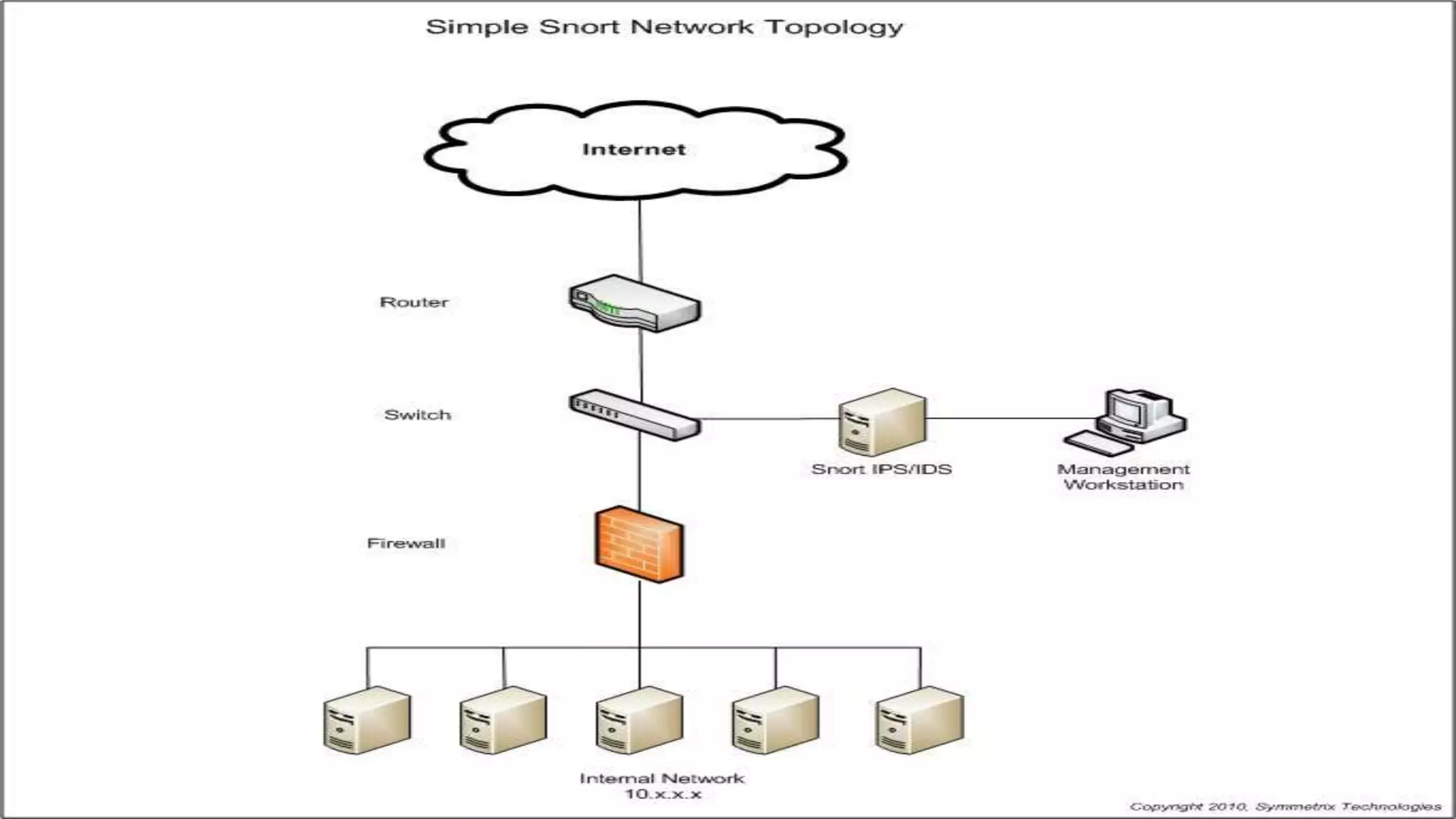
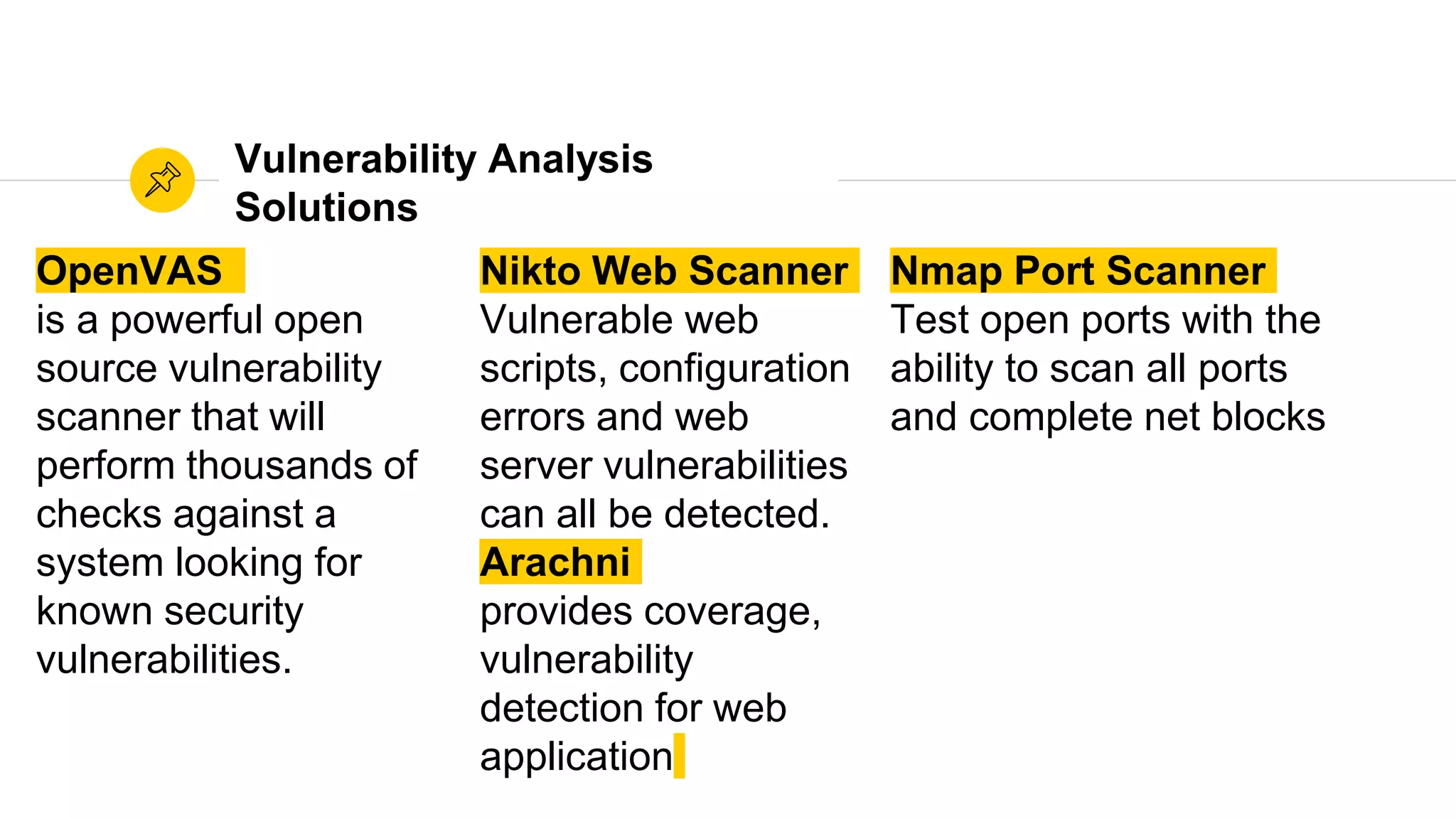
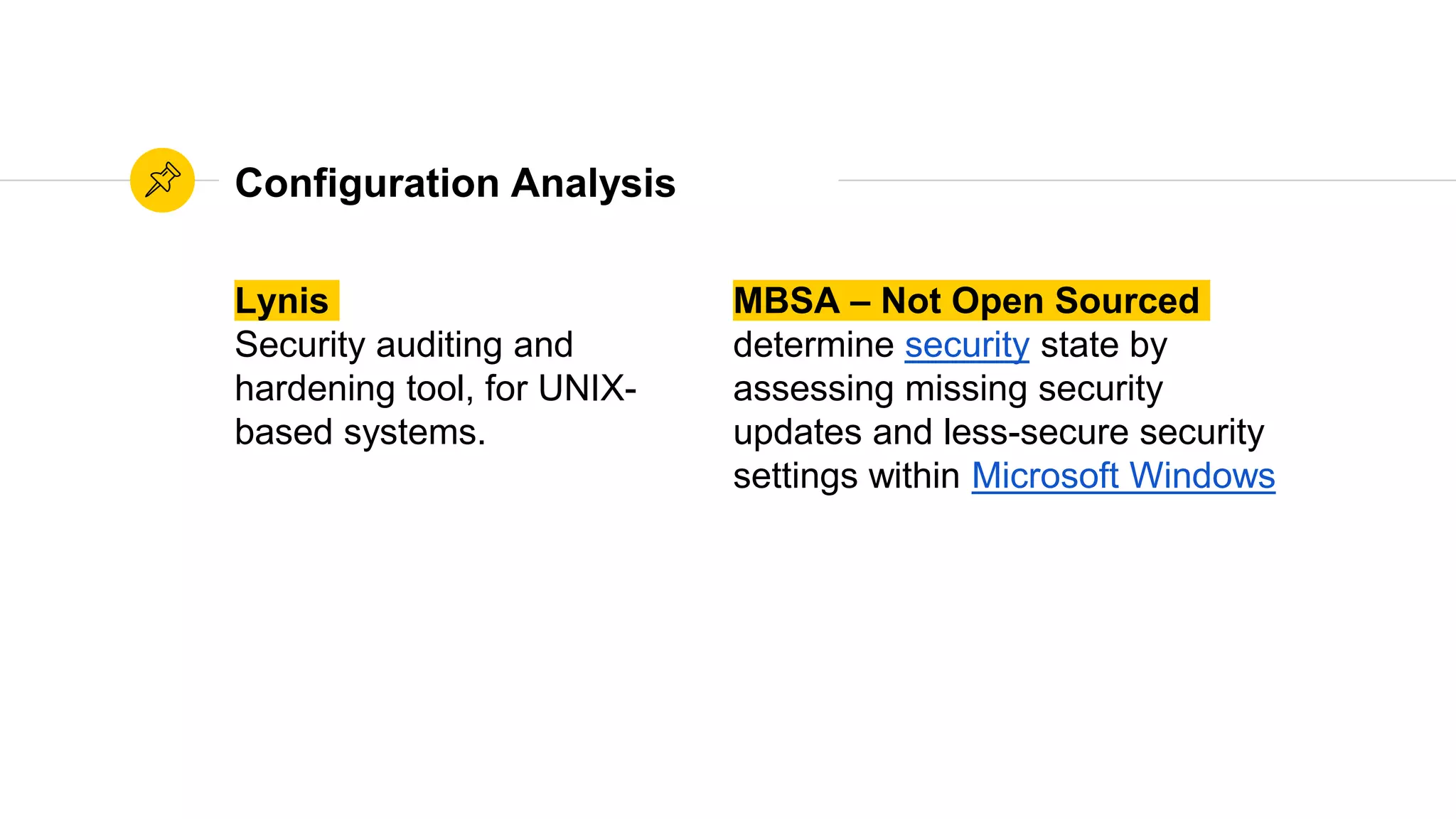
