Embed presentation
Download to read offline




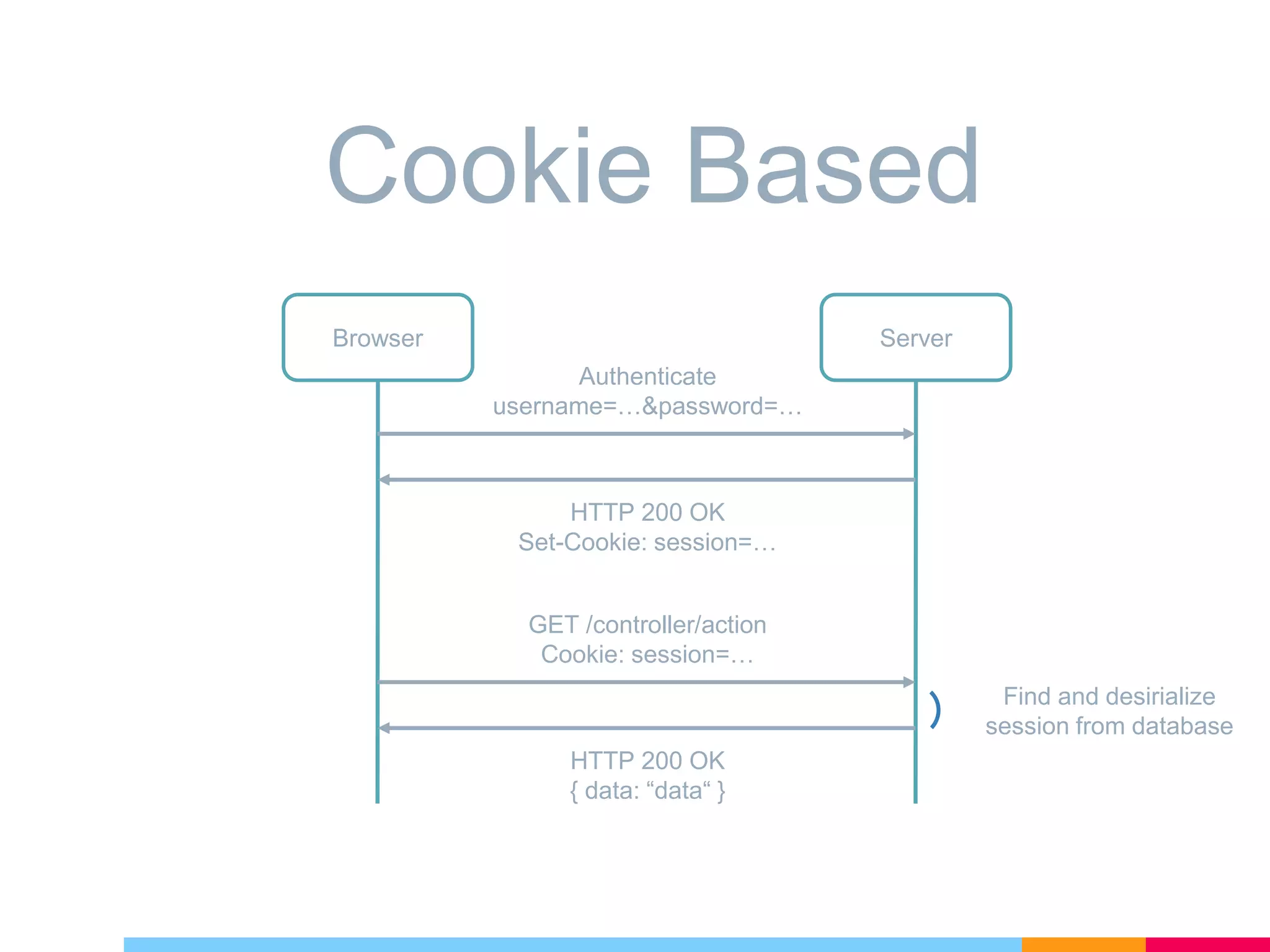

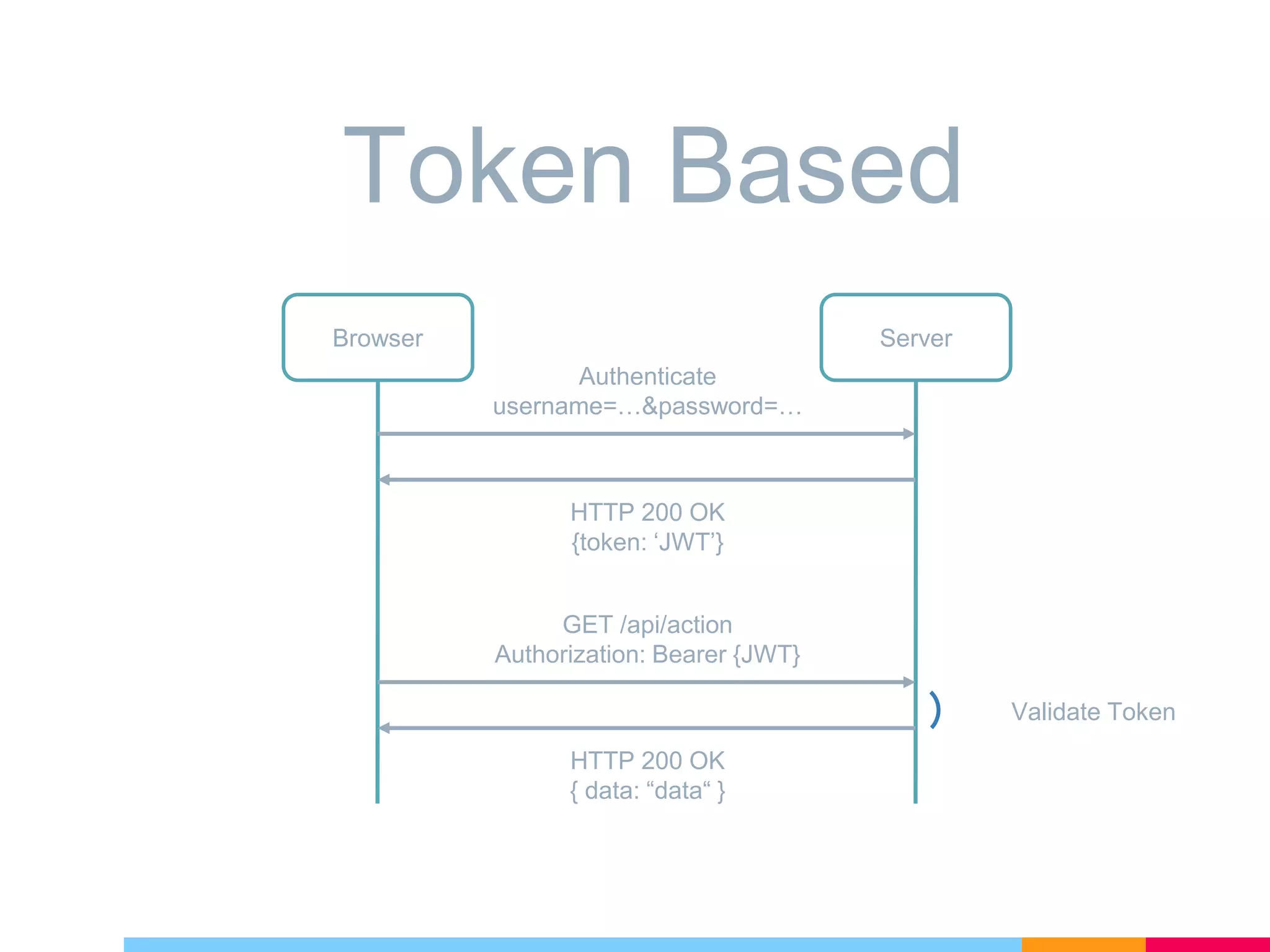

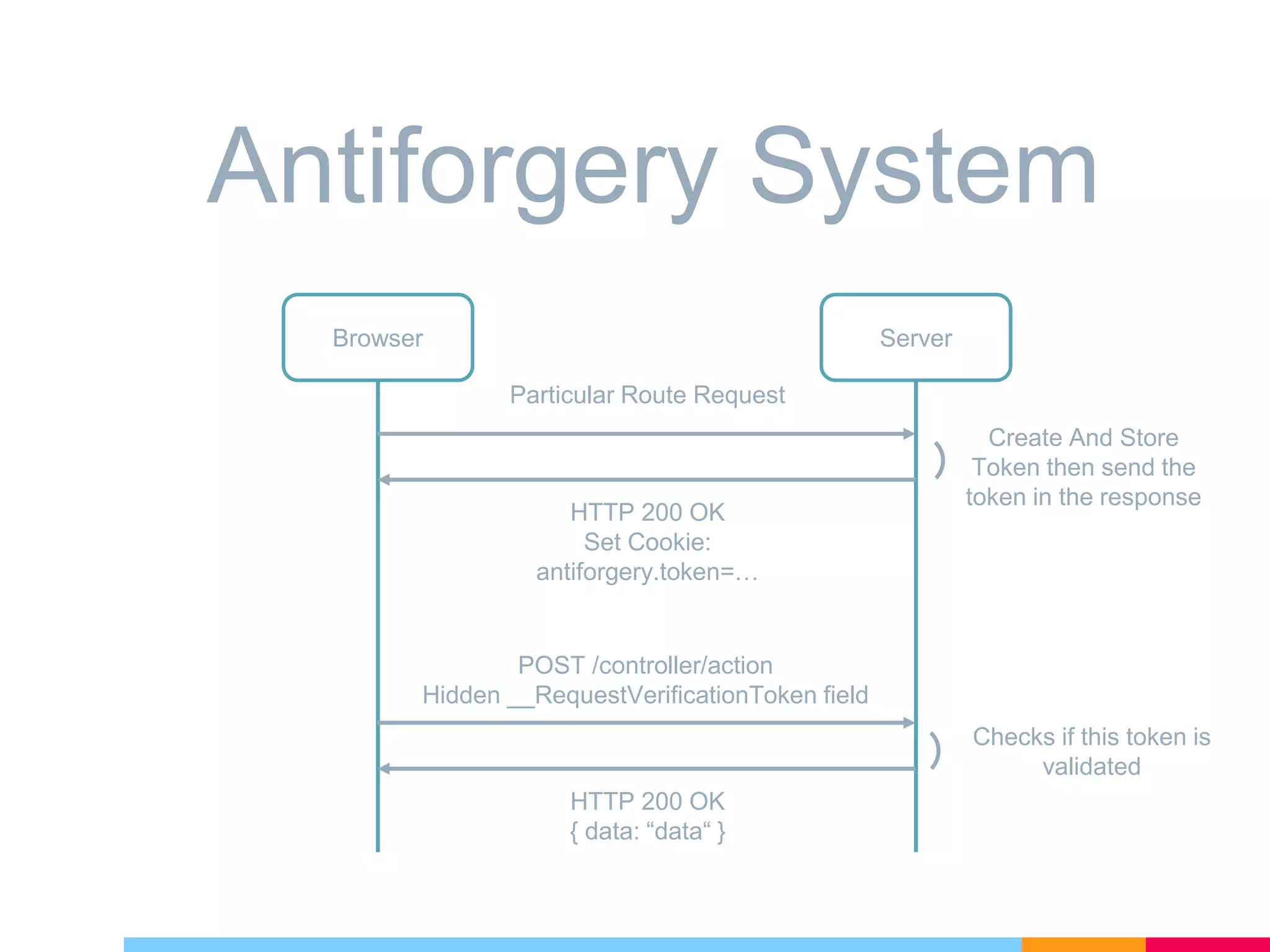



The document discusses cross-site request forgery (XSRF/CSRF) attacks and how to prevent them in ASP.NET Core applications. It explains that XSRF attacks trick authenticated users into performing unwanted actions on a web application. To prevent XSRF, ASP.NET Core uses antiforgery tokens that are validated on requests. It provides built-in support for adding antiforgery tokens to MVC forms and tag helpers. Additionally, antiforgery middleware can validate tokens on incoming requests to the application.












