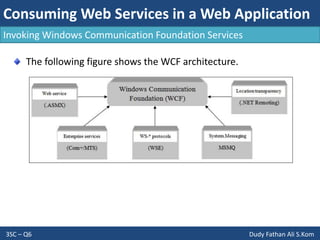
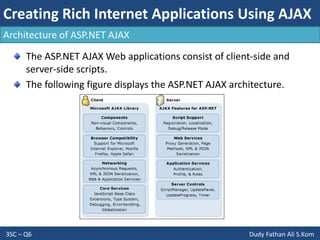
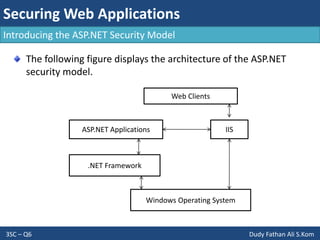
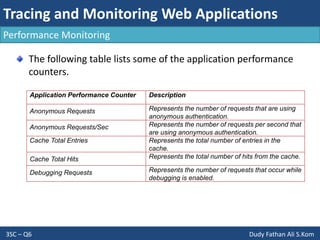
- The document discusses consuming web services in web applications, including invoking web services, consuming Windows Communication Foundation services, and the architecture of ASP.NET AJAX. It also covers implementing internationalization in applications by discussing globalization, localization, and factors to consider like language, formatting, strings, and user interfaces.