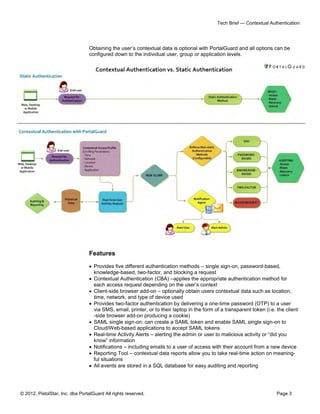
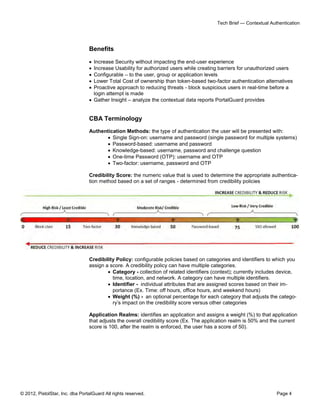
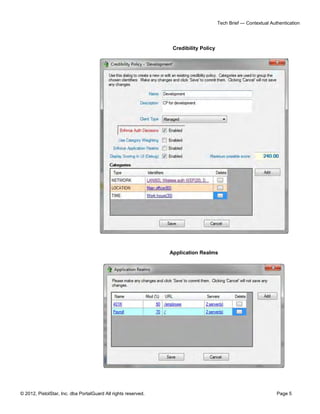
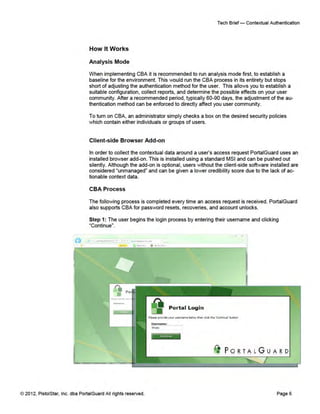
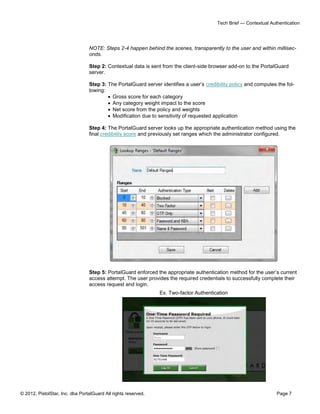
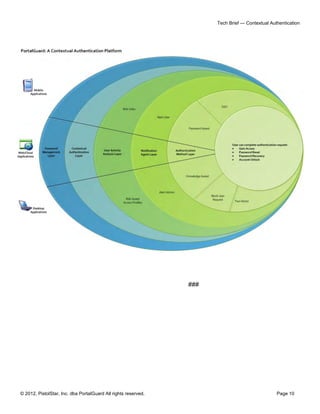
The document outlines PortalGuard's Contextual Authentication (CBA), a multi-factor security solution that blends usability with enhanced security for remote access scenarios. It addresses the challenges and costs associated with traditional two-factor authentication methods while offering a flexible, configurable approach that adapts based on each user's context. CBA offers multiple authentication methods, optional contextual data capture, and aims to improve security without compromising on user experience.