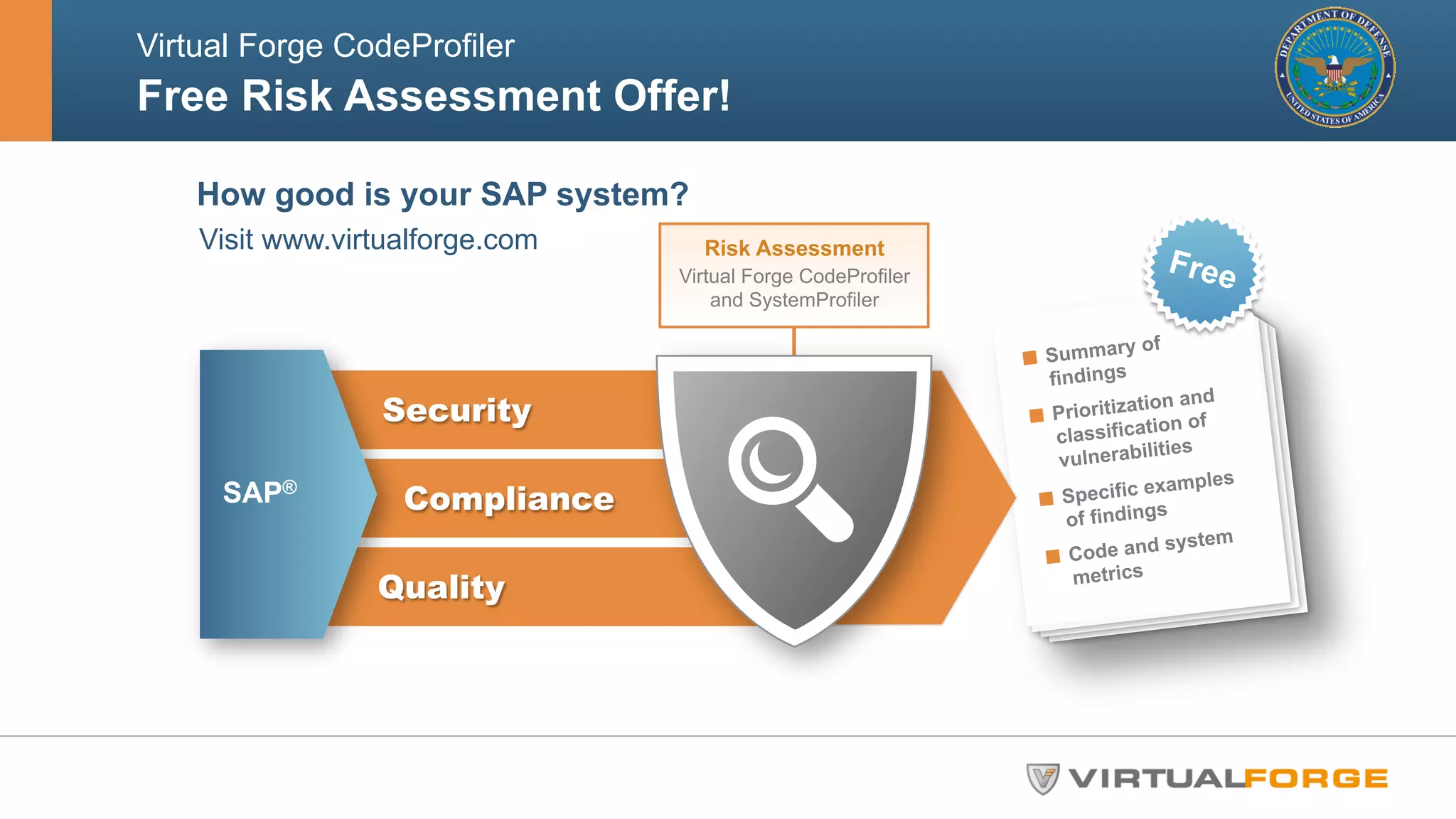
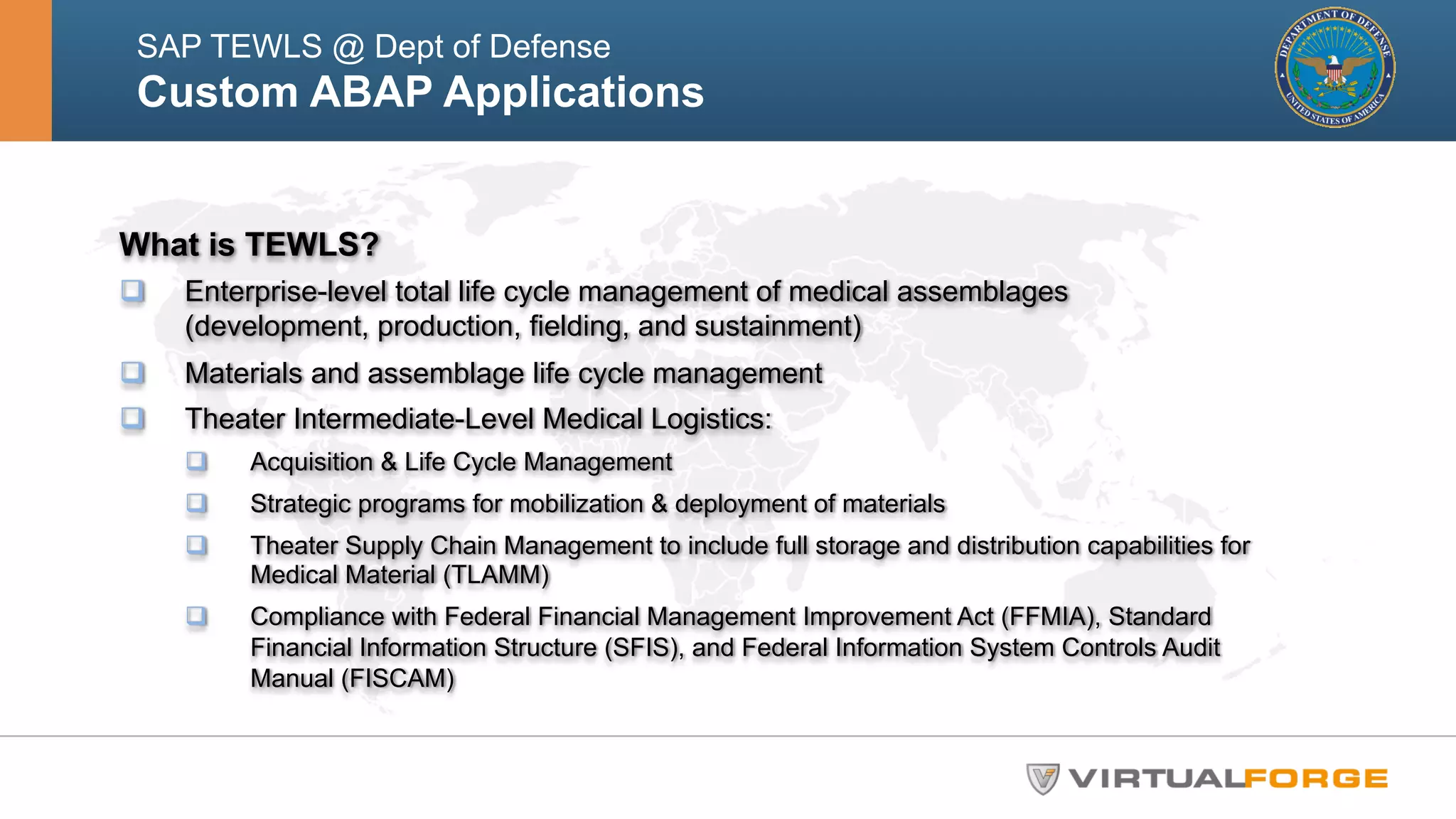
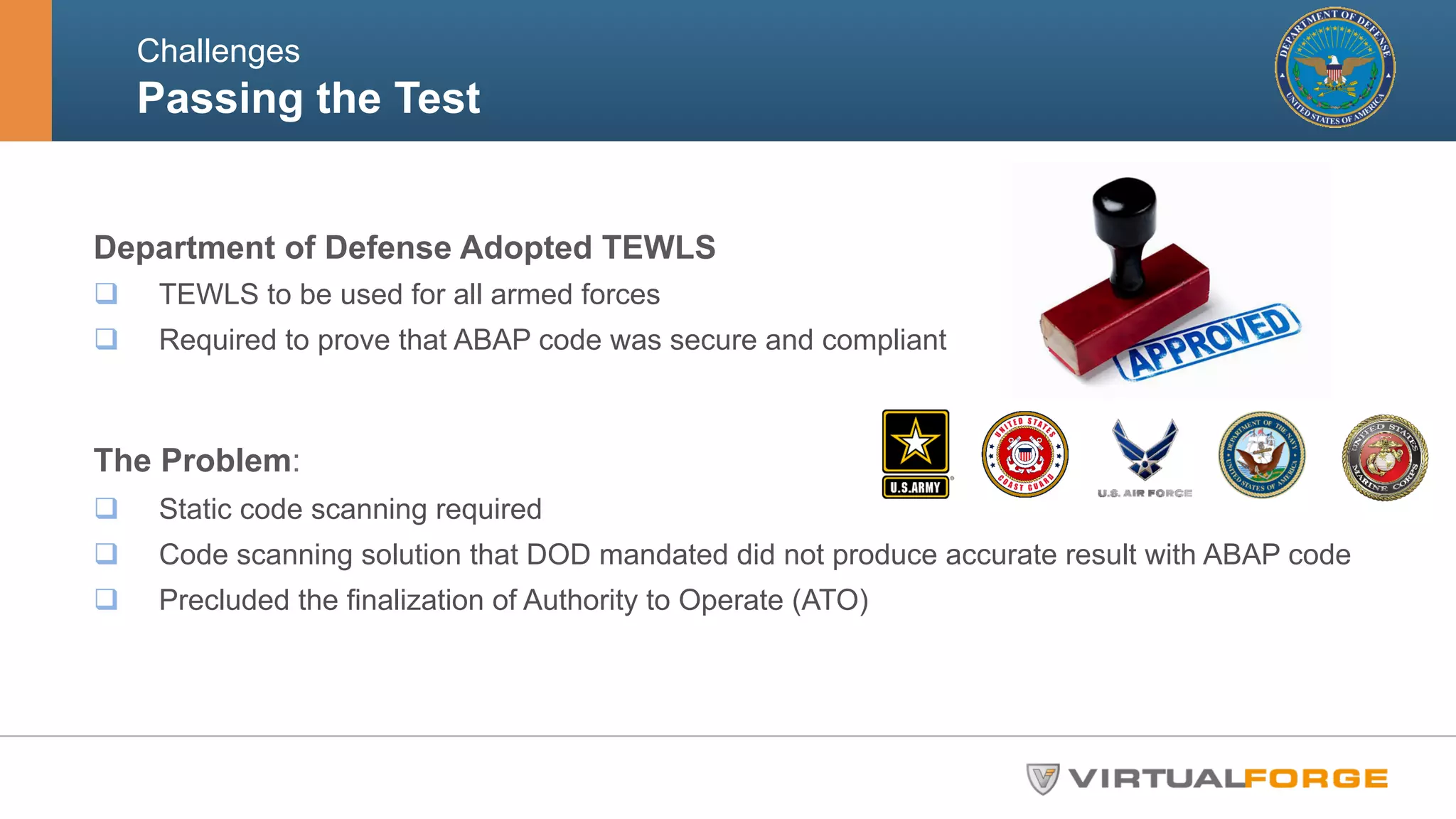
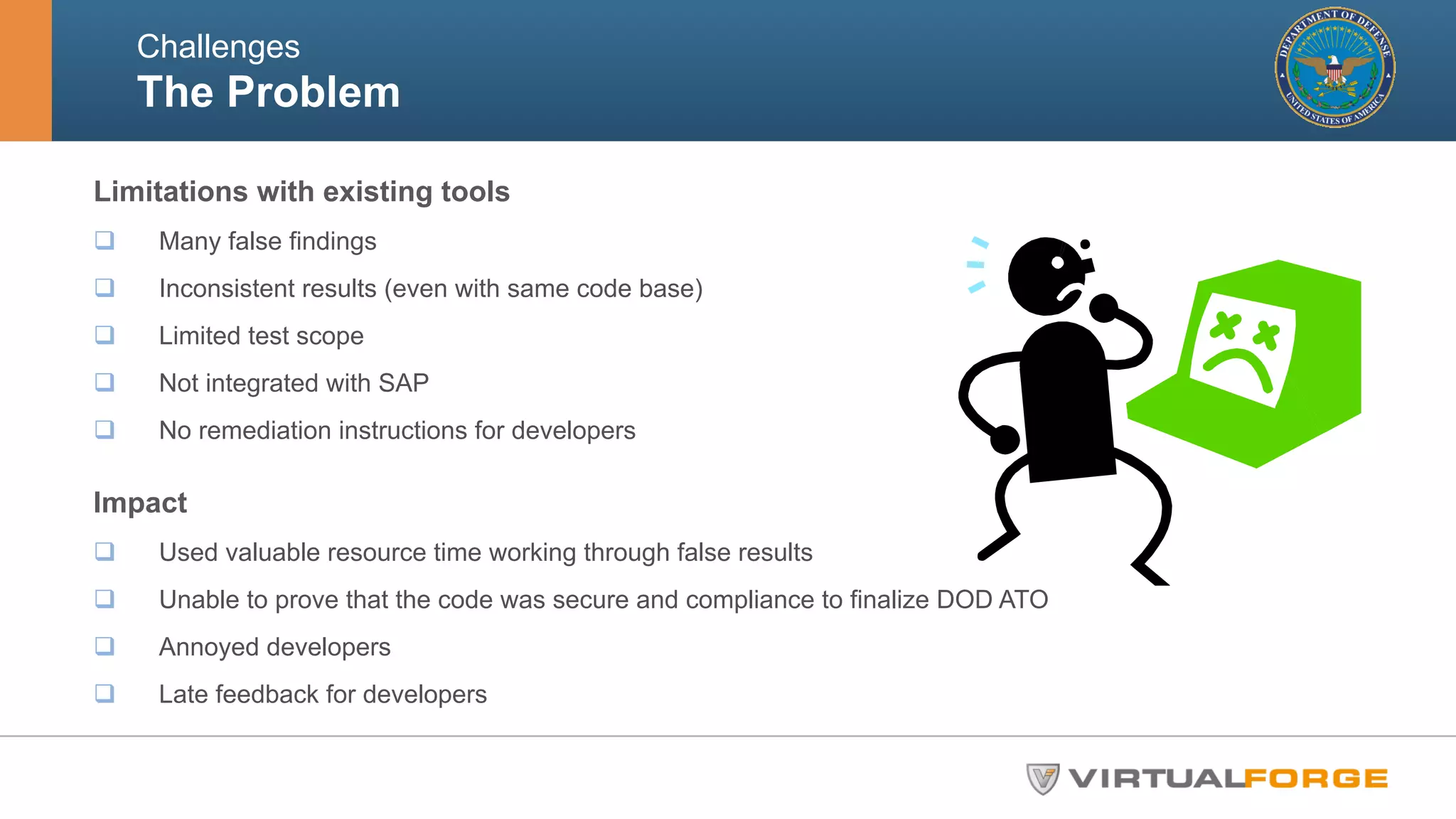
The document outlines the challenges and solutions related to the security and quality of custom ABAP applications within the Department of Defense's SAP systems, specifically focusing on the Theater Enterprise Wide Logistics System (TEWLS). It highlights the limitations of existing code scanning tools and presents the Virtual Forge CodeProfiler as a more effective solution for accurate risk assessment and remediation of vulnerabilities. Best practices for ensuring compliance and performance improvements are also discussed, emphasizing the importance of early and continuous static code scanning.







![Virtual Forge CodeProfiler
Customer Testimonials
Proven success
[ “Applying the Virtual Forge CodeProfiler and the close collaboration helped us to
increase the level of security and improved the quality of our business solutions.” ]
Ralph Salomon, Vice President IT Security & Risk Office at SAP
[ “One of the key requirements was to scan several billions lines of code each week.
Together with Virtual Forge we have been able to create a truly unique solution.” ]
Michael Brauer, Director of Corporate Automation within the Corporate IT department at Siemens
[ “With Virtual Forge CodeProfiler tightly integrated into our SAP change and transport
management processes, we were able to scan all our custom ABAP® code and identify non-compliant
code in no time at all.” ]
Joby Joseph, SAP Security Lead at Globe and Mail](https://image.slidesharecdn.com/sec2014techeddod-141111094605-conversion-gate01/75/Case-Study-Ensuring-the-Quality-and-Security-of-Custom-SAP-Applications-at-the-Department-of-Defense-30-2048.jpg)