The document discusses a framework for re-computing processes that are subject to multiple change events in software and data dependencies. It introduces concepts like change front, re-computation front, and restart tree, aimed at enabling efficient updates of past process outcomes based on changes. The proposed algorithm for identifying the re-computation front is effective and available on GitHub, marking a step towards optimizing execution in complex hierarchical workflows.

![Problem Outline
• Consider process P, e.g. the following NGS pipeline [5]:
[5] Cała, J., Marei, E., Xu, Y., Takeda, K., Missier, P.: Scalable and efficient whole-exome data processing using workflows on the cloud.
Future Generation Computer Systems (Jan 2016).](https://image.slidesharecdn.com/2018-07-09ipawprovenanceannotationandanalysis-180709151905/85/Provenance-Annotation-and-Analysis-to-Support-Process-Re-Computation-2-320.jpg)
![Problem Outline
• Only rarely P is a static entity.
• Usually, a variety of elements in P change:
• data dependencies,
• software tools & dependencies,
• [out of scope] the structure of P.
• Changes in the elements of P
=> the need to update past P outcomes
=> the need for re-computation.](https://image.slidesharecdn.com/2018-07-09ipawprovenanceannotationandanalysis-180709151905/85/Provenance-Annotation-and-Analysis-to-Support-Process-Re-Computation-3-320.jpg)
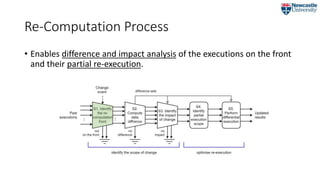
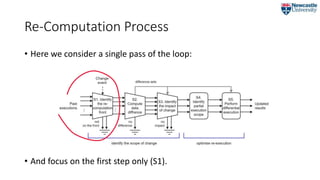
![The Re-Computation Framework
• To control the re-computation of processes
• proposed earlier in [6].
• The core of the framework is
the re-computation loop:
[6] Cała, J., Missier, P.: Selective and recurring re-computation of Big Data analytics
tasks: insights from a Genomics case study. Big Data Research (2018); in press.](https://image.slidesharecdn.com/2018-07-09ipawprovenanceannotationandanalysis-180709151905/85/Provenance-Annotation-and-Analysis-to-Support-Process-Re-Computation-4-320.jpg)
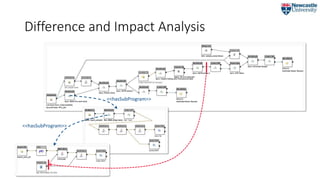
![Preliminaries
• The ProvONE model: prospective + retrospective provenance [7].
• Set of software and data dependencies: D ={a0, b0, …}
• Process, input and execution configuration: E(P, x,V)
• Version change event: C = {an → an-1}
• Composite version change event: C = {an → an-1, bm → bm-1, …}
• Change front.
• Re-computation front.
• Restart tree.
[7] Cuevas-Vicenttín, V., Ludäscher, B., Missier, P., et al.: ProvONE: A PROV Extension Data Model for Scientific Workflow Provenance (2016).](https://image.slidesharecdn.com/2018-07-09ipawprovenanceannotationandanalysis-180709151905/85/Provenance-Annotation-and-Analysis-to-Support-Process-Re-Computation-6-320.jpg)
![Change Front
• The accumulation of change events over a specified time window.
t
C0
{a1 → a0}
CF3
{a3, b1, c2}
CF5
{a3, b2, c2, d1}
C1
{b1 → b0}
C3
{a3 → a2, c2 → c1}
C4
{d1 → d0}
C5
{b2 → b1}
C2
{a2 → a1, c1 → c0}
E(…, [a0, b0, e0])
E(…, [a0, b1, d0])
E(…, [a2, b1, c1])](https://image.slidesharecdn.com/2018-07-09ipawprovenanceannotationandanalysis-180709151905/85/Provenance-Annotation-and-Analysis-to-Support-Process-Re-Computation-7-320.jpg)

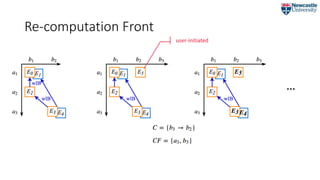
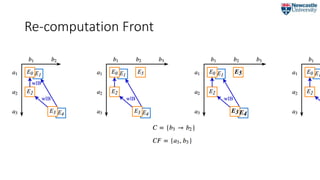
![Re-computation Front
We use:
wasInformedBy(..., [prov:type=“recomp:re-execution”])
to denote a ReComp-initiated re-execution.](https://image.slidesharecdn.com/2018-07-09ipawprovenanceannotationandanalysis-180709151905/85/Provenance-Annotation-and-Analysis-to-Support-Process-Re-Computation-9-320.jpg)
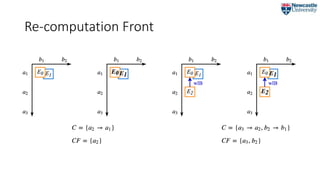

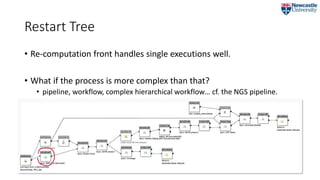
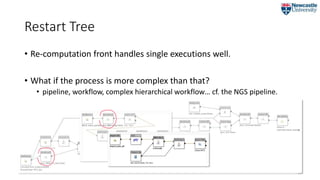
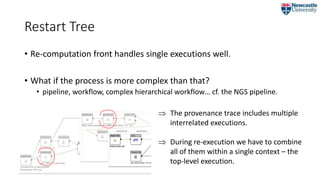
![Restart Tree
• Captures the vertical dimension of a single execution
• the transitive closure of the wasPartOf relation.
RT ≝ {Execution, [DataChange], [Children]}
CF = {b2, e1}](https://image.slidesharecdn.com/2018-07-09ipawprovenanceannotationandanalysis-180709151905/85/Provenance-Annotation-and-Analysis-to-Support-Process-Re-Computation-19-320.jpg)
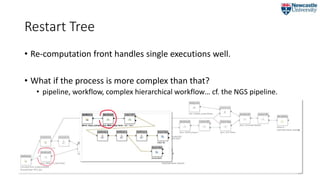
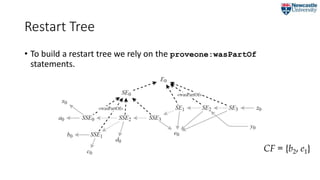
![Restart Tree
• Captures the vertical dimension of a single execution
• the transitive closure of the wasPartOf relation.
RT = {E0, [], [{SE0, [], [{SSE1, [⟨b2 → b0⟩], []},{SSE3, [⟨e1 → e0⟩], []}]}, {SE1, …}, …]}
CF = {b2, e1}](https://image.slidesharecdn.com/2018-07-09ipawprovenanceannotationandanalysis-180709151905/85/Provenance-Annotation-and-Analysis-to-Support-Process-Re-Computation-20-320.jpg)