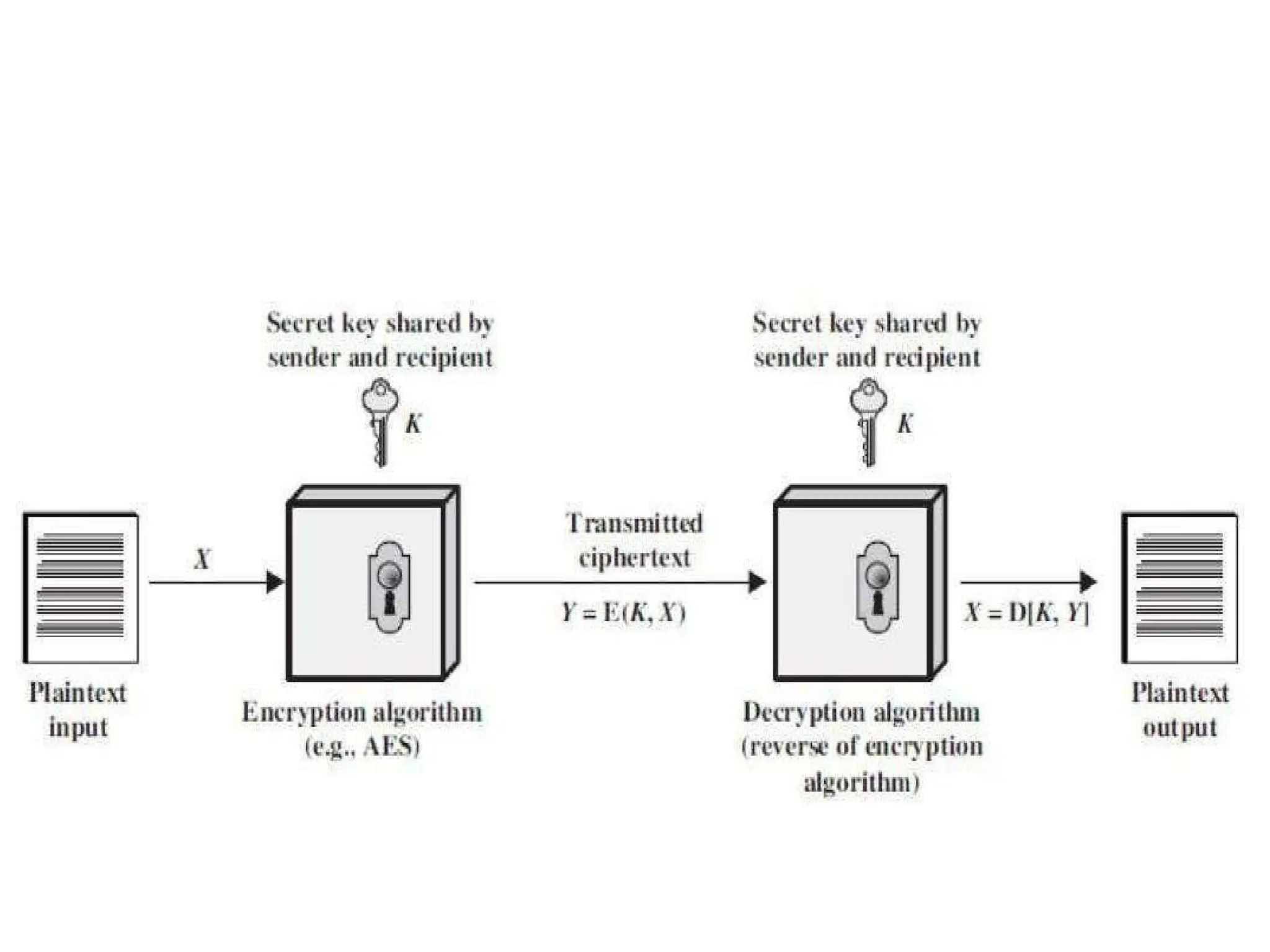
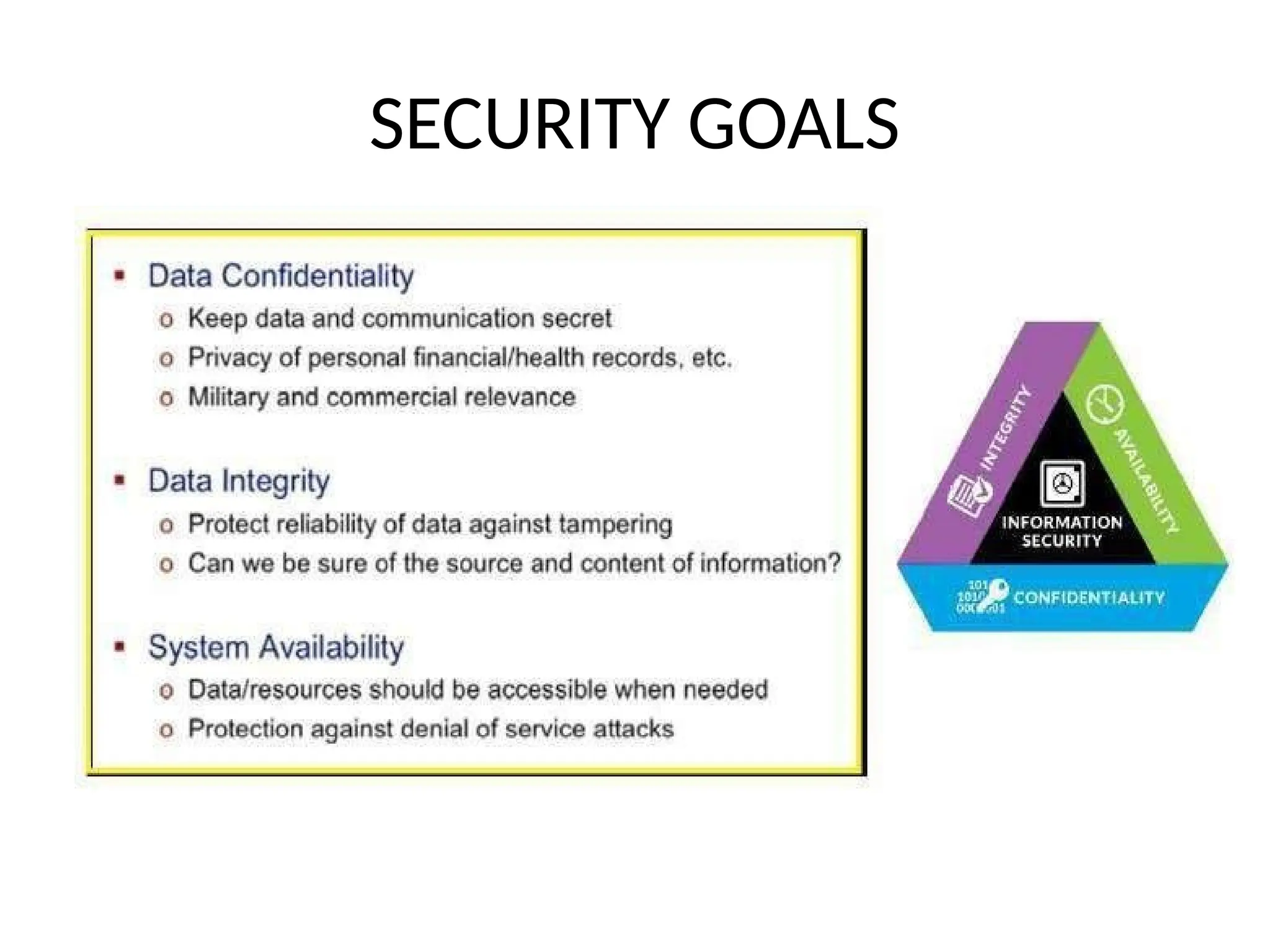
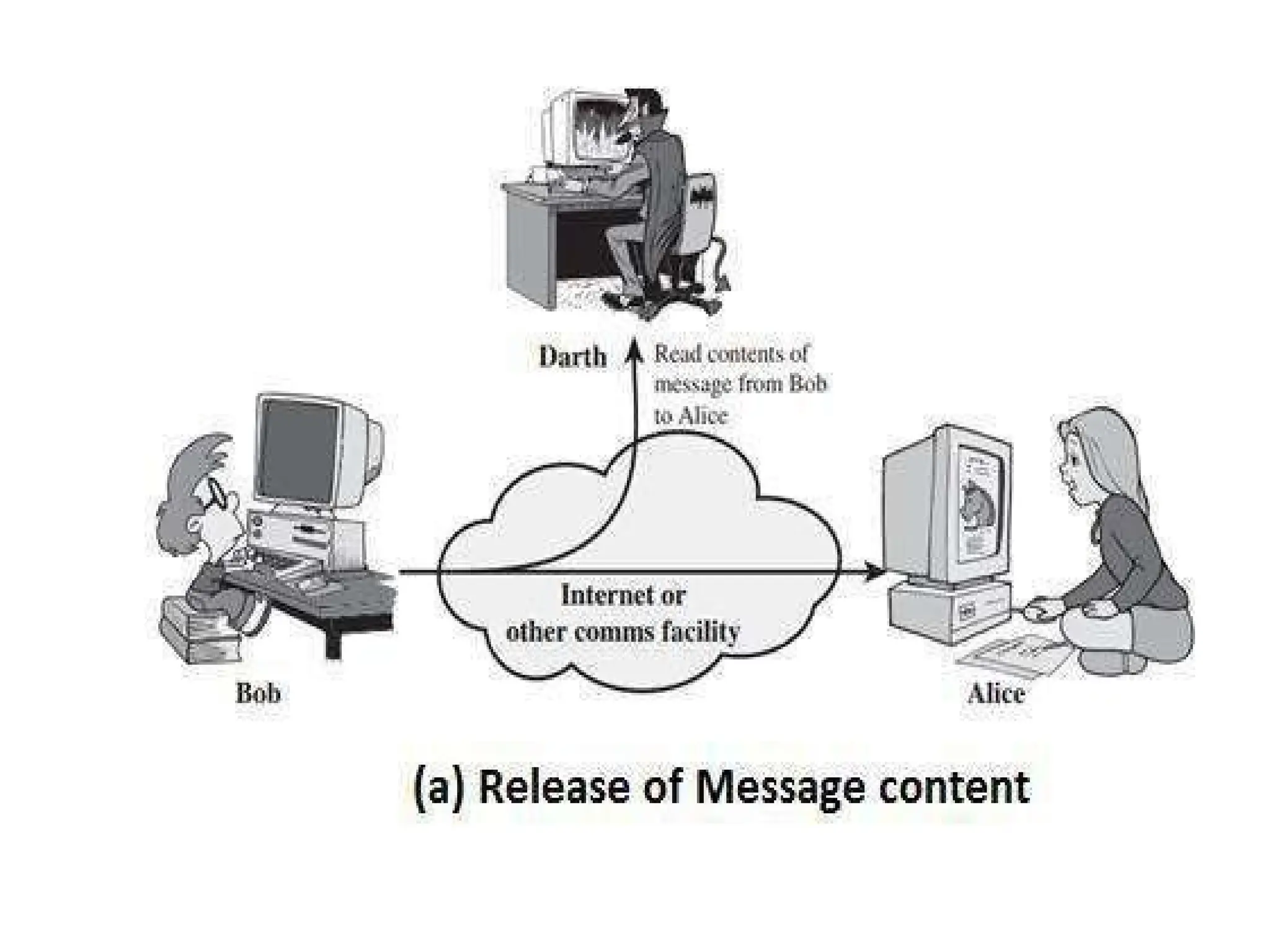
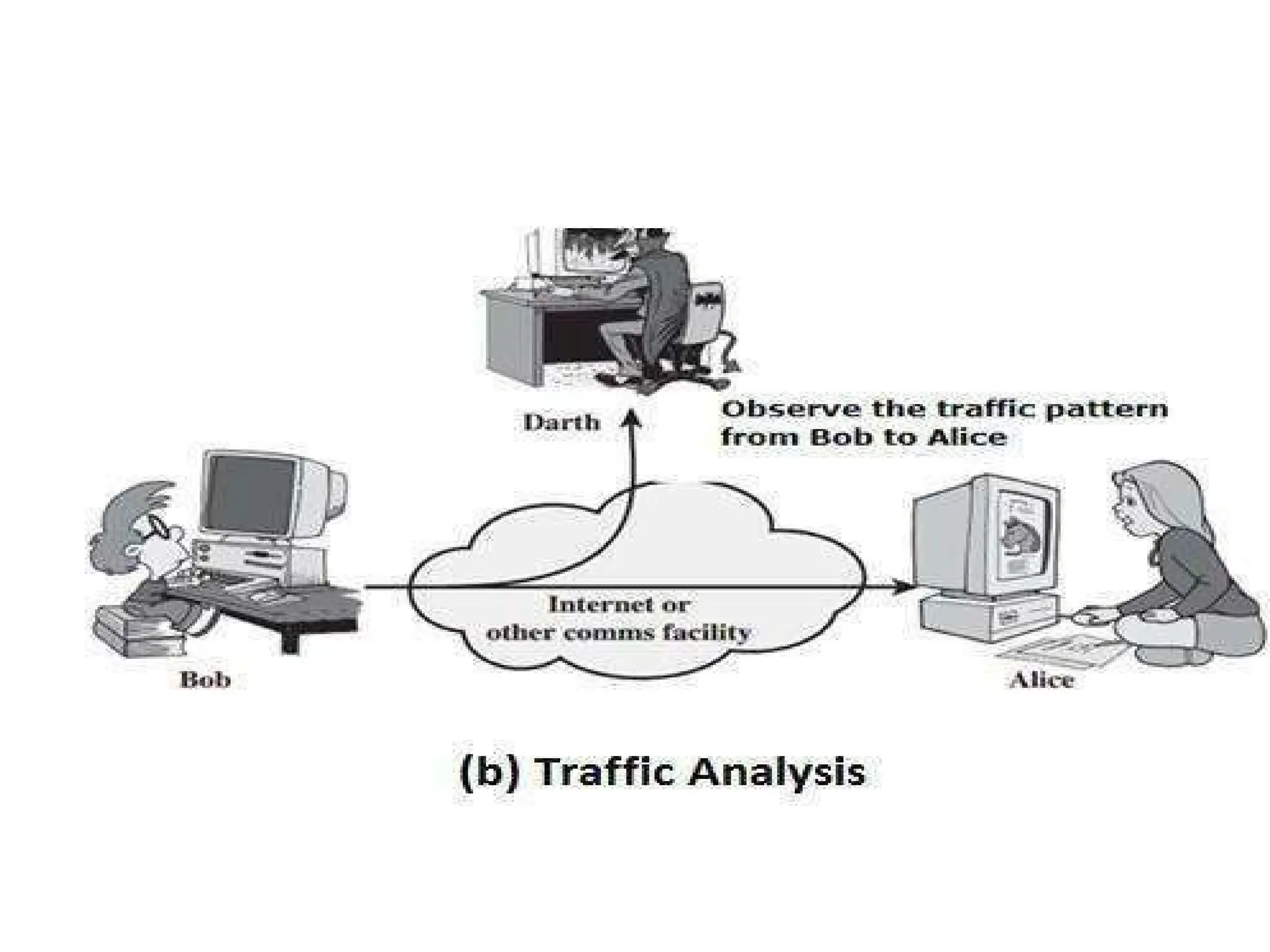
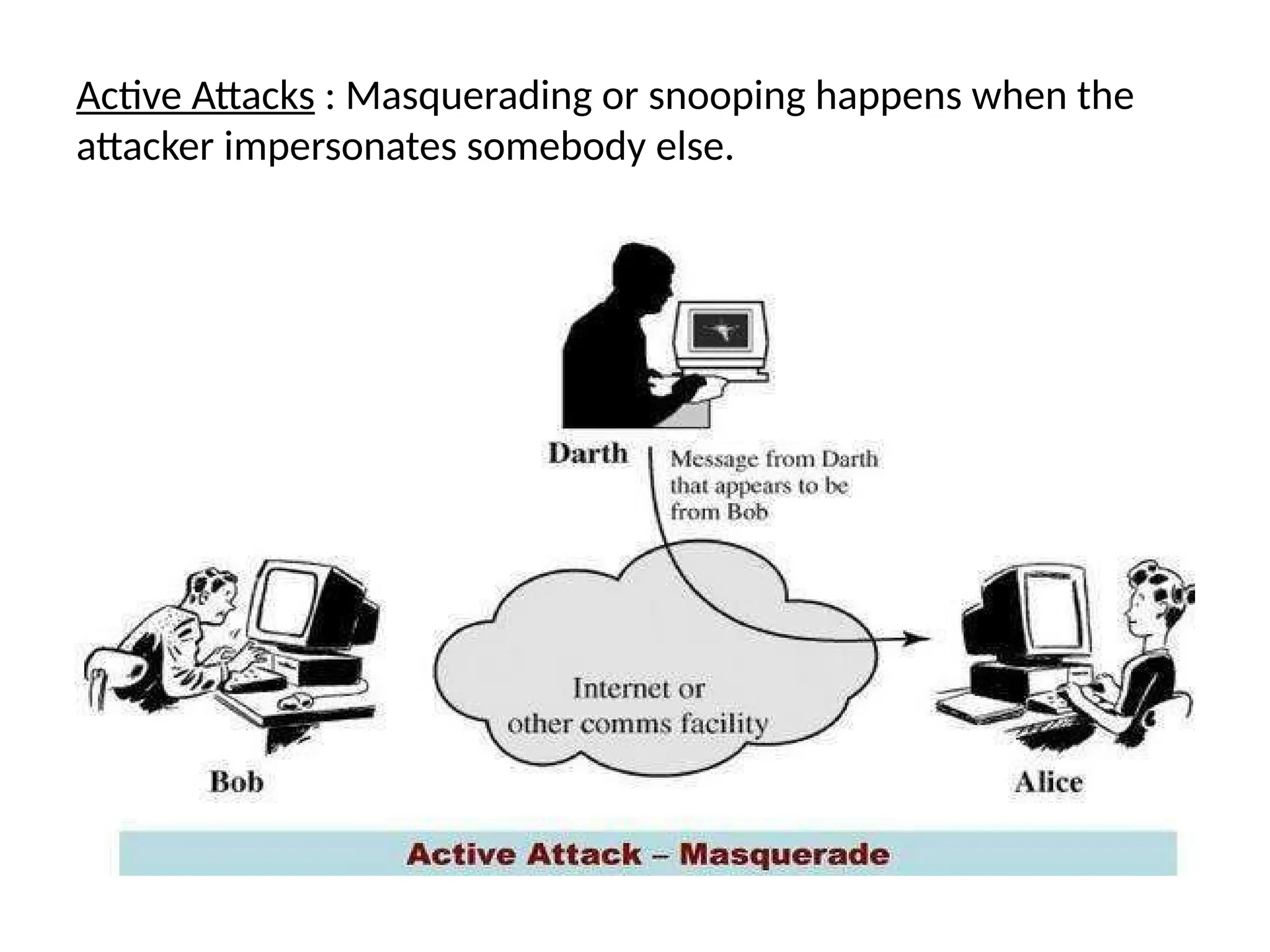
