Embed presentation
Download as PDF, PPTX























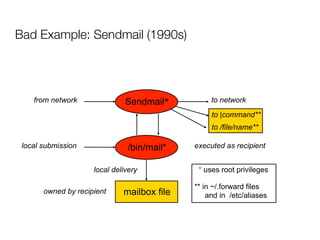
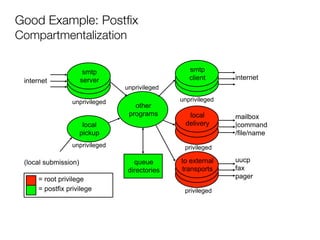
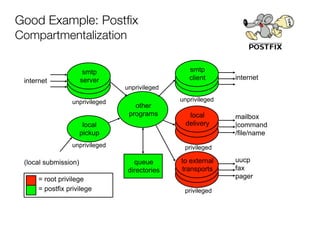


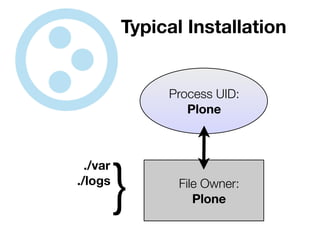
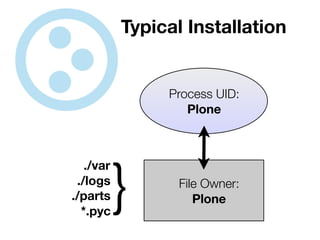


