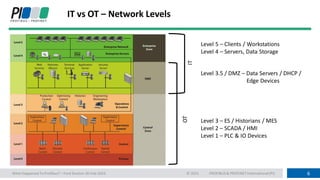
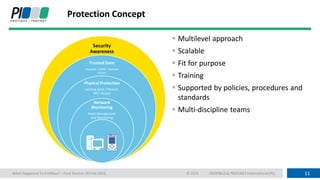
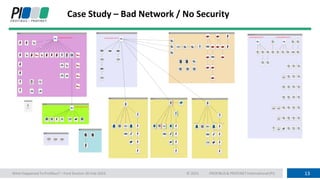
This document discusses operational technology (OT) cyber security. It begins by explaining why OT networks need security due to the merging of IT and OT networks, which has exposed OT assets to compromise. It then describes the differences between IT and OT approaches, with OT prioritizing control, availability, integrity and confidentiality over just data. Several common attack paths for OT networks are outlined, including social engineering, malware from removable devices, and internet-connected components. The document advocates for a multi-layered protection concept including security awareness training, firewalls, physical protection and network monitoring. It stresses that security should be considered from the initial design phase.