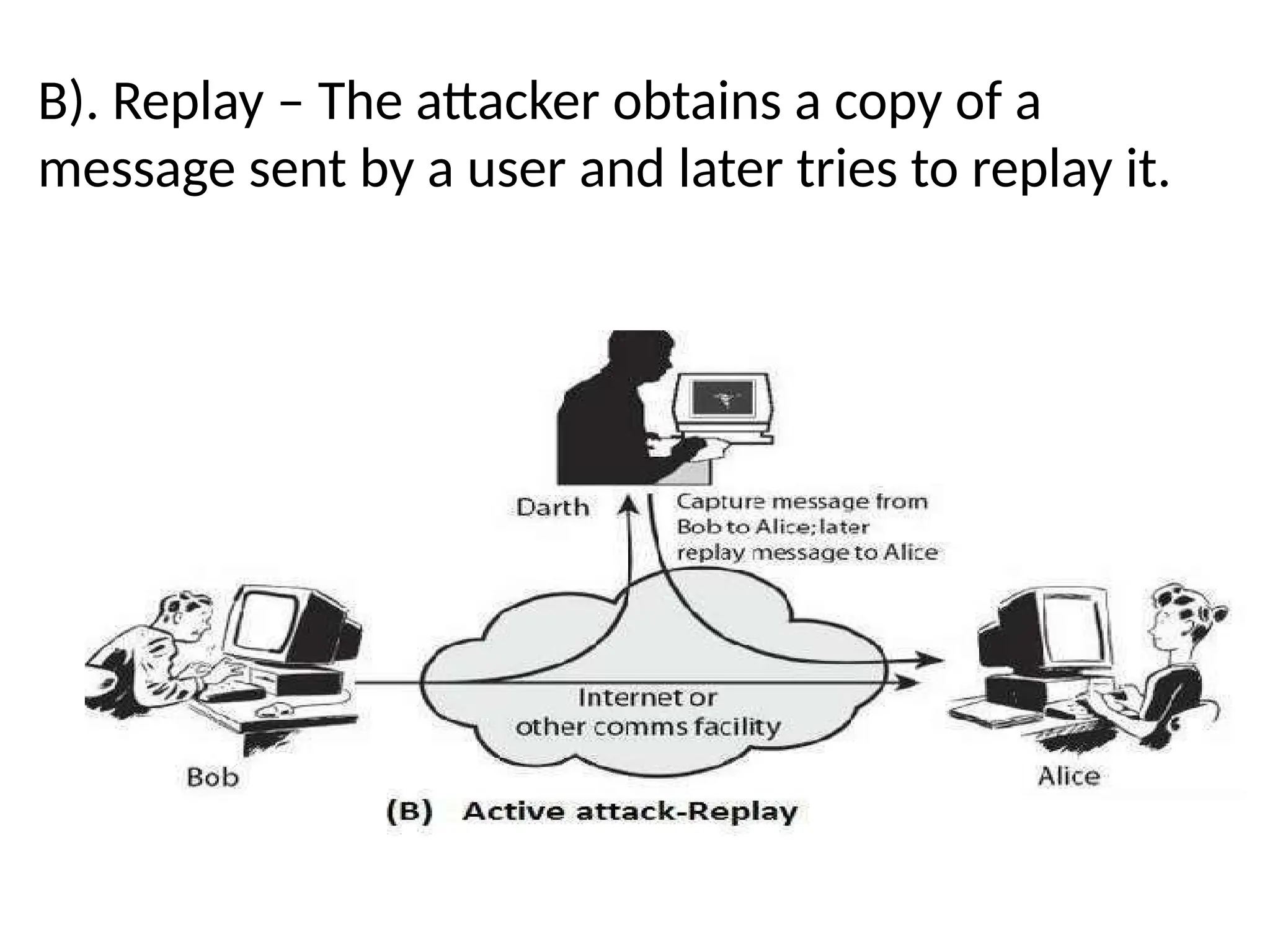
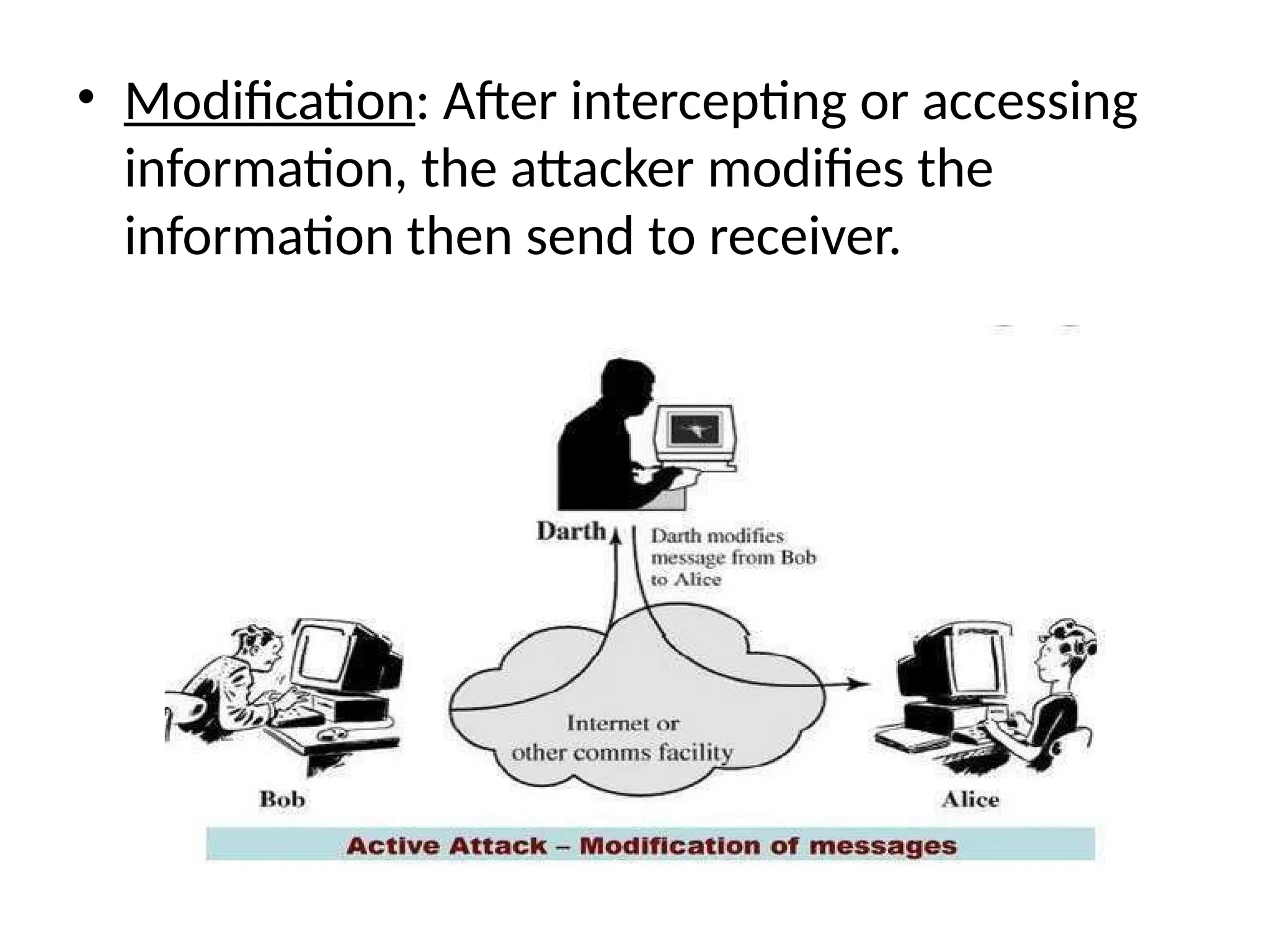
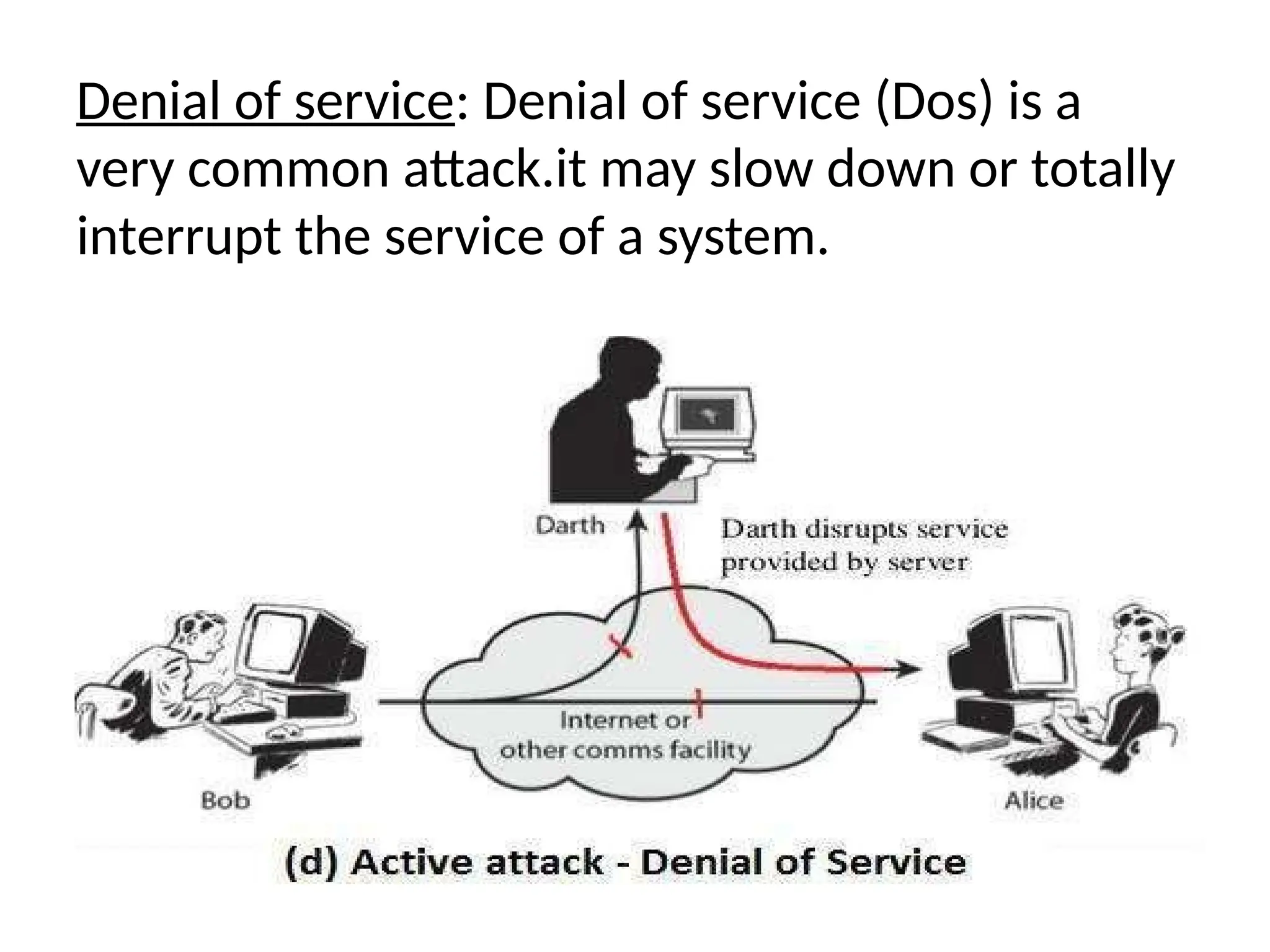
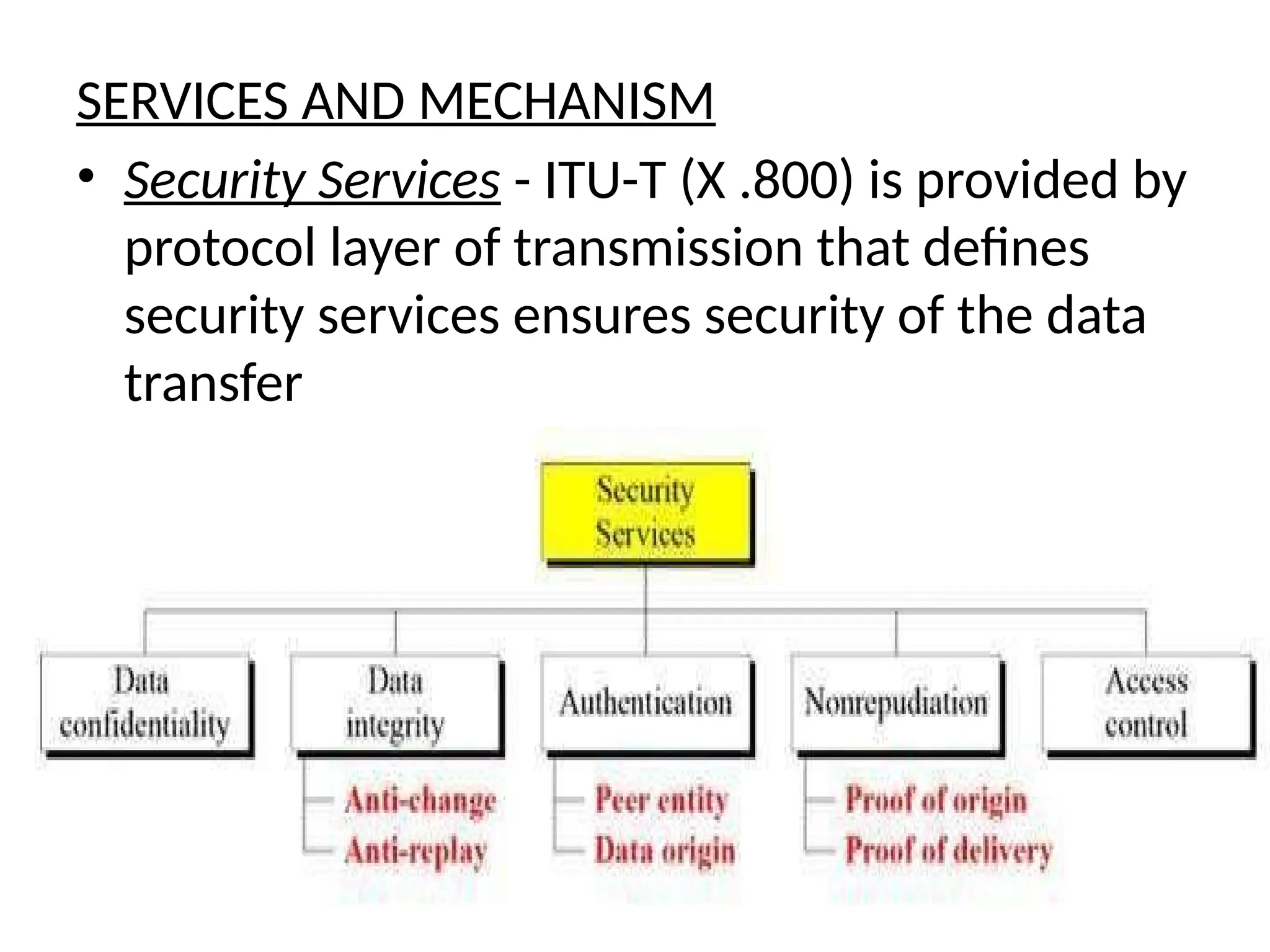
