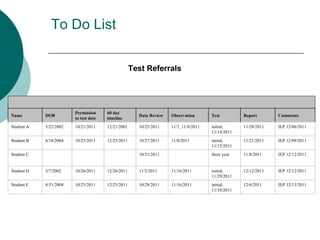
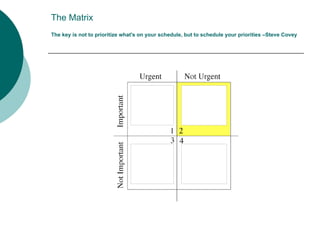
The document discusses prioritizing tasks and making efficient use of time. It provides the original and revised daily schedules of a school psychologist. It also includes tools for prioritization like a to-do list with student evaluations and a matrix for categorizing tasks as urgent/important vs not urgent/important to help focus on long-term goals.