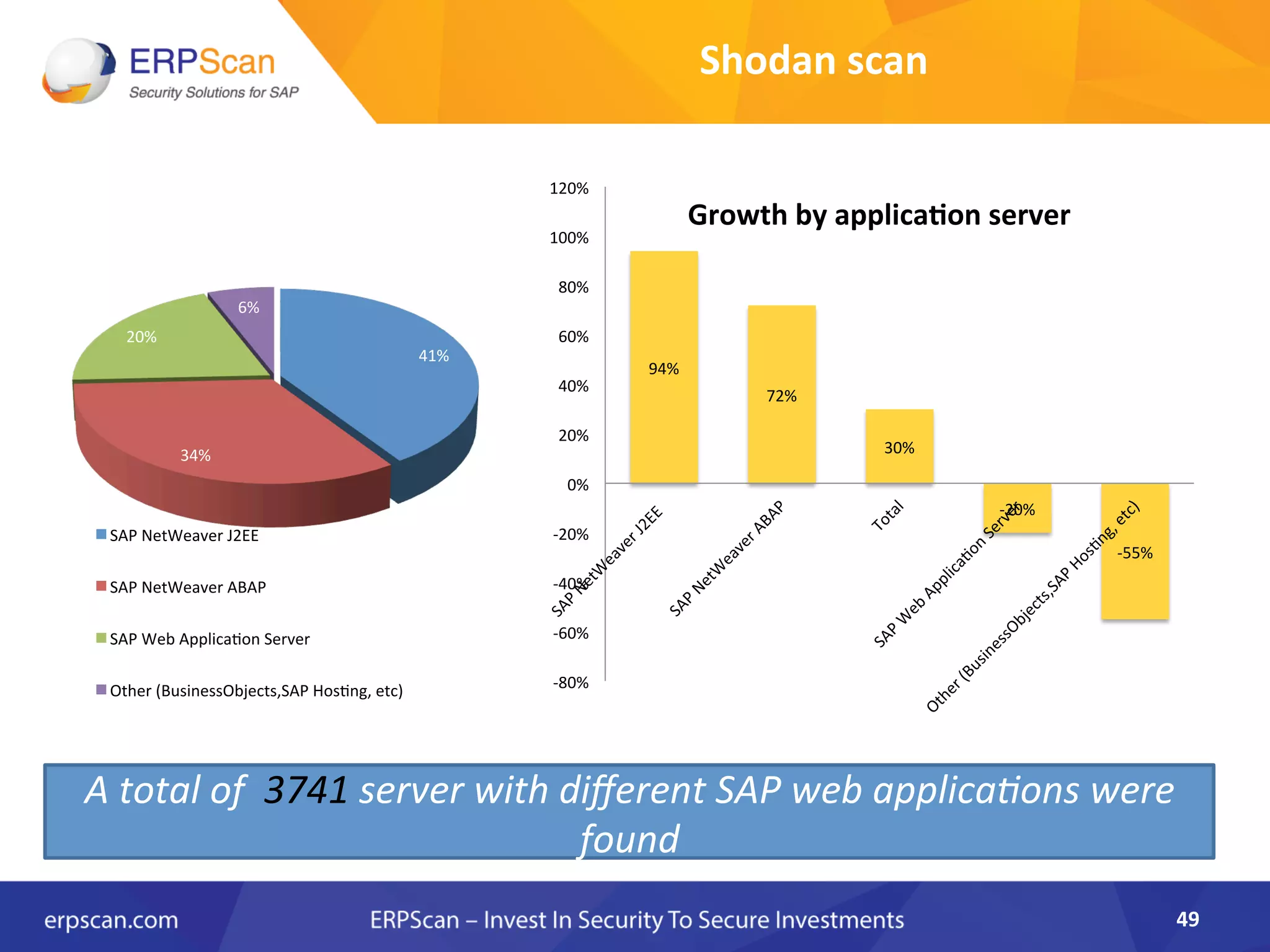
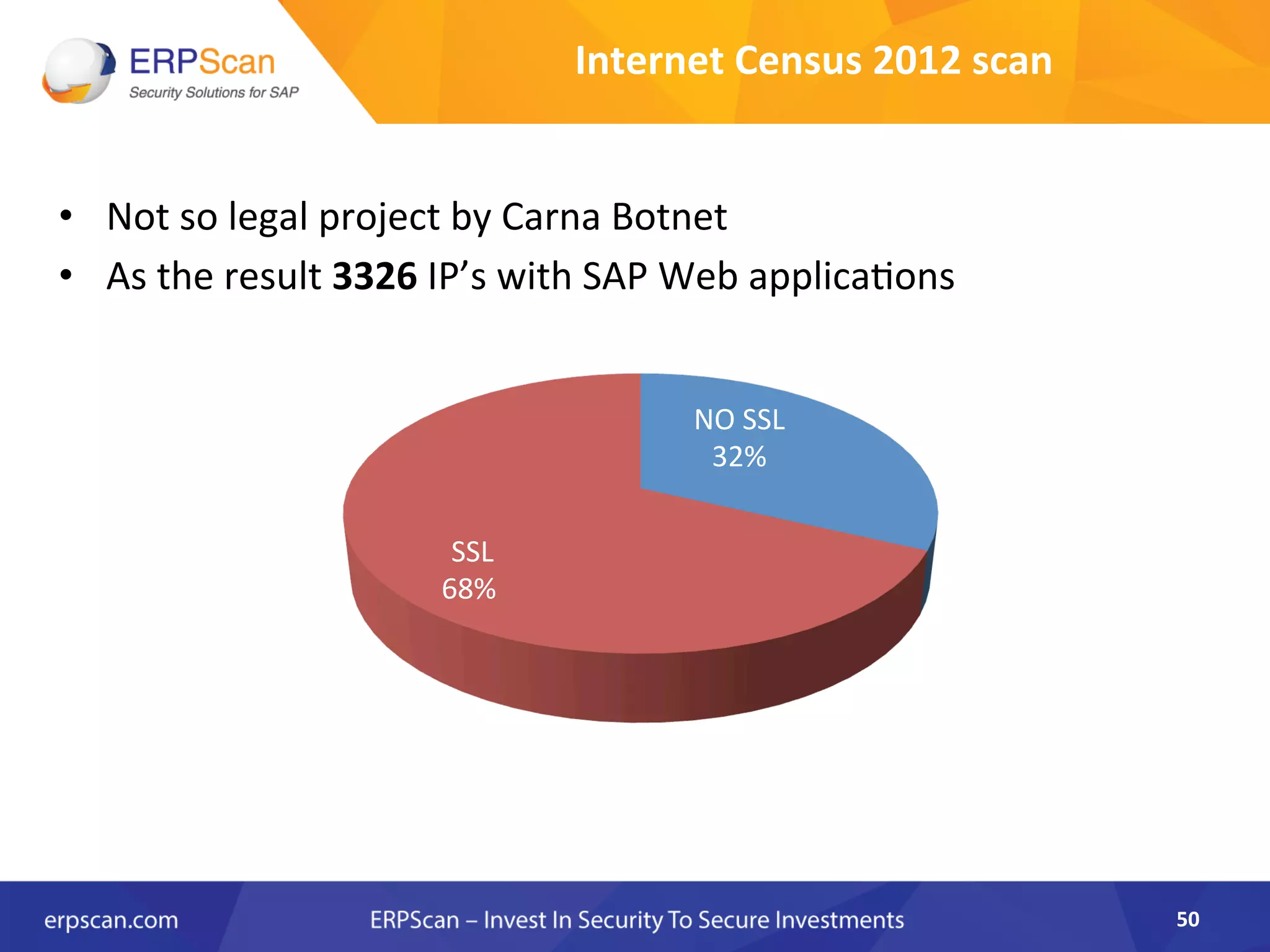
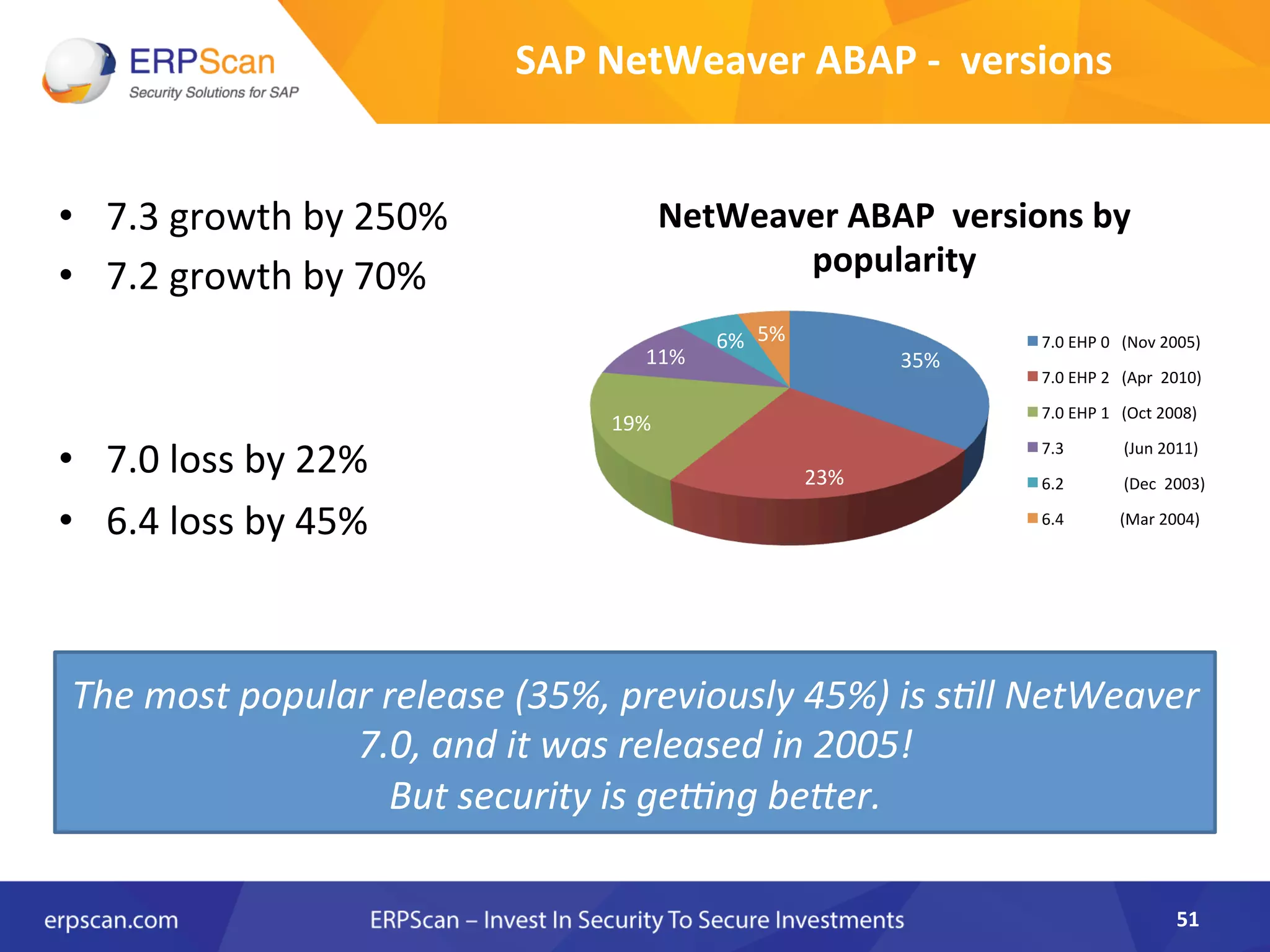
