The document discusses the implications of social media on employee privacy and employer interests, highlighting legal protections for employees, monitoring methods, and case law influencing privacy expectations. It underscores the challenges posed by social media use, including misunderstandings and potential legal ramifications, while also emphasizing the role of employer policies and federal statutes like the Electronic Communications Privacy Act. Additionally, the paper examines various court rulings that shape the landscape of employee rights regarding digital communications and social media interactions.



![Types of Social Media Sites
Sharing of all sorts of things
News & Articles [blogs, news
aggregators]
Information [chat rooms, IMs, texts]
Images [Flickr, Picasa, Google
Images, iReporter]
Knowledge [Wikipedia]
5](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-5-320.jpg)








![Federal Statutes
Electronic Communications Privacy Act of 1986,
amending the Wiretapping Act
FACTA: Fair & Accurate Credit Transaction Act of
2003, amending the Fair Credit Reporting Act
[FCRA]
Health Insurance Portability & Accountability Act of
1996 [“HIPAA”], 42 U.S.C. § 1302(d) & regulations
no private right of action under HIPAA, go thru
HHS & Department of Justice
14](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-14-320.jpg)


![Methods of Monitoring
Telephone
Computer [keystroke monitoring]
Mail, eMail,
Voicemail
Video surveillance
Social Media
17](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-17-320.jpg)
![Cautions re Monitoring
Depends on application of EPCA, Federal and
State* Laws, Employer policies and assurances.
Telephone
Computer [keystroke monitoring]
Mail, eMail [not private if employer’s terminal]
Voicemail, IMs
Video surveillance
Social Media
*Note: Iowa differs from California, etc.
18](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-18-320.jpg)

![Government Employees
O’Connor v. Ortega [1987]: 4th
Amendment applies == the question is
whether the employee
has a reasonable expectation of privacy in
area searched
whether employer’s search of area was
reasonable under circumstances: “context”
20](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-20-320.jpg)




![Private Employee Rights
Must be provided a copy of his or her personnel file, under
Section 91B, Iowa Code
ADA & ICRA Protections ref. medical information; see
ADA § 12112(d)(3)(B) & 29 CFR § 1630.14(b)(1)
Electronic Communications Privacy Act [ECPA];
digital privacy protections, outstripped by
technology
25](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-25-320.jpg)


![Unionized Employees
Brewers & Maltsters, Local No. 6, D.C.
Cir. 2005 [NLRB]:
secretive installation of hidden
surveillance cameras in workplace
violated NLRA because their use was a
subject of bargaining
28](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-28-320.jpg)

![NLRB v. American Medical Response
NLRA gives employees rights to complain
about pay, safety and other working
conditions.
AMR: employee who called her supervisor
a “scumbag” [and worse] on Facebook
from home computer could not be fired -
postings were made in online discussion
among employees about supervisory
action, provoked by unlawful denial of
union representation.
30](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-30-320.jpg)

![Huffington Post: “Fired over Facebook, 13 Posts
that Got People CANNED”
surfing FB while home ‘sick’
FB posted photos caused firing of professional football
cheerleader
13 crew members on Virgin Atlantic participated in FB
discussion; references to passengers & bringing company into
disrepute
fired for a derogatory, mocking FB group that mocked
customers
high school teacher for FB photos with wine, beer & expletive
posting of video derogatory of employer; exposing patient
confidential information [HIPPA violation]
32](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-32-320.jpg)
![TSA Agent - anti-Muslim, racist FB comments
Doctor fired after posting information about a
trauma patient on FB page, even if did not
reveal name
State police officer fired because of FB photos
and comments about being drunk
Professor fired after posting about a failing
student; teacher fired for joking about
drowning her students
[search, Huffington Post, “fired over Facebook”; not all firings
were upheld]
33](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-33-320.jpg)

![Wiretapping & Eavesdropping
“Get a good night’s sleep, and don’t
bug anybody without asking me.”
Richard M. Nixon to re-election campaign manager
Clark MacGregor, recorded on tape [Christian
Science Monitor, 8/14/80]
35](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-35-320.jpg)




![Can we Use the Information?
Genetic Nondiscrimination Act of 2008
[GINA]; illegal to use or discriminate because of
‘genetic information’
“Genetic Information” broadly defined [disease/disorder in
family]
Exceptions for inadvertent disclosure, etc.
Example: Employee fired a week after mentioning that her
mother had died of Huntington’s disease and she had 50%
chance of developing it.
in context of social media: mention of such on blog, FB,
etc. in casual conversation which is then known to
employer - Q whether ‘inadvertent’ or not?
40](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-40-320.jpg)
![1986 Electronic Communications Privacy Act
[ECPA], 18 U.S.C. § 2510 et. seq.
prohibits interception of wire, oral or
electronic communications
ECPA added prohibition against
interception or accessing electronic
communications
Warrant requires to obtain emails stored up
to 180 days, not afterward
41](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-41-320.jpg)

![United States v. Jones, U.S.S.Ct., decided
Jan 2012: GPS Satellite monitoring of
vehicle’s movements is a “search” and violates
the 4th Amendment to the U.S. Constitution.
-- Earlier cases [Karo, Knotts] in
U.S.S.Ct. had allowed use of a
monitoring device while moving in
public or if limited in extent.
43](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-43-320.jpg)
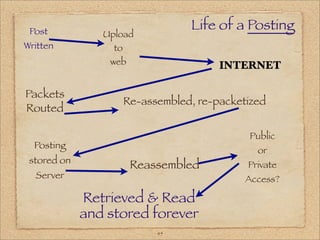
![Life of an Email
Email message
Written [computer] packetized
INTERNET
Packets Packet Re-packetized
Routed Reassembled
& Copied
Message Received at
Stored Reassembled Mailserver
Retrieved & Read
44](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-44-320.jpg)




![Risk to Employers: Failing to treat social
media abuse differently from harassment
Kiesau v. Bantz, 686 N.W.2d 164 [Iowa
2004]: emailed photoshopped image
resulted in $150,000 judgment plus
possibility of more for failure to
properly supervise
51](https://image.slidesharecdn.com/privacysocialmedia020512-120205125700-phpapp02/85/Privacy-and-Social-Media-51-320.jpg)

