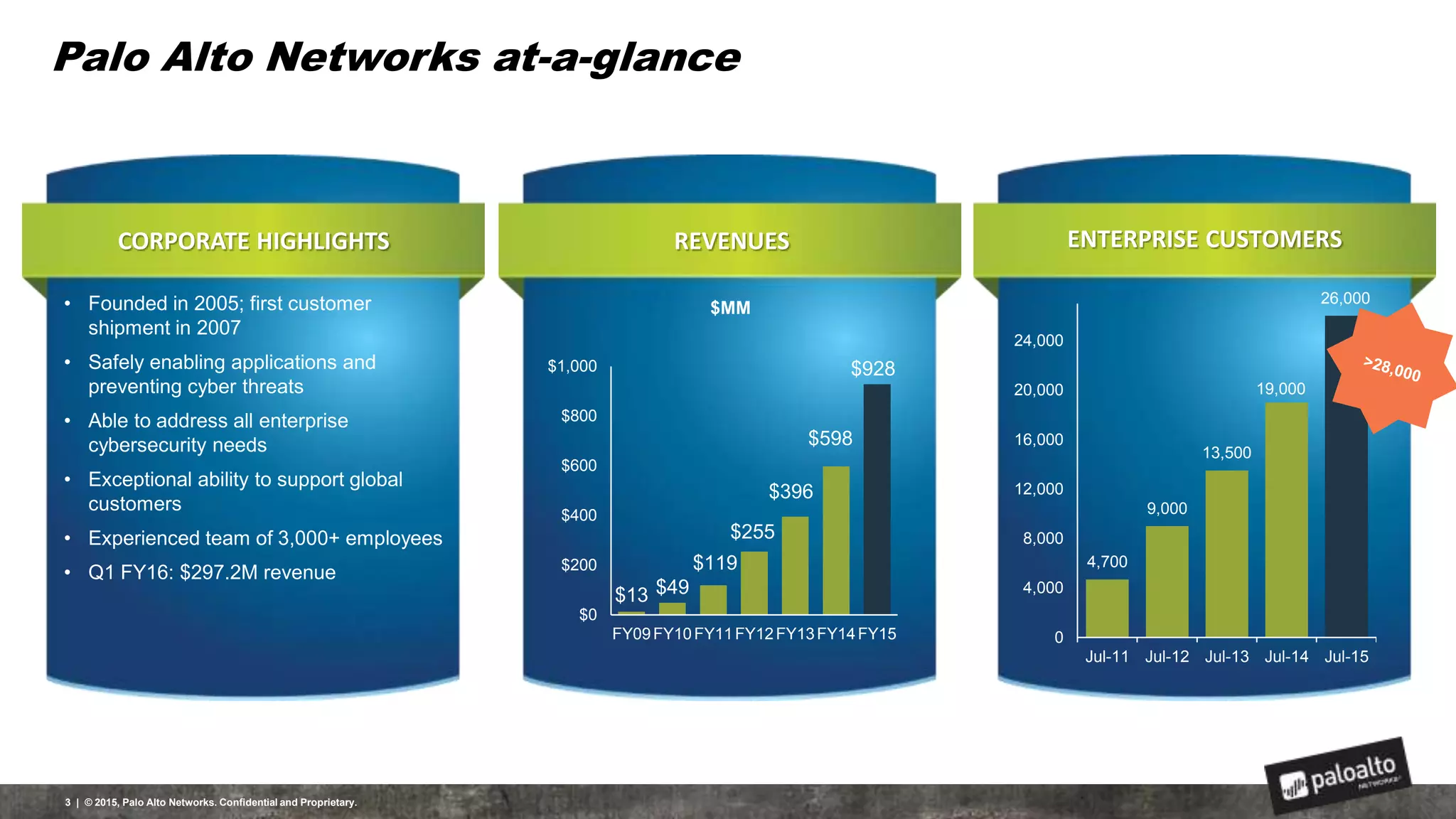
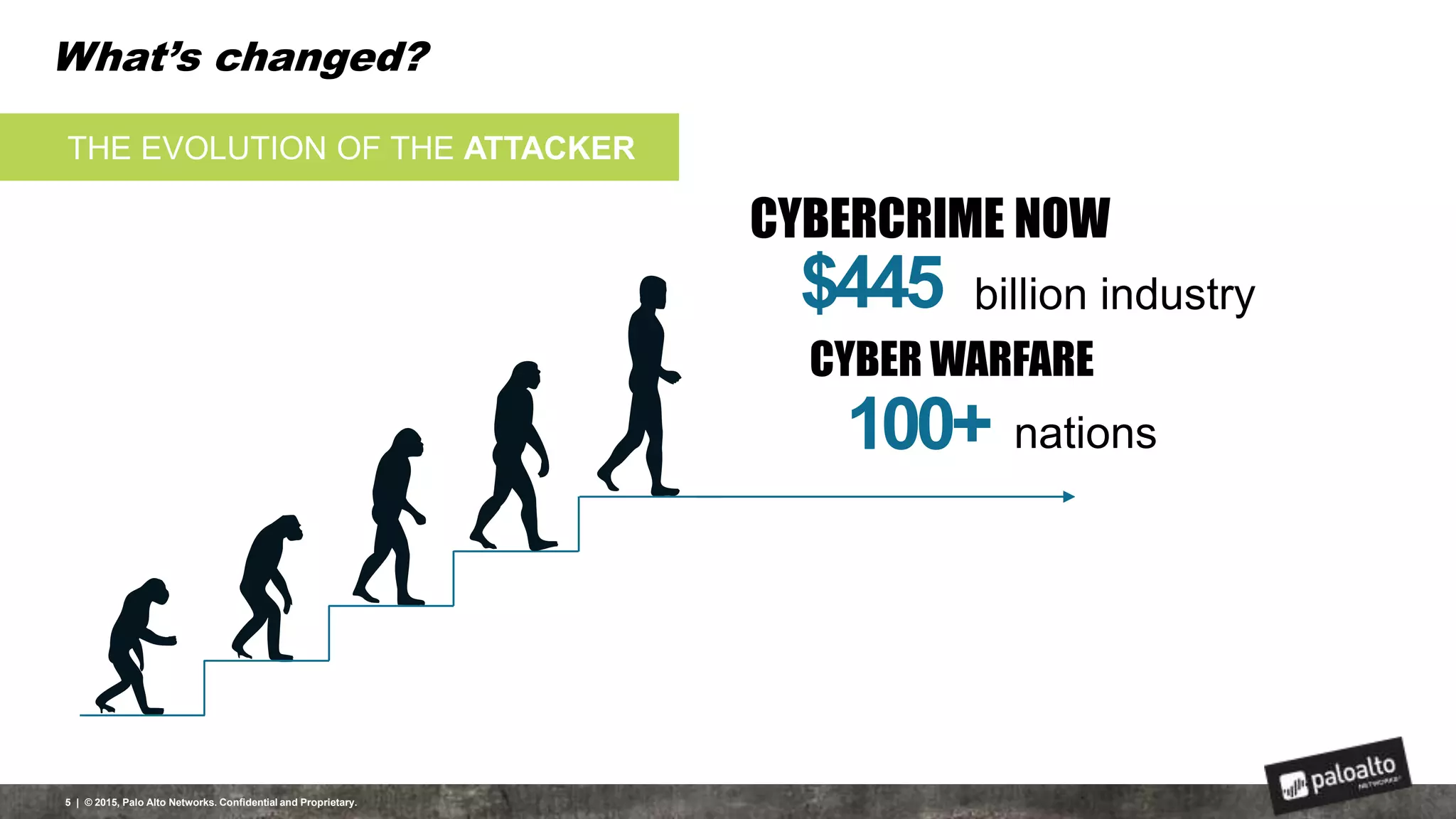
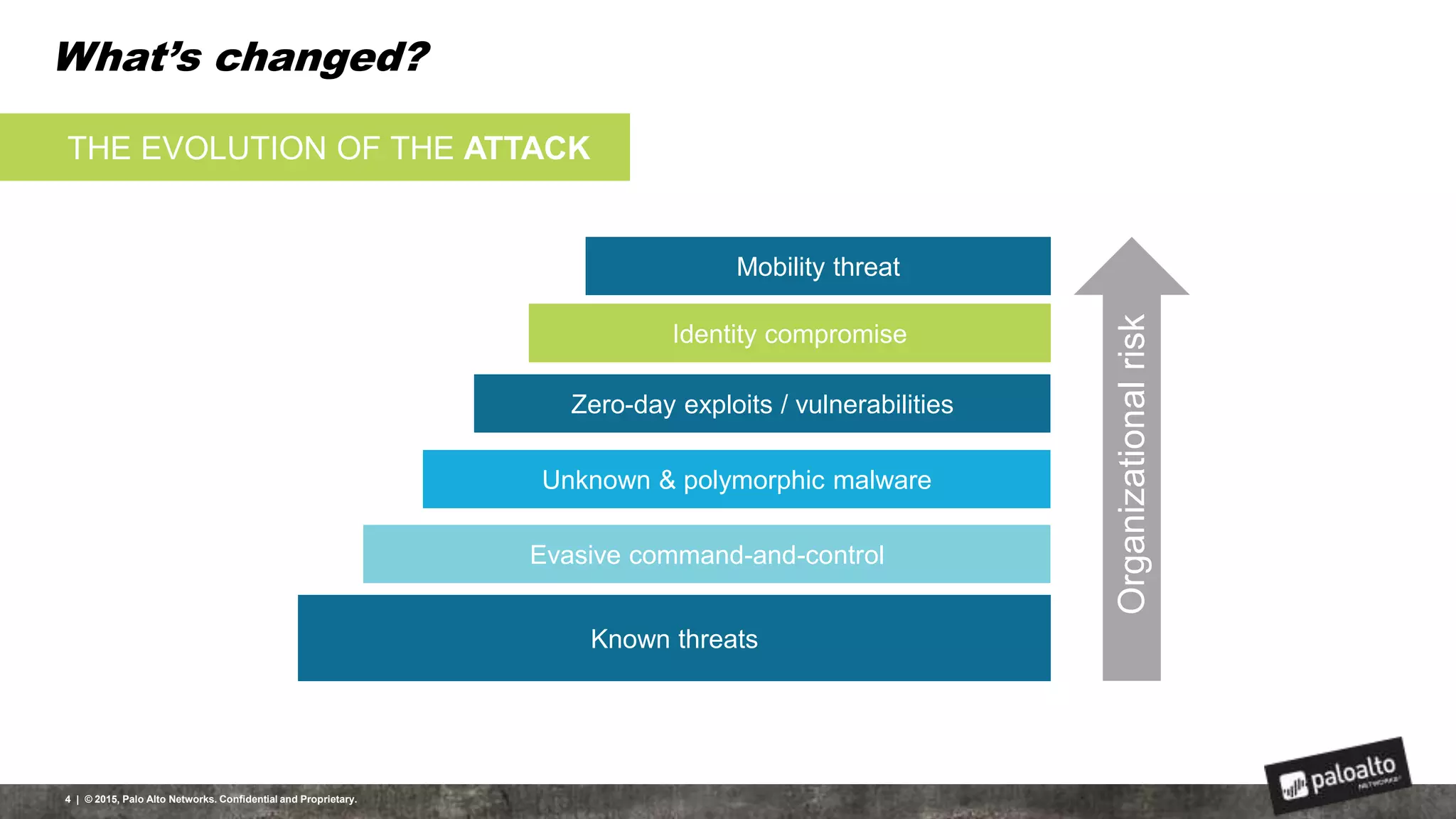
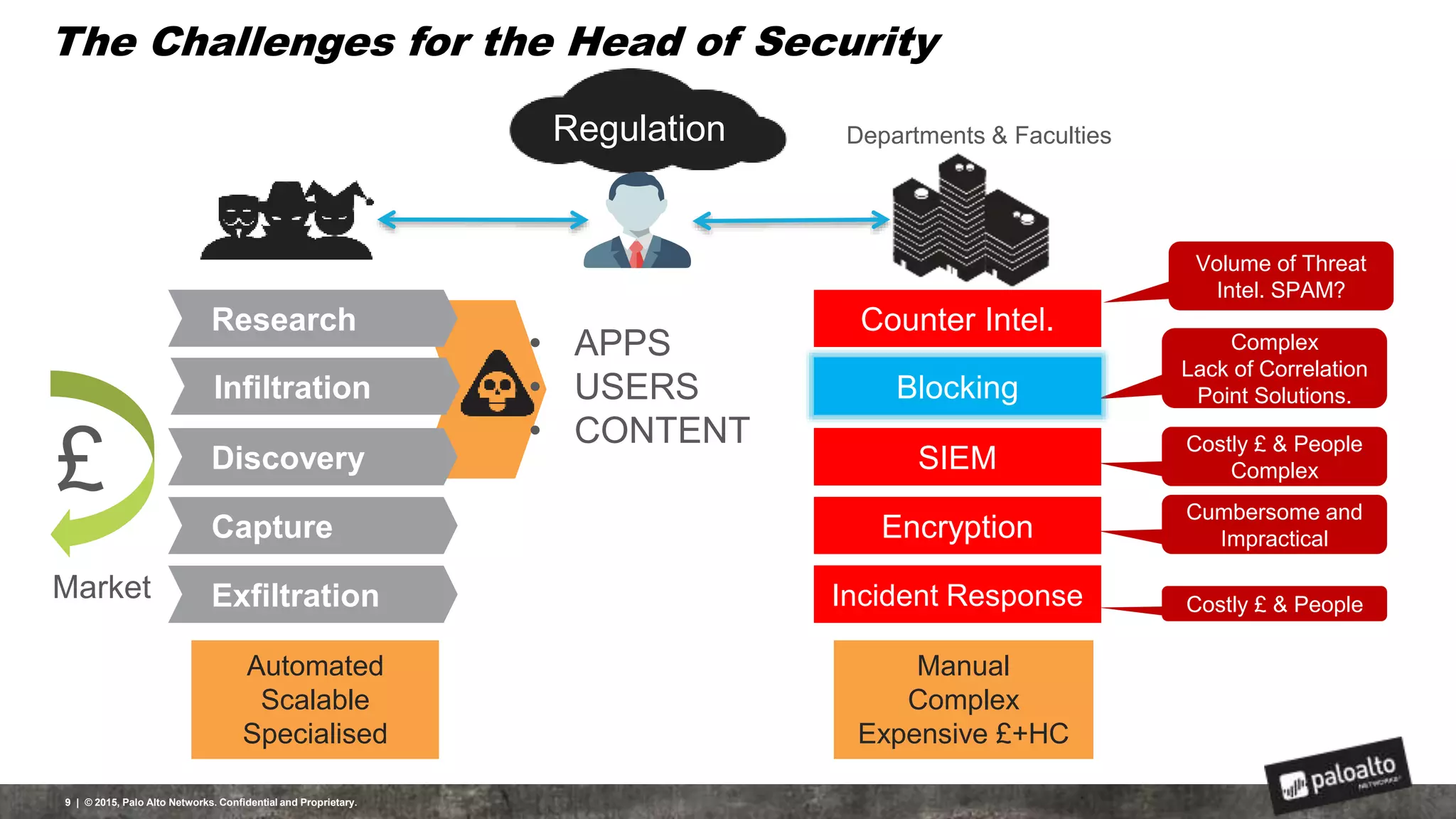