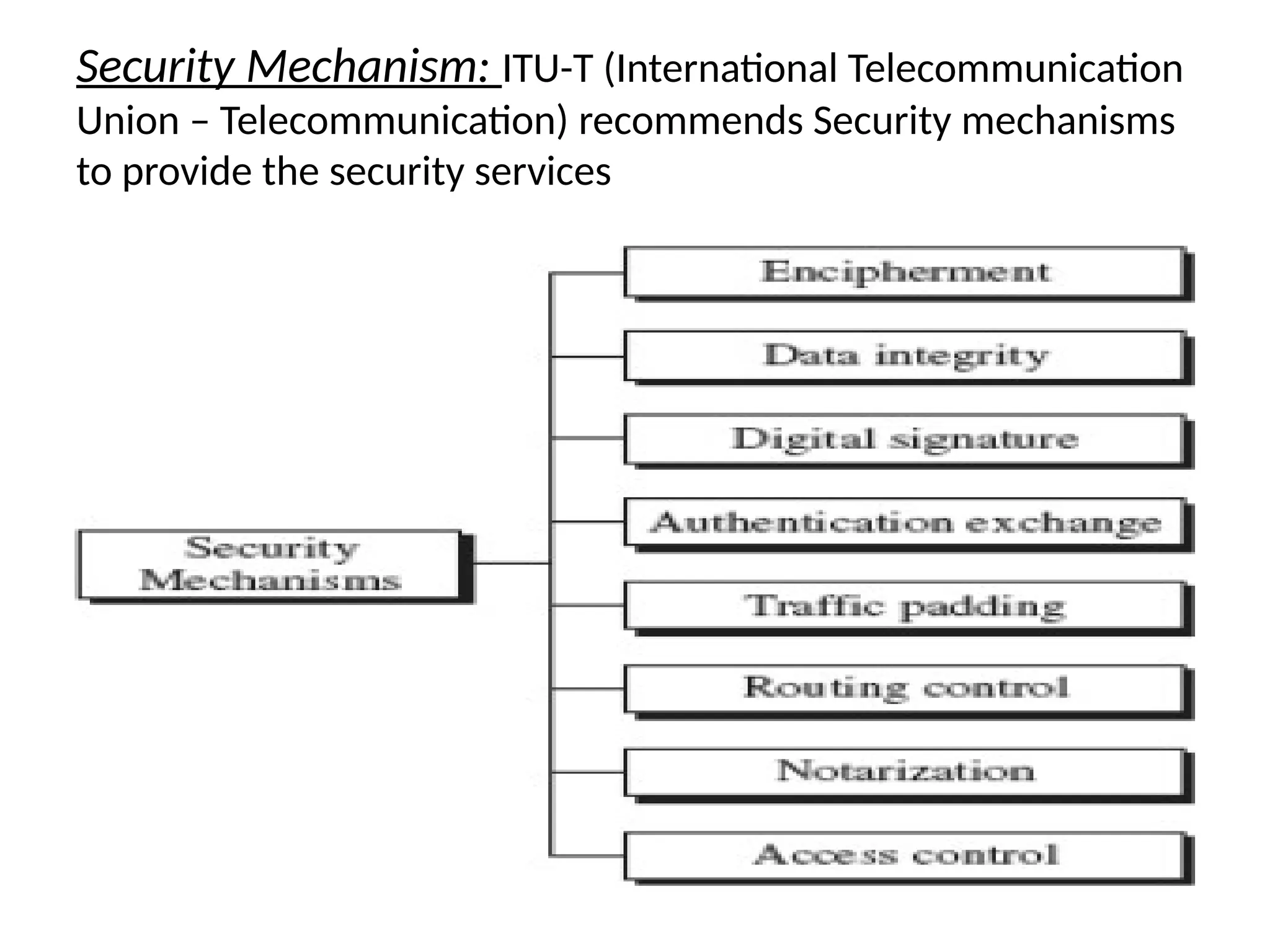
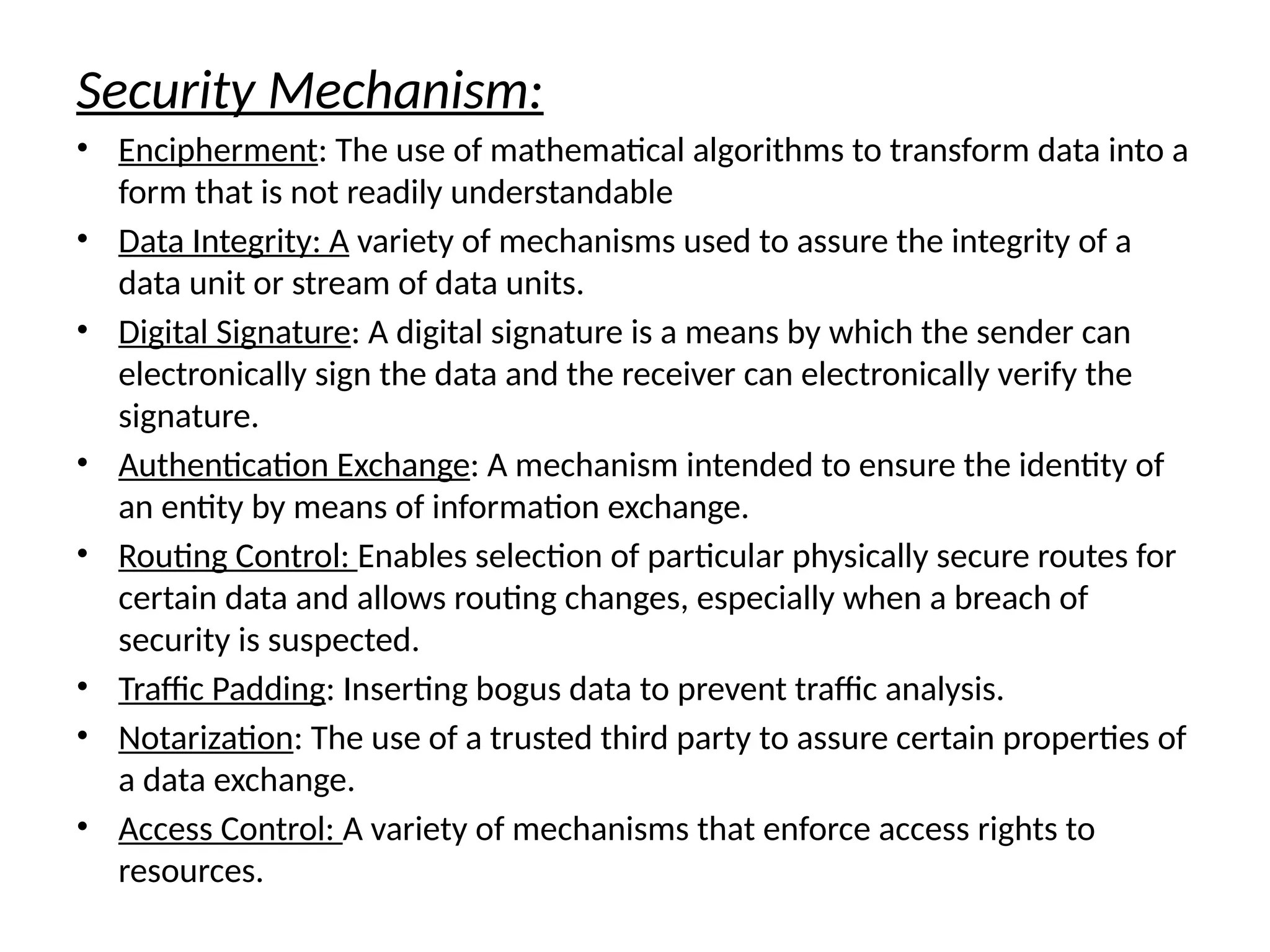
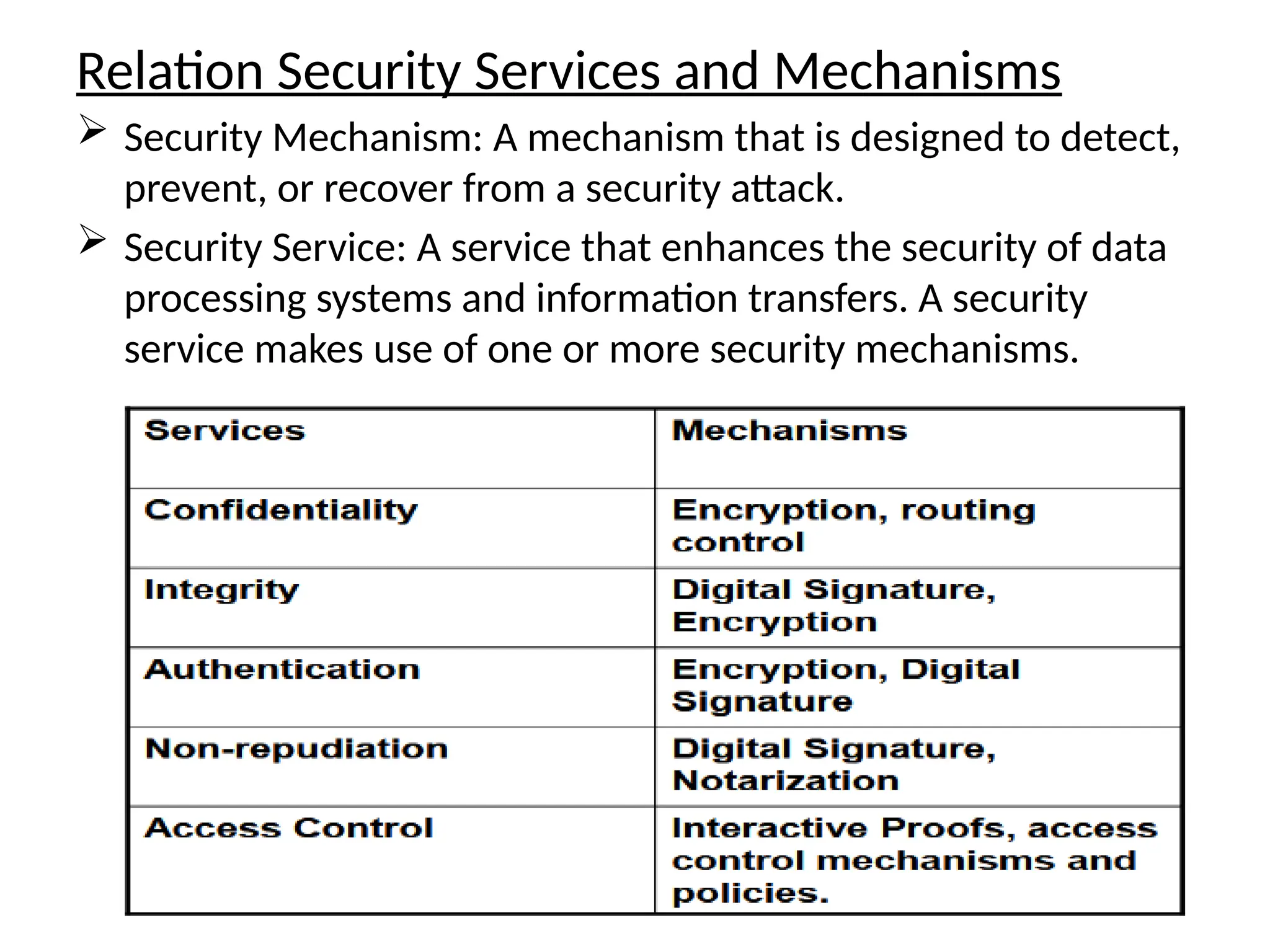
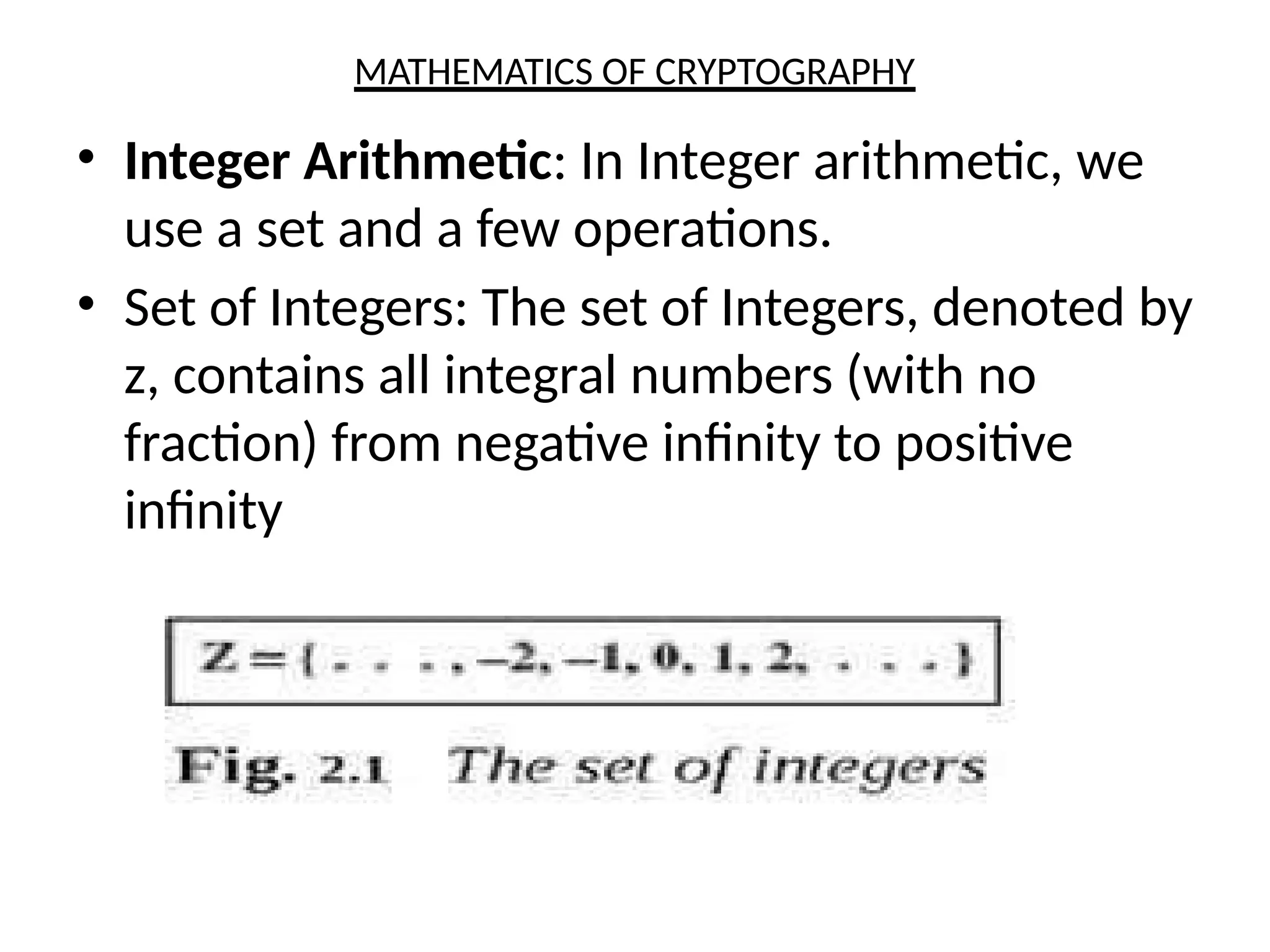
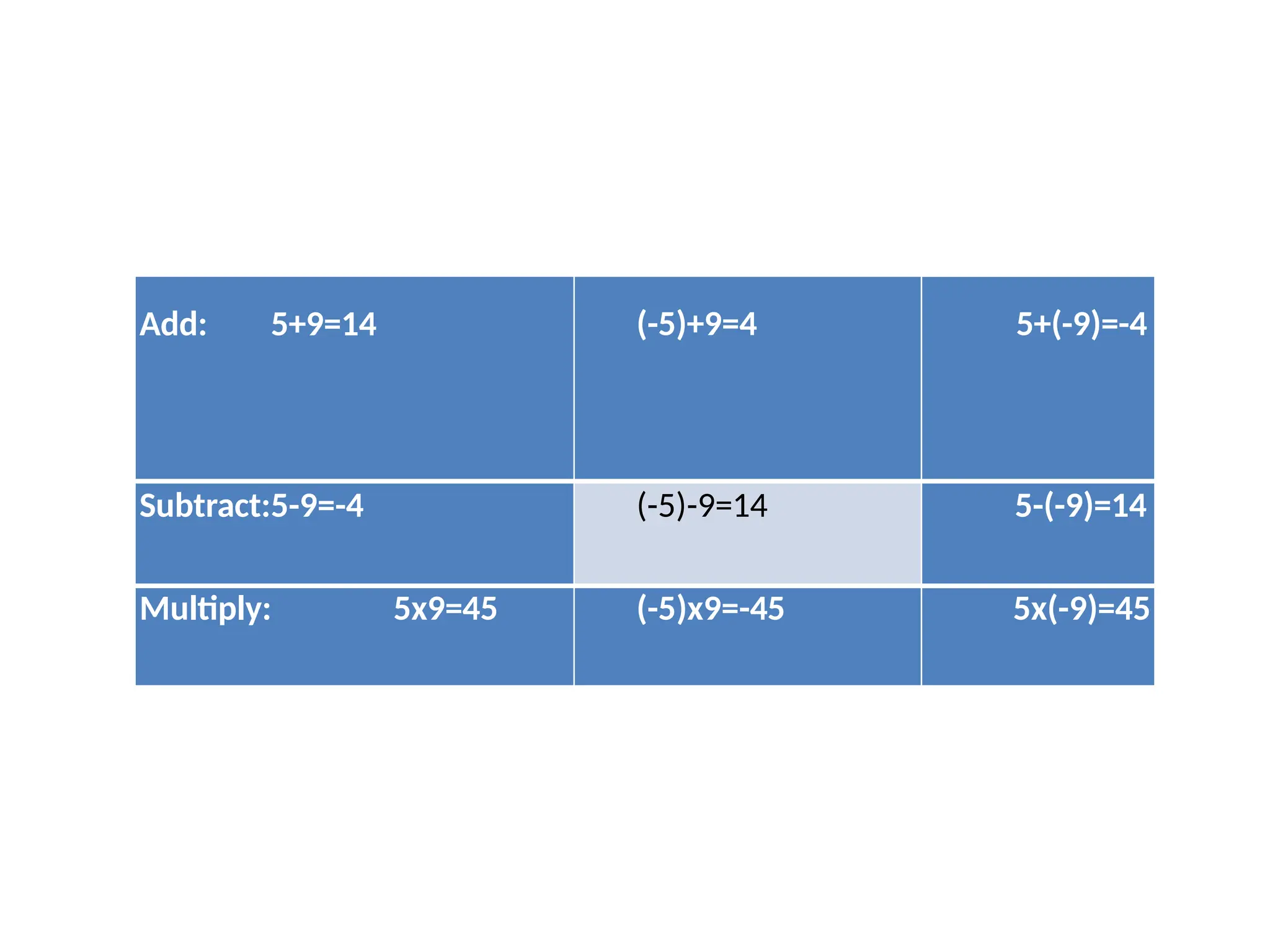
