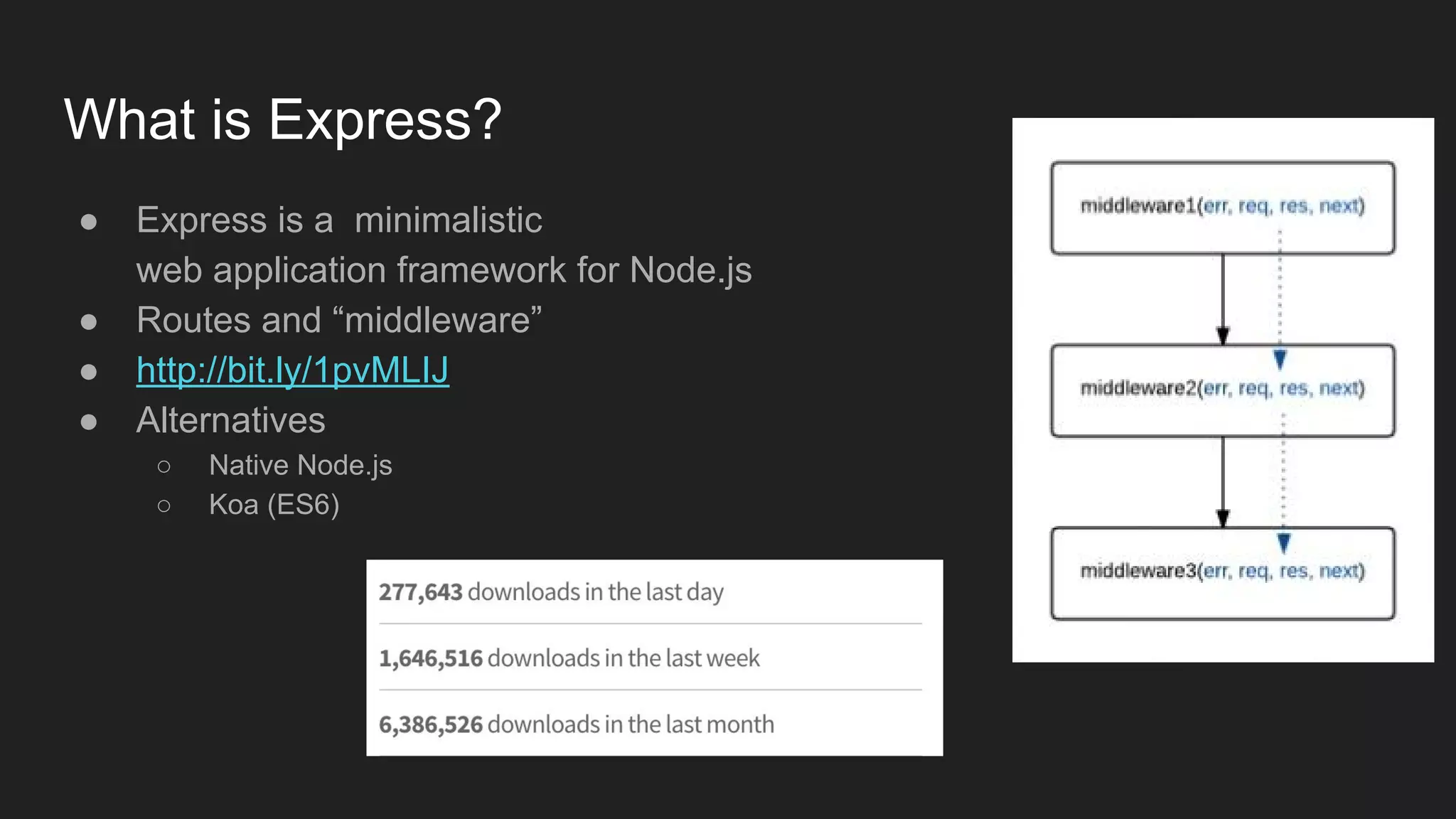
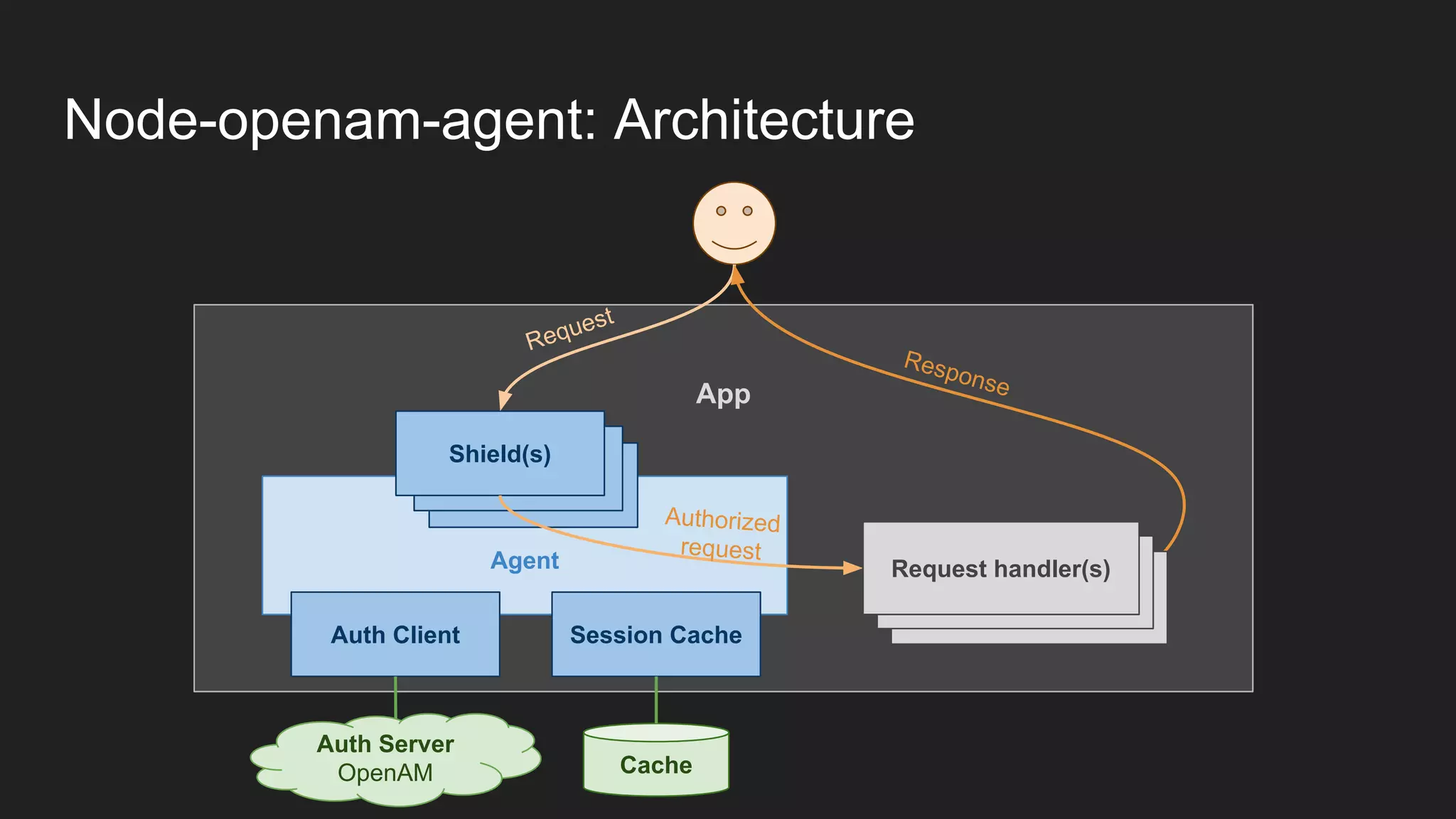
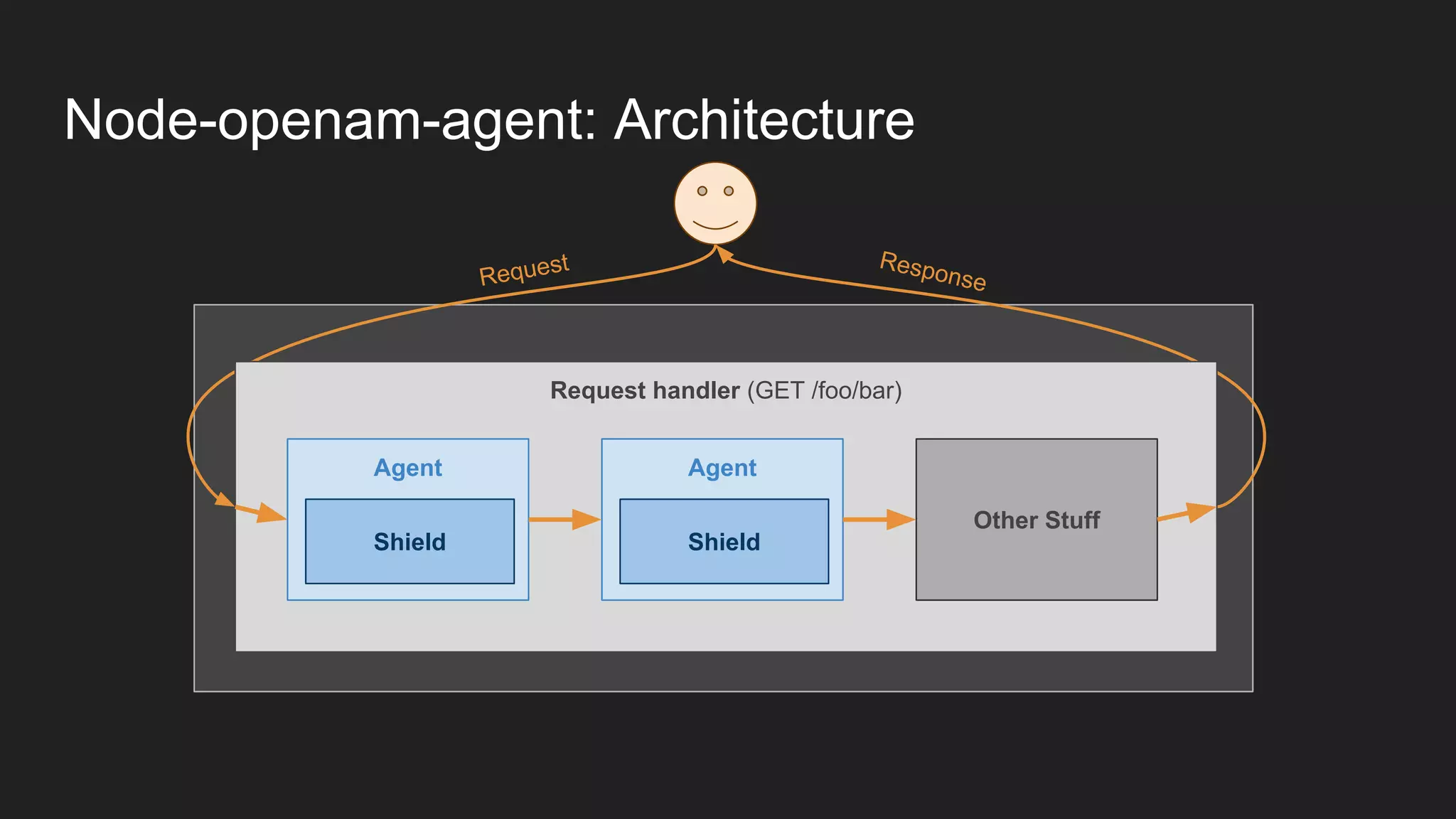
