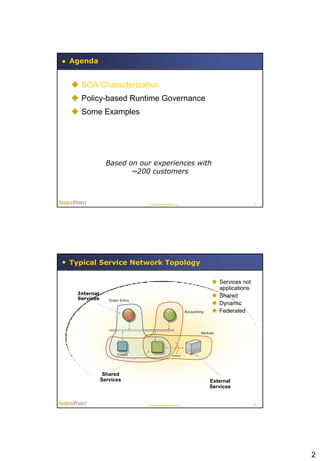
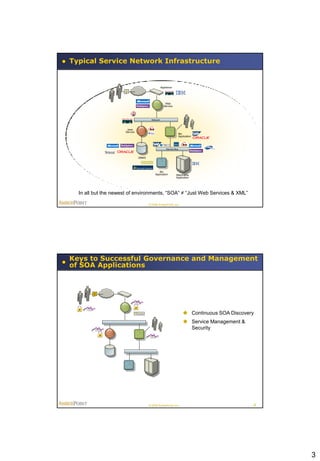
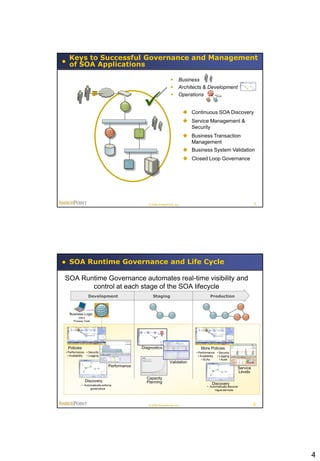
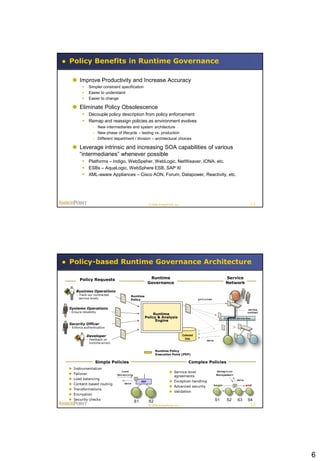
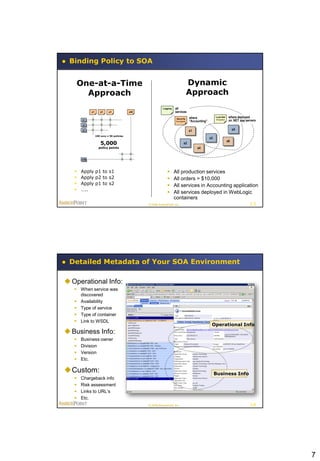
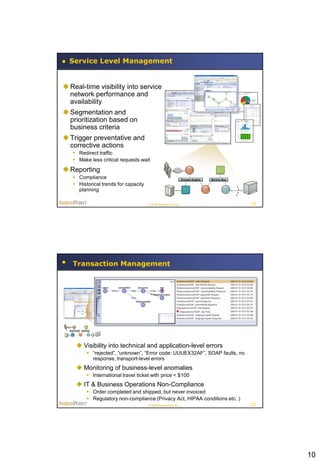
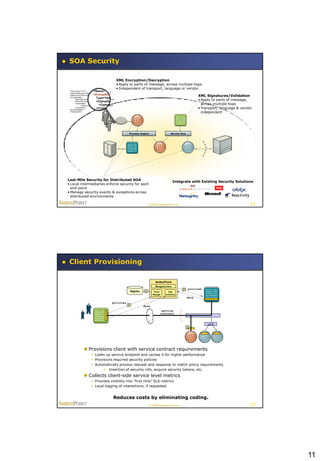
This document summarizes a presentation on policy-based runtime governance for SOA applications. It discusses how policies can specify governance constraints declaratively, provide benefits like improved productivity and reduced policy obsolescence, and be enforced at runtime using a policy engine. The architecture involves defining policies for stakeholders like business operations and security, and enforcing them at runtime execution points across the service network.