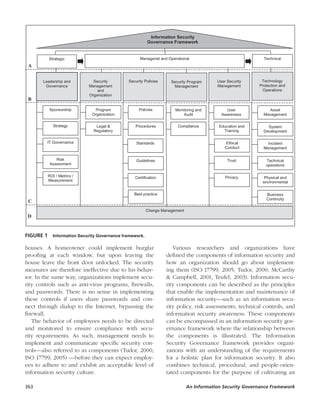
This document discusses information security governance frameworks. It evaluates four existing approaches: ISO 17799, PROTECT, the Capability Maturity Model, and the Information Security Architecture. Based on the components of these approaches, the document compiles a comprehensive list of information security components. It then uses these components to construct a new Information Security Governance Framework, which considers technical, procedural, and human behavioral components to holistically govern information security and cultivate an appropriate security culture.