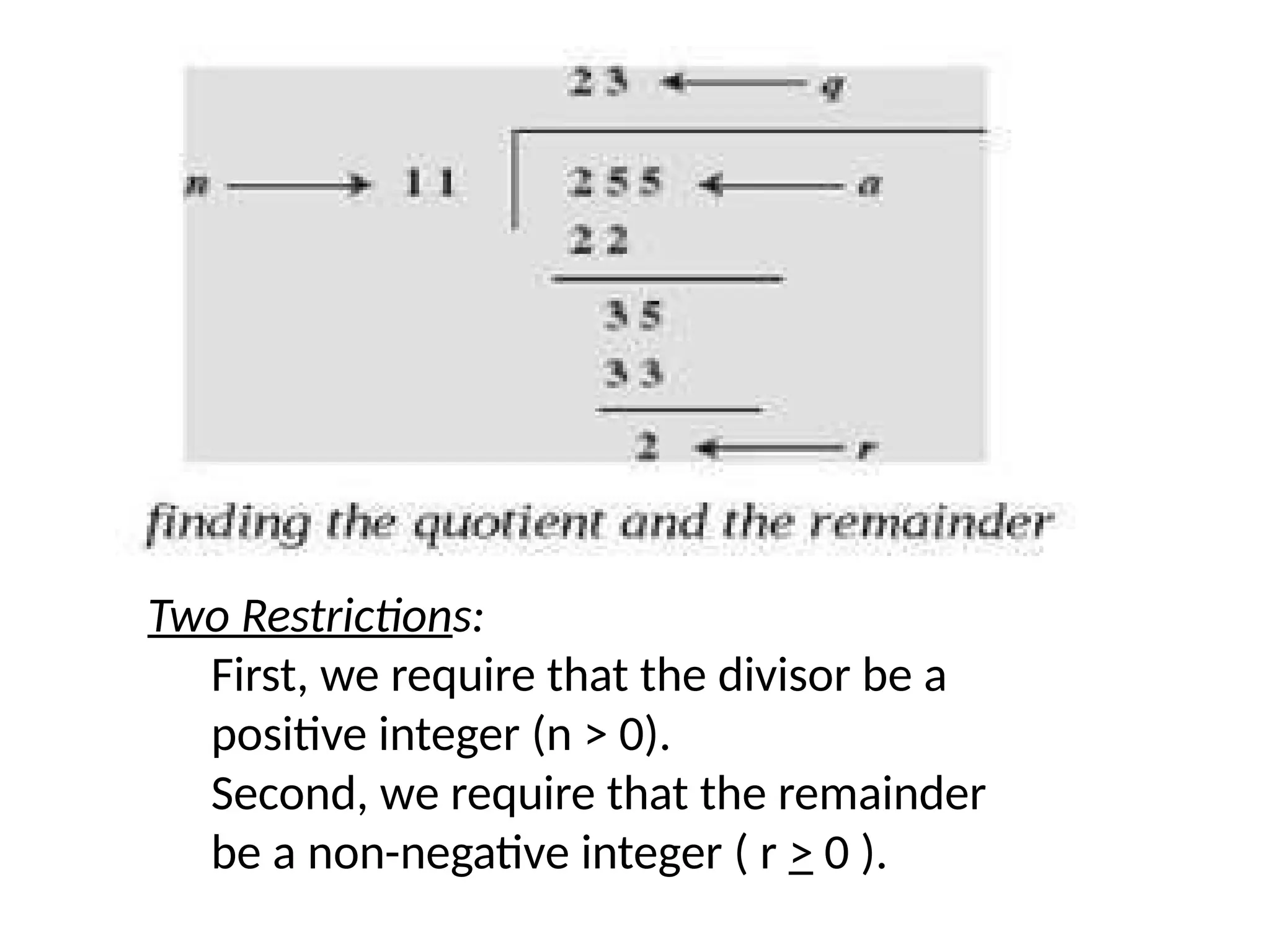
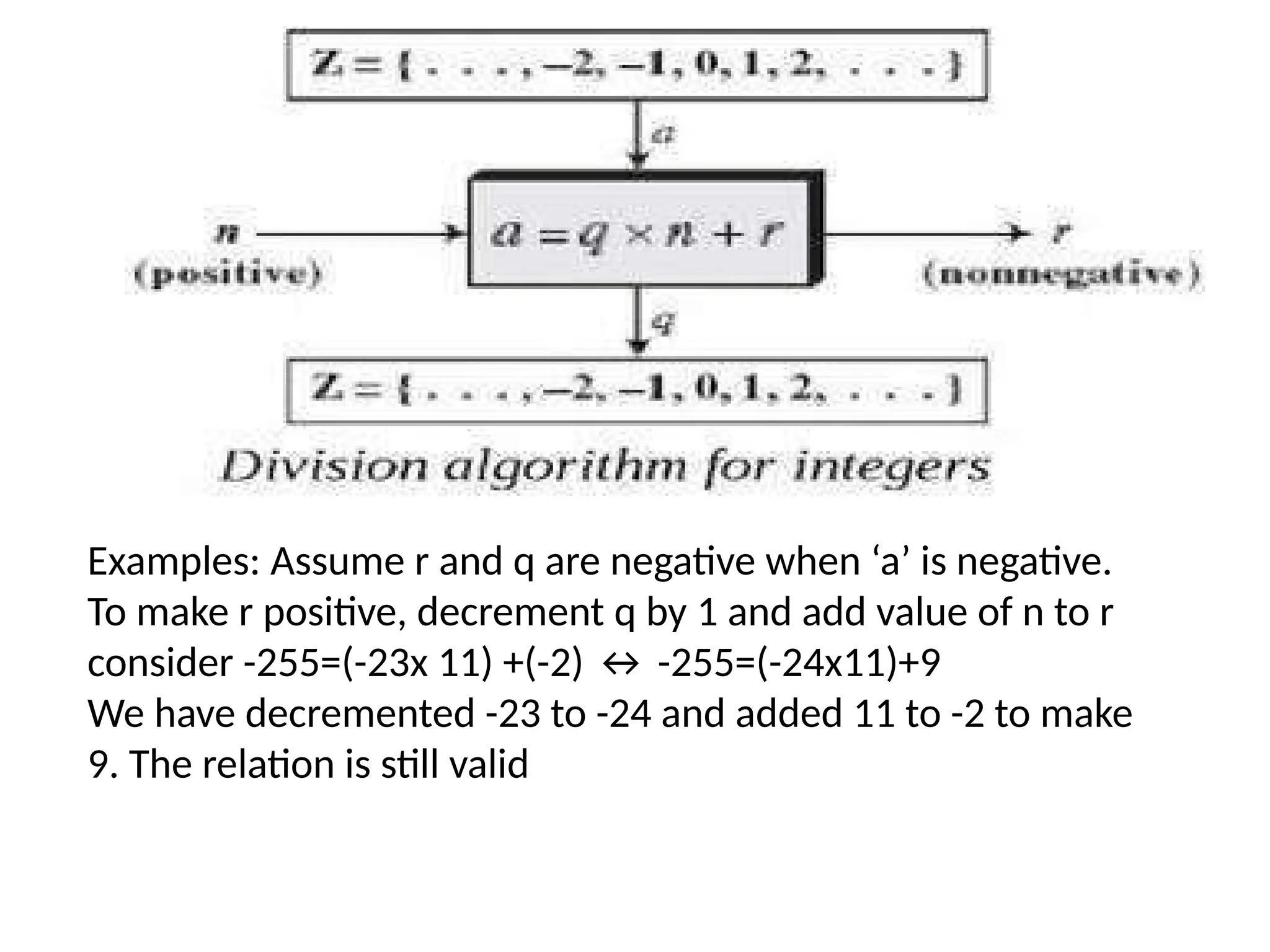
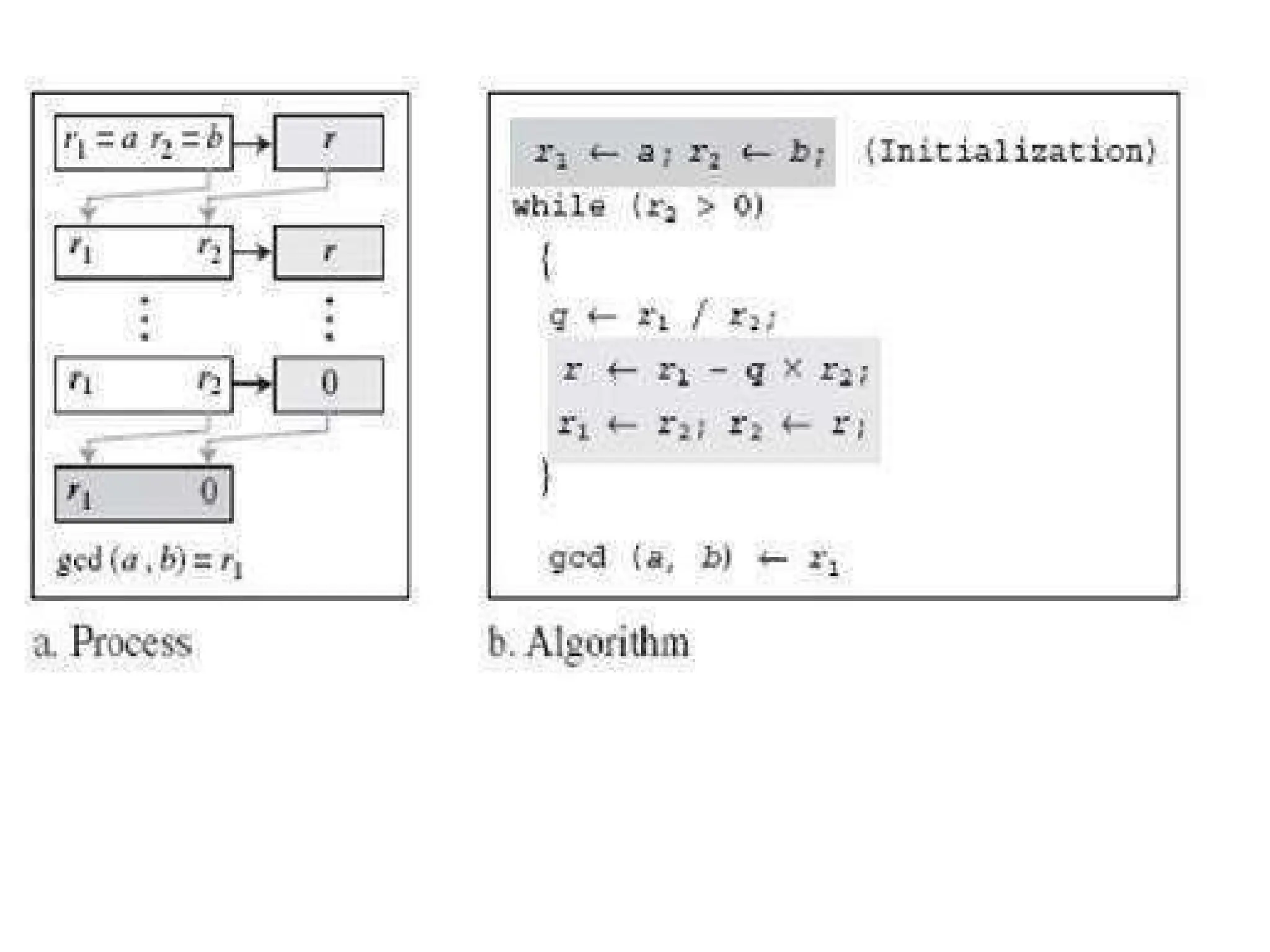
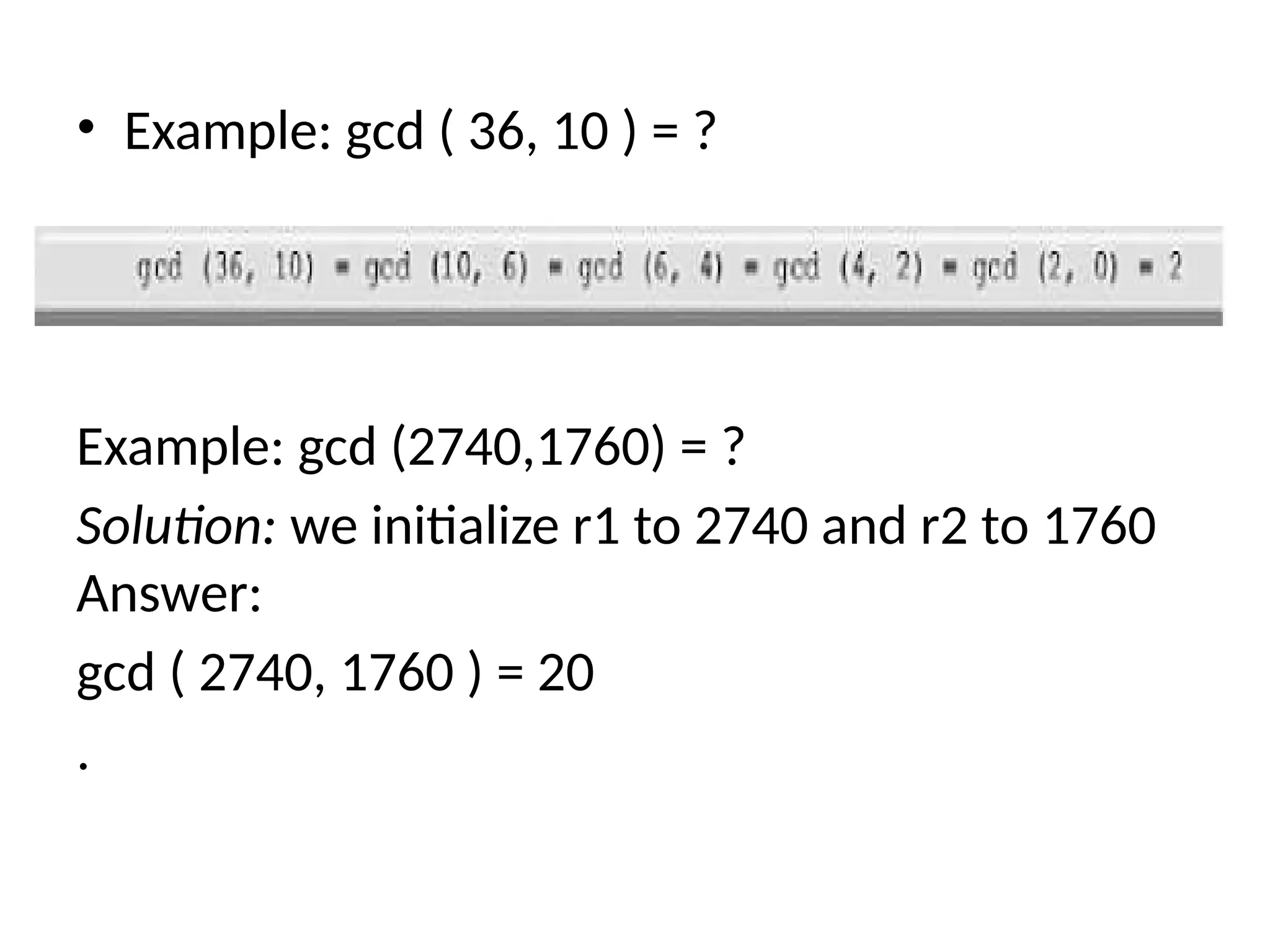