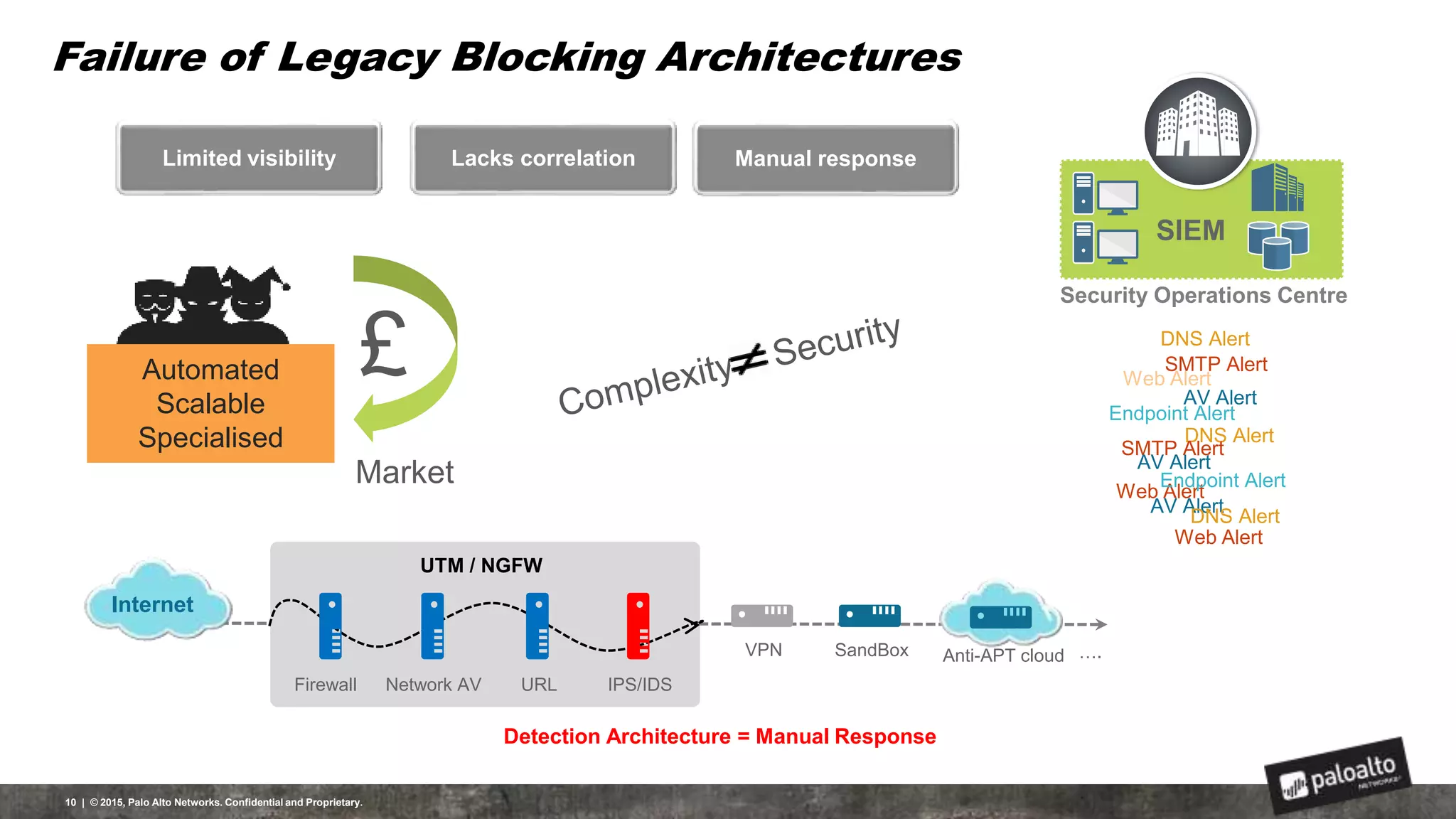
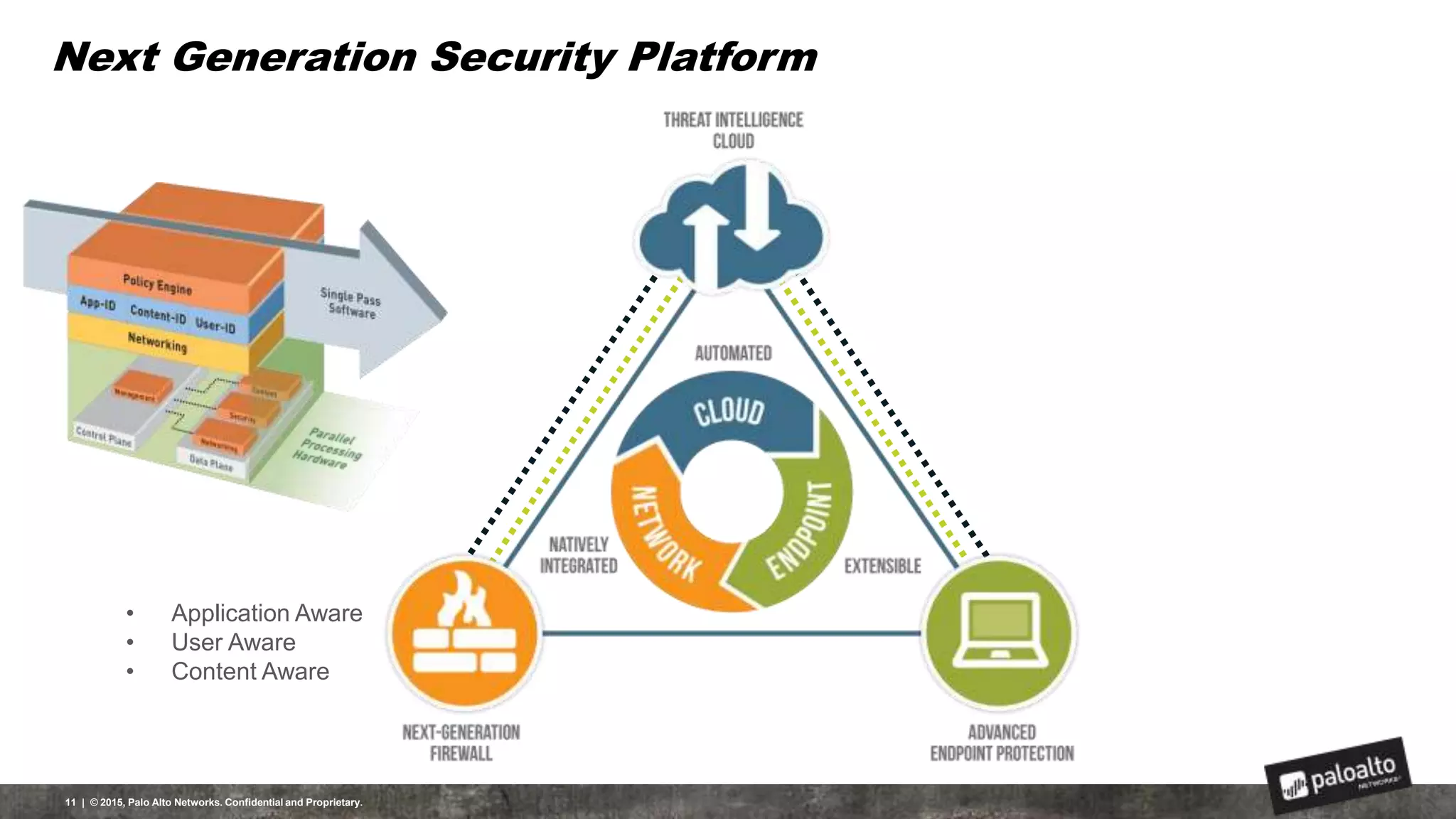
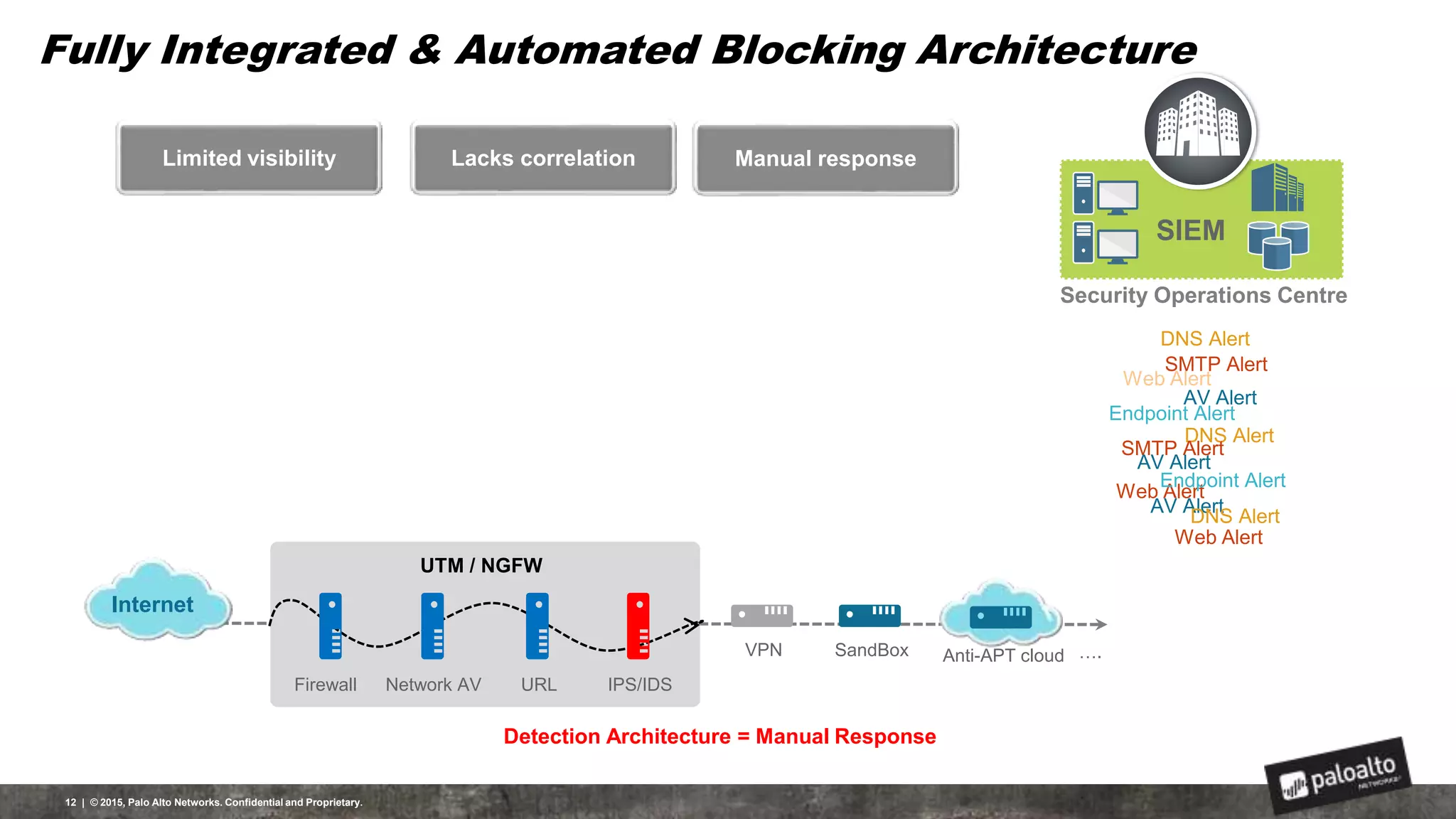
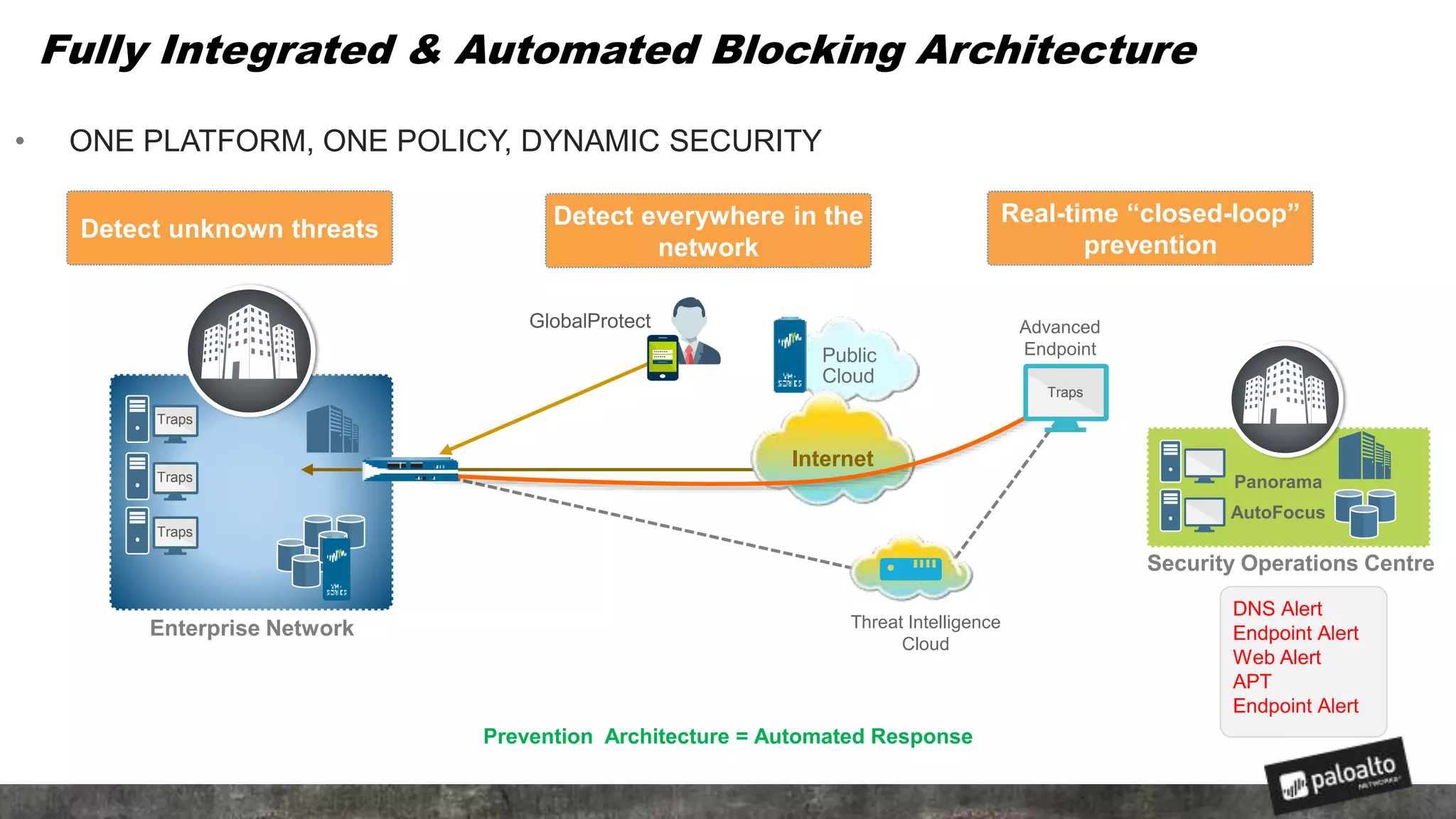
