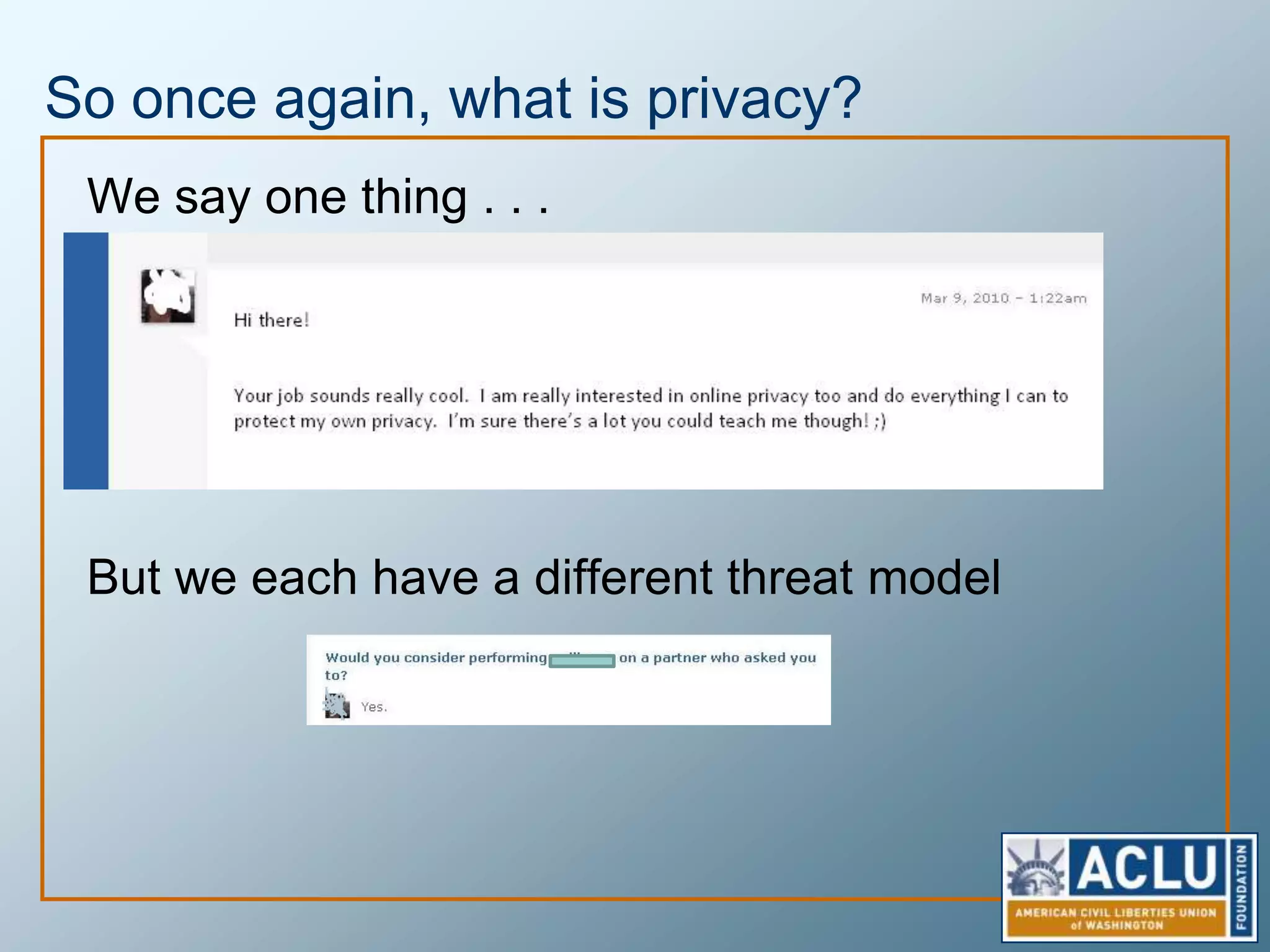
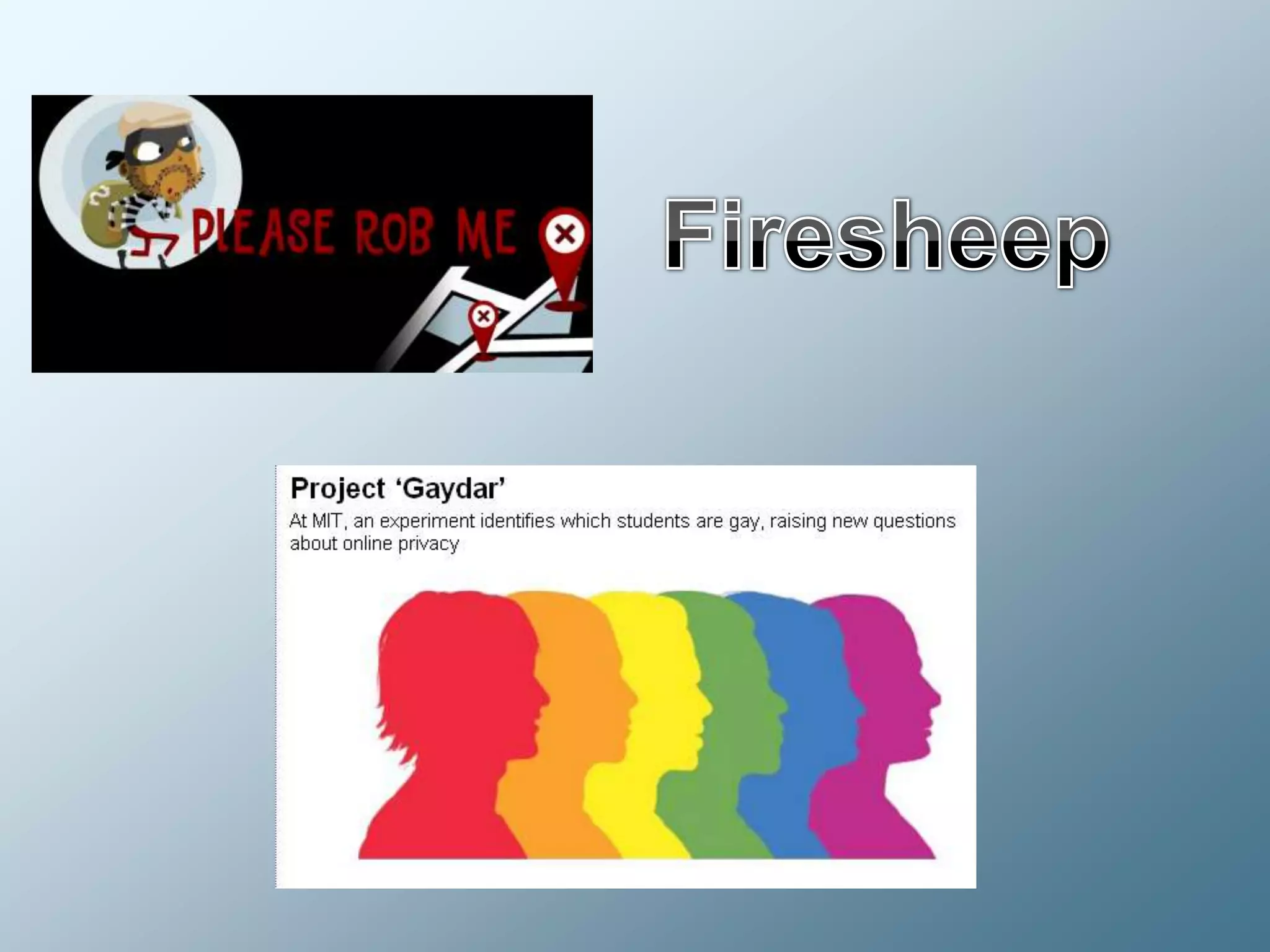
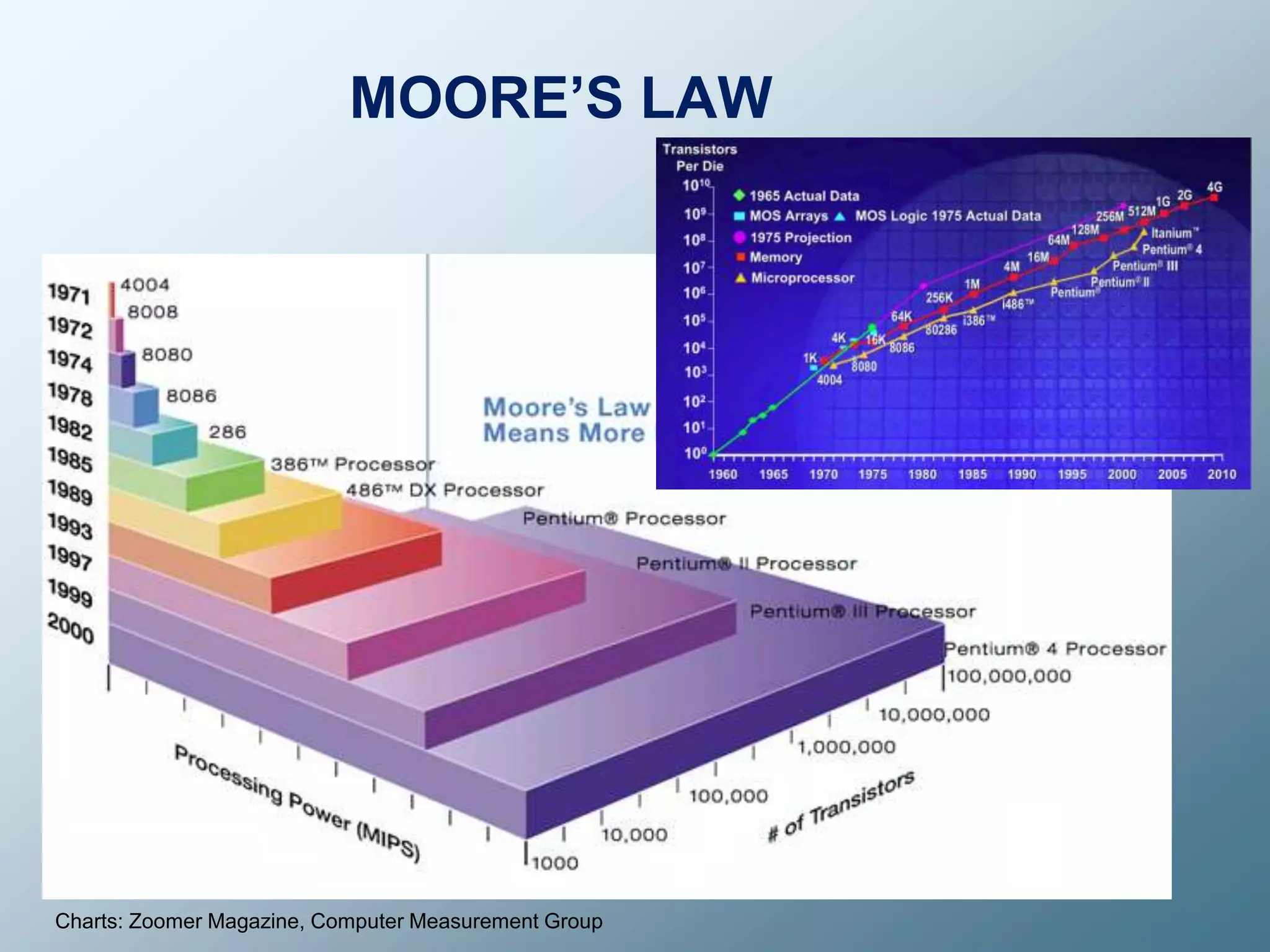
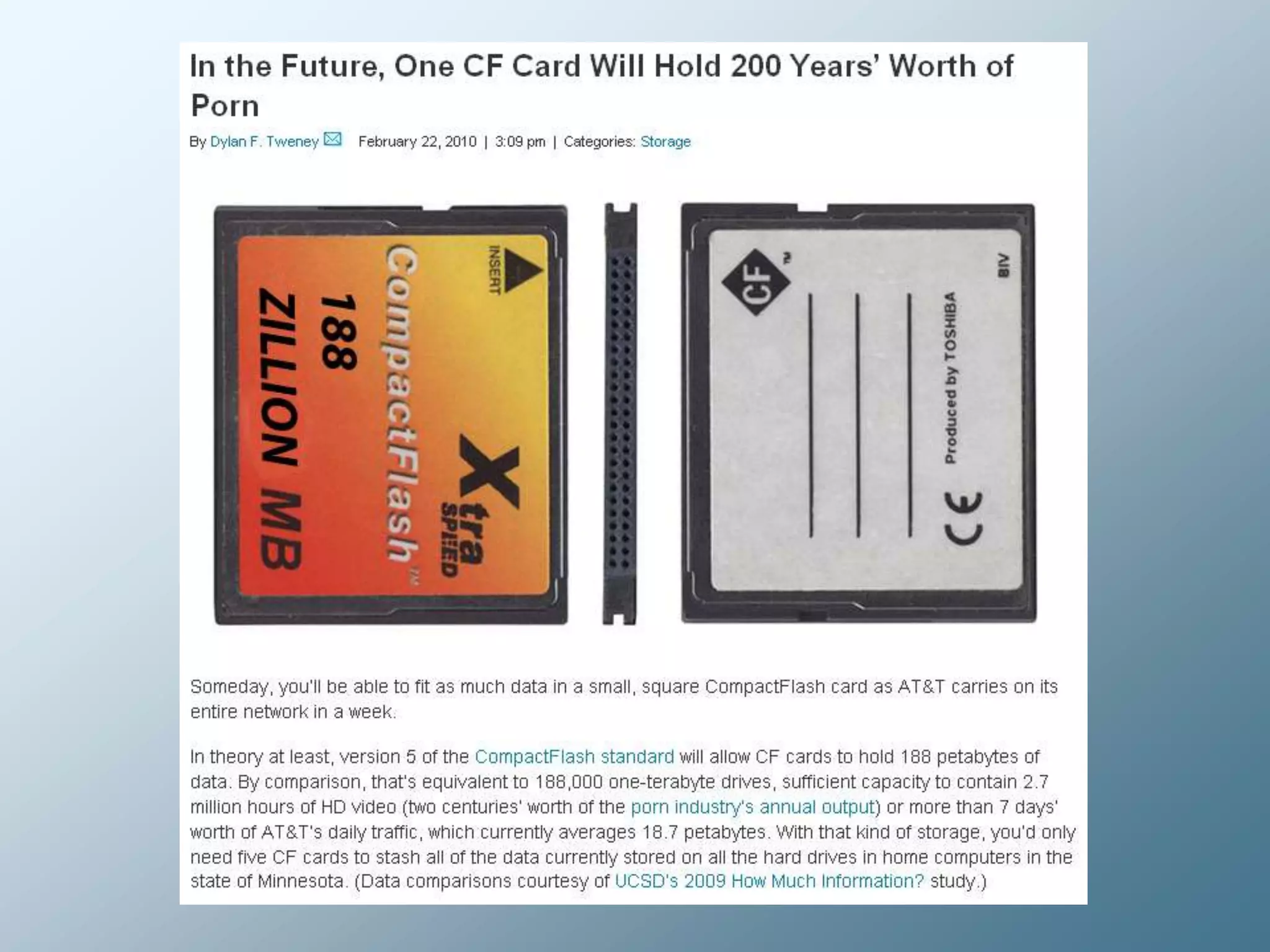
