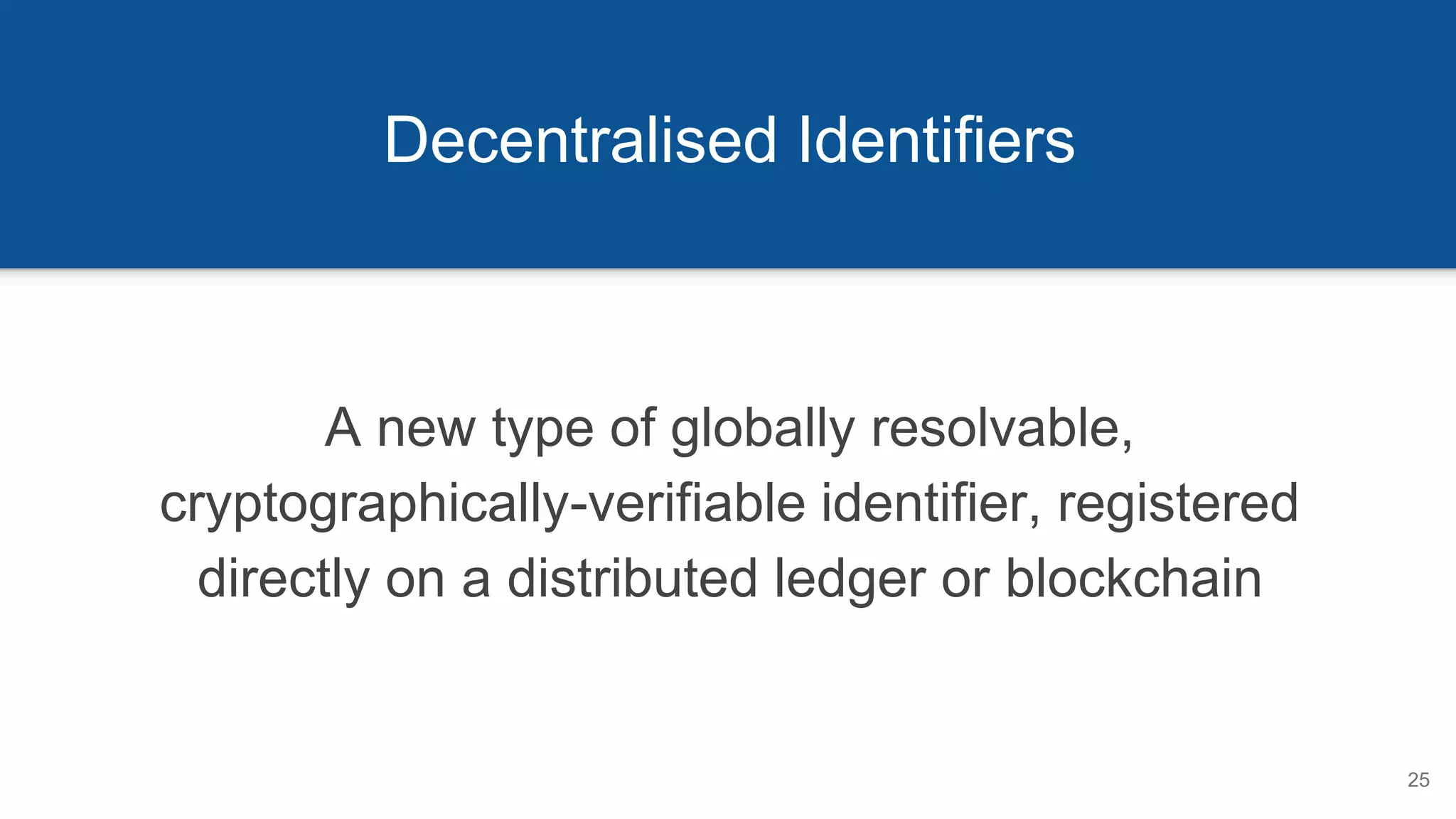
This document provides an overview of online privacy and identity. It discusses how current online identifiers are controlled by third parties rather than individuals. It then introduces decentralized identifiers (DIDs) as a new type of cryptographically-verifiable identifier that is owned by individuals rather than companies. DIDs allow for portable, privacy-respecting identifiers and verifiable credentials that do not depend on central authorities. The document outlines the potential benefits of this approach for data portability, privacy and security compared to the current internet identifier system.


















