This document summarizes an enterprise deployment of PostgreSQL at a large mobile advertising company. It discusses:
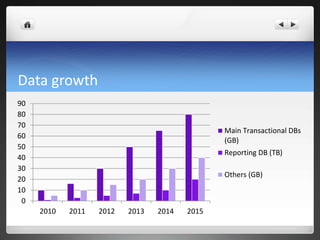
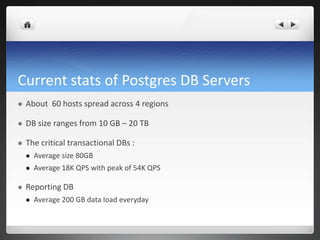
1) The company uses PostgreSQL for transaction processing and reporting across 60 servers storing 10GB to 20TB of data each, with the critical databases averaging 80GB and handling 18,000 queries per second.
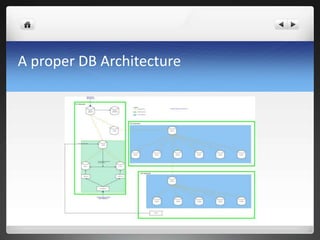
2) To achieve 99.99% uptime, the company employs disaster recovery planning including cascaded replication across data centers and regular disaster drills to test backups.
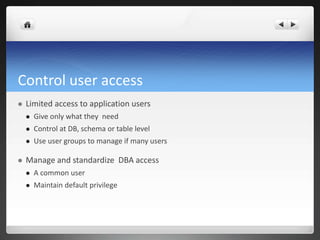
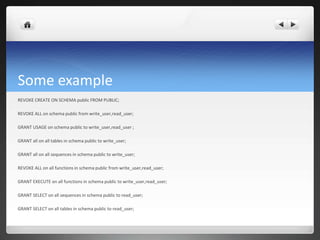
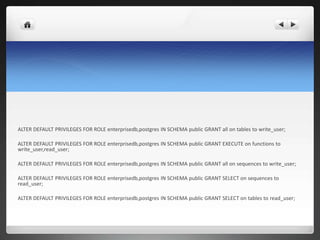
3) The company uses Puppet for configuration management, stored procedures to optimize queries, monitoring tools, and access control and encryption to secure user access and network traffic.