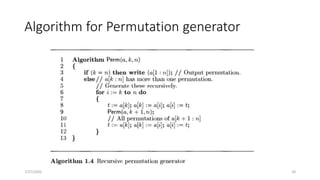
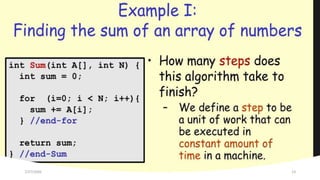
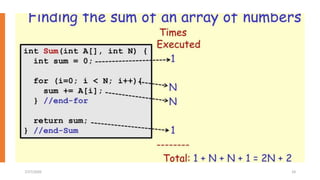
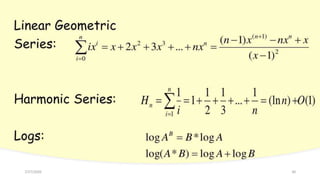
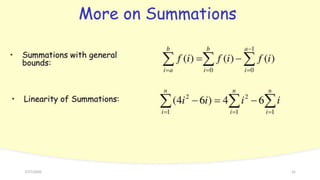
The document provides an overview of recursive and iterative algorithms. It discusses key differences between recursive and iterative algorithms such as definition, application, termination, usage, code size, and time complexity. Examples of recursive algorithms like recursive sum, factorial, binary search, tower of Hanoi, and permutation generator are presented along with pseudocode. Analysis of recursive algorithms like recursive sum, factorial, binary search, Fibonacci number, and tower of Hanoi is demonstrated to determine their time complexities. The document also discusses iterative algorithms, proving an algorithm's correctness, the brute force approach, and store and reuse methods.







![Recursive Binary Search
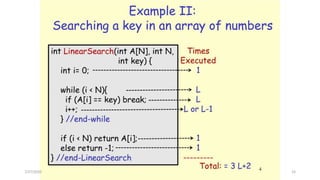
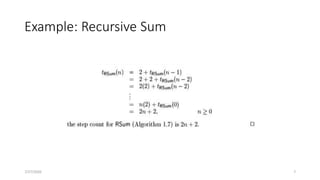
• The recurrence relation for the running time of the method is:
T(1) = a if n = 1 (one element array)
T(n) = T(n / 2) + b if n > 1
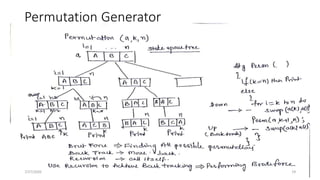
Algorithm BinarySearch (target,array, low, high) {
if (low > high)then
return ;
else {
middle = (low + high)/2;
if (array[middle] == target)then
return middle;
else if(array[middle] < target)then
return BinarySearch(target, array, middle + 1, high);
else
return BinarySearch(target, array, low, middle - 1);
}
}
7/27/2020 9](https://image.slidesharecdn.com/recursivealgorithms-200728093138/85/Recursive-algorithms-9-320.jpg)
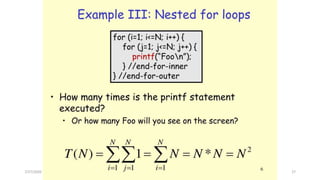
![Analysis of Recursive Binary Search
Expanding:
T(1) = a (1)
T(n) = T(n / 2) + b (2)
= [T(n / 22) + b] + b = T (n / 22) + 2b by substituting T(n/2) in (2)
= [T(n / 23) + b] + 2b = T(n / 23) + 3b by substituting T(n/22) in (2)
= ……..
= T( n / 2k) + kb
The base case is reached when n / 2k = 1 n = 2k k = log2 n, we then
have:
T(n) = T(1) + b log2 n
= a + b log2 n
Therefore, Recursive Binary Search is O(log n)
Without loss of generality, assume n, the problem size, is a multiple of 2, i.e., n = 2k
7/27/2020 10](https://image.slidesharecdn.com/recursivealgorithms-200728093138/85/Recursive-algorithms-10-320.jpg)
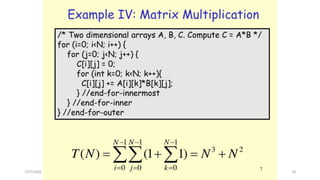
![Recursive Fibonacci number Algorithm
T(n) = c if n = 1 or n = 2 (1)
T(n) = T(n – 1) + T(n – 2) + b if n > 2 (2)
We determine a lower bound on T(n):
Expand : T(n) = T(n - 1) + T(n - 2) + b
≥ T(n - 2) + T(n-2) + b
= 2T(n - 2) + b
= 2[T(n - 3) + T(n - 4) + b] + b by substitute T(n - 2) in (2)
2[T(n - 4) + T(n - 4) + b] + b
= 22T(n - 4) + 2b + b
= 22[T(n - 5) + T(n - 6) + b] + 2b + b by substitute T(n - 4) in (2)
≥ 23T(n – 6) + (22 + 21 + 20)b
. . .
2kT(n – 2k) + (2k-1 + 2k-2 + . . . + 21 + 20)b
= 2kT(n – 2k) + (2k – 1)b
The base case is reached when n – 2k = 2 k = (n - 2) / 2
Hence, T(n) ≥ 2 (n – 2) / 2 T(2) + [2 (n - 2) / 2 – 1]b
= (b + c)2 (n – 2) / 2 – b
= [(b + c) / 2]*(2)n/2 – b Récursive Fibonacci is exponentiel
Algorithm Fibonacci (n) { // Recursively calculates
Fibonacci number
if( n == 1 || n == 2)then
return 1;
else
return Fibonacci(n – 1) + Fibonacci(n – 2);
}
7/27/2020 11](https://image.slidesharecdn.com/recursivealgorithms-200728093138/85/Recursive-algorithms-11-320.jpg)
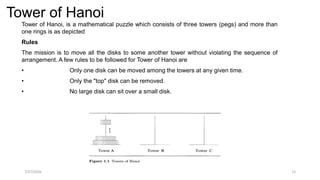
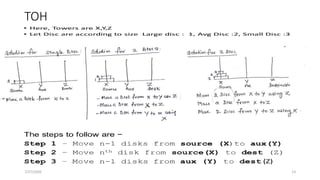

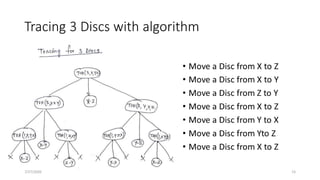
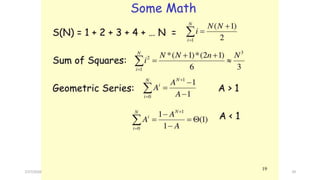
![Analysis of Recursive Towers of Hanoi Algorithm
Expanding:
T(1) = a (1)
T(n) = 2T(n – 1) + b if n > 1 (2)
= 2[2T(n – 2) + b] + b = 22 T(n – 2) + 2b + b by substituting T(n – 1) in (2)
= 22 [2T(n – 3) + b] + 2b + b = 23 T(n – 3) + 22b + 2b + b by substituting T(n-2) in (2)
= 23 [2T(n – 4) + b] + 22b + 2b + b = 24 T(n – 4) + 23 b + 22b + 21b + 20b by substituting
T(n – 3) in (2)
= ……
= 2k T(n – k) + b[2k- 1 + 2k– 2 + . . . 21 + 20]
The base case is reached when n – k = 1 k = n – 1, we then have:
Therefore, The method hanoi is O(2n)
7/27/2020 16](https://image.slidesharecdn.com/recursivealgorithms-200728093138/85/Recursive-algorithms-16-320.jpg)