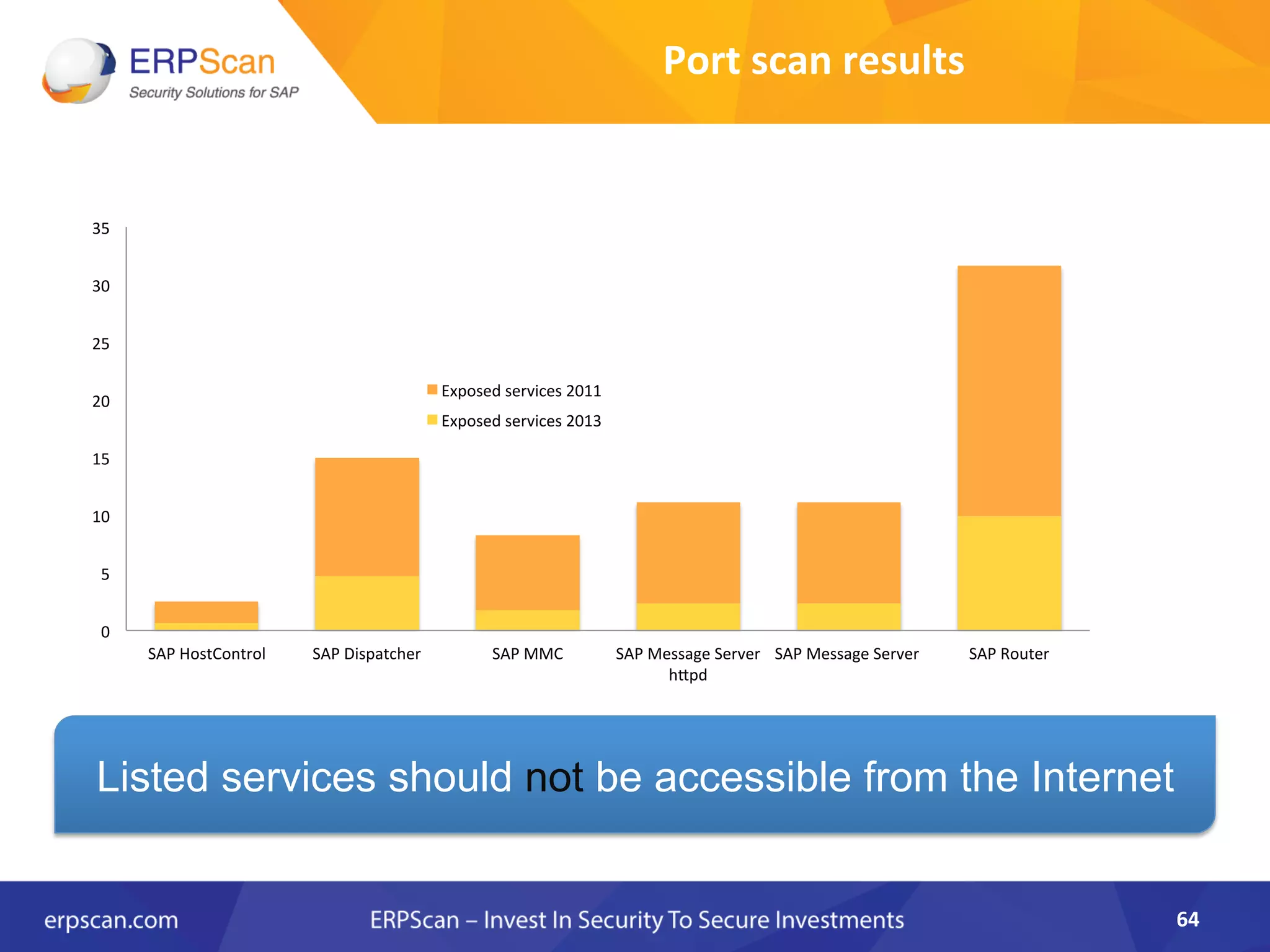
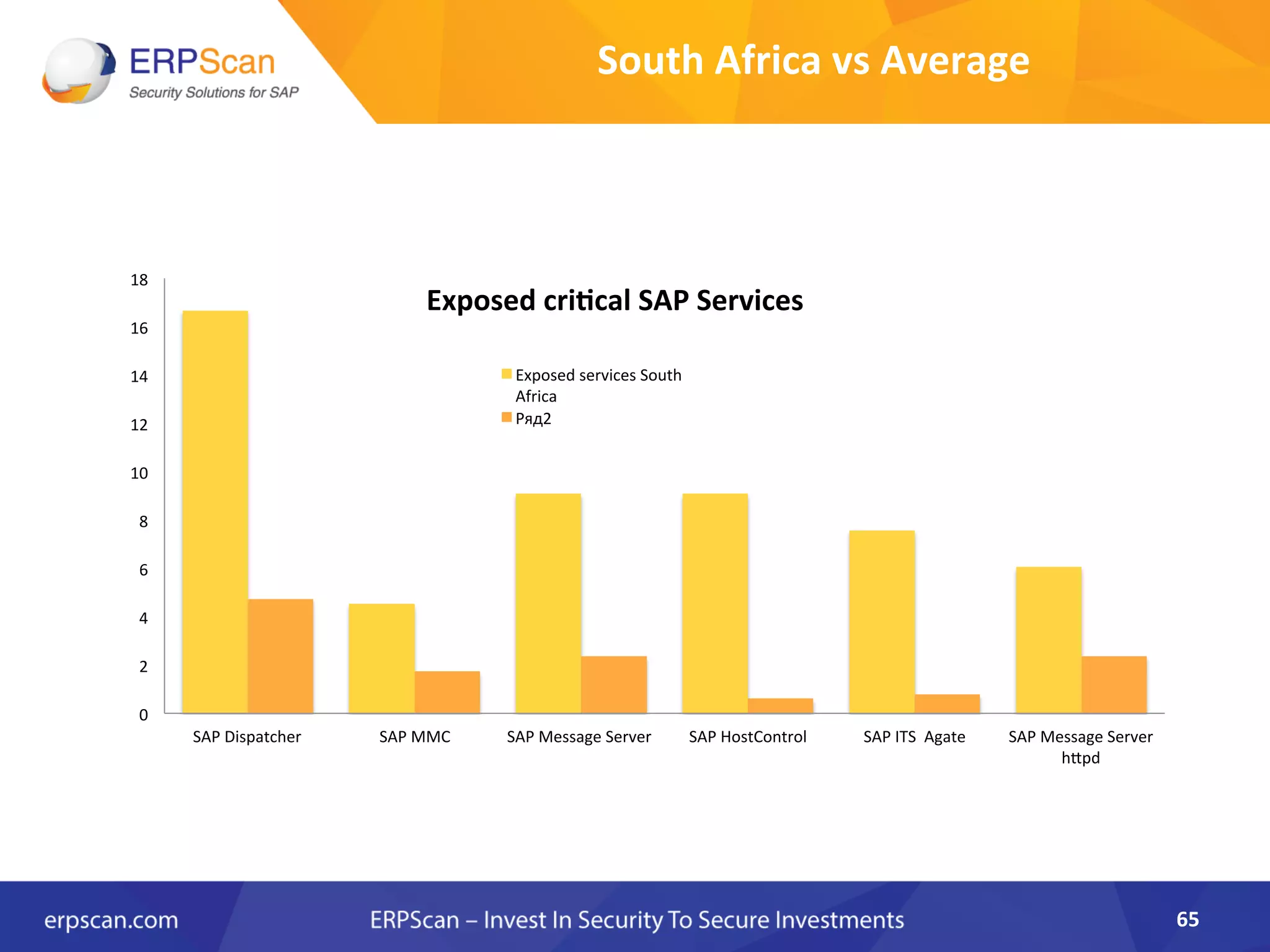
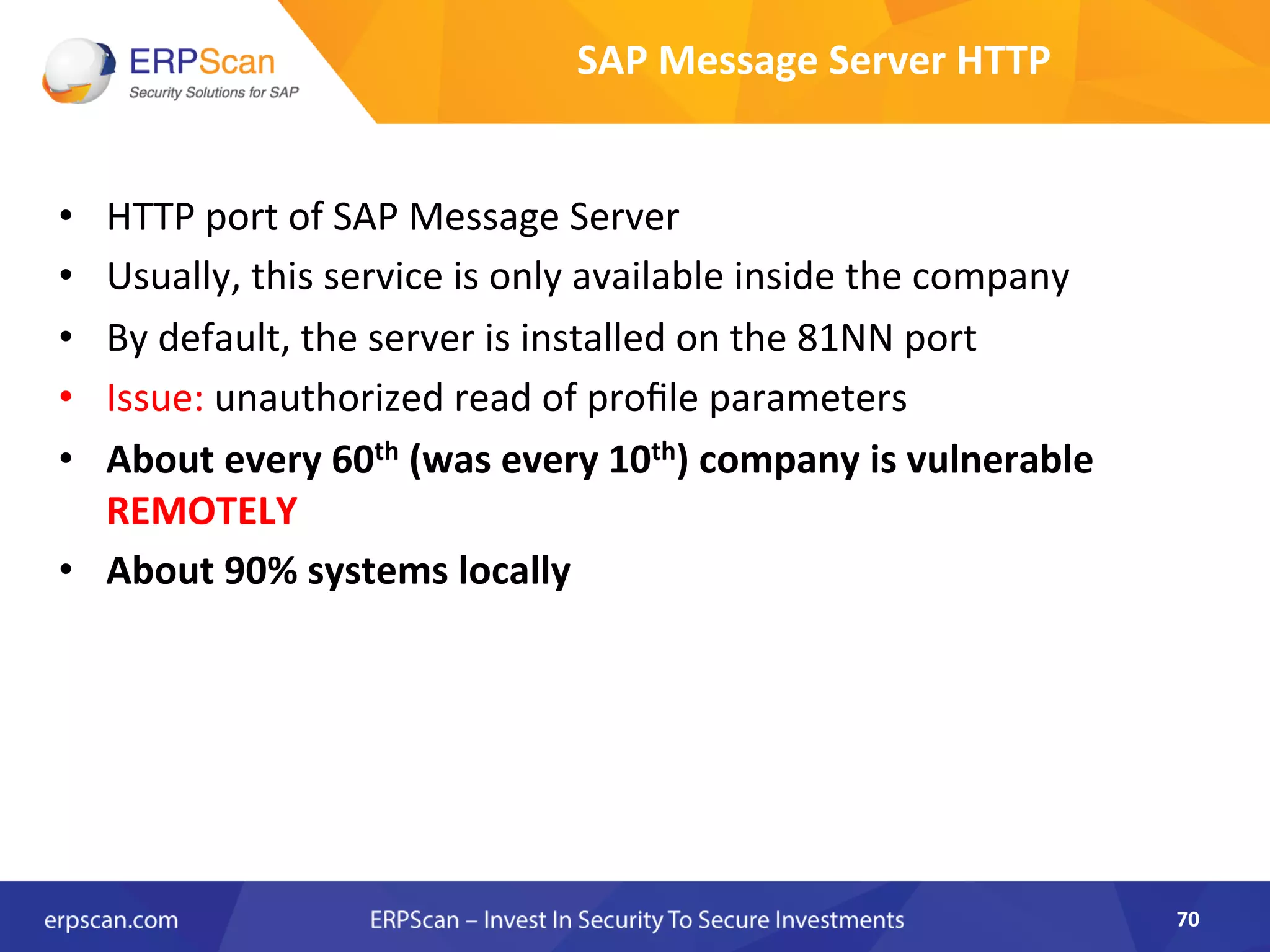