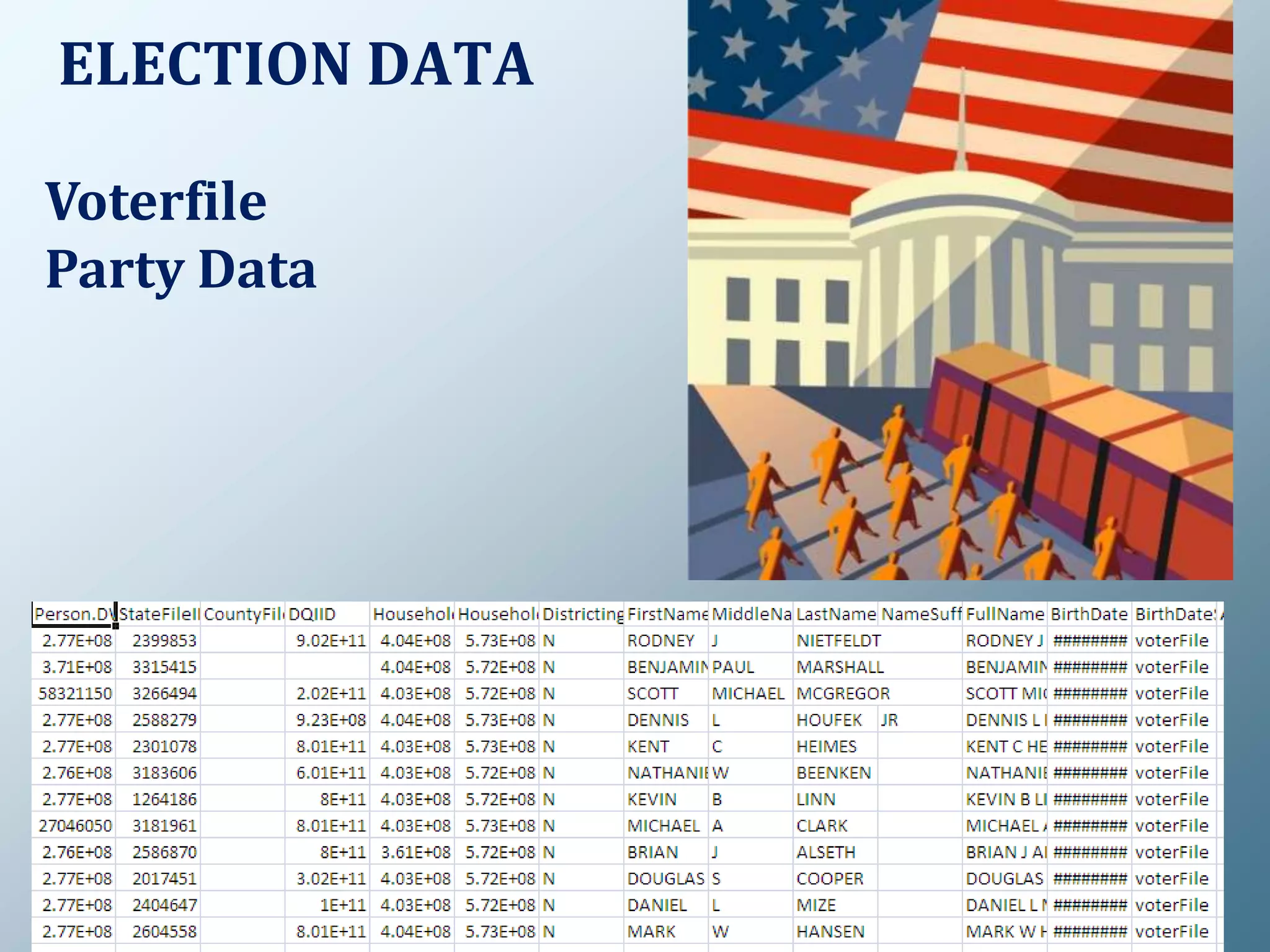
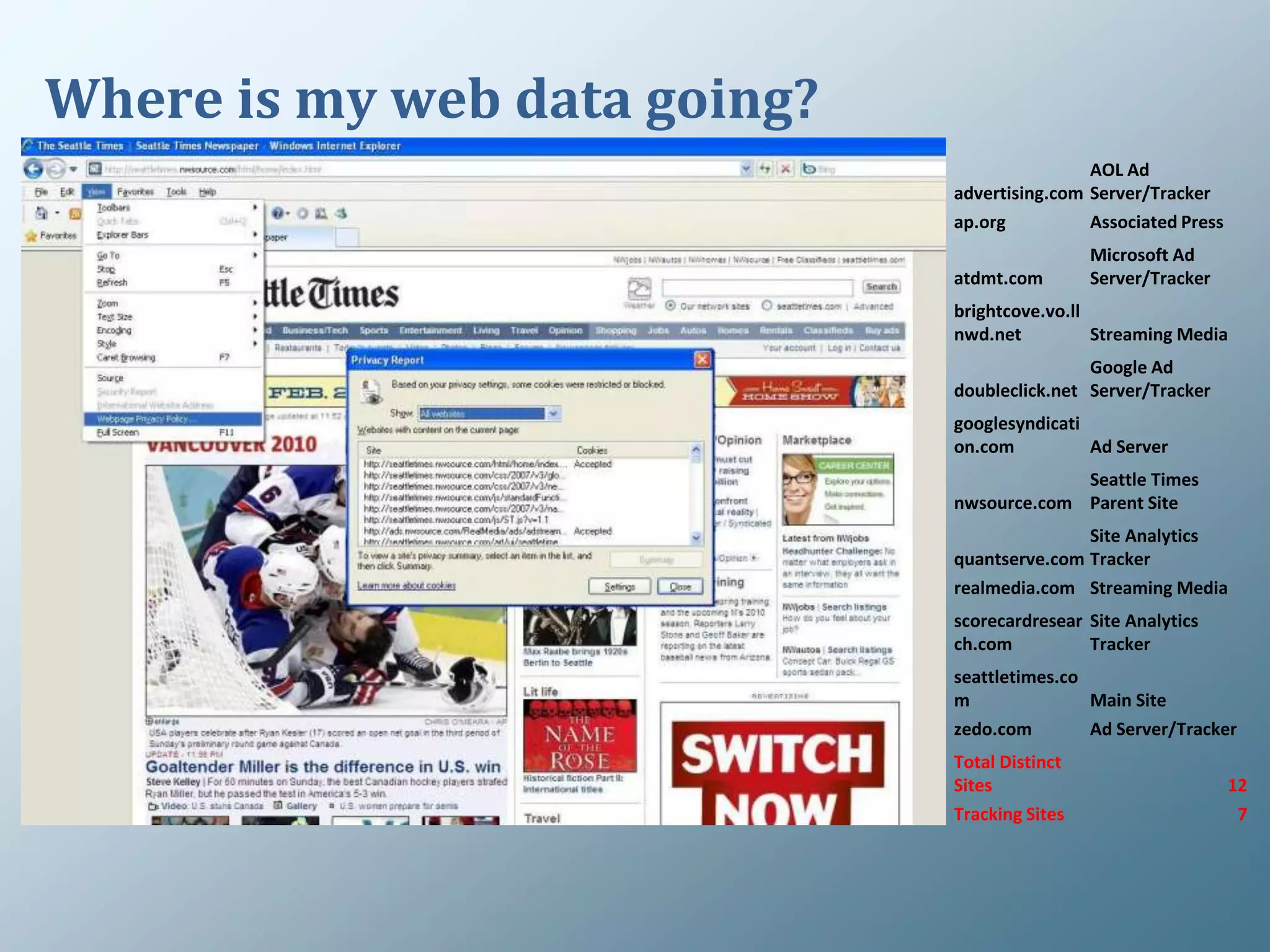
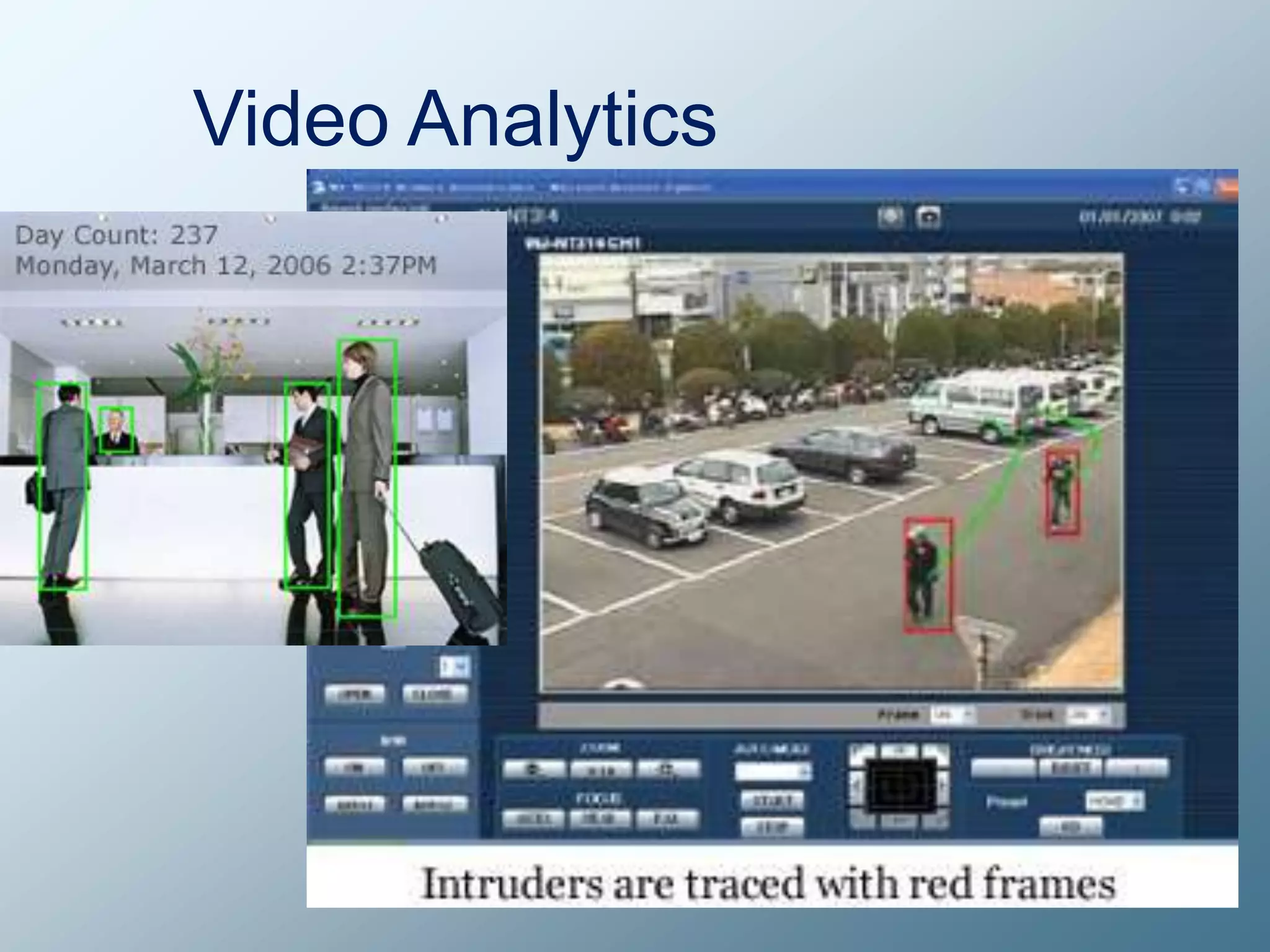
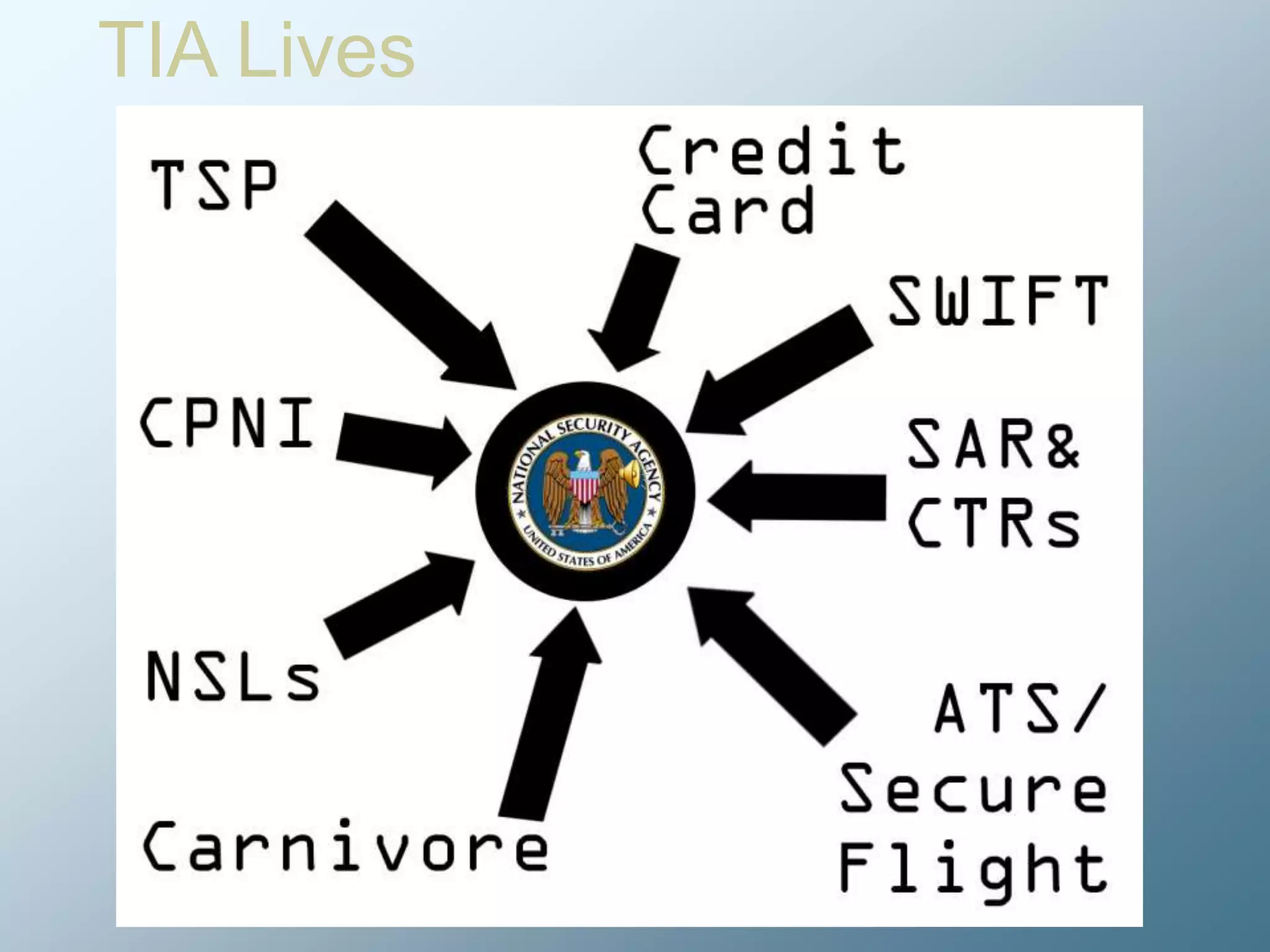