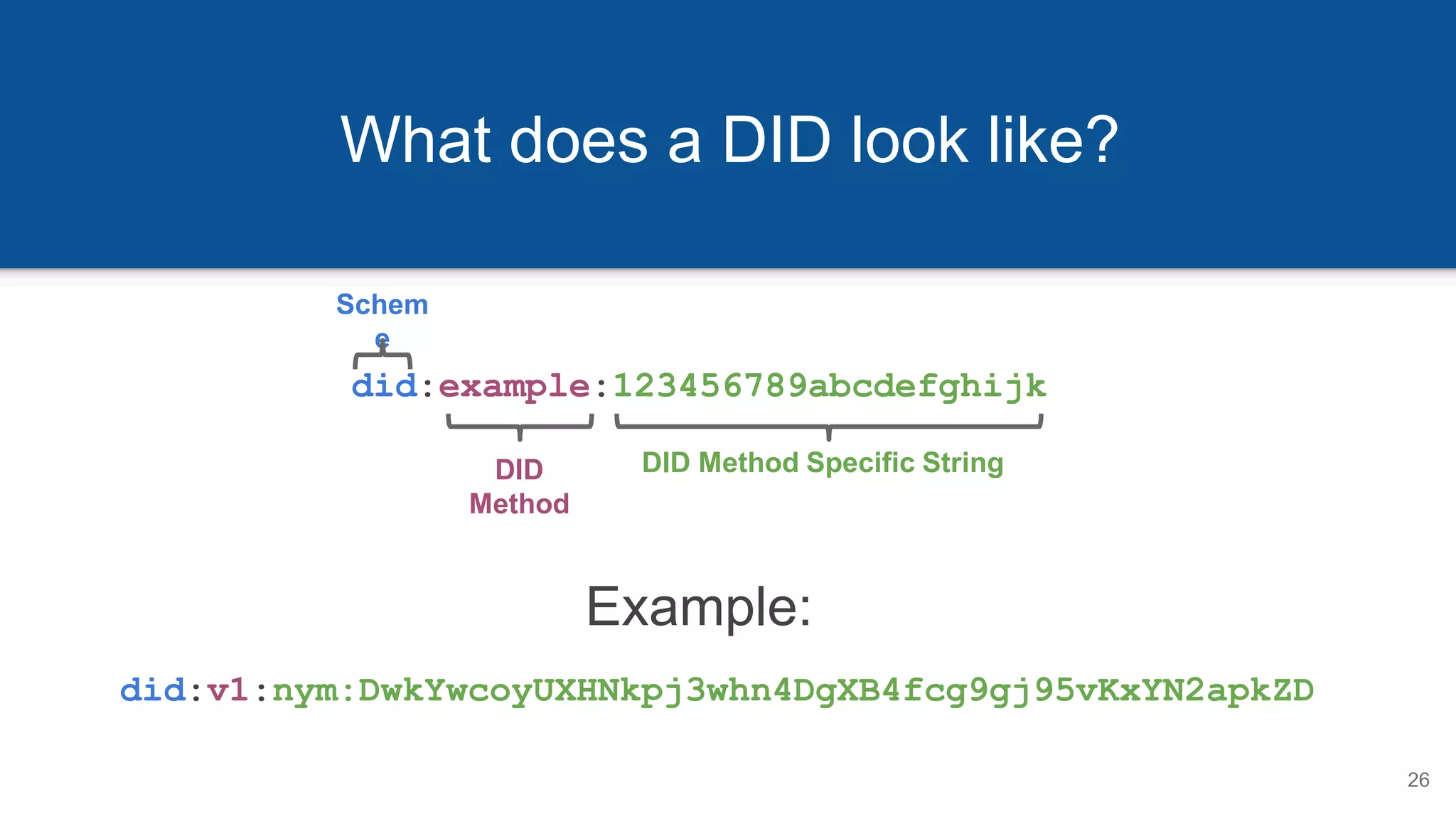
![DIDs Resolve to DID Documents
27
{
"@context": "https://w3id.org/veres-one/v1",
"id": "did:v1:nym:DwkYwcoyUXHNkpj3whn4DgXB4fcg9gj95vKxYN2apkZD",
"authentication": [{
"type": "Ed25519SignatureAuthentication2018",
"publicKey": [{
"id": "did:v1:test:nym:DwkYwcoyUXHNkpj3whn4DgXB4fcg9gj95vKxYN2apkZD#authn-key-1",
"type": "Ed25519VerificationKey2018",
"owner": "did:v1:nym:DwkYwcoyUXHNkpj3whn4DgXB4fcg9gj95vKxYN2apkZD",
"publicKeyBase58": "DwkYwcoyUXHNkpj3whn4DgXB4fcg9gj95vKxYN2apkZD"
}]
}],
"service": [{
"type": "ExampleMessagingService",
"serviceEndpoint": ”https://example.com/services/messages”
}],
… more DID-specific information here …
}
1. Authentication Mechanisms
3. Service Discovery
2. Public Key Material](https://image.slidesharecdn.com/returningtoonlineprivacy-uqlibrary20191105-191104122359/75/Returning-to-Online-Privacy-25-2048.jpg)