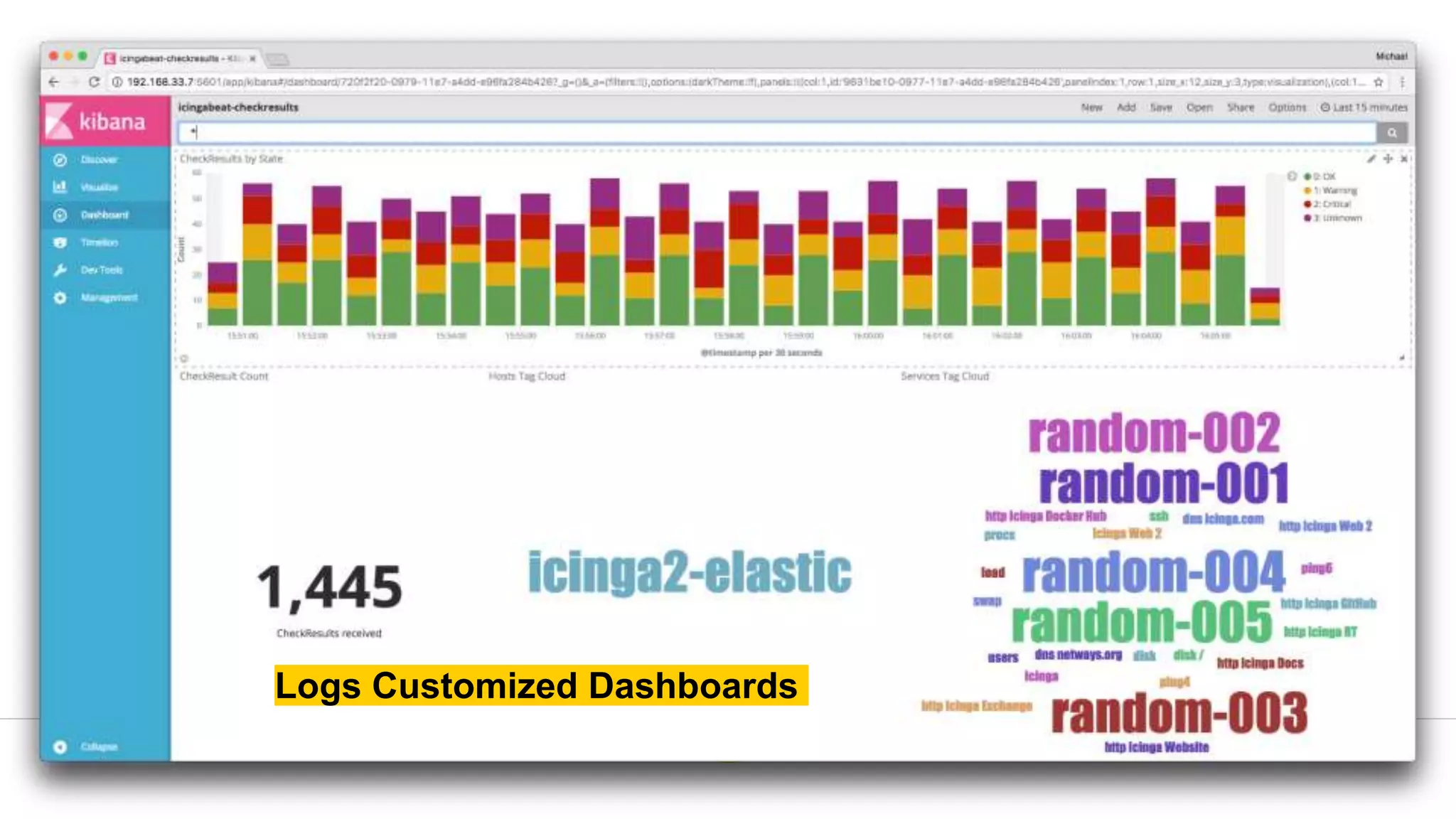
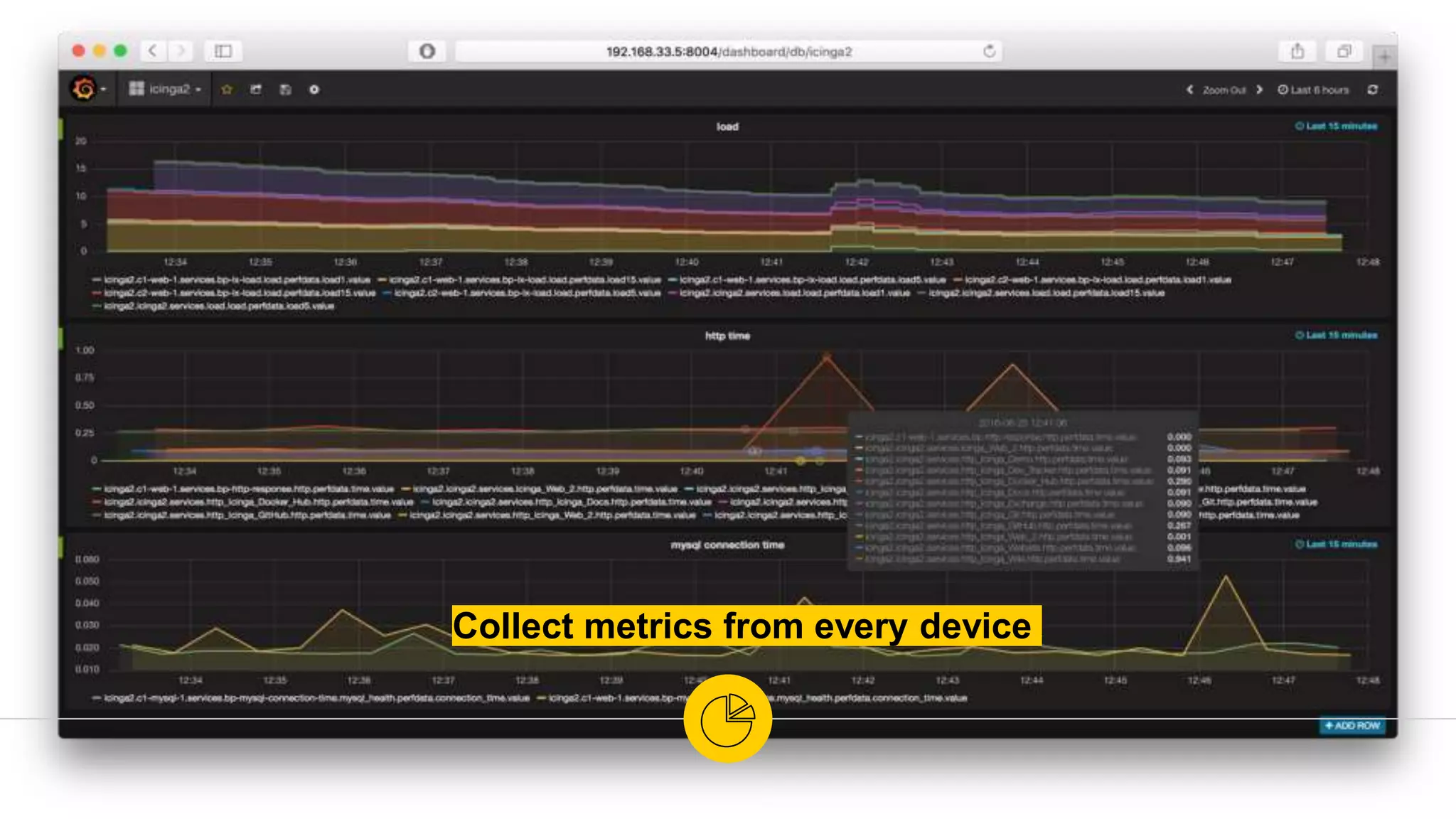