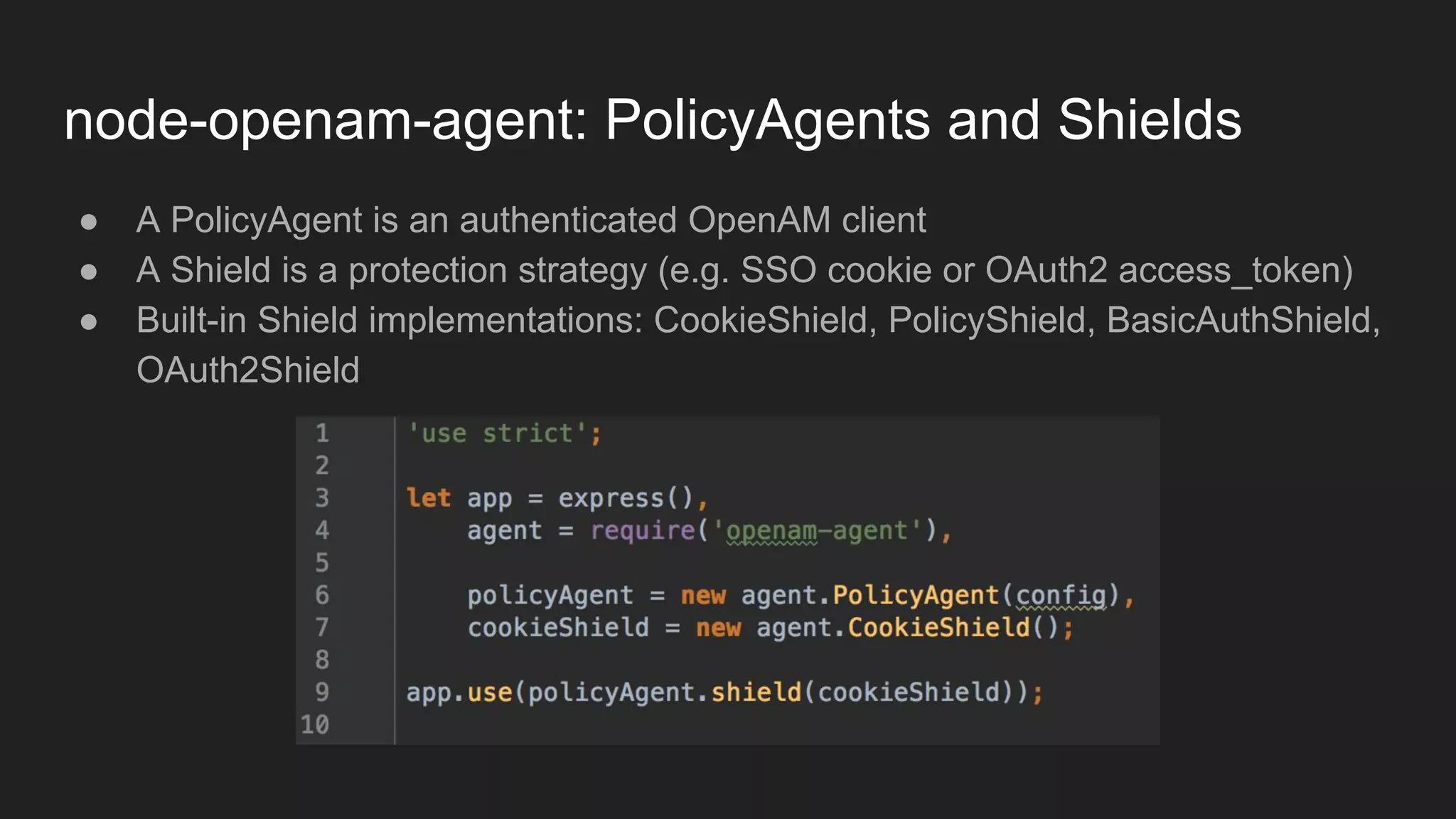
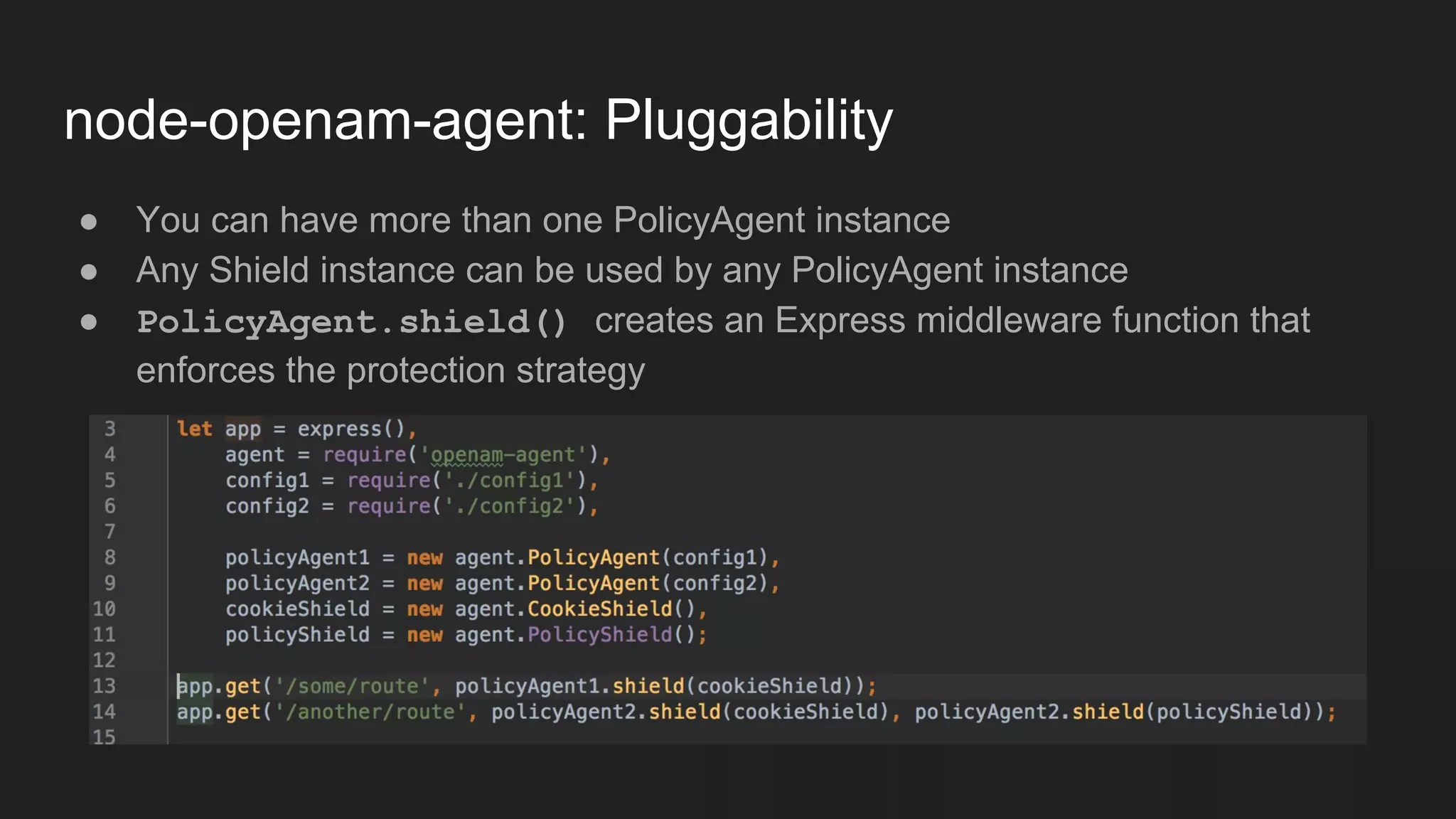
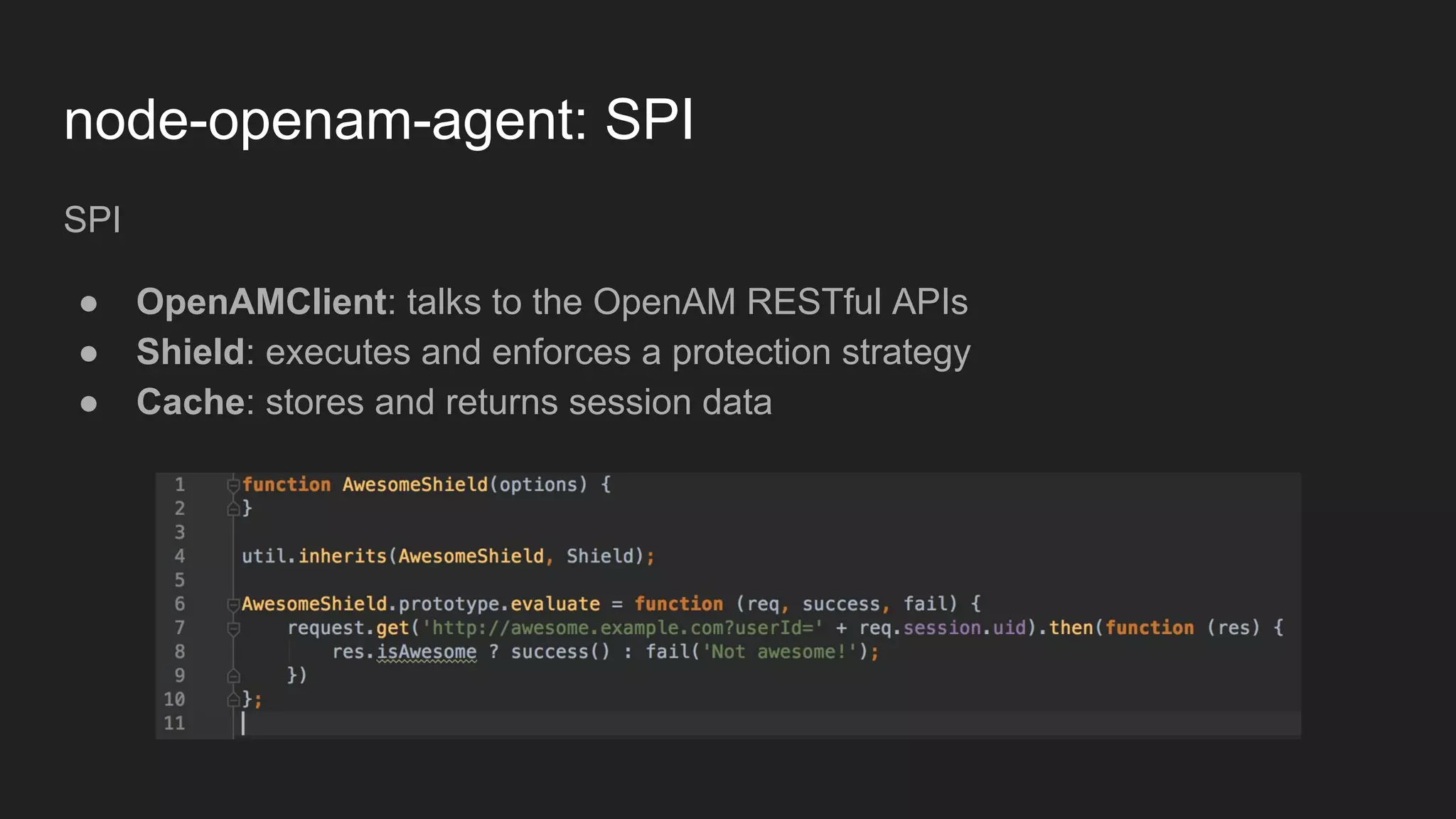
Node.js is a JavaScript runtime for building server applications. Express is a web application framework for Node.js. The document discusses problems with traditional policy agents and proposes a new decentralized policy agent architecture called node-openam-agent. Node-openam-agent uses Express middleware to enforce authentication strategies from OpenAM and allows multiple agent instances to each use different authentication strategies on different routes. It aims to be more extensible, lightweight, and integrated with applications than traditional monolithic policy agents.