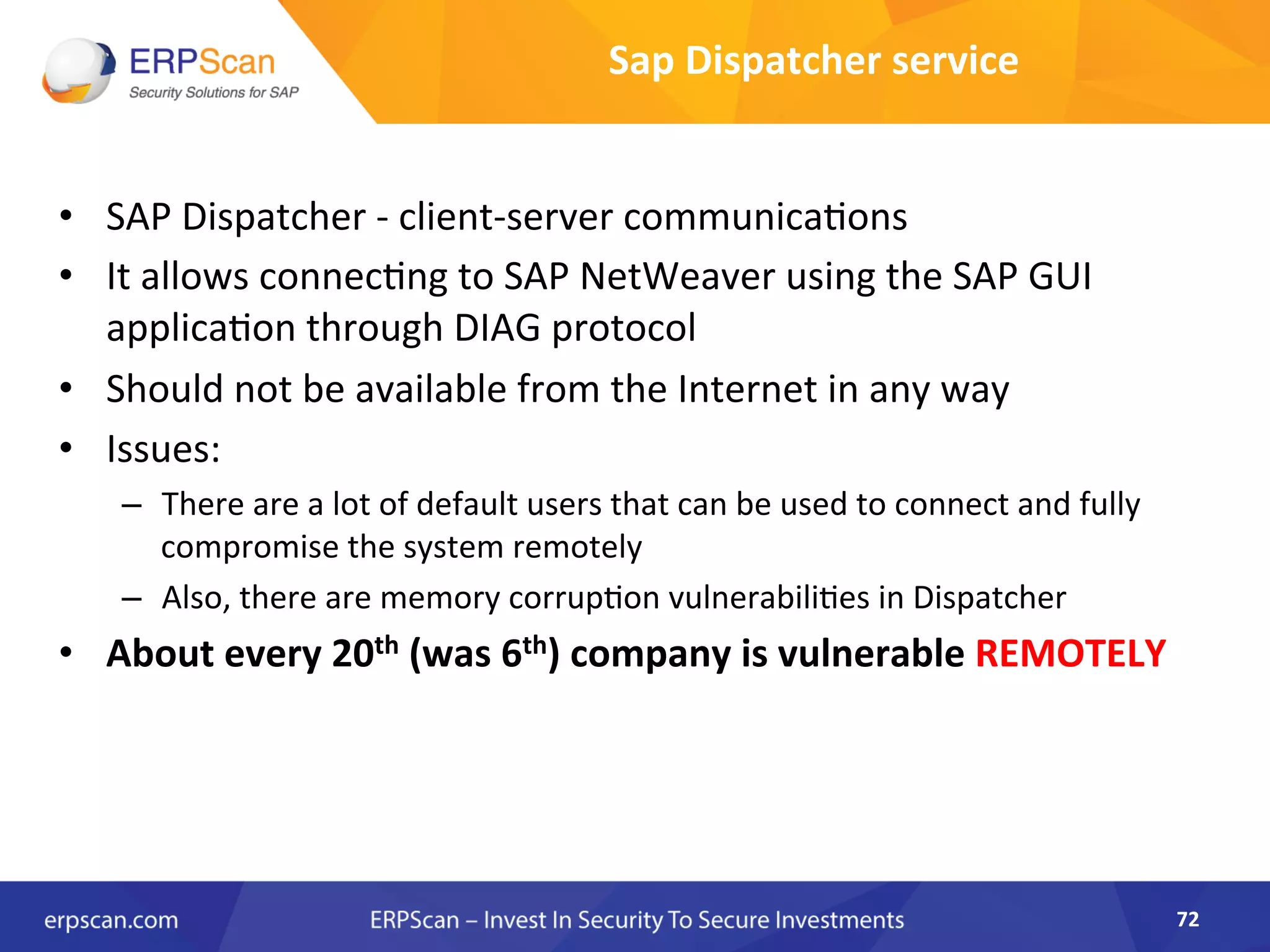
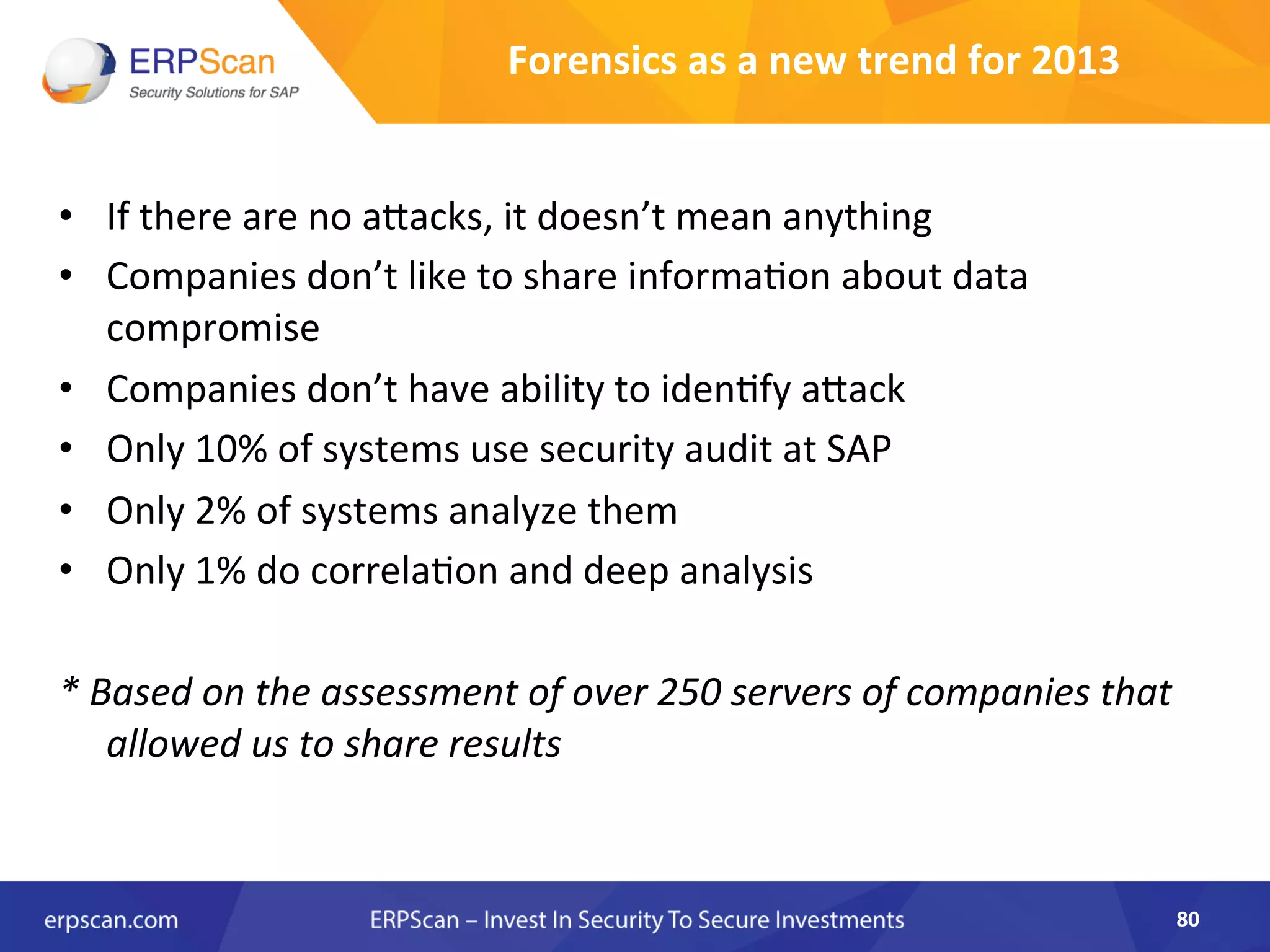
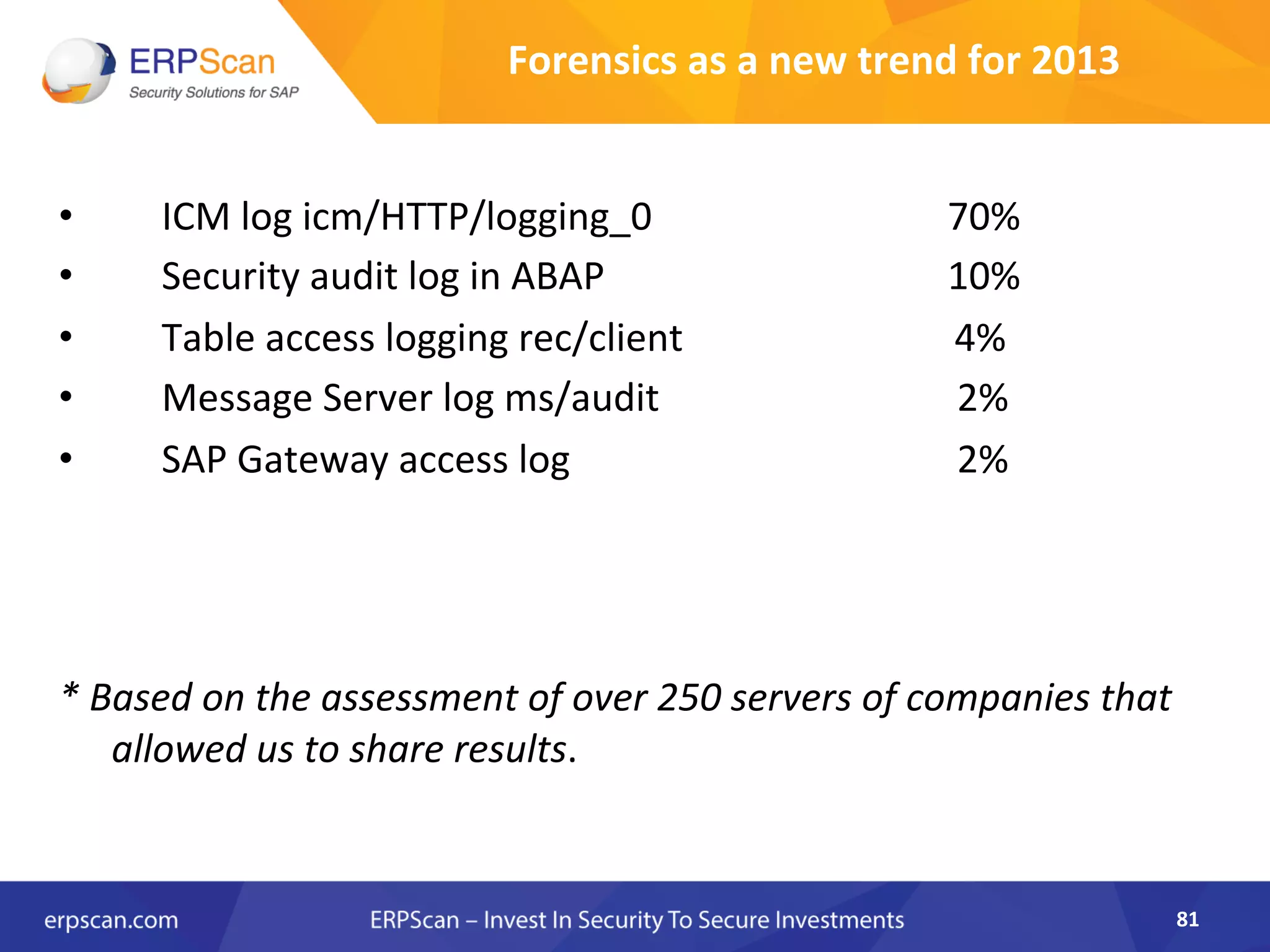