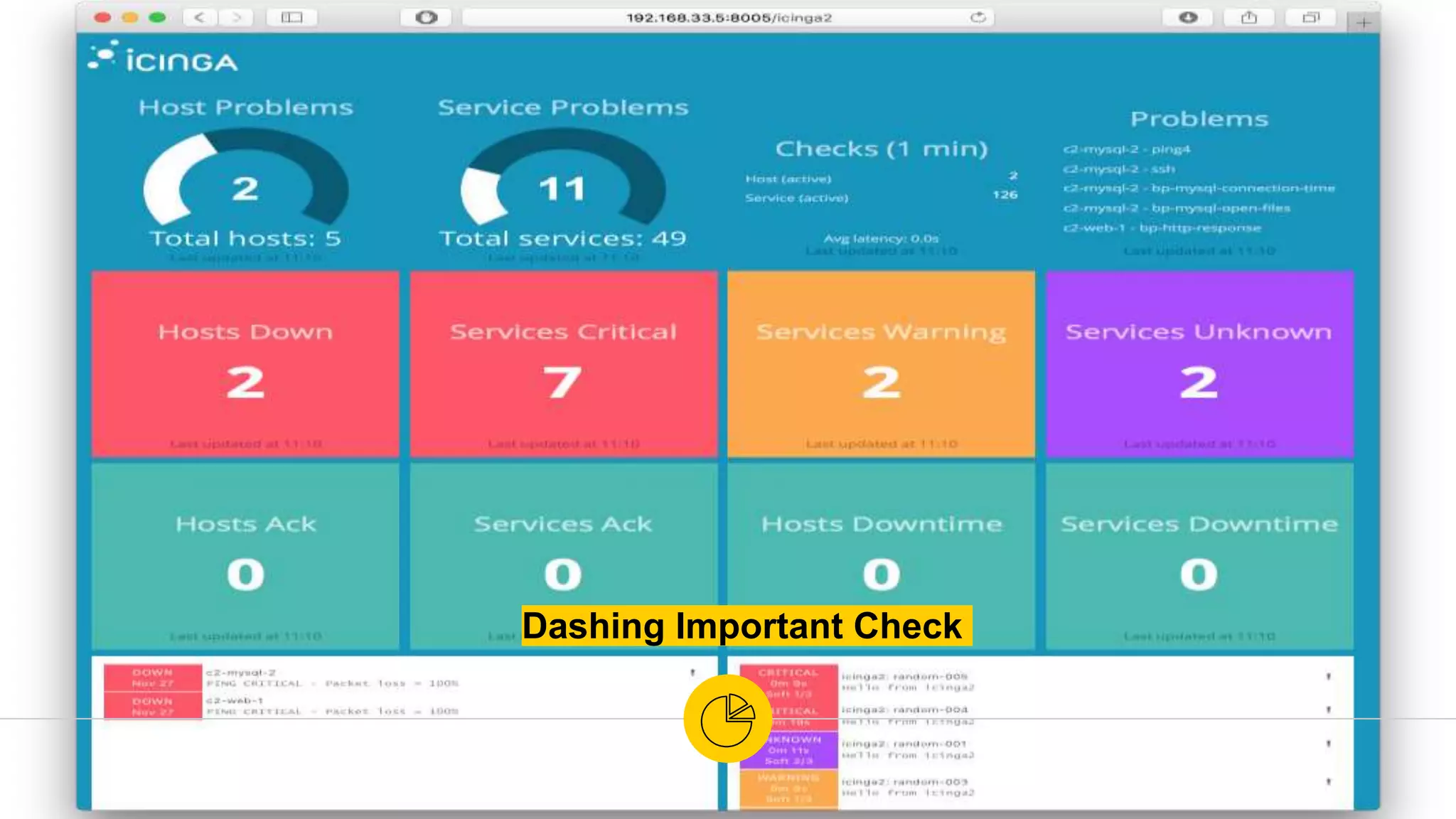
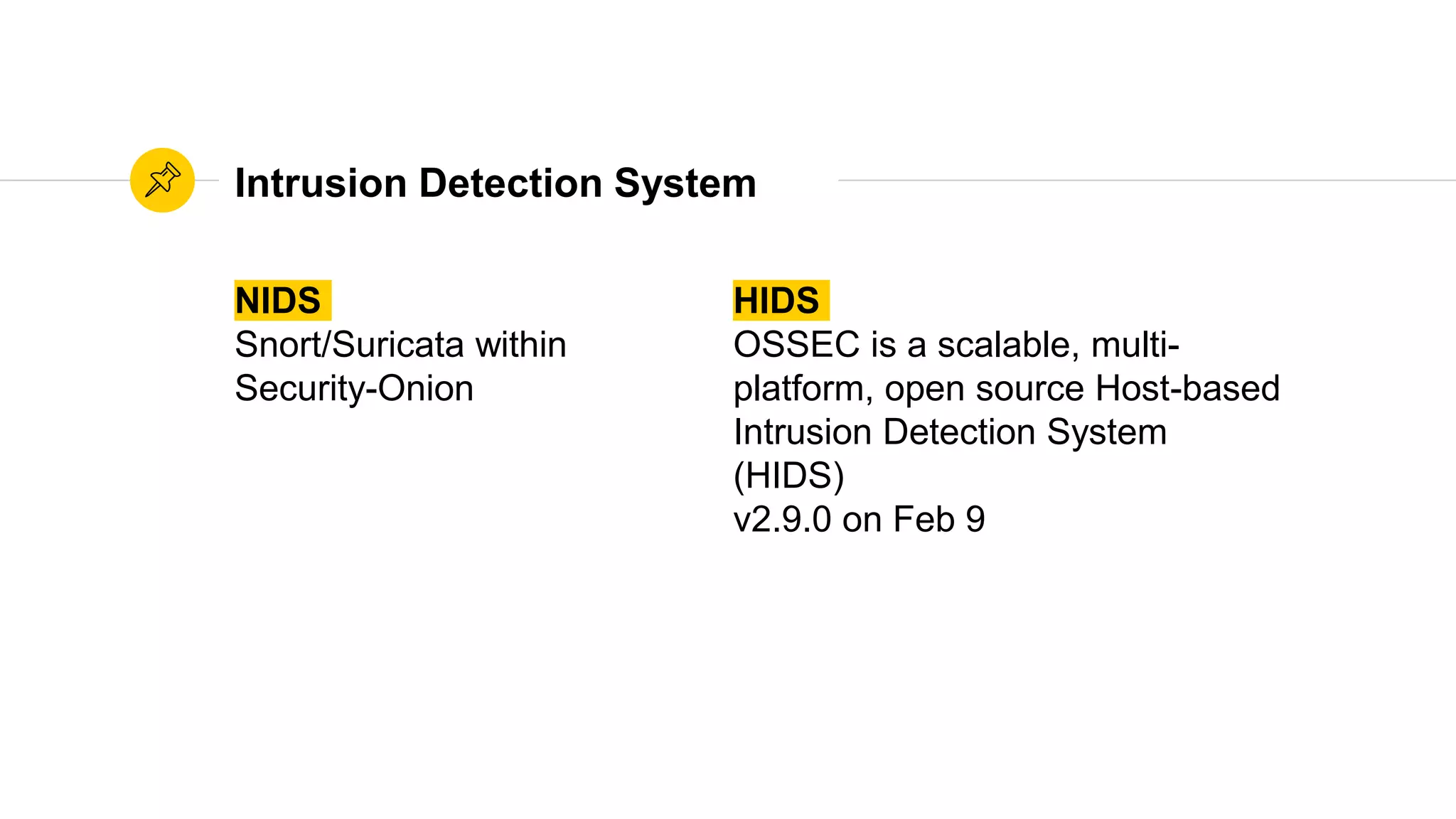
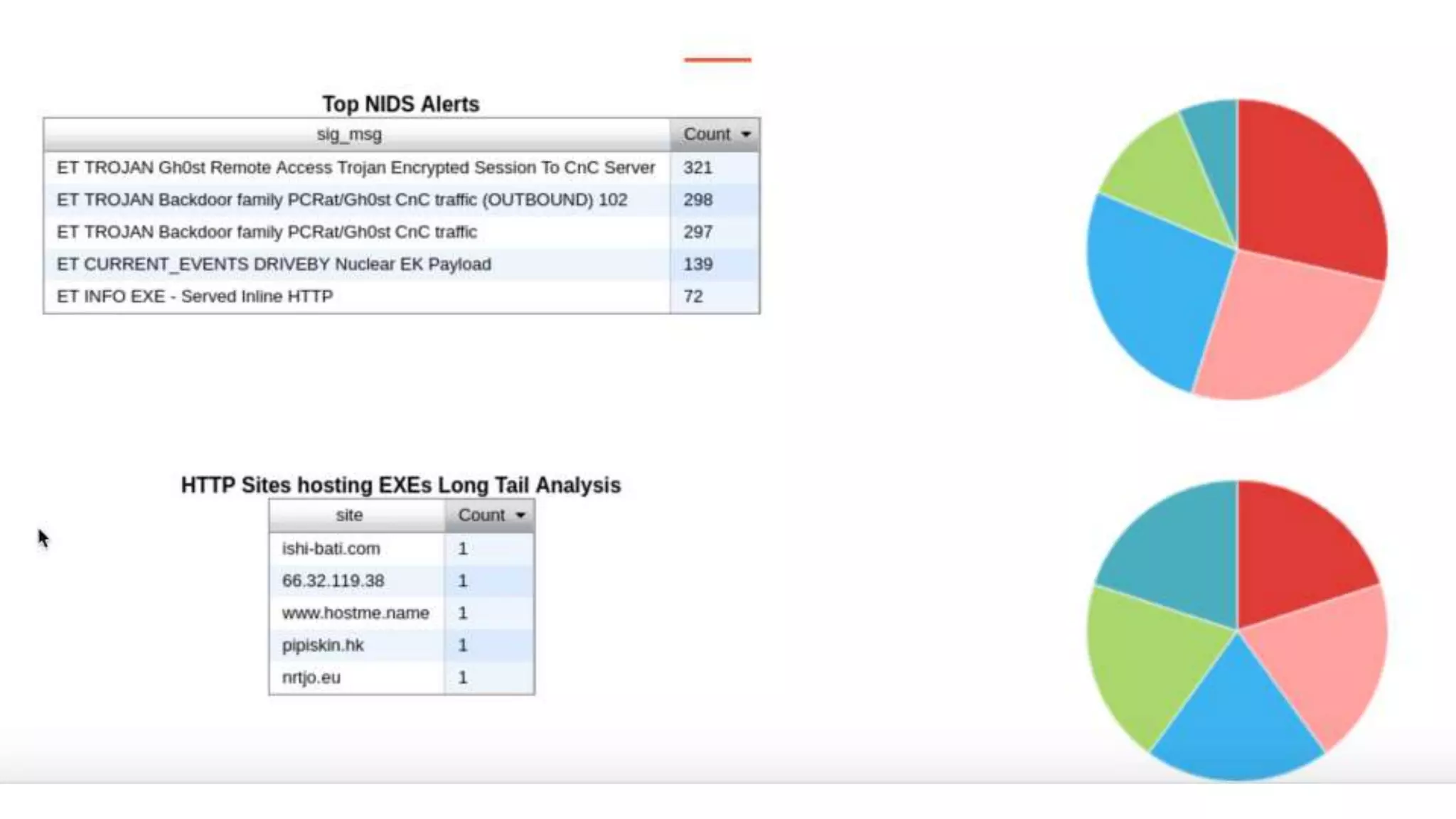