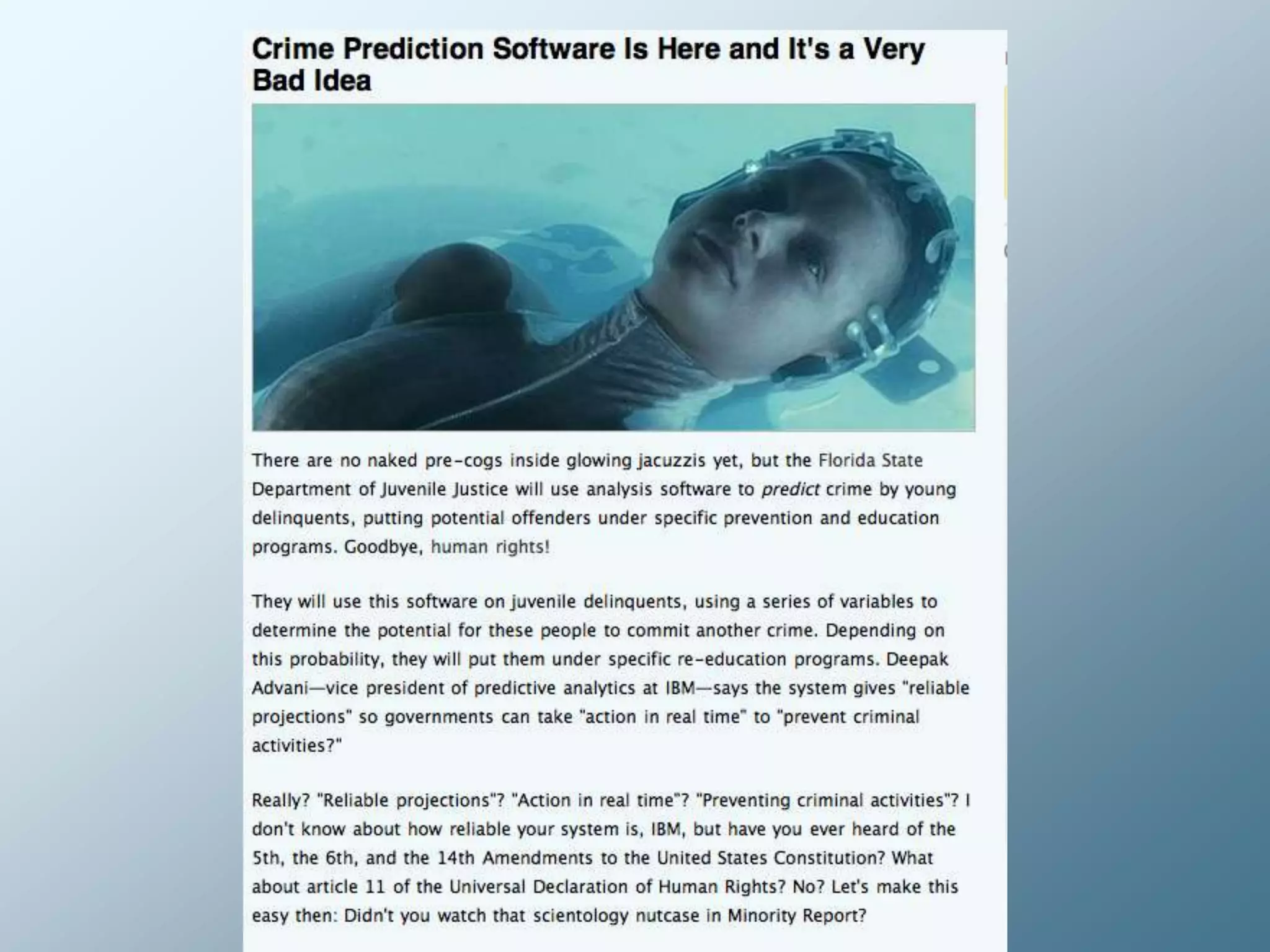
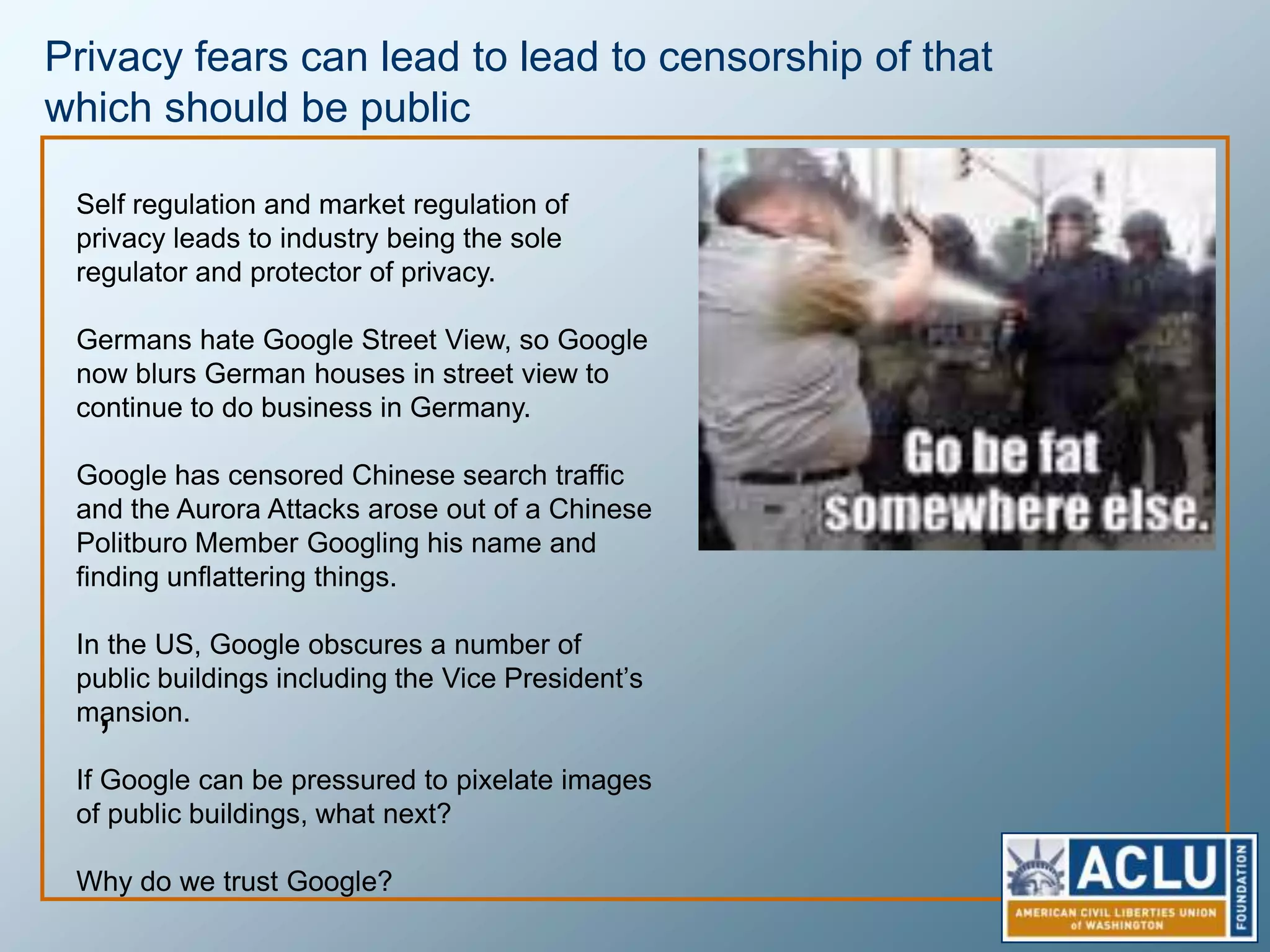
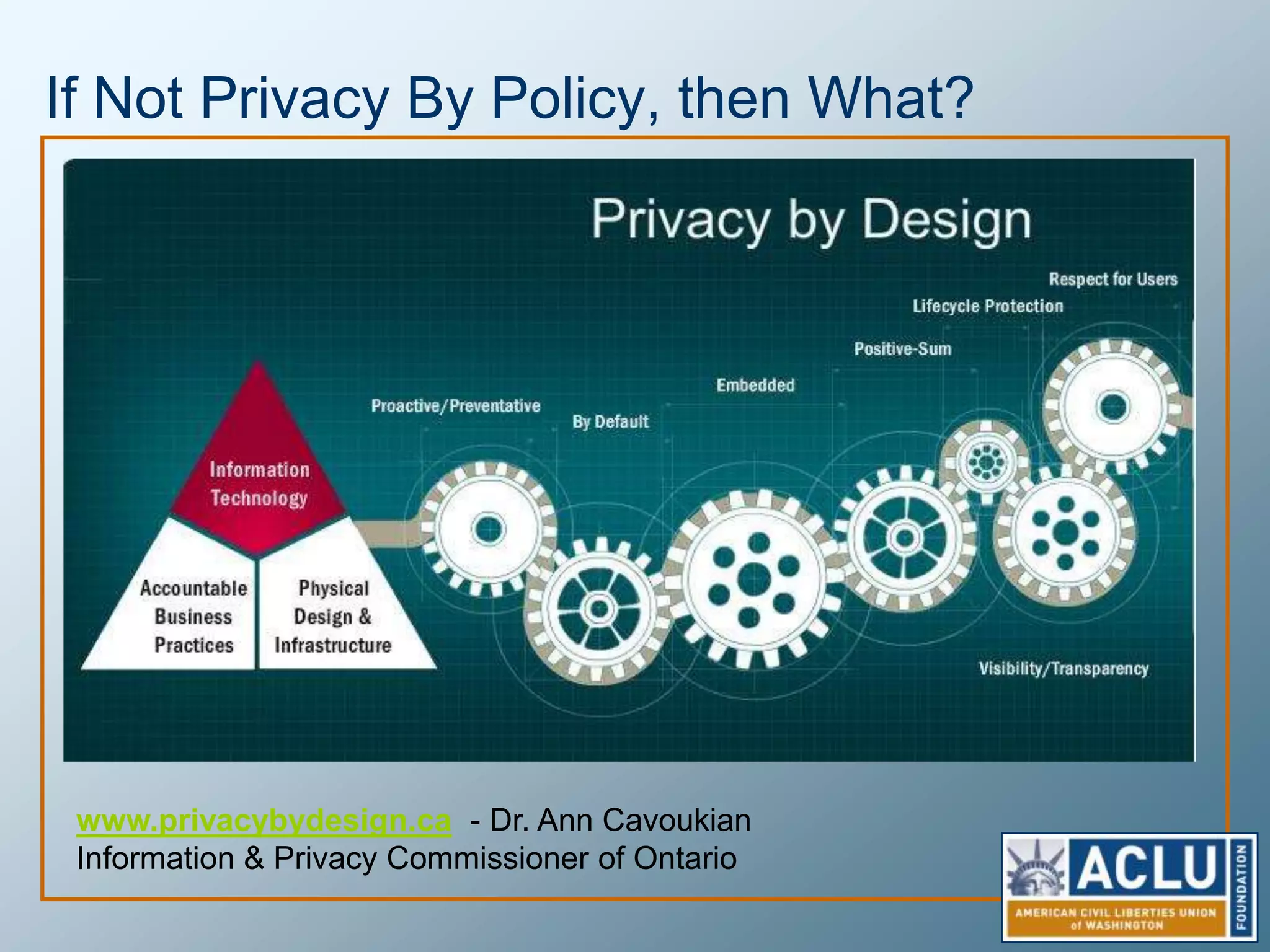
