This document discusses and dispels four common myths about process security:
Myth One: Even systems claimed to not be connected to the internet have been found to be connected through investigations.
Myth Two: Viruses have been found on every system checked, with a 100% detection rate.
Myth Three: Viruses have been seen transmitted via infected USB drives, hard drives and laptops, even from "trusted" vendors.
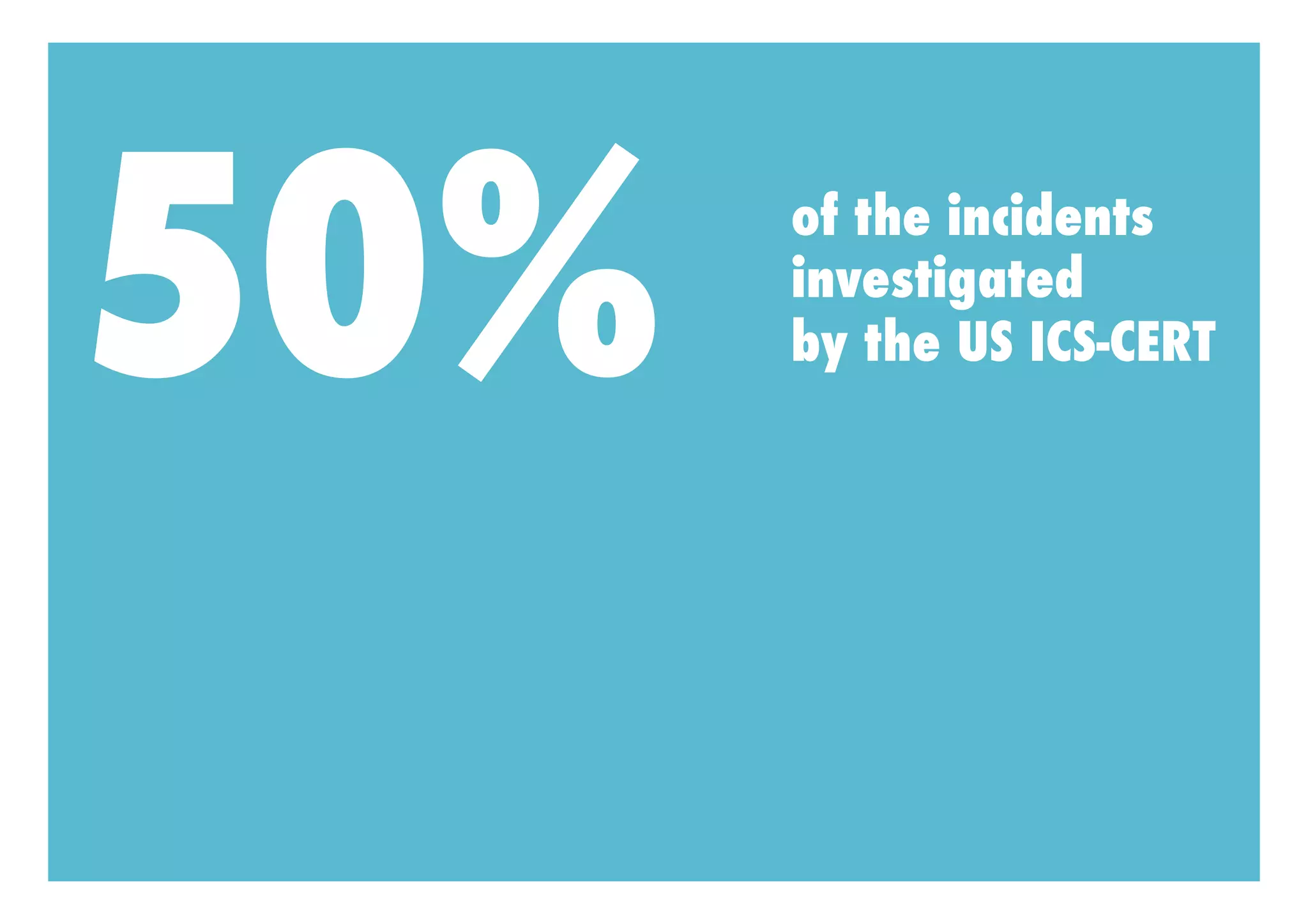
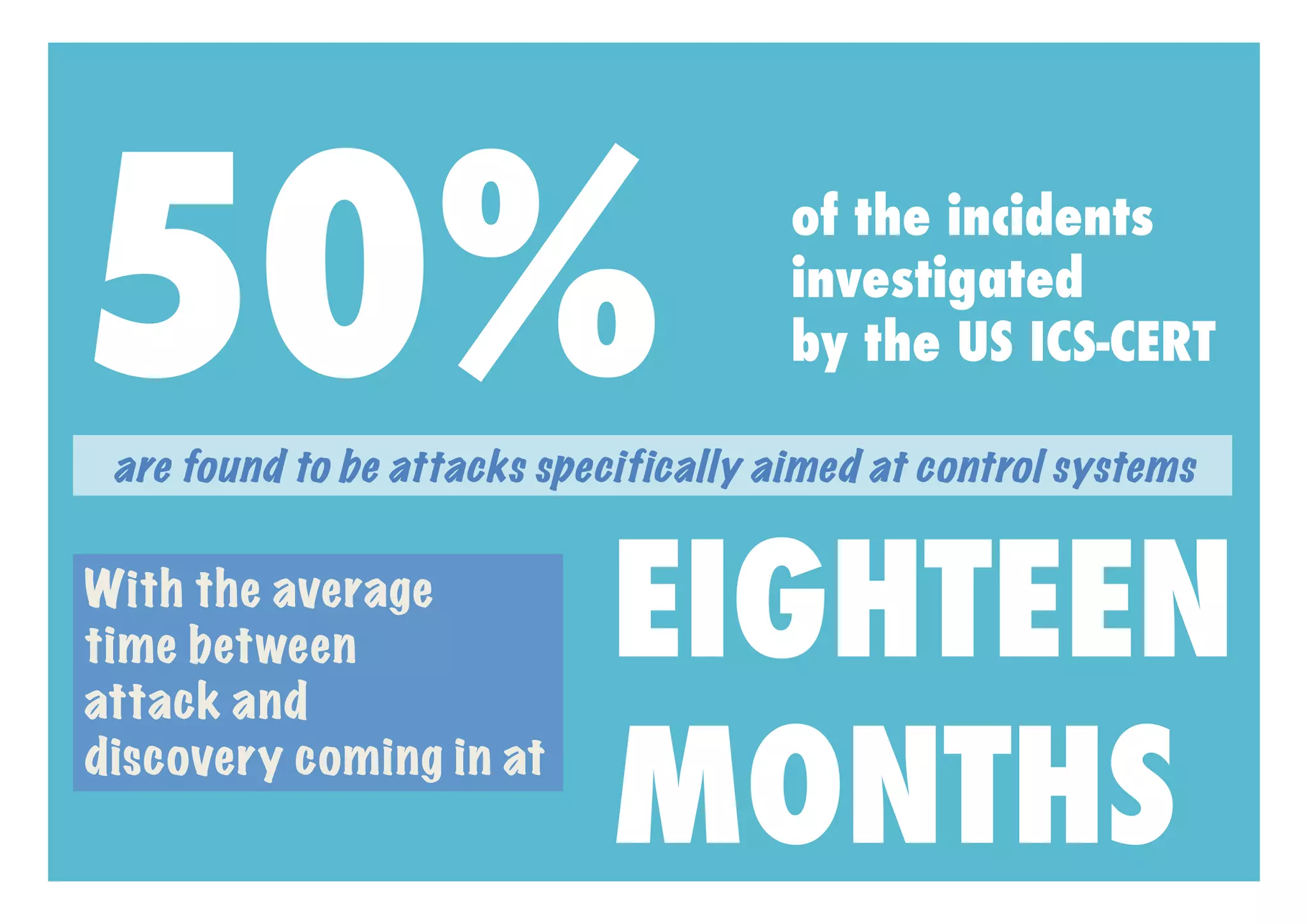
Myth Four: 50% of incidents investigated by US ICS-CERT were attacks aimed at control systems, with the average time between attack and discovery being 18 months.