PortalGuard Reports Uncover User Authentication Insights
•
0 likes•251 views
PortalGuard provides reports that allow administrators to monitor user authentication events and take action in real-time. The reports provide insights into blocked users, password recovery attempts, access to sensitive data, password expiration rates, average risk scores by group, device usage, employee productivity, application access patterns, functionality adoption rates, and cost metrics.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
Similar to PortalGuard Reports Uncover User Authentication Insights
Similar to PortalGuard Reports Uncover User Authentication Insights (20)
Contextual Authentication: A Multi-factor Approach

Contextual Authentication: A Multi-factor Approach
Security from the Start: Optimizing Your Acquia Experience with Acquia Cloud...

Security from the Start: Optimizing Your Acquia Experience with Acquia Cloud...
Windows Network Access Control for Government Traffic Department

Windows Network Access Control for Government Traffic Department
IRJET- Password Management Kit for Secure Authentication

IRJET- Password Management Kit for Secure Authentication
Information Security in the Banking Sector. A Case Study on UserLock

Information Security in the Banking Sector. A Case Study on UserLock
Cybersecurity Insiders Webinar - Zero Trust: Best Practices for Securing the...

Cybersecurity Insiders Webinar - Zero Trust: Best Practices for Securing the...
Inflectra Enterprise Agile Planning Briefing for Gartner 2018

Inflectra Enterprise Agile Planning Briefing for Gartner 2018
Intelligent Authentication (Identity Live Berlin 2018)

Intelligent Authentication (Identity Live Berlin 2018)
More from PortalGuard
More from PortalGuard (15)
Designing and Implementing a Secure, Fully Brandable Web Portal

Designing and Implementing a Secure, Fully Brandable Web Portal
The Role of Password Management in Achieving Compliance

The Role of Password Management in Achieving Compliance
Centralized Self-service Password Reset: From the Web and Windows Desktop

Centralized Self-service Password Reset: From the Web and Windows Desktop
Sever-based Password Synchronization: Managing Multiple Passwords

Sever-based Password Synchronization: Managing Multiple Passwords
Configurable Password Management: Balancing Usability and Compliance

Configurable Password Management: Balancing Usability and Compliance
Avoiding Two-factor Authentication? You're Not Alone

Avoiding Two-factor Authentication? You're Not Alone
Portal Authentication: A Balancing Act Between Security Usability and Complia...

Portal Authentication: A Balancing Act Between Security Usability and Complia...
Recently uploaded
Recently uploaded (20)
(Genuine) Escort Service Lucknow | Starting ₹,5K To @25k with A/C 🧑🏽❤️🧑🏻 89...

(Genuine) Escort Service Lucknow | Starting ₹,5K To @25k with A/C 🧑🏽❤️🧑🏻 89...
Unveiling Design Patterns: A Visual Guide with UML Diagrams

Unveiling Design Patterns: A Visual Guide with UML Diagrams
Building Real-Time Data Pipelines: Stream & Batch Processing workshop Slide

Building Real-Time Data Pipelines: Stream & Batch Processing workshop Slide
Professional Resume Template for Software Developers

Professional Resume Template for Software Developers
Recruitment Management Software Benefits (Infographic)

Recruitment Management Software Benefits (Infographic)
Automate your Kamailio Test Calls - Kamailio World 2024

Automate your Kamailio Test Calls - Kamailio World 2024
Building a General PDE Solving Framework with Symbolic-Numeric Scientific Mac...

Building a General PDE Solving Framework with Symbolic-Numeric Scientific Mac...
Call Us🔝>༒+91-9711147426⇛Call In girls karol bagh (Delhi)

Call Us🔝>༒+91-9711147426⇛Call In girls karol bagh (Delhi)
PortalGuard Reports Uncover User Authentication Insights
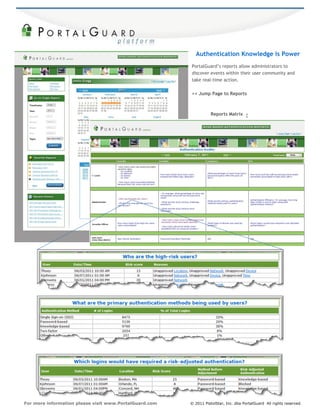
- 1. << © 2011 PistolStar, Inc. dba PortalGuard All rights reserved.For more information please visit www.PortalGuard.com Authentication Knowledge is Power PortalGuard’s reports allow administrators to discover events within their user community and take real-time action. << Jump Page to Reports Reports Matrix
- 2. More Reports Available... How many users have been blocked because their risk score was too low? How many users show multiple aborted password recoveries? How many users are accessing highly sensitive data (by location, device, network, or time)? What percentage of active users have had a password expire within the past 30 days? What is the average risk score (by user group)? And many more... Beyond Authentication: PortalGuard can pull real-time reports on... Devices: type, usage and location Productivity: are your employees working? Applications: who’s accessing them and when? Functionality: have users adopted it? Cost: can you answer the c-level questions? © 2011 PistolStar, Inc. dba PortalGuard All rights reserved.For more information please visit www.PortalGuard.com