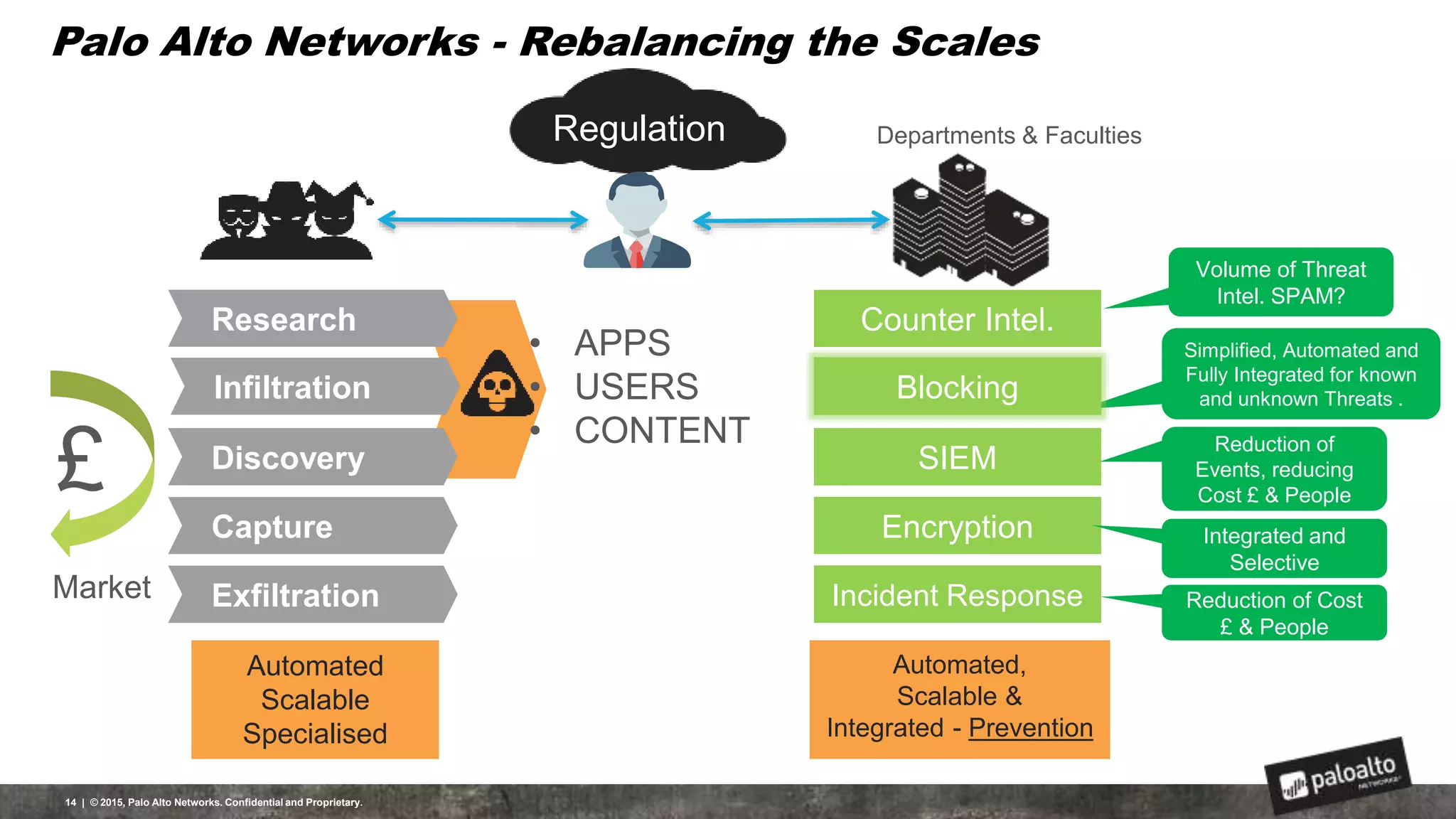
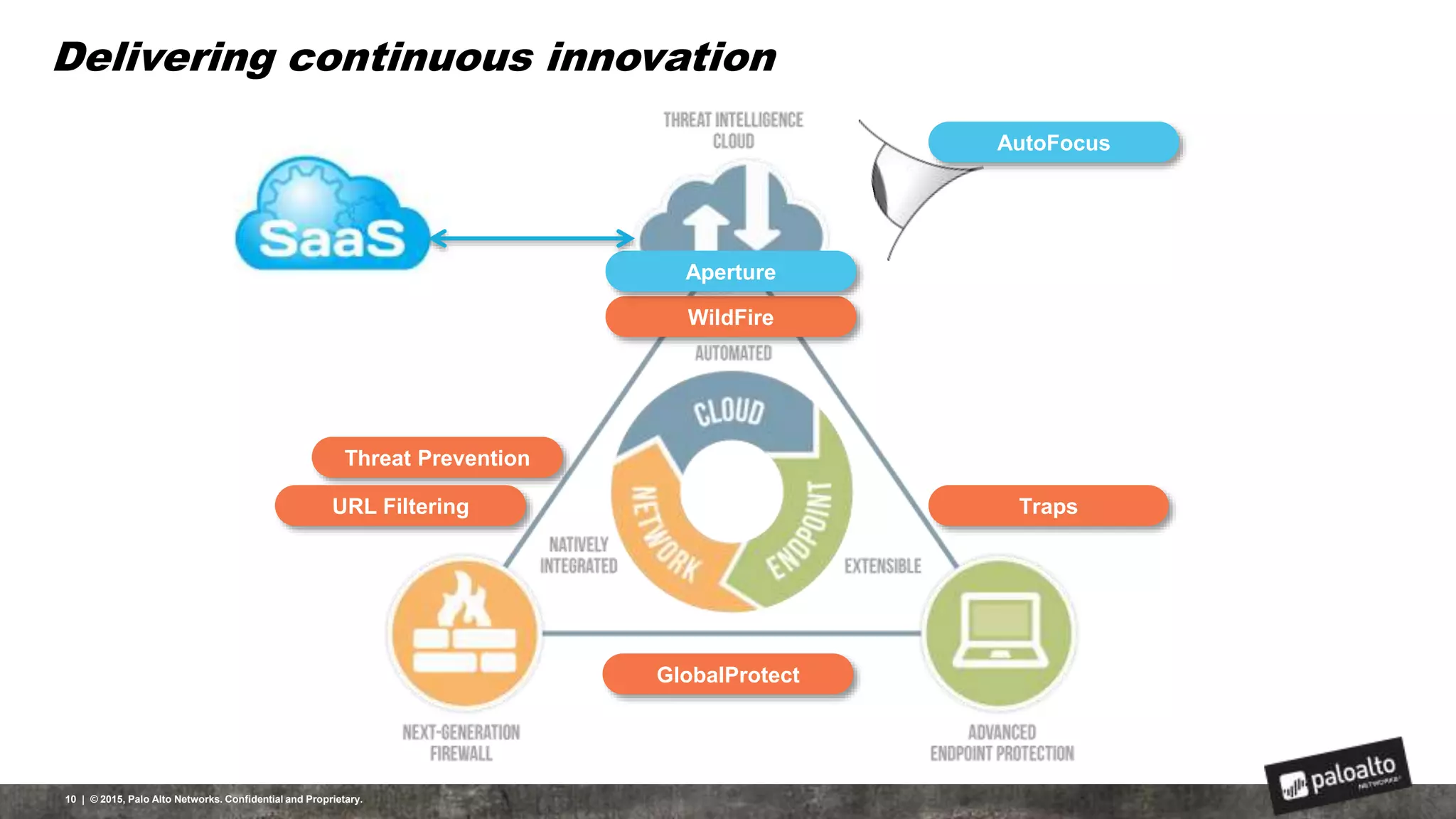
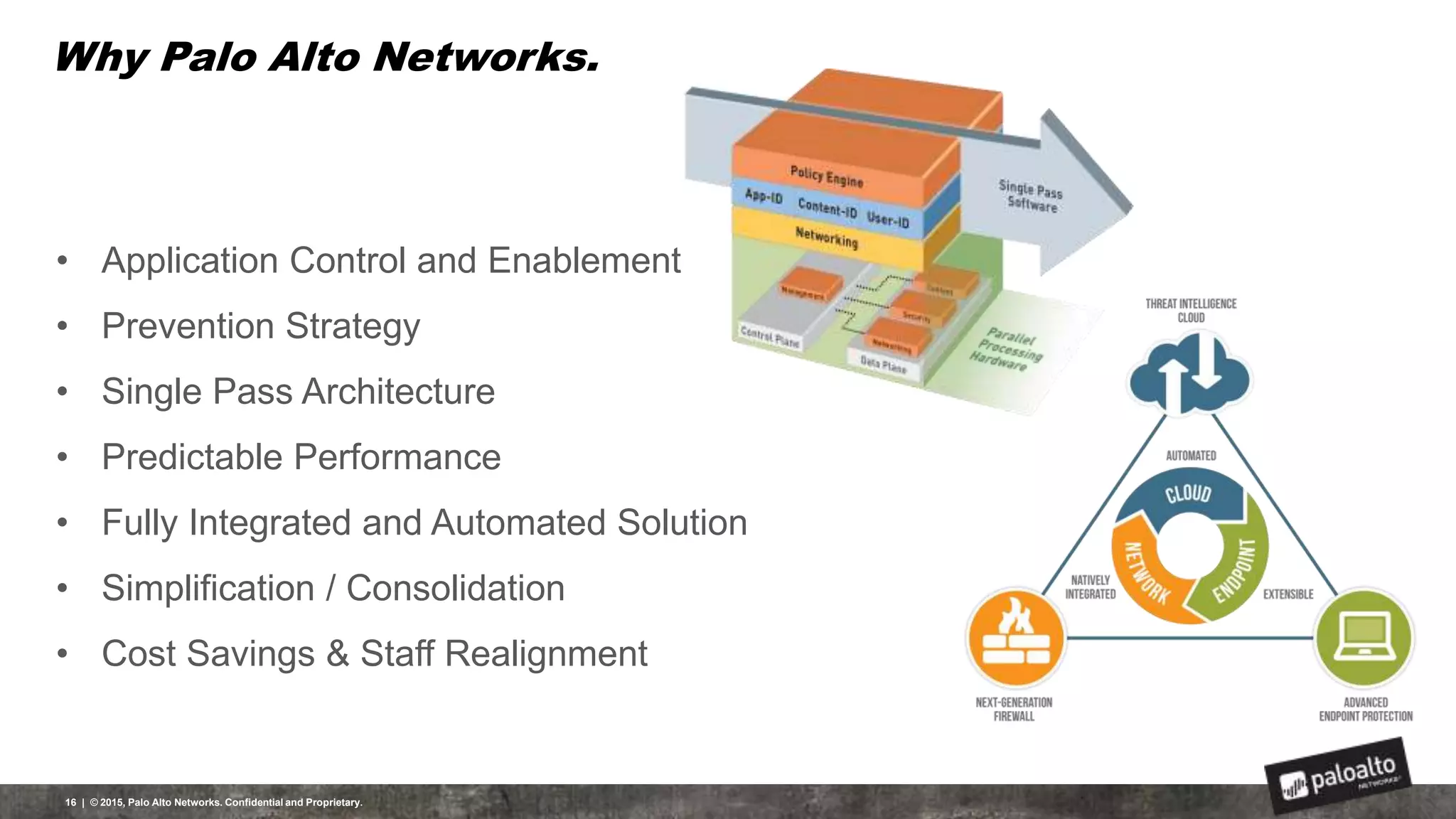
This document discusses the need for organizations to change their security strategies to address modern cyber threats. It describes how attackers have evolved over time and now operate at scale through cybercrime industries in many nations. Legacy security approaches using individual point solutions are no longer effective and lack coordination. The document promotes the Palo Alto Networks next-generation security platform as a fully integrated automated solution that can prevent both known and unknown threats through continuous innovation like the Traps, GlobalProtect, WildFire, and AutoFocus features. It argues this approach reduces risk, simplifies security operations, and saves costs through staff realignment compared to traditional complex and manual security methods.