Embed presentation
Downloaded 26 times














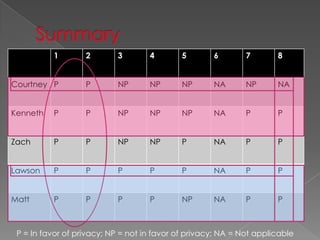
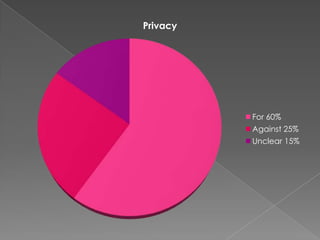
The document contains responses from 5 students - Courtney, Kenneth, Zach, Lawson, and Matt - to questions about online privacy. Most of the students were generally in favor of protecting individual privacy online, though some acknowledged tradeoffs between privacy and other issues like law enforcement investigations. A majority of responses supported privacy in questions related to search histories, social media content, and antivirus software protecting against government malware.

