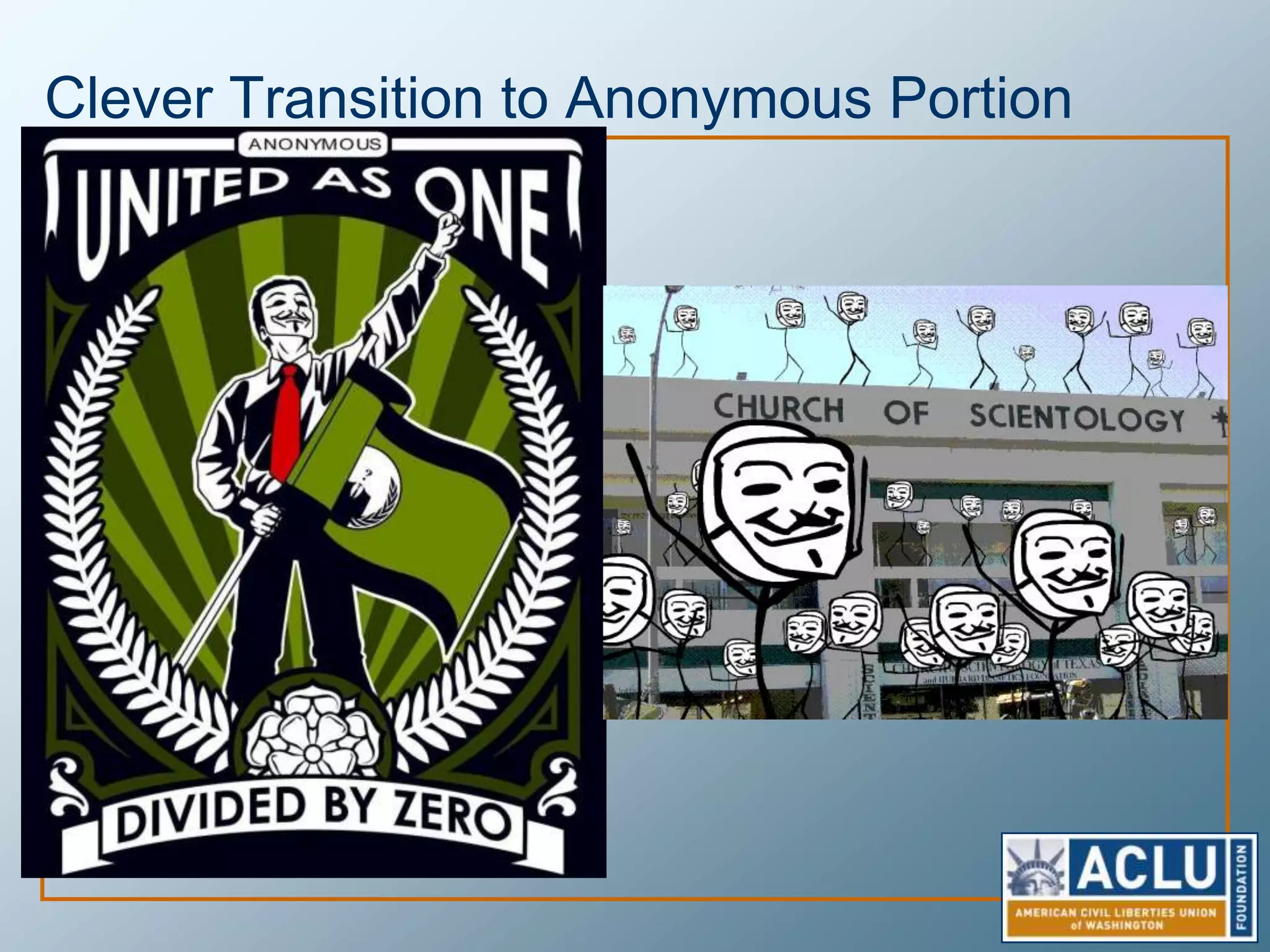
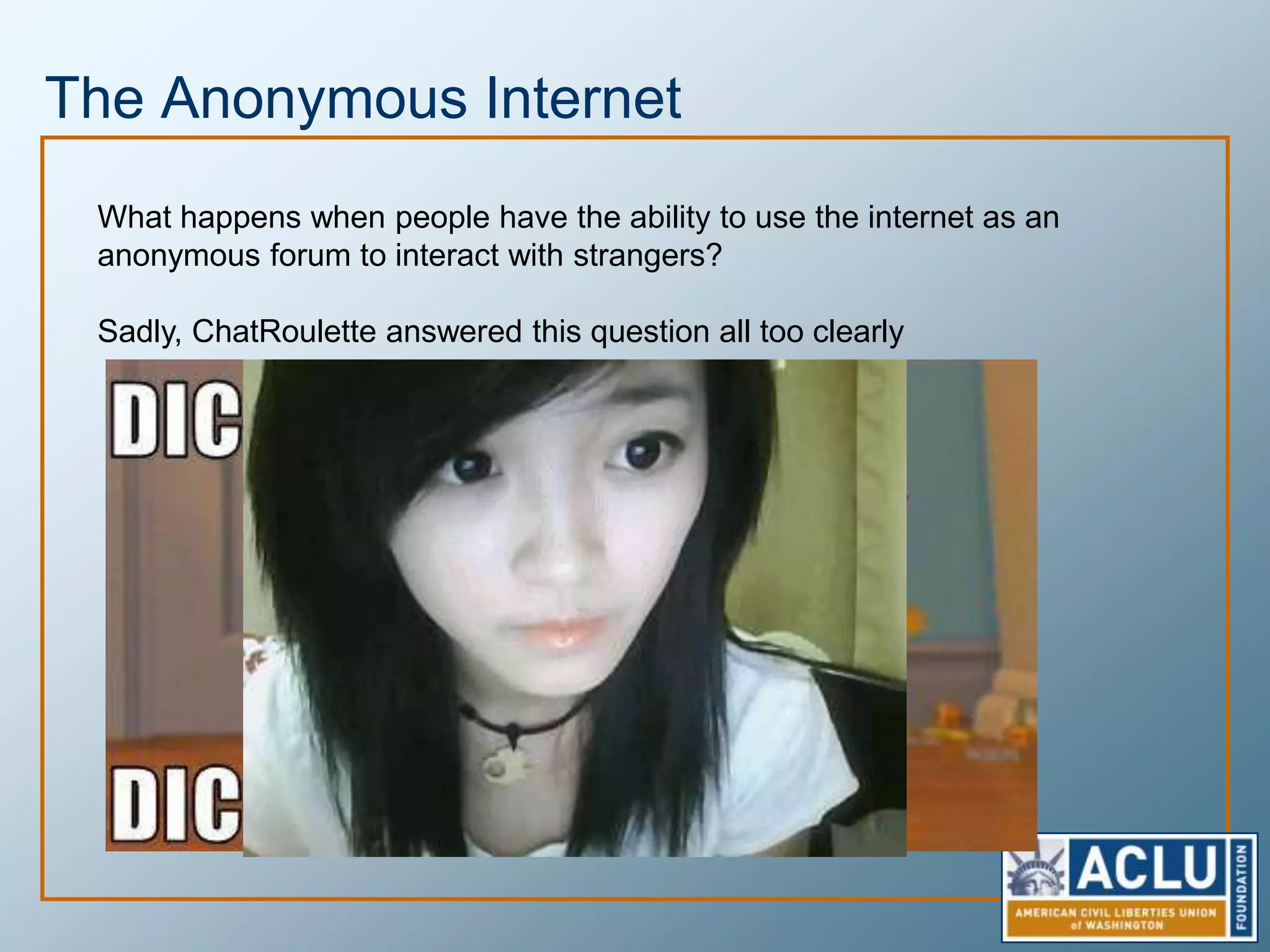
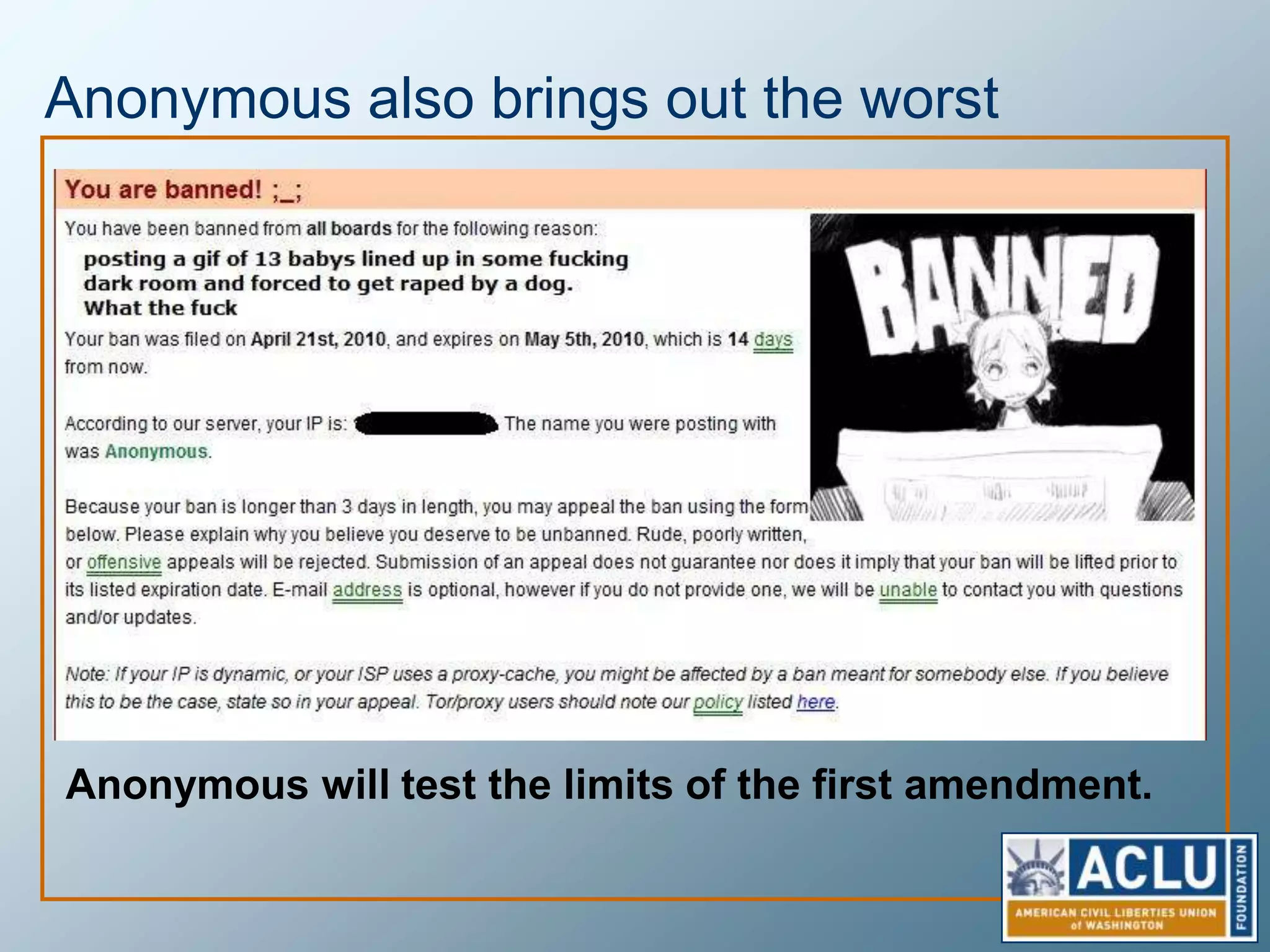
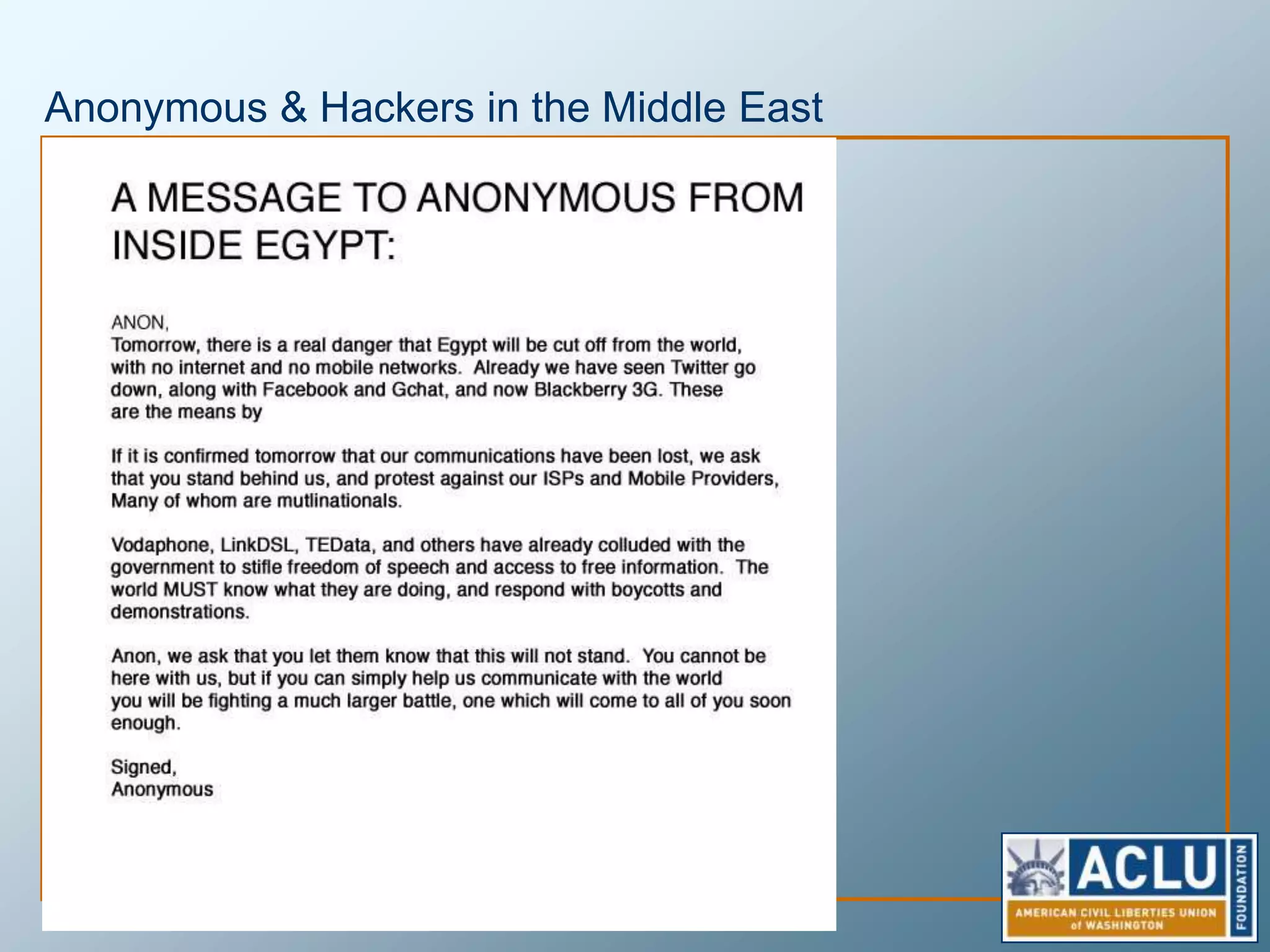