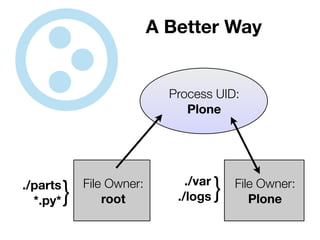


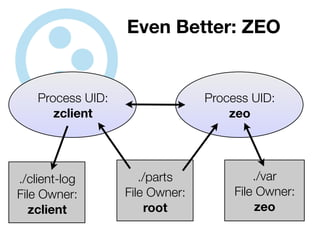




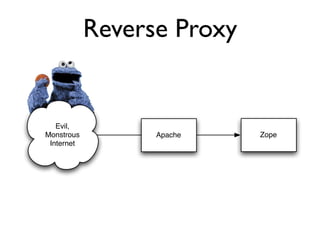
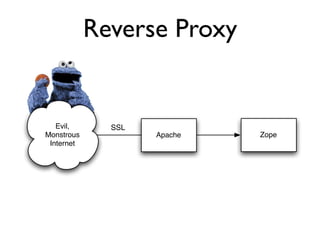
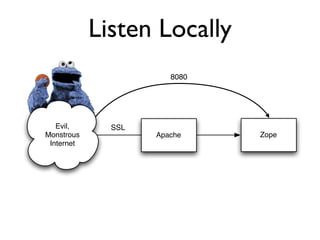
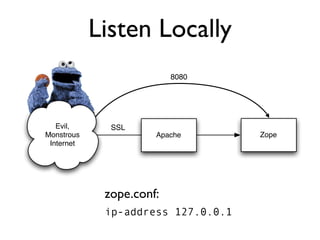
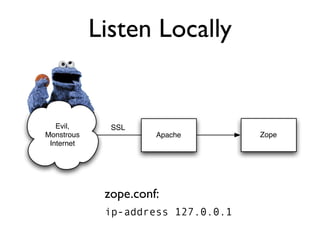
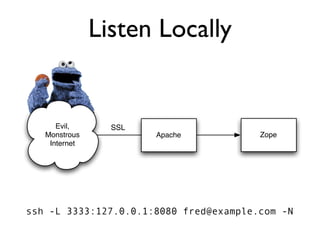
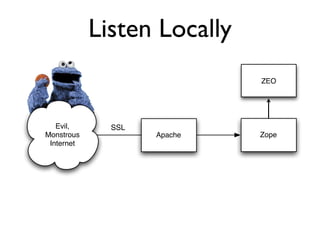
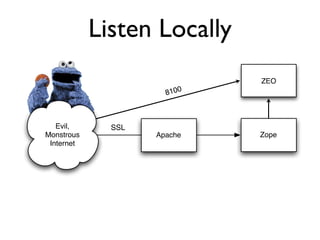
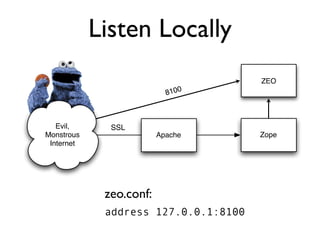
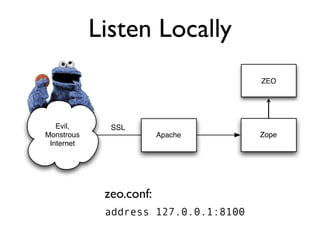
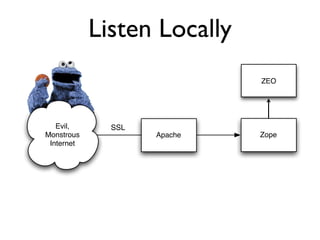
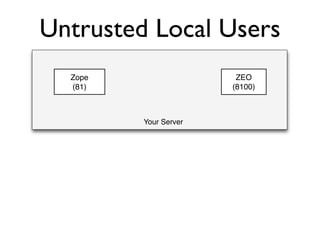
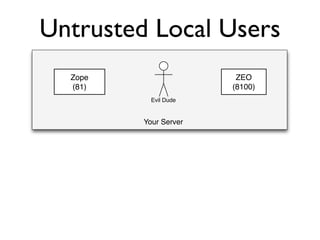
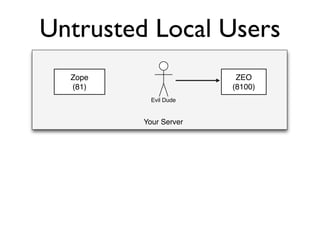
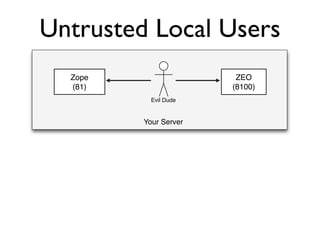
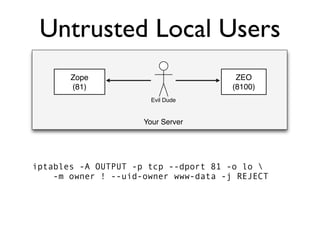
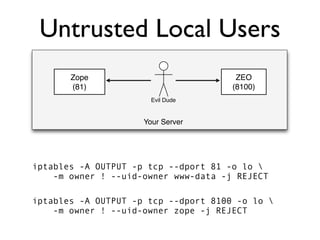
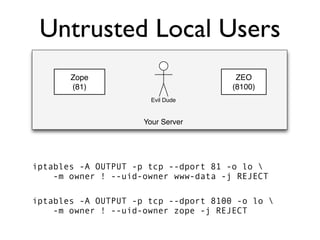

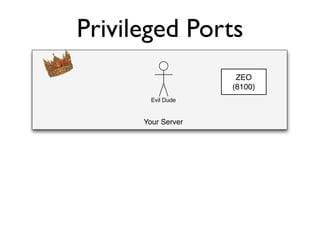

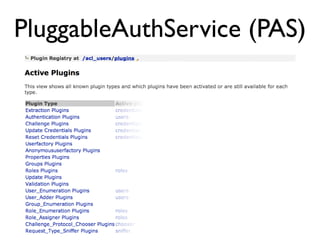


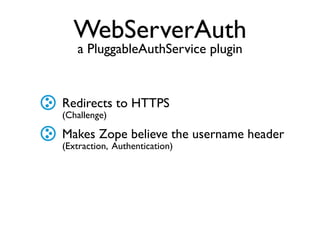


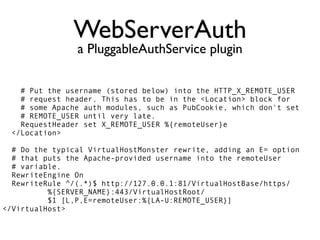

















The document discusses the security vulnerabilities of Plone, specifically versions 2.5 through 3.0. It emphasizes the importance of defense in depth and the principle of least privilege, while also detailing specific security implementations and best practices for protecting against remote code execution vulnerabilities. The document further explores various components such as Pluggable Authentication Services, reverse proxies, and integration with LDAP for user management.
































































