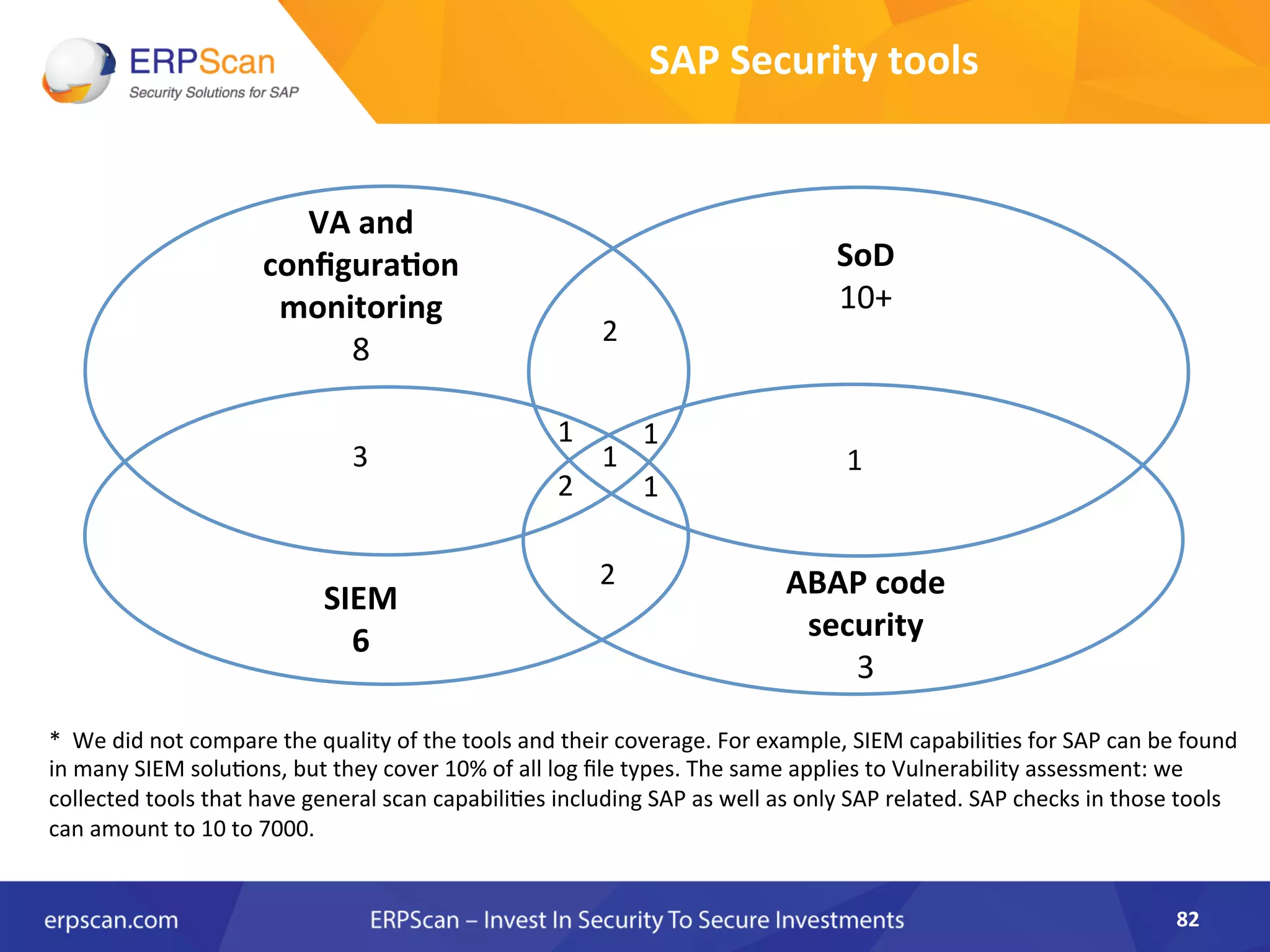
The document discusses the critical importance of security in SAP systems, highlighting common vulnerabilities, myths about ERP security, and best practices for protecting these business applications against cyber threats. It emphasizes that many businesses are unaware of the extent to which their ERP systems can be targeted, and that security should not rely solely on software solutions but must encompass comprehensive strategies including network access controls and proper implementation. Future trends, statistics on vulnerabilities, and specific solutions aimed at improving SAP security are also outlined.