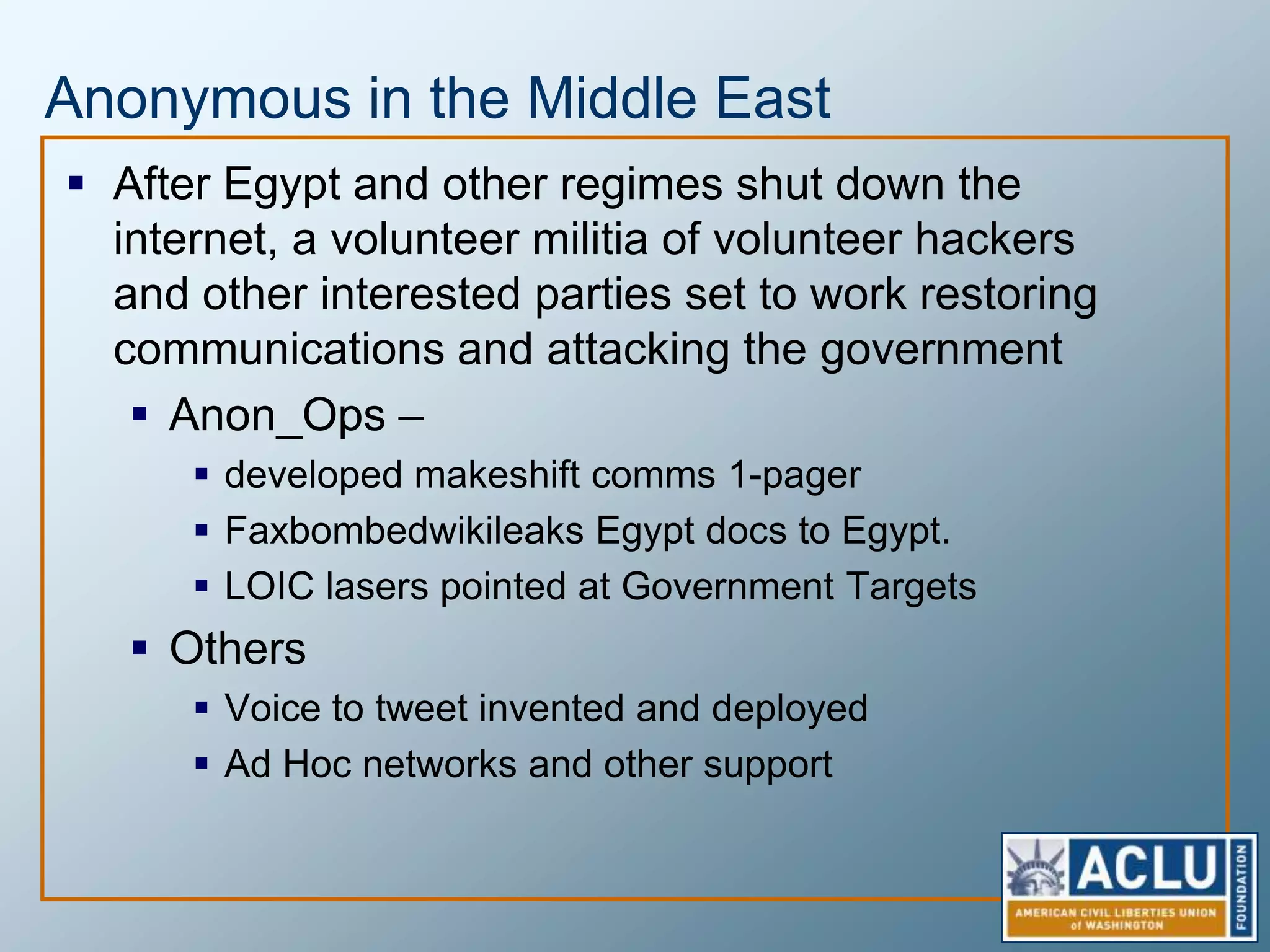
Privacy is a complex concept that is impacted by new technologies. While many are concerned about online privacy and data collection, anonymity on the internet allows for important anonymous speech. However, anonymous online spaces are also used for harassment and illegal activities. An ethical approach to privacy involves balancing openness with appropriate limits, through principles like "privacy by design" and laws that protect both privacy and security. Anonymous platforms have enabled important political speech but are also threatened by calls for increased monitoring.