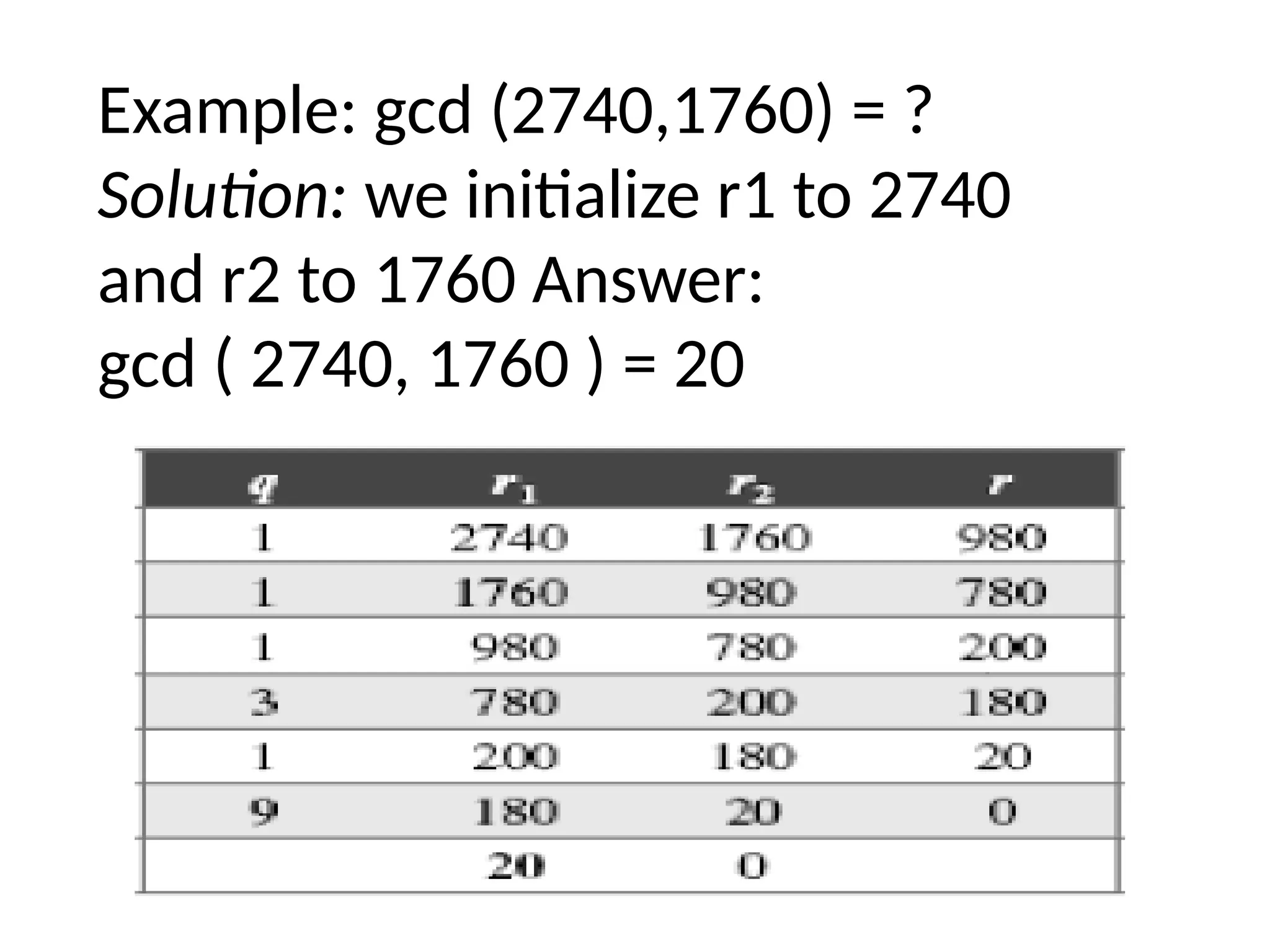
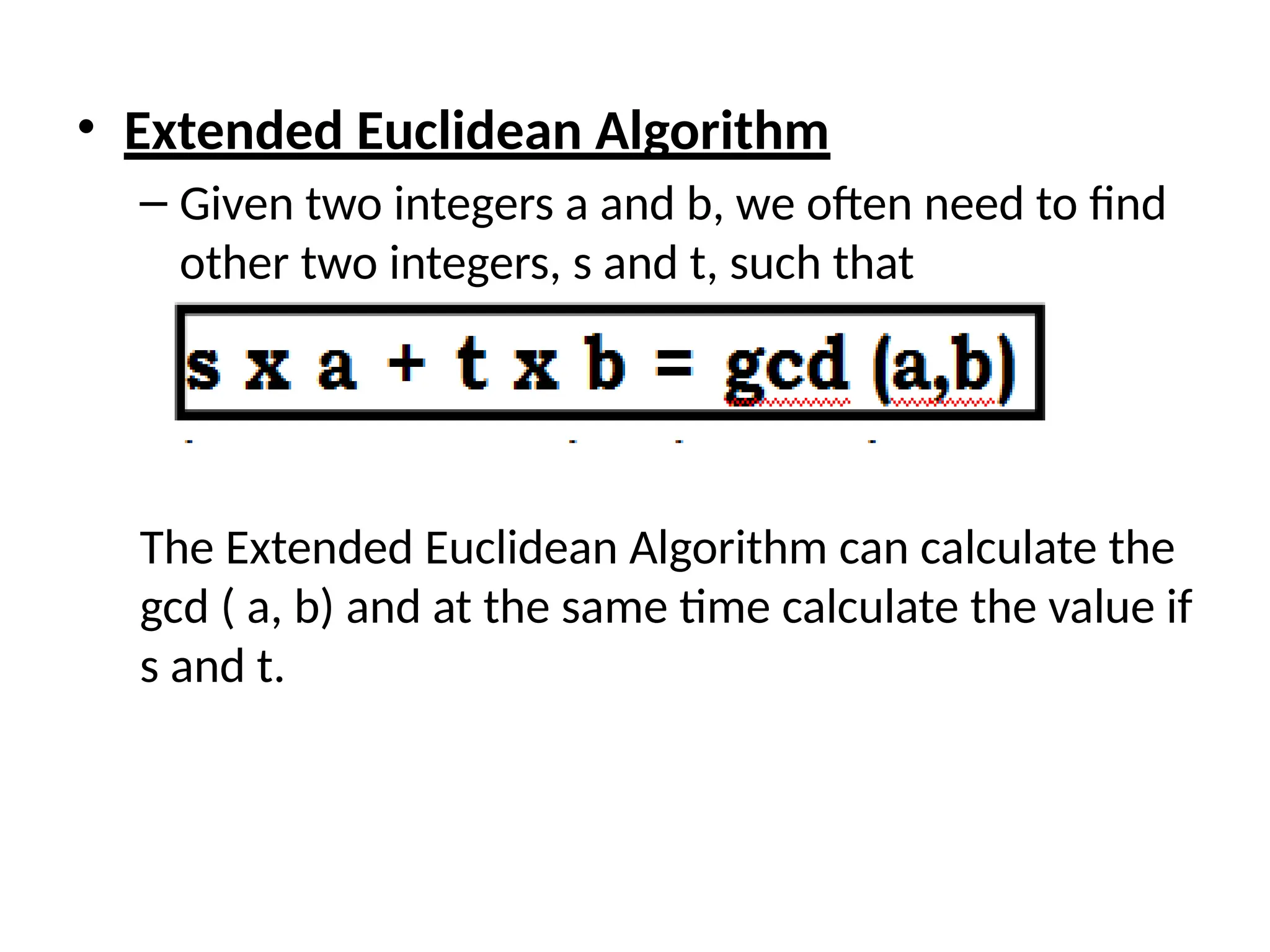
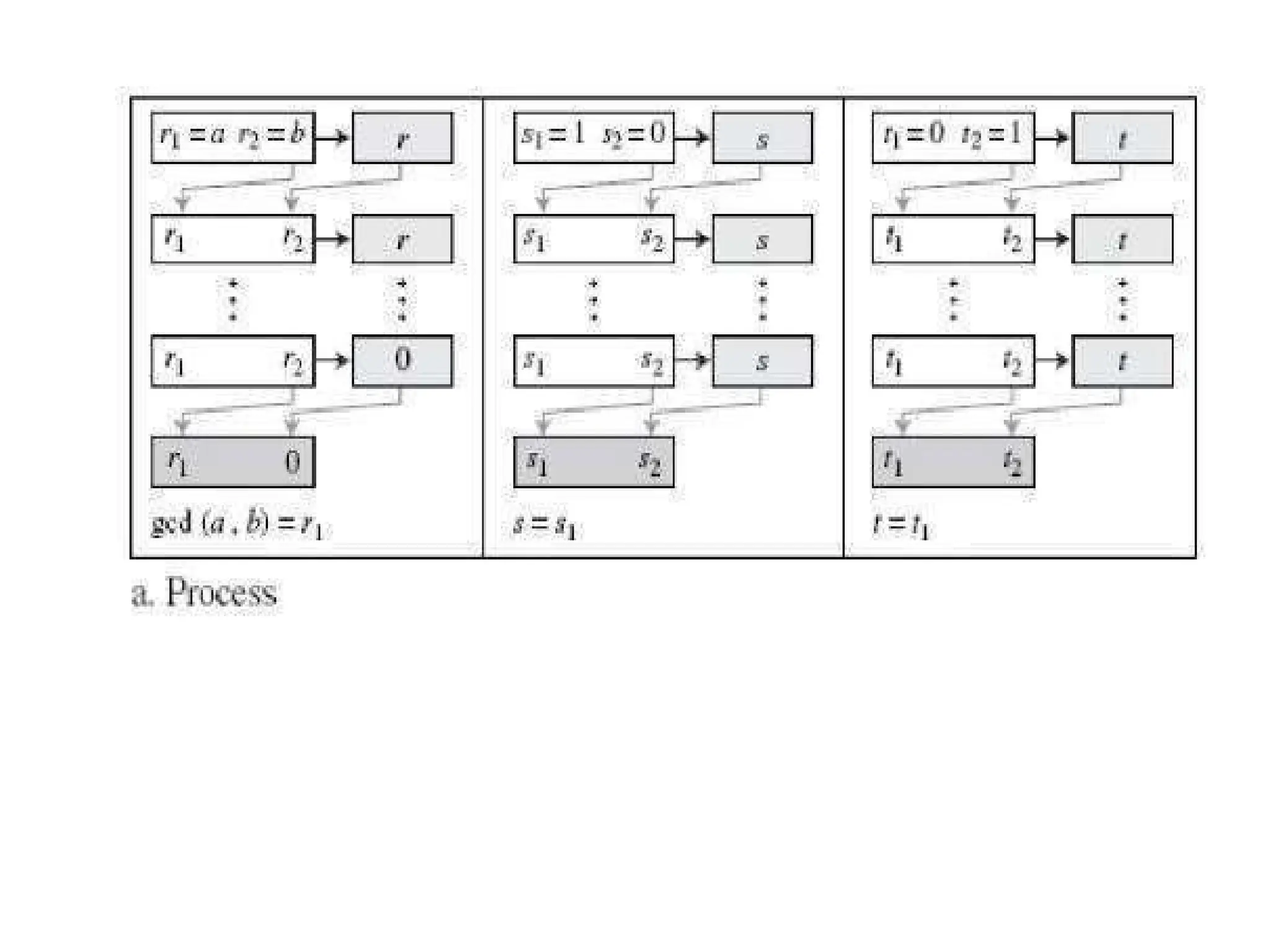
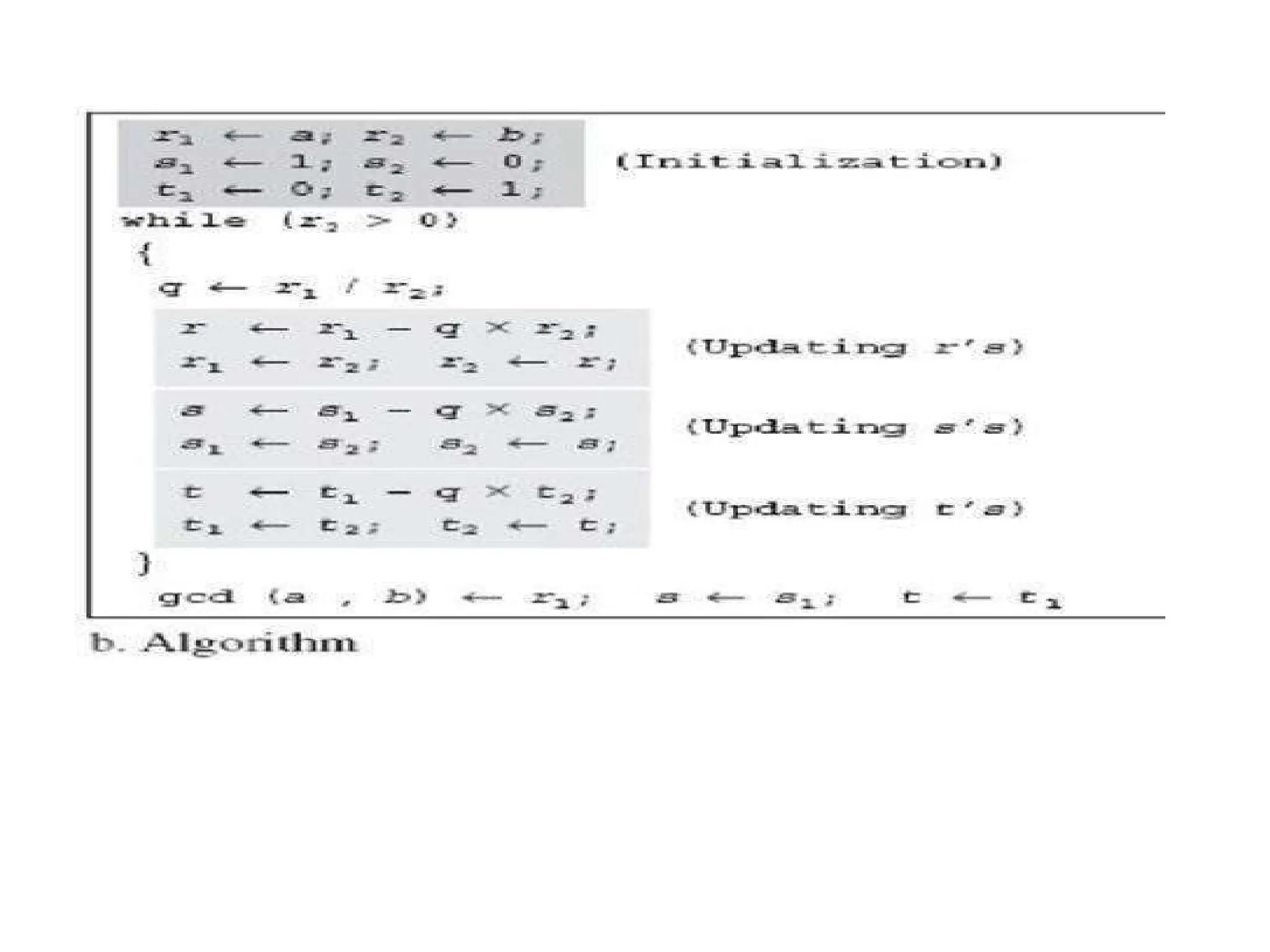
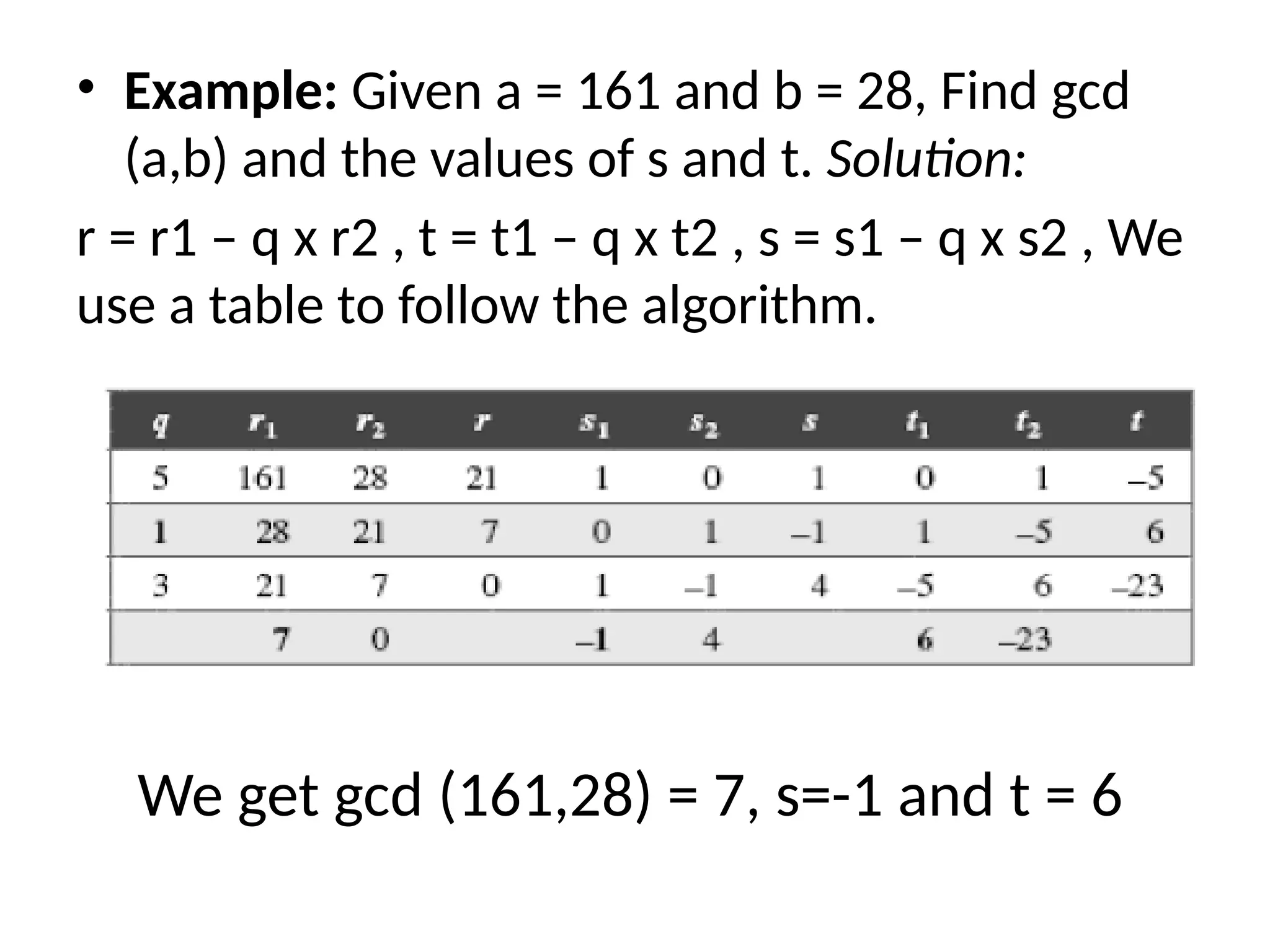
The document provides an overview of cryptography and network security, discussing core concepts such as plaintext, ciphertext, encryption, and various types of attacks (active and passive). It outlines security goals and mechanisms, including data confidentiality, integrity, authentication, and access control while highlighting cryptographic attacks and their classifications. Additionally, it covers the mathematics of cryptography, focusing on integer arithmetic, divisibility, and the Euclidean algorithm for finding the greatest common divisor.