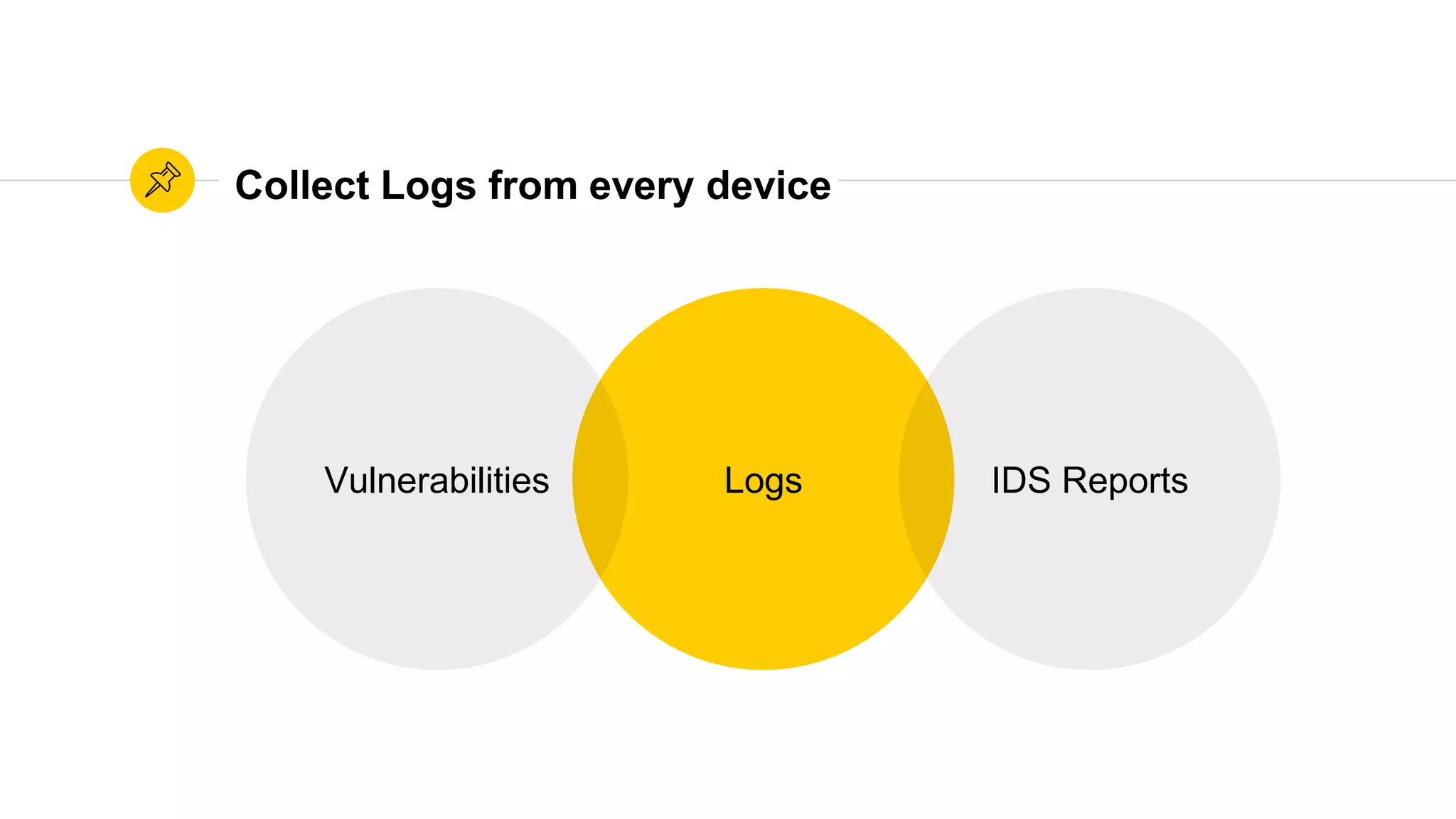
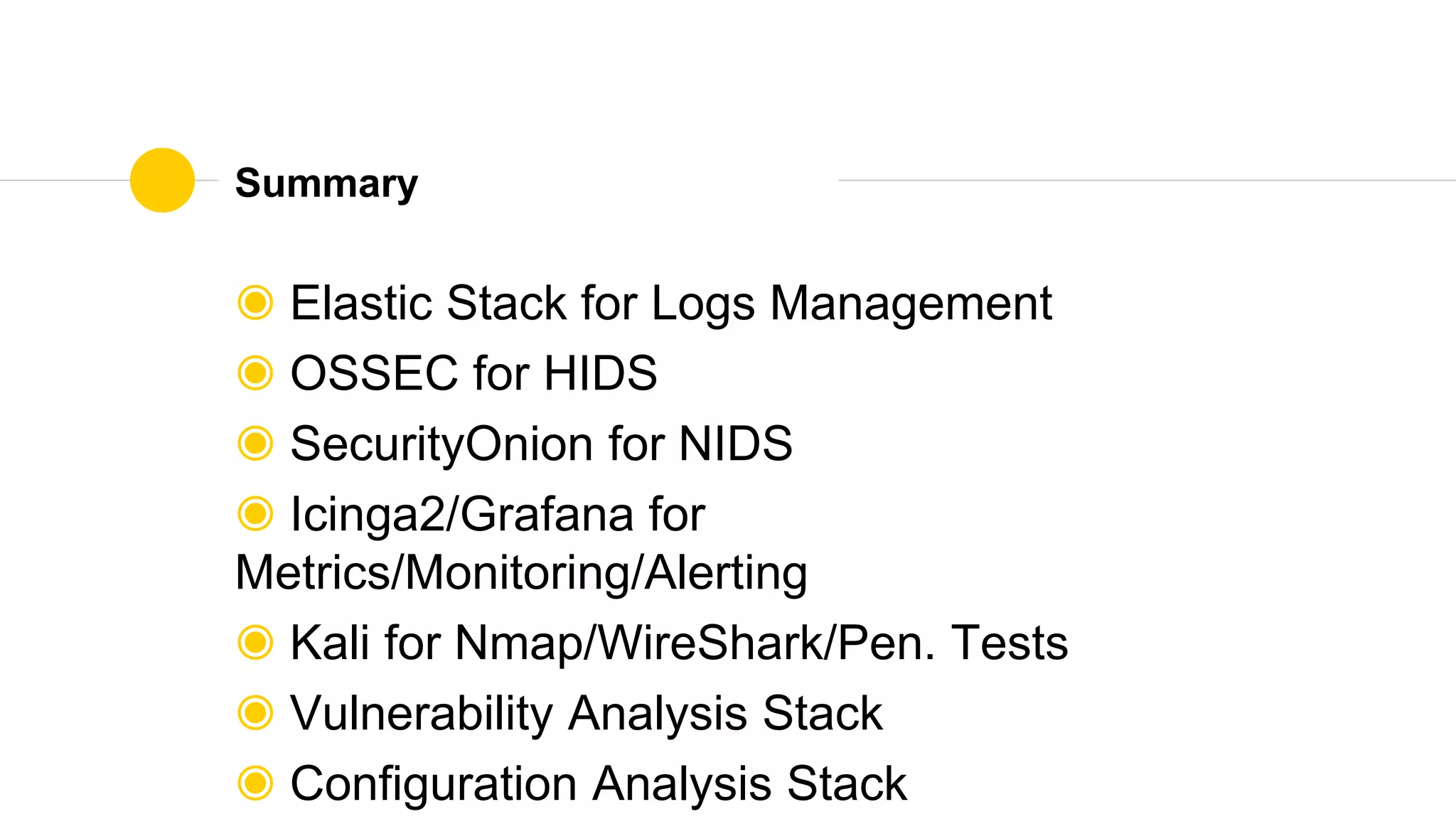
The document is a presentation on utilizing open source tools to enhance network security, presented by Mohamed Almusaddar. It outlines a five-stage DIY process for network security, encompassing vulnerability analysis, configuration analysis, log analysis, monitoring and alerting, and intrusion detection systems, along with recommended open source tools for each stage. Additional resources, including slides, code, and demos, will be available on the presenter's blog and GitHub.