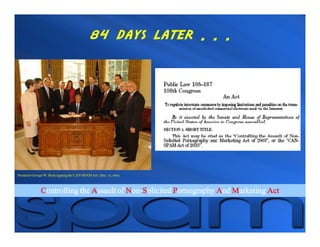
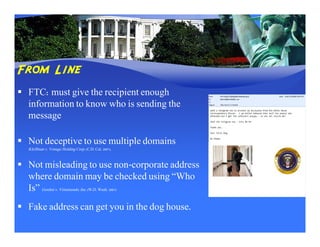
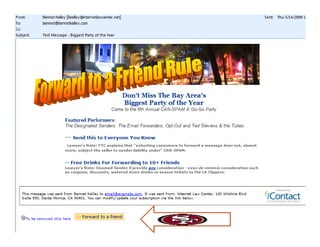
This document summarizes key aspects of privacy concerns and regulations regarding marketing and commercial communications, specifically the CAN-SPAM Act of 2003. It outlines what CAN-SPAM does and does not do, its principal requirements regarding from lines, subject lines, opt-out mechanisms, and plaintiffs. It also discusses regulatory timelines, determining when CAN-SPAM applies, selected court cases, and issues of preemption